Wilamowski B.M., Irwin J.D. The Industrial Electronics Handbook. Second Edition: Industrial Communication Systems
Подождите немного. Документ загружается.


27-8 Industrial Communication Systems
27.3 Industrial Multimedia applications
27.3.1 Monitoring applications
Monitoring.applications.are.very.well.known.in.industrial.areas,.although.mainly.at.the.LAN.and.WAN.
leve
l.
.Typi
cally,
.in.all.kind
s
.of.indu
stries
.mach
ines
.are.quit
e
.larg
e,
.and.beca
use
.of.this.die
rent
.came
ras
.
tran
smit
.the.info
rmation
.to.the.cont
rol
.poin
t
.to.ensu
re
.the.corr
ect
.mana
gement
.of.the.mach
ine
.by.the.
work
er.
.Anot
her
.appl
ication
.is.that.the.imag
es
.are.requ
ired
.from.anot
her
.poin
t
.of.the.facto
ry
.for.work.
supe
rvision
.from.glob
al
.cont
rol
.cent
ers.
.ese.syst
ems
.are.oen.used.in.area
s
.that.pres
ent
.a.cert
ain
.
dang
er
.for.the.work
er.
.Fina
lly,
.glob
al
.cont
rol
.cent
ers
.need.to.moni
tor
.the.remo
te
.inst
allations’
.stat
e
.
in.orde
r
.to.cont
rol
.thei
r
.perf
ormance
.(esp
ecially
.to.cont
rol
.netw
ork
.util
ities
.[SAS
06][SSA07]).
.In.all.of.
thes
e
.situa
tions,
.mult
imedia
.info
rmation
.is.tran
smitted
.thro
ugh
.netw
orks
.for.a.bett
er
.use.of.mach
ines
.
and.equ
ipments
.due.to.the.ric
h
.con
text
.inf
ormation
.tha
t
.mul
timedia
.has.for.the.wor
kers.
e
.requ
irements
.of.this.type.of.appl
ication
.are.not.typi
cally
.too.dema
nding,
.but.they.are.conn
ected
.
to.the.nal.use.of.the.imag
es
.in.the.appl
ication
.and.the.netw
orks
.avai
lable,
.since.it.can.invo
lve
.stro
ng
.
limi
tations.
.e.imag
e
.reso
lutions
.are.usua
lly
.betw
een
.CIF.and.4CIF.or.VGA.since.thes
e
.reso
lutions
.are.
more.than.adeq
uate
.to.gath
er
.the.info
rmation
.of.inte
rest
.and.do.not.over
load
.the.huma
n
.capa
city
.for.
proc
essing
.this.type.of.info
rmation.
.Grea
ter
.reso
lutions
.can.be.used.if.the.imag
es,
.in.addi
tion
.to.live.
huma
n
.supe
rvision,
.are.store
d
.for.a.late
r
.use.(e.g
.,
.tech
nical
.repo
rts
.in.the.cont
rol
.of.util
ities
.netw
orks,
.
comp
laints
.in.surv
eillance
.appl
ications).
.e.qual
ity
.of.the.imag
es
.is.anot
her
.impo
rtant
.para
meter,
.and.
for.moni
toring
.appl
ications,
.it.is.consi
dered
.appr
opriate
.to.have.at.leas
t
.30.dB..Conc
erning
.tran
smission
.
time
s,
.we.can.consi
der
.here.two.grou
ps.
.In.the.appl
ications
.wher
e
.only.live.moni
toring
.is.perf
ormed
.
(wit
hout
.stora
ge)
.and.the.info
rmation
.is.used.by.the.work
er
.who.is.oper
ating
.the.mach
ine,
.this.late
ncy
.
has.to.be.lower.than.1000.ms,.since.the.machinery.has.to.be.managed.with.real-time.information..In.
the.seco
nd
.grou
p
.we.can.consi
der
.the.appl
ications
.wher
e
.a.huma
n
.oper
ator
.rece
ives
.and.proc
esses
.the.
info
rmation,
.usua
lly
.from.seve
ral
.sour
ces,
.and.in.whic
h
.ther
e
.is.no.stora
ge.
.In.this.case
,
.the.late
ncy
.is.
conn
ected
.wit
h
.the.hum
an
.cap
acity
.for.pro
cessing
.thi
s
.typ
e
.of.inf
ormation.
27.3.2 Computer Vision applications
ese.types.of.applications.are.characterized.by.the.use.of.image.processing.techniques.for.industrial.
autom
ation.
.ere.are.basic
ally
.thre
e
.appl
ication
.type
s:
.oine.insp
ection
.appl
ications,
.onli
ne
.insp
ec-
tion
.appl
ications,
.and.guid
ance
.appl
ications
.(suc
h
.as.robo
ts).
.In.the.rst.case
,
.they.are.appl
ications
.of.
qual
ity
.cont
rol.
.eir.objec
tive
.is.to.know.the.prod
uct’s
.stat
e
.in.orde
r
.to.dete
rmine
.what.furt
her
.pro-
c
essing
.is.nece
ssary,
.or.in.the.case.of.nis
hed
.prod
ucts,
.its.deli
very
.to.the.custo
mer.
.A.very.high.work
-
ing
.spee
d
.may.be.requ
ired
.even.thou
gh
.ther
e
.are.no.hard.real
-time
.requ
irements.
.For.exam
ple,
.qual
ity
.
insp
ection
.of.20–8
0
.m/mi
n
.of.fabr
ic,
.but.in.whic
h
.the.faul
ts
.are.store
d
.for.repo
rt
.purp
oses,
.or,.in.case
s
.
wher
e
.it.is.nece
ssary
.to.stop.the.mach
ine,
.ther
e
.is.some.toler
ance
.in.the.orde
r
.dela
y.
.In.the.seco
nd
.case
,
.
the.visio
n
.syst
em
.insp
ects
.the.prod
uct
.or.the.proc
ess
.in.orde
r
.to.dete
rmine
.what.acti
on
.is.nece
ssary.
.In.
othe
r
.word
s,
.the.imag
e
.proc
essing
.resu
lt
.will.have.cons
equences
.on.the.prod
uction
.proc
ess
.(e.g
.,
.regu
la-
tion
.on.the.widt
h
.of.rubb
er
.band
s
.[SS0
7]),
.and.ther
efore,
.ther
e
.are.some.temp
oral
.rest
rictions
.that.must.
be.adhe
red
.to.in.the.tran
smission
.and.proc
essing
.of.imag
es.
.In.the.thir
d
.appl
ication
.type
,
.the.info
rma-
tion
.extr
acted
.from.the.imag
es
.is.used.to.guid
e
.the.mana
gement
.of.cutt
ing
.stan
ds,
.robo
ts,
.etc.,.and.in.
whic
h
.cas
e
.adh
erence
.to.tem
poral
.req
uirements
.is.eve
n
.mor
e
.imp
ortant.
