Wilamowski B.M., Irwin J.D. The Industrial Electronics Handbook. Second Edition: Industrial Communication Systems
Подождите немного. Документ загружается.


68-4 Industrial Communication Systems
that.are.hierarchical.as.well,.but.nevertheless.strongly.interconnected.with.each.other.(Figure.68.1)..
Obse
rving
.the.beha
vior
.with
in
.one.expe
riment
.cann
ot
.lead.to.a.comp
lete
.desc
ription
.of.the.syst
em.
.is.
is.the.wron
g
.appr
oach,
.even.if.it.look
s
.stun
ningly
.simpl
e.
.To.give.an.anal
ogy:
.biol
ogists
.do.not.expl
ain
.
owe
rs
.by.visu
al
.feat
ures
.any.more
,
.but.they.look.for.func
tional
.unit
s
.by.consi
dering
.the.owe
r
.as.a.
“pro
cess.”
.Simi
larly
.[Dav
97],
.tryi
ng
.to.desc
ribe
.mere
ly
.the.beha
vior
.of.a.comm
unication
.proto
col
.unde
r
.
die
rent
.cond
itions
.is.a.lost.caus
e,
.since.it.will.neve
r
.cove
r
.the.comp
lete
.abil
ities
.of.a.comm
unication
.
proto
col.
.But.it.is.possi
ble
.to.deve
lop
.a.func
tional
.mode
l
.of.a.proc
ess
.[HJ9
7]
.(whe
re
.we.use.the.word.
“pro
cess”
.to.refe
r
.to.both.tech
nical
.and.biol
ogical
.occu
rrences)
.and.unde
rstand
.its.beha
vior
.base
d
.on.
this.mode
l.
.If.we.want.to.buil
d
.robo
ts
.or.othe
r
.syst
ems
.that.are.inte
lligent
.in.a.more.huma
n-like
.way,.
we.have.to.get.away.from.beha
vioral
.desc
ription
.and.empl
oy
.func
tional
.deve
lopment
.inst
ead.
.Whil
e
.
this.is.well.unde
rstood
.in.comp
uter
.and.comm
unications
.engi
neering,
.some.psyc
hological
.scho
ols
.like.
beha
viorists
.hav
e
.a.sli
ghtly
.di
erent
.vie
w
.of.the.mat
ter.
68.4 automated Methods for Sensor and actuator Systems
Today’s.building.sensor.and.control.systems.are.primarily.based.upon.the.processing.of.sensor.informa-
tion
.usin
g
.prede
ned
.rule
s.
.e.user.or.oper
ator
.den
es,
.e.g.,.the.rang
e
.of.valid.temp
eratures
.for.a.room.
by.a.rule
—when
.the.temp
erature
.value.in.that.room.is.out.of.rang
e
.(e.g..caused.by.a.defec
t),
.the.syst
em
.
reac
ts
.(e.g.
,
.with.an.erro
r
.mess
age).
.More.comp
licated
.diag
nostics
.requ
ire
.an.expe
rienced
.oper
ator
.who.
can.obser
ve
.and.inte
rpret
.real
-time
.sensor.value
s.
.Howe
ver,
.as.syst
ems
.becom
e
.larg
er,
.are.depl
oyed
.in.a.
wide
r
.varie
ty
.of.envi
ronments,
.and.are.targ
eted
.at.techn
ically
.less
-sophisticated
.users
,
.both.poss
ibilities
.
(rul
e-based
.syst
ems
.and.expe
rt
.users
)
.becom
e
.prob
lematic.
.e.cont
rol
.syst
em
.woul
d
.requ
ire
.comp
rehen-
sive
.prio
r
.know
ledge
.of.poss
ible
.oper
ating
.cond
itions,
.rang
es
.of.value
s
.and.erro
r
.cond
itions.
.is.know
l-
edge
.may.not.be.read
ily
.avail
able,
.and.will.be.dic
ult
.for.an.unsop
histicated
.user.to.inpu
t.
.It.is.impr
actical
.
for.expe
rienced
.oper
ators
.to.direc
tly
.obser
ve
.larg
e
.syst
ems,
.and.naiv
e
.users.can.not.inte
rpret
.sensor.value
s.
A
.solu
tion
.to.this.prob
lem
.is.to.autom
atically
.reco
gnize
.erro
r
.cond
itions
.spec
ic
.to.a.give
n
.sens
or
.
[HLS
99],
.actu
ator,
.or.syst
em
.with
out
.the.need.of.prep
rogrammed
.erro
r
.cond
itions,
.user
-entered
.para
m-
eters,
.or.expe
rienced
.oper
ators.
.e.syst
em
.shou
ld
.obse
rve
.sens
or
.and.actu
ator
.data.over.time.[JGJ
S99],
.
cons
truct
.a.mode
l
.of.“nor
mality”
.[PL0
3],
.and.issu
e
.erro
r
.aler
ts
.when.sens
or
.or.actu
ator
.valu
es
.vary.from.
norm
al.
.e.resu
lt
.woul
d
.be.a.syst
em
.that.can.reco
gnize
.sens
or
.erro
rs
.or.abno
rmal
.sens
or
.or.actu
ator
.
read
ings,
.with.mini
mal
.manu
al
.con
guration
.of.the.syst
em
.[SH0
3].
.Furt
her,
.if.sens
or
.read
ings
.vary.or.
dri.over.time
,
.the.syst
em
.coul
d
.autom
atically
.adapt.itse
lf
.to.the.new.“nor
mal”
.cond
itions,
.adju
sting
.its.
erro
r
.cri
teria
.acc
ordingly.
68.5 the Diagnostic System
For.illustration,.a.diagnostic.system.utilizing.statistical.methods.(BASE.[SBR05]).is.compared.to.a.stan-
dard
.buil
ding
.auto
mation
.syst
em
.(BAS
).
.e.BAS.cons
ists
.of.a.numb
er
.of.sensor
s
.and.actu
ators
.conn
ected
.
by.the.LonW
orks
.eld
bus
.(LON
)
.[LDS
01].
.It.oer
s
.a.visu
al
.inte
rface
.usin
g
.a.mana
gement
.info
rmation
.
base.(MIB
)
.for.retr
ieving
.and.mani
pulating
.syst
em
.para
meters
.and.for.the.visu
alization
.of.syst
em
.mal-
f
unctions.
.e.diag
nostic
.syst
em
.BASE.is.based.on.stat
istical
.“gen
erative”
.mode
ls
.(SGMs
).
.e.goal.of.the.
syst
em