A
.comm
on
.requ
irement
.of.the.thre
e
.type
s
.of.comp
uter
.visi
on
.appli
cation
.is.the.nece
ssity
.of.high
-
quality
.imag
es.
.ere.has.been.some.work.carr
ied
.out.to.anal
yze
.the.limi
ts
.of.imag
e
.degr
adation,
.but.
this.has.been.main
ly
.for.spec
ic
.medi
cal
.appli
cations,
.and.ther
e
.have.been.no.stud
ies
.on.indu
strial
.
envi
ronments
.or.into.a.gene
ral
.theo
ry
.to.gain.prio
r
.know
ledge
.of.this
.
.e.targ
et
.of.the.comp
uter
.
visi
on
.appli
cation
.dete
rmines
.the.imag
e
.reso
lution
.and.the.tran
smission
.time
s.
.Typi
cal
.appli
cations
.
use.4CIF.reso
lution
.with.tran
smission
.betw
een
.1.and.60.fram
es/s.
.In.some.case
s,
.more.than.one.came
ra
.
© 2011 by Taylor and Francis Group, LLC

Industrial Multimedia 27-9
is.necessary,.or.even.in.wide.network.inspection,.the.use.of.lineal.cameras.(lineal.cameras.are.devices.
with.a.sens
or
.of.only.one.line.of.pixe
ls
.form
ing
.the.imag
e
.with.the.conc
atenation
.of.cons
ecutive
.line
s).
27.4 Image transmission
Since.processing.of.image/video.data.typically.does.not.take.place.in.the.camera.that.captures.the.data,.
the.data.has.to.be.tran
smitted
.over.some.kind.of.data.netw
ork.
.ere.are.tran
sport
.proto
cols
.that.den
e
.
how.mult
imedia
.data.has.to.be.put.into.data.pack
ets
.that.are.sent.on.the.netw
ork
.[W06
].
.is.typi
cally
.
also.invo
lves
.some.time
stamps
.that.are.used.for.sync
hronization
.purp
oses.
.ere.are.also.proto
cols
.
nece
ssary
.to.set.up.and.star
t
.stre
aming
.of.the.data.over.the.netw
ork.
.ese.proto
cols
.are.usua
lly
.tigh
tly
.
coup
led
.with.the.tran
sport
.proto
cols.
.Each.kind.of.netw
ork
.has.die
rent
.kind
s
.of.data.form
ats
.that.are.
tran
sported
.by.the.tran
sport
.proto
col.
.is.depe
nds
.on.the.spec
ial
.feat
ures
.(lik
e
.avai
lable
.band
width)
.
of.the.netw
ork.
.Two.kind
s
.of.netw
ork
.will.be.desc
ribed
.more.in.deta
il
.here
:
.IEEE.1394.and.IP-ba
sed
.
netw
orks
.(ty
pically
.bas
ed
.on.Ethe
rnet)
.[W0
5].
27.4.1 IEEE 1394
IEEE.1394.[IEEE1394],.also.known.as.FireWire.or.i.Link,.is.a.serial.bus.designed.to.connect.up.to.
63.devi
ces
.(lik
e
.camc
orders,
.CD.play
ers,
.sate
llite
.tune
rs,
.but.also.pers
onal
.comp
uters
.and.peri
pherals
.
like.hard.disk
s,
.scann
ers,
.etc.
).
.e.orig
inal
.vers
ion
.of.this.bus.supp
orts
.up.to.400.Mbps
,
.has.an.auto
matic
.
con
guration
.mecha
nism
.allo
wing
.hot.plug
ging
.of.devi
ces,
.and.is.very.well.suit
ed
.for.stre
aming
.of.mult
i-
media
.cont
ent
.[A99
].
.It.supp
orts
.4.5.m.link
s
.and.up.to.16.hops.betw
een
.two.devi
ces
.lead
ing
.to.a.maxi
mum
.
dist
ance
.of.72.m.betw
een
.two.node
s.
.is.clea
rly
.show
s
.that.it.is.suit
ed
.for.smal
l
.area.envi
ronments
.like.
home
s
.or.auto
mobiles,
.but.it.is.used.in.indu
strial
.envi
ronments
.as.well
.
.IEEE.1394
a
.[IEE
E1394a]
.intr
o-
duced
.some.new.feat
ures,
.main
ly
.to.incr
ease
.the.bus.eci
ency
.(redu
ction
.of.idle.time
s),
.but.the.main.
char
acteristics
.were.prese
rved.
.e.newe
r
.vers
ion
.IEEE.1394
b
.supp
orts
.up.to.1600.Mbps.and.has.arch
itec-
tural
.supp
ort
.for.3200.Mbps.[IEE
E1394b].
.It.intr
oduced
.some.new.phys
ical
.media.in.addi
tion
.to.shie
lded
.
twis
ted
.pair.(STP
)
.copp
er
.cabl
es
.and.also.incr
eased
.the.maxi
mum
.dist
ance
.betw
een
.devi
ces
.(up.to.100.m.
usin
g
.opti
cal
.ber
s
.or.CAT-
5
.UTP)
.
.e.tran
smission
.mode
l
.and.codi
ng
.of.data.is.comp
letely
.die
rent
.to.
IEEE.1394
a;
.howe
ver,
.comp
atibility
.is.main
tained
.by.intr
oduction
.of.bili
ngual
.node
s.
On
.the.physi
cal
.laye
r,
.a.Fire
Wire
.bus.is.a.tree.consi
sting
.of.poin
t-to-point
.conn
ections
.betw
een
.the.
devi
ces.
.Howe
ver,
.the.physi
cal
.laye
r
.tran
sforms
.this.tree.into.a.logi
cal
.bus,.wher
e
.each.node.(exc
ept
.the.
node.that.is.curr
ently
.tran
smitting
.a.pack
et)
.acts.as.repe
ater.
.e.high
er
.laye
rs
.(lin
k
.laye
r
.and.tran
sac-
tion
.laye
r
.of.the.thre
e-layer
.desig
n
.used.in.IEEE.1394
)
.have.a.view.as.a.bus,.wher
e
.all.pack
ets
.are.rece
ived
.
by.eve
ry
.nod
e,
.pro
vided
.the.use
d
.spe
ed
.is.sup
ported
.on.all.lin
ks
.in.bet
ween.
Two
.dieren
t
.data.tran
sfer
.mode
s
.are.supp
orted:
.asyn
chronous
.and.isoc
hronous
.data.tran
sfer.
.e.
isochronous.mode.has.been.designed.to.meet.the.requirements.of.multimedia.streaming..There.
are.64.isoc
hronous
.chan
nels.
.Such.chan
nel
.can.be.rega
rded
.as.a.mult
icast
.grou
p.
.In.fact
,
.the.pack
ets
.are.
tran
smitted
.to.each.node.on.the.netw
ork,
.but.the.hard
ware
.insi
de
.the.node.usua
lly
.lter
s
.and.disc
ards
.
pack
ets
.of.isoc
hronous
.chan
nels
.that.are.not.of.inter
est.
.ere.is.a.reso
urce
.mana
gement
.mech
anism:
.
band
width
.and.chan
nel
.can.be.reser
ved
.at.the.isoc
hronous
.reso
urce
.mana
ger
.(a.func
tionality
.prov
ided
.
by.one.of.the.node
s
.in.the.netw
ork)
.and.are.then.guar
anteed.
.is.mean
s
.that.qual
ity
.of.servi
ce
.is.pro-
v
ided.
.e.requ
irement
.for.the.guar
antee
.of.isoc
hronous
.band
width
.is.that.all.node
s
.have.to.obey.the.
rule
s
.of.IEEE.1394.and.reser
ve
.band
width
.and.chan
nel
.befo
re
.they.are.used
.
.Sinc
e
.this.is.not.enfor
ced
.
by.hard
ware
.or.sow
are,
.node
s
.viol
ating
.thes
e
.rule
s
.can.comp
romise
.QoS..e.sour
ce
.can.send.one.
isoc
hronous
.pack
et
.every.125.μs.(lea
ding
.to.8000.isoc
hronous
.cycl
es/s).
.e.allo
wed
.size.of.the.pack
et
.
corr
esponds
.to.the.reser
ved
.band
width.
.In.case.of.error
s,
.no.retr
ansmission
.occu
rs,
.so.timi
ng
.is.guar
an-
teed,
.but.not.deli
very.
.On.the.other.side
,
.the.asyn
chronous
.tran
sfer
.mode.is.used.for.deli
very
.of.vari
able-
length
.pack
ets
.to.expl
icitly
.addr
essed
.node
s.
.ere.is.an.ackn
owledgment
.and.a.retr
y
.proc
edure
.in.case.
of.error
s.
.eref
ore,
.the.deli
very
.of.inte
ger
.data.can.be.guar
anteed,
.but.timi
ng
.is.not.guar
anteed.
© 2011 by Taylor and Francis Group, LLC
27-10 Industrial Communication Systems
In.the.area.of.streaming.multimedia.data,.asynchronous.transactions.are.not.used.for.the.transfer.
of.mul
timedia,
.but.the
y
.are.use
d
.for.con
trol
.pur
poses.
.IEC.618
83-1
.use
s
.asy
nchronous
.tra
nsactions
.for.
set
up
.and.tea
rdown
.of.iso
chronous
.con
nections,
.whi
ch
.als
o
.inc
ludes
.the.iso
chronous
.res
ource
.man
age-
ment
.[IE
C61883-1].
.Hig
her
.lev
el
.con
trol
.pro
tocols
.lik
e
.AV/
C
.are.bas
ed
.on.IEC.618
83-1
.and.use.asy
nchro-
nous
.tra
nsactions
.to.com
municate.
.Rea
l-time
.tra
nsmission
.of.aud
io
.and.vid
eo
.dat
a
.is.wel
l-standardized
.
by.the.ser
ies
.of.IEC
61883.
.IEC.618
83-1
.de
nes
.gen
eral
.thi
ngs
.lik
e
.a.com
mon
.for
mat
.for.iso
chronous
.
pac
kets
.as.wel
l
.as.mec
hanisms
.for.est
ablishing
.and.bre
aking
.iso
chronous
.con
nections
.[IE
C61883-1].
.
is.al
so
.in
cludes
.ti
mestamps,
.wh
ich
.ar
e
.us
ed
.fo
r
.sy
nchronization
.[W
Z03].
Transmission
.of.dat
a
.in.the.dig
ital
.vid
eo
.(DV
)
.for
mat
.[IE
C61834-2]
.(ty
pically
.use
d
.on.han
dheld
.
dig
ital
.vid
eo
.cam
eras)
.is.spe
cied
.in.IEC.618
83-2
.[IE
C61883-2].
.An.adv
antage
.of.thi
s
.for
mat
.is.the.
hig
h
.qua
lity
.and.a.low.com
plexity
.of.enc
oding
.and.dec
oding
.bec
ause
.it.doe
s
.not.use.the.sop
histicated
.
int
erframe
.com
pression
.tec
hniques
.kno
wn
.fro
m
.MPE
G-2.
.On.the.oth
er
.han
d,
.it.imp
oses
.rat
her
.hig
h
.
ban
dwidth
.req
uirements
.(ab
out
.25.Mbp
s
.for.an.SD.for
mat
.DV.vid
eo
.str
eam,
.toge
ther
.wit
h
.aud
io
.and.
oth
er
.in
formation
.it.yi
elds
.ab
out
.29.Mbp
s).
For
.tra
nsmission
.of.aud
io
.dat
a,
.IEC.618
83-6
.is.use
d
.[IE
C61883-6].
.It.is.use
d
.by.con
sumer
.ele
ctronic
.
aud
io
. equ
ipment
. lik
e
. CD. pla
yers,
. amp
liers,
. spe
aker
. sys
tems,
. etc
.
. Usu
ally,
. aud
io
. is. dis
tributed
. as.
unc
ompressed
.aud
io
.sam
ples
.at.44,
100
.or.48,
000
.Hz.sam
ple
.rat
e,
.but.oth
er
.dat
a
.for
mats
.are.sup
ported
.as.
wel
l.
.But.aud
io
.dis
tribution
.is.de
nitely
.mor
e
.of.int
erest
.in.hom
e
.env
ironments
.tha
n
.in.ind
ustrial
.one
s.
Transmission
.of.MPE
G-2
.tra
nsport
.str
eams
.[MP
G2]
.ove
r
.IEE
E
.139
4
.is.spe
cied
.in.IEC.618
83-4
.
[IEC61883-4]..is.allows.the.distribution.of.digital.television.over.IEEE.1394,.since.both.DVB.and.
ATS
C
.use.MPE
G-2
.tra
nsport
.str
eams.
.MPE
G-2
.pro
vides
.a.goo
d
.tra
de-o
.bet
ween
.qua
lity
.and.uti
lized
.
ban
dwidth.
.A.ty
pical
.PA
L
.TV.pr
ogram
.re
quires
.ab
out
.6.Mbp
s.
In
.add
ition
.to.the.two.pos
sibilities
.bas
ed
.on.IEC.618
83
.men
tioned
.abo
ve
.to.tra
nsmit
.vid
eo
.in.DV.
or.MPE
G-2
.dat
a
.for
mat,
.the
re
.is.ano
ther
.pro
tocol
.tha
t
.is.pri
marily
.tar
geting
.ind
ustrial
.env
ironments
.
(al
beit
.the
re
.are. som
e
. Web. cam
eras
.usin
g
.thi
s
.pro
tocol
.as.wel
l):
. the.Ins
trumentation
.&. Ind
ustrial
.
Dig
ital
.Cam
era
.(II
DC)
.pro
tocol
.[II
DC1394].
.is.is.a.ver
y
.simp
le
.pro
tocol
.(no
t
.bas
ed
.on.IEC.618
83)
.
tha
t
.tra
nsmits
.unc
ompressed
.dig
ital
.vid
eo
.ove
r
.iso
chronous
.Fir
eWire
.cha
nnels.
.er
efore,
.it.req
uires
.
sign
icantly
.mo
re
.ba
ndwidth,
.bu
t
.do
es
.no
t
.re
quire
.en
coding
.an
d
.de
coding.
27.4.2 IP-Based Networks
IP,.the.Internet.protocol,.is.a.very.widely.used.network.protocol..e.main.reason.is.that.it.can.be.used.on.
top.of.alm
ost
.eve
ry
.low
er
.laye
r
.net
working
.sys
tem
.(Et
hernet,
.tok
en
.rin
g,
.IEE
E
.139
4,
.etc
.)
.[AS
T03].
.es
e
.
net
works
.wer
e
.not.des
igned
.for.the.pur
pose
.of.mul
timedia
.tra
nsmission
.and
,
.the
refore,
.hav
e
.som
e
.wea
k-
nesses
.wit
h
.reg
ard
.to.rea
l-time
.dat
a
.tra
nsmission.
.QoS.is.ver
y
.lim
ited.
.er
e
.are.mec
hanisms
.for.QoS.
in.IP.net
works,
.but.the
y
.pro
vide
.onl
y
.so.gua
rantees.
.e.res
ource
.res
ervation
.pro
tocol
.(RS
VP)
.is.the.
sta
ndard
.pro
tocol
.to.res
erve
.res
ources
.in.IP.net
works
.[WZ0
1].
.In.fact
,
.RSV
P
.is.onl
y
.a.sig
naling
.pro
tocol
.
for.res
ource
.res
ervation
.req
uests
.and.doe
s
.not.by.its
elf
.res
erve
.res
ources.
.IP.net
works
.onl
y
.oe
r
.bes
t
.eo
rt
.
ser
vices,
.and.the
refore,
.QoS.is.usu
ally
.onl
y
.ach
ieved
.by.ove
rsizing
.the.net
work
.and.pro
viding
.muc
h
.mor
e
.
per
formance
.tha
n
.nee
ded
.in.ave
rage
.to.ensu
re
.goo
d
.per
formance
.eve
n
.in.wors
t-case
.sce
narios.
Besides
.the.so-
called
.int
egrated
.ser
vices
.app
roach
.wit
h
.per
-stream
.res
ervations,
.the
re
.is.als
o
.the.dif
-
ferentiated
.ser
vices
.app
roach,
.whi
ch
.doe
s
.not.pro
vide
.per
-stream
.res
ervations,
.but.has.adv
antages
.in.
sca
lability
.[WZ
01].
.Bel
ow
.IP,.on.the.Ethe
rnet
.lay
er,
.IEE
E
.802
.1p
.als
o
.pro
vides
.som
e
.kin
d
.of.QoS.mec
ha-
nism.
.But.thi
s
.is.ver
y
.wea
k.
.It.jus
t
.all
ows
.de
ning
.pri
orities
.of.ind
ividual
.Ethe
rnet
.pac
kets.
.It.doe
s
.not.
res
erve
.res
ources
.and.doe
s
.not.pro
vide
.any.gua
rantees.
.One.pro
blem
.of.IP.net
works
.is.tha
t
.tra
nsmis-
sion
.of.aud
io
.and.vid
eo
.is.not.ver
y
.wel
l-standardized.
.er
e
.is.a.wid
e
.var
iety
.of.dat
a
.and.tra
nsmission
.
for
mats,
.op
en
.an
d
.pr
oprietary
.on
es,
.wh
ich
.ar
e
.no
t
.co
mpatible
.wi
th
.ea
ch
.ot
her.
In
.IP-
based
.net
works,
.man
y
.di
erent
.pro
tocols
.are.com
monly
.used.for.rea
l-time
.tra
nsmission
.of.mul
-
timedia.
.e.mos
t
.pri
mitive
.one.is.HTT
P,
.the.hyp
ertext
.tra
nsfer
.pro
tocol.
.er
e
.are.imp
lementations
.tha
t
.
use.HTT
P
.to.str
eam
.rea
l-time
.aud
io
.dat
a.
.But.bes
ides
.some.adva
ntages
.(it.is.ver
y
.sim
ple
.and.wor
ks
.wel
l
.
© 2011 by Taylor and Francis Group, LLC

Industrial Multimedia 27-11
with.proxies.and.rewalls),.it.also.has.many.disadvantages..It.does.not.support.multicast,.only.unicast..
ere
fore,
.if.more.than.one.node.is.list
ening
.to.the.stre
am,
.sever
al
.conn
ections
.have.to.be.esta
blished
.that.
use.the.corr
esponding
.mult
iple
.of.the.neces
sary
.band
width.
.Furt
hermore,
.HTTP.is.based.on.TCP,.whic
h
.
is.a.reli
able
.prot
ocol,
.that.is,.it.does.perf
orm
.retr
ansmission
.of.pack
ets
.that.were.not.tran
smitted
.corr
ectly.
.
is.is.comp
letely
.inad
equate
.for.real
-time
.tran
smission
.becau
se
.the.retr
ansmitted
.data.will.oen.be.late.
and,.ther
efore,
.usele
ss.
.In.fact
,
.the.use.of.HTTP.is.just.an.exte
nsion
.of.prog
ressive
.down
load
.(the.prese
nta-
tion
.of.a.mult
imedia
.le.star
ts
.whil
e
.down
loading),
.but.it.was.neve
r
.desi
gned
.for.real.stre
aming.
A
.much.more.suit
able
.prot
ocol
.for.tran
smission
.of.mult
imedia
.data.is.real
-time
.tran
sport
.prot
ocol
.
(RTP
)
.as.prop
osed
.in.RFC1
889,
.whic
h
.is.usua
lly
.based.on.UDP.and.in.prin
ciple
.supp
orts
.mult
icast
.as.well.
as.unic
ast.
.It.also.incl
udes
.time
stamps,
.whic
h
.are.used.for.sync
hronization
.purp
oses;
.but.it.has.to.deal.
with.the.fact.that.in.IP.netw
orks
.ther
e
.is.no.glob
al
.time.base.that.is.sync
hronized
.auto
matically.
.Real
-time
.
stre
aming
.prot
ocol
.(RTS
P)
.can.be.used.for.setti
ng
.up.the.tran
smission.
.ere.are.also.prop
rietary
.prot
o-
cols
.like.Micr
oso
.media.serve
r
.(MMS
)
.or.Real.deli
very
.tran
sport
.(RDT
)
.and.othe
rs.
.ey.have.simi
lar
.
feat
ures
.and.are.used.by.the.tool
s
.of.the.corr
esponding
.comp
anies
.(Mic
roso,
.Real
Networks,
.etc.
).
Many
.die
rent
.(ope
n
.and.prop
rietary)
.form
ats
.for.audi
o
.and.vide
o
.exis
t
.and.can.be.tran
smitted
.in.an.
RTP.stre
am
.[W05
].
.Conce
rning
.audi
o,
.the.most.impo
rtant
.open.form
ats
.are.unco
mpressed
.audi
o
.with.16,.
20,.or.24.bit.reso
lution
.and.MPEG.comp
ressed
.audi
o
.stre
ams.
.For.vide
o,
.RFC2
250
.spec
ies
.how.to.tran
smit
.
MPEG.vide
o
.elem
entary
.stre
ams.
.If.audi
o
.and.vide
o
.are.to.be.tran
smitted
.in.one.stre
am,
.MPEG-
2
.tran
sport
.
stre
ams
.can.be.used
,
.but.the.conc
ept
.of.RTP.is.to.tran
sport
.each.medi
a
.in.a.sepa
rate
.stre
am
.rath
er
.than.usin
g
.
multiplexes..Digital.video.in.the.DV.format.of.IEC.61834.[IEC61834-2].can.be.transported.in.RTP.according.
to.RFC3
189
.[IEC
61883-2].
.Howe
ver,
.it.shou
ld
.be.ment
ioned
.that.this.is.a.form
at
.comm
only
.used.on.IEEE.
1394.[IEC
61883-2]
.but.not.on.IP.netw
orks.
.Impo
rtant
.prop
rietary
.form
ats
.are.Real
Audio
.and.Real
Video.
IPv6,
.the.succ
essor
.of.IP.versi
on
.4,.has.some.adva
ntages
.conc
erning
.mult
imedia
.stre
aming.
.Mult
icast
.
has.been.inte
grated
.into.IPv6
,
.so.ever
y
.comp
liant
.impl
ementation
.supp
orts
.mult
icast.
.ere.are.feat
ures
.
(esp
ecially
.the.ow.labe
ls
.shou
ld
.be.ment
ioned)
.that.make.the.prov
ision
.of.QoS.for.stre
ams
.easi
er.
.
e.func
tionality
.of.Inte
rnet
.Grou
p
.Mana
gement
.Proto
col
.(IGM
P)
.is.inte
grated
.into.ICMP
v6
.(Int
ernet
.
cont
rol
.mess
age
.proto
col).
.e.“mul
ticast
.list
ener
.disc
overy”
.(MLD
)
.used.for.the.signa
ling
.betw
een
.
rout
ers
.and.hos
ts
.is.a.sub
protocol
.of.ICM
Pv6.
27.5 Conclusions
Multimedia.has.a.wide.range.of.applications.in.the.industrial.area..ese.applications.also.have.a.wide.range.
of.requ
irements,
.like.reso
lution,
.fram
e
.rate
s,
.imag
e
.qual
ity,
.late
ncy,
.etc..Indu
strial
.comm
unications
.netw
orks
.
prov
ide
.the.nece
ssary
.infra
structure
.for.many.appl
ications.
.In.this.chap
ter,
.indu
strial
.mult
imedia
.appl
ica-
tions
.and.thei
r
.part
icular
.requ
irements
.are.disc
ussed.
.Compr
ession
.tech
nology,
.which.is.need
ed
.in.many.
appl
ications
.due.to.band
width
.or.stor
age
.limit
ations,
.is.brie
y
.revi
ewed.
.Fina
lly,
.two.die
rent
.exam
ples
.of.
netw
ork
.and.the.asso
ciate
.prot
ocols
.for.tran
smission
.of.mult
imedia
.data.are.pres
ented.
acknowledgment
is.work.was.partially.supported.by.de.MCYT.of.Spain.under.the.project.TSI2007-66637-C02-02.
references
[A99].D..Anderson..FireWire System Architecture: IEEE 1394a,.2nd.edn.,.Addison-Wesley,.Reading,.MA,.
1999..ISBN.0-201-48535-04.
[AST03]
.A..S..Tanen
baum.
.Comp
uter Networks. Paerson Education International,
.4th.edn.,.Upper.Saddle.
River
,
.NJ,.2003..ISBN.0-13-038488-7.
[CS
E00]
.C..Chri
stopoulos,
.A..Skod
ras,
.and.T..Ebra
himi.
.The.JPEG
2000
.stil
l
.imag
e
.codi
ng
.syst
em:
.an.
over
view,
.IEEE
Transactions on Consumer Electronics
.46(4
),
.1103
–1127,
.2000
.
© 2011 by Taylor and Francis Group, LLC
27-12 Industrial Communication Systems
[IEC61883-1].IEC..Consumer Audio/Video Equipment—Digital Interface—Part 1: General. Standard IEC
61883-1,
.1st.edn.,.IEC,.Gen
eva,
.Sw
itzerland,
.Fe
bruary
.1998.
[IEC61834-2]
. IEC.. Rec
ording—Helical-Scan Digital Video Cassette Recording System Using 6,35
mm
Ma
gnetic Tape for Consumer Use (525–60, 625–50, 1125–60 and 1250–50 systems)—Part 2: SD
Format for 525–60 and 625–50 Systems.
.Sta
ndard
.IEC.61834-2,.1st.edn.,.IEC,.Gene
va,
.Swi
tzerland,
.
Augus
t
.1998.
[IEC61883-2]
. IEC.. Cons
umer Audio/Video Equipment—Digital Interface—Part 2: SD-DVCR Data
Transmission.
.St
andard
.IEC.61883-2,.1st.edn.,.IEC,.Gen
eva,
.Sw
itzerland,
.Fe
bruary
.1998.
[IEC61883-6]
.IEC..Cons
umer Audio/Video Equipment—Digital Interface—Part 6: Audio and Music Data
Transmission Protocol.
.St
andard
.IEC.61883-6,.1st.edn.,.IEC,.Gen
eva,
.Sw
itzerland,
.Oc
tober
.2002.
[IEC61883-4]
. IEC.. Cons
umer Audio/Video Equipment—Digital Interface—Part 4: MPEG2-TS Data
Transmission.
.St
andard
.IEC.61883-4,.1st.edn.,.IEC,.Gen
eva,
.Sw
itzerland,
.Fe
bruary
.1998.
[IEEE1394]
.IEEE.Com
puter
.Societ
y.
.IEEE St
andard for a High Performance Serial Bus.
.Sta
ndard
.IEEE.
1394-1995,.Ne
w
.Yo
rk,
.1995.
[IEEE1394a]
.IEEE.Com
puter
.Societ
y.
.IEEE St
andard for a High Performance Serial Bus—Amendment 1.
Standard IEEE 1394a-2000,
.Ne
w
.Yo
rk,
.Ma
rch
.2000.
[IEEE1394b]
.IEEE.Com
puter
.Societ
y.
.IEEE St
andard for a High Performance Serial Bus—Amendment 2.
Standard IEEE 1394b-2002,
.Ne
w
.Yo
rk,
.De
cember
.2002.
[IIDC1394]
.1394.Trade.Ass
ociation.
.IIDC 1394-b
ased Digital Camera Specication Ver.1.31, TA Document
2003017,
.Grapevine,.TX,.February.2004.
[ISO94]
. Inf
ormation Technology-Digital Compression and Coding of Continuous Tone Still Images:
Requirements and Guidelines.
. Int
ernational
. Organiza
tion
. for. Sta
ndardization/International
.
Elec
trotechnical
.Co
mission
.(ISO/IEC).10918-1,.Gen
eva,
.Sw
itzerland,
.Fe
bruary
.1994.
[M
PG2]
.ISO
/IEC.
.Inf
ormation Technology—Generic Coding of Moving Pictures and Associated Audio Information:
Systems.
.Int
ernational
.Sta
ndard
.ISO
/IEC
.138
18-1,
.2nd.edn
.,
.Gen
eva,
.Swi
tzerland
.ISO
/IEC,
.200
0.
[P98]
.J..R..Pim
entel.
.In
dustrial
.mu
ltimedia
.syst
em,
.IEEE In
dustrial Electronics Newsletter
.45(2),.1998.
[R
SB99]
.S..M..Rah
man,
.R..Sar
ker,
.B..Big
naill.
.App
lication
.of.mul
timedia
.tec
hnology
.in.man
ufacturing:
.
A.rev
iew,
.Co
mputer in Industry
.38,.43–52,.1999.
[S
AS06]
.V..Sem
pere,
.T..Alb
ero,
.and.J..Sil
vestre.
.Ana
lysis
.of.com
munication
.alt
ernatives
.in.a.het
-
erogeneous
.net
work
.for.a.sup
ervision
.and.con
trol
.sys
tem,
.Com
puter Communications
.29(
8),
.
113
3–114,
.200
6.
[SS07]
.J..Sil
vestre
.and.V..Semp
ere.
.An.arc
hitecture
.for.exible.sch
eduling
.in.Pro
bus
.netw
orks,
.Com
puter
Standards & Interfaces
.29,.546–560,.2007.
[SSA04]
.J..Sil
vestre,
.V..Semp
ere,
.and.T..Alb
ero.
.Ind
ustrial
.video.seq
uences
.for.netw
ork
.perf
ormance
.eval-
u
ation,
.in.Pro
ceedings of International IEEE Factory Communication Systems,
.Vienna,.Aus
tria,
.2004,.
pp..343–347.
[SSA07]
.J..Sil
vestre,
.V..Semp
ere,
.and.T..Alb
ero.
.Wire
less
.metr
opolitan
.are
a
.netw
orks
.for.telem
onitoring
.
app
lications,
.in.Pro
ceedings of the Seventh IFAC International Conference on Fieldbuses & Networks
in Industrial & Embedded System,
.To
ulouse
.Uni
versity,
.Fra
nce,
.No
vember
.7–9,.2007.
[V
RZ07]
.M..Vra
njez,
.S..Rim
ac-Drlje,
.and.D..Zag
ar.
.Obj
ective
.vid
eo
.qua
lity
.met
rics,
.in.Pro
ceedings
of the 49th International IEEE Symposium ELMAR,
.Zad
ar,
.Cro
atia,
.Sep
tember
.12–
14,
.200
7,
.
pp..45–
49.
[W05]
. M.. Wei
hs.
. Mul
timedia
. str
eaming
. in. hom
e
. env
ironments,
. in. P.. Lor
enz
. and. P.. Din
i,
. edi
tors,
.
Net
working—ICN 2005: Fourth International Conference on Networking,
.Reu
nion
.Isl
and,
.Fra
nce,
.Apr
il
.
17–
21,
.200
5;
.Pro
ceedings,
.Par
t
.I,.num
ber
.342
0
.in.LNC
S,
.pp..873
–881,
.Reu
nion
.Isl
and,
.Fra
nce,
.
Apr
il
.200
5.
.IEE
E,
.IEE
,
.IAR
IA,
.Spr
inger-Verlag.
.ISB
N
.3-5
40-25339-4.
.doi
:
.10.
1007/b107117.
[W06]
.M..Weih
s.
.Con
vergence
.of.rea
l-time
.audio.and.video.str
eaming
.tec
hnologies.
.PhD.diss
ertation,
.
Vienna.Uni
versity
.of.Te
chnology,
.Vienn
a,
.Au
stria,
.2006.
[WBSS04]
.Z..Wan
g,
.C..Bov
ik,
.H..R..Shei
kh,
.and.E..P..Simo
ncelli.
.Ima
ge
.qua
lity
.ass
essment:
.Fro
m
.visi
bility
.
to.st
ructural
.Simi
larity,
.IEEE Tr
ansactions on Image Processing
.13(4),.600–612,.2004.
© 2011 by Taylor and Francis Group, LLC
Industrial Multimedia 27-13
[WIF01].C.-H..Wu,.J..D..Irwin,.and.F..F..Dai..Enabling.multimedia.applications.for.factory.automation,.
IEEE Tra
nsactions on Industrial Electronics
.48(5),.913–919,.2001.
[WZ01]
.R..Wit
tmann
.and.M..Zit
terbart.
.Mul
ticast Communication—Protocols and Applications,
.Academic.
Pres
s,
.San.Diego
,
.CA,.2001..ISB
N
.1-55860-645-9.
[WZ03]
. M.. Weih
s
. and. M.. Zieh
ensack.
. Con
vergence
. betw
een
. IEEE. 1394. and. IP. for. rea
l-time
. A/V.
tran
smission,
.in.D..Dietric
h,
.P..Neuma
nn,
.and.J.-P..om
esse,
.edit
ors,
.Fie
ldbus Systems and eir
Applications 2003,
.Av
eiro,
.Po
rtugal,
.IFA
C,
.El
sevier,
.2003,.pp
.
.299–305..ISB
N
.0-08-044247-1.
© 2011 by Taylor and Francis Group, LLC
© 2011 by Taylor and Francis Group, LLC
28-1
28.1 Introduction
e.use.of.wireless.communications.in.industrial.environments.poses.a.dierent.set.of.challenges.than.
depl
oyment
.in.home.and.ente
rprise
.envi
ronments.
.Sign
icant
.amou
nts
.of.elec
trical
.nois
e
.such.as.vari
-
able
.freq
uency
.driv
es,
.comp
eting
.radi
o
.syst
ems,
.rada
r
.and.micr
owave
.sour
ces,
.and.weld
ers
.are.pro-
d
uced
.in.ind
ustrial
.env
ironments.
.Sig
nal
.att
enuation
.and.re
ects
.are.alw
ays
.pre
sent
.[1]
.
e
.plac
ement
.of.wire
less
.acce
ss
.poin
ts
.(APs
),
.or.radi
o
.node
s,
.and.adju
stment
.of.tran
smitter
.powe
r
.
to.matc
h
.rece
iver
.sensi
tivities
.is.more.cruc
ial
.in.indu
strial
.sett
ings
.wher
e
.the.reli
ability
.of.the.over
all
.
syst
em
.can.aec
t
.plan
t
.safe
ty
.and.secu
rity
.as.well.as.oper
ational
.cost
.
.Data.late
ncy,
.the.time.dela
y
.expe
-
rienced
.when.data.is.sent.from.one.poin
t
.to.anot
her,
.as.well.as.possi
ble
.data.corr
uption
.can.aec
t
.syst
em
.
perf
ormance.
Security
. is. a. sign
icant
. obst
acle
. to. wide
r
. deplo
yment
. of. wire
less
. tech
nology
. in. ente
rprise
. and.
indu
strial
.envi
ronments.
.e.secu
rity
.issu
es
.and.prot
ocols
.as.well.as.deplo
yment
.guid
elines
.are.pre-
s
ented
.for.wire
less
.loca
l
.area.netw
orks,
.pers
onal
.area.netw
orks,
.and.mesh.netw
orks
.that.may.conc
ern
.
indu
strial
.user
s.
e
.rela
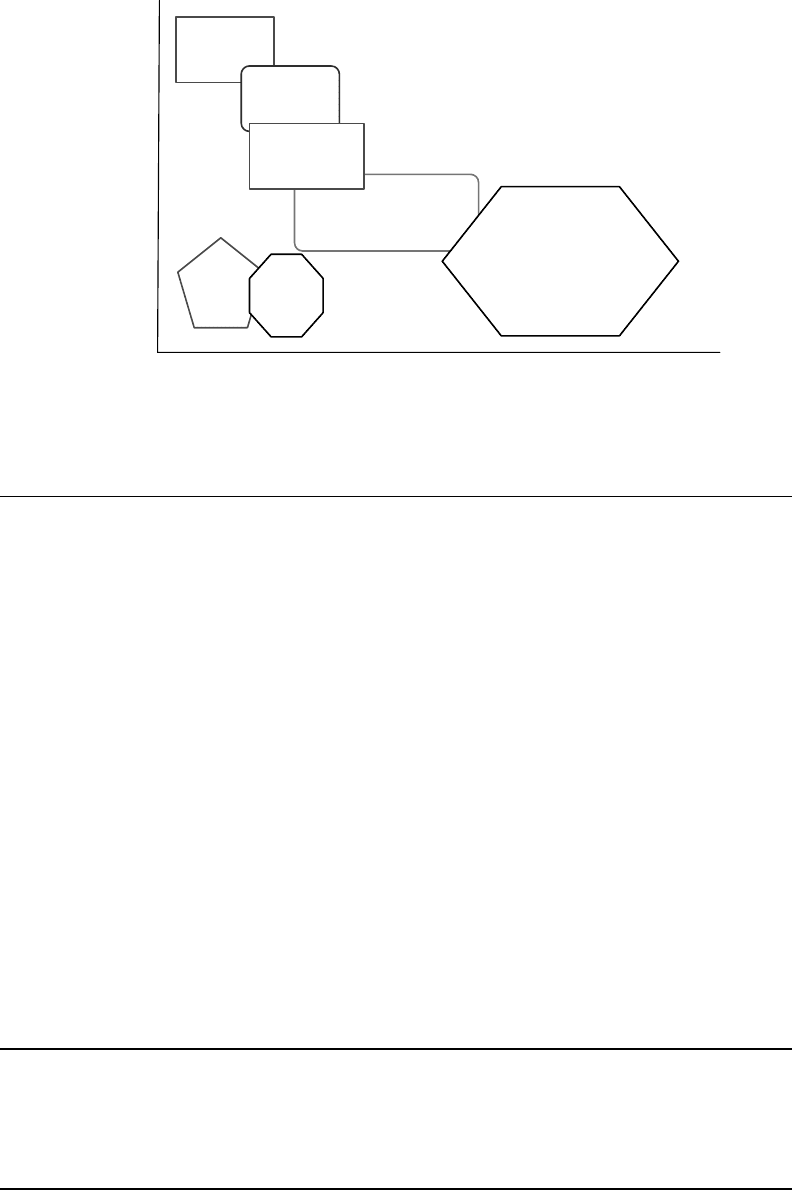
tionship
.betw
een
.vari
ous
.wire
less
.netw
orks
.in.terms.of.range.versu
s
.data.rate.(num
ber
.of.bits.
proc
essed
.per.unit.of.time
)
.is.show
n
.in.Figu
re
.28.1
.
.ose.are.wire
less
.perso
nal
.area.netw
ork
.(WPA
N),
.
wire
less
.metr
opolitan
.area.netw
ork
.(WMA
N),
.wire
less
.loca
l
.area.netw
ork
.(WLA
N),
.and.wire
less
.wide.
area.netw
ork
.(WWA
N).
.WWAN.typi
cally
.assu
me
.prot
ocols
.such.as.IEEE.802.
22
.or.wire
less
.regi
onal
.area.
netw
ork,
.whil
e
.WMAN.incl
ude
.IEEE.802.
20,
.or.mobi
le
.broa
dband
.wire
less
.acce
ss
.(MBW
A).
.ese.wire
-
less
.netw
orks
.are.in.deta
il
.spec
ied
.by.IEEE.stan
dard
.spec
ications
.[2,3
].
.e.most.ubiq
uitous
.netw
orks
.
belo
ng
.to.WPAN.tech
nologies.
.ese.are.(low
est
.to.high
est
.data.rate
)
.ZigB
ee,
.Bluet
ooth,
.and.802.
15.3
.
(hig
h
.data.rate.WPAN
).
.is.chap
ter
.pres
ents
.netw
ork
.secu
rity
.issu
es
.and.solu
tions
.of.WLAN
,
.WPAN
,
.
and.mesh.networks,.in.the.order.which.is.representative.of.their.market.size.and.their.longevity.in.the.
mark
etplace.
28
Industrial Wireless
Communications
Security (IWCS)/C42
28.1. Introduction.....................................................................................28-1
28.2
. Wirel
ess
.LAN.Sec
urity...................................................................28-2
Security.Issues/Attacks.on.WiFi. •. Security.Mechanisms. •. .
Deployment.Issues
28.3. PAN.Security....................................................................................28-6
28.4
. Summ
ary...........................................................................................28-8
References.....................................................................................................28-8
Milos Manic
University of Idaho
Idah
o
Fal
ls
Kurt Derr
Idaho National Laboratory
© 2011 by Taylor and Francis Group, LLC
28-2 Industrial Communication Systems
28.2 Wireless LaN Security
WLAN.standards.extend.the.functionality.of.a.wired.LAN.providing.location.freedom.(cable-free.net-
working).
.WLANs.are.based.on.the.IEEE.802.11.standard..e.most.widely.used.WLANs.are.in.the.
industrial,.scientic,.and.medical.(ISM).radio.band..Table.28.1.shows.the.802.11.Protocol.Family..e.
IEEE.802.11n.standard.was.nalized.in.September.2009.and.published.in.October.2009..Many.“dra.
IEEE.802.11n”.products.were.available.in.the.marketplace.prior.to.the.adoption.of.this.standard.
28.2.1 Security Issues/attacks on WiFi
e.characteristics.of.the.wireless.communications.channel.leave.WiFi.communications.open.to.attack.
(authentication,.access.control,.encryption,.jamming,.interception,.and.hijacking).[4–6]..ese.charac-
teristics
.are.discussed.further.in.this.section.
Authentication
.is.the.process.of.verifying.that.someone/something.is.authentic;.i.e.,.the.claims.they.
make.are.true..Security.protocols.are.used.to.authenticate.computers.in.possession.of.a.cryptographic.key.
and.users..Mobility.and.ease.of.connectivity.are.advantages.of.wireless.versus.wired.communications.
Access
.control.is.necessary.to.protect.against.unauthorized.use.of.wireless.communications.systems..
Several.approaches.to.controlling.access.to.a.wireless.LAN.include
. 1..Use.of.shared.keys
. 2.. Media.access.control.(MAC).address.ltering.by.a.wireless.AP
. 3..Link-layer.security.protocols
. 4.. Firewalls
. 5..Virtual.private.network.(VPN).encryption.in.order.to.provide.security
IEEE 802.22
IEEE 802.20
WiFi
IEEE 802.11
IEEE 802.15.3
IEEE 802.15.3a
IEEE 802.15.3c
WWAN
WMAN
WLAN
WPAN
0.01 0.1 1 10
Data rate (Mbps)
100 1000
Range
ZigBee
802.15.4
Bluetooth
802.15.1
WiMax
IEEE 802.16
FIGURE 28.1 Wireless.technologies:.range.versus.data.rates.
TABLE 28.1 IEEE.802.11.Standards
Standard 802.11 802.11a 802.11b 802.11g 802.11n
Year 1997 1999 1999 2003 2009
Frequency 2.4
.GHz 5.GHz 2.4.GHz 2.4.GHz 2.4.GHz,.5.GHz
Max
.Data.Rate 2.Mbps 54.Mbps 11.Mbps 54.Mbps 600.Mbps
Modulation
.Type FHSS,.DSSS,.&.IR Orthogonal.FDM DSSS Orthogonal.FDM Orthogonal.FDM
© 2011 by Taylor and Francis Group, LLC
Industrial Wireless Communications Security (IWCS)/C42 28-3
Encryption. transforms. data. from. a. readable. form. to. a. nonreadable. form. for. humans.. e. key.
length.is.an.indicator.for.the.strength.of.the.encryption.algorithm..Examples.of.encryption.algorithms.
include.RC4.(Rivest.Cypher.4),.Data.Encryption.Standard.(DES),.Triple-DES,.Blowsh,.International.
Data.Encryption.Algorithm.(IDEA),.Soware-Optimized.Encryption.Algorithm.(SEAL),.RSA.(Rivest.
Shamir.Adelman),.and.RC4..Encryption.prevents.eavesdropping.of.wirelessly.transmitted.data.
Radio
.communications.are.subject.to.jamming.regardless.of.the.form.of.wireless.signal..APs.monitor.
channel.quality.and.bit.rate.for.other.stations,.which.enables.the.detection.of.jamming..However,.unless.
APs.have.collaborative.soware.for.sharing.and.analyzing.this.information,.the.location.of.the.attacker.
cannot.be.identied.
Wireless
.signals.radiate.in.free.space.and.are.subject.to.interception..Wireless.laptop.computers.placed.
near.industrial.enterprises.can.intercept.WLAN.signals,.collect.sensitive.information,.and.potentially.
disrupt.the.network.
Hijacking
.a.wireless.channel.is.a.dicult.task.because.the.attacker.must.ensure.that.the.two.par-
ties
.cannot.communicate.with. one.another. [7]..e.two.users. must.be. out.of.wireless.range.or.be.
.
desynchronized.to.set.up.a.man.in.the.middle.(MITM).attack..In.an.MITM.attack,.the.attacker.must.
eavesdrop.on.both.users.and.impersonate.each.user.to.the.other..One.MITM.attack.approach.would.be.
to.jam.the.receiver.of.one.user.using.a.directional.antenna.while.receiving.the.transmitted.trac.from.
another.user.
28.2.2 Security Mechanisms
Security.mechanisms.and.protocols.are.necessary.to.maintain.the.secrecy.of.data.transmitted.through.
the.air.and.to.ensure.that.the.data.is.not.tampered.with..Since.the.introduction.of.802.11.WLAN,.new.
protocols.have.been.developed.as.insecurities.were.found.in.existing.deployed.protocols.(WEP,.WPA,.
WPA2,.TKIP,.CCMP,.and.WAPI)..A.survey.of.these.protocols.follows.
28.2.2.1
Wireless Encryption Protocol
e
.rst.security.mechanism.for.WiFi.is.the.wireless.encryption.protocol.(WEP),.which.requires.little.
computational.power..WEP.is.based.on.the.RC4.encryption.algorithm.and.is.not.as.sophisticated.as.the.
cryptographic.protocols.that.follow..Researchers.demonstrated.the.insecurity.of.WEP.within.the.rst.
few.years.of.its.deployment.[8].
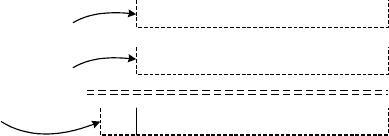
WEP
.uses.a.symmetric.secret.key.cipher,.k,.and.an.initialization.vector,.IV,.to.generate.a.keystream.
(a.pseudorandom.sequence.of.bits).as.shown.in.Figure.28.2.
e
.decryption.key.is.identical.to.the.encryption.key.in.symmetric.key.algorithms..WEP.is.not.scal-
able
.due.to.a.lack.of.automatic.key.management..e.key.is.either.64.or.128.bits..An.integrity.checksum.
is.computed.on.the.message/data.and.then.the.two.are.concatenated.to.create.a.plaintext..e.keystream.
is.mathematically.combined.(Exclusive.OR).with.the.plaintext.to.create.a.ciphertext..e.ciphertext.and.
IV.are.transmitted.between.a.sender.and.receiver..e.receiver.uses.the.identical.secret.key.to.recover.
the.message.from.the.ciphertext..RC4.was.developed.in.1987.by.Ron.Rivest.of.RSA.Security..e.process.
for.the.RC4.encryption.and.decryption.is.shown.in.Figure.28.3.
Plaintext
Ciphertext
Keystream
Plaintext XOR keystream
Message
RC4 (IV, k)
CRC|
IV
FIGURE 28.2 Encrypted.WEP.frame.
© 2011 by Taylor and Francis Group, LLC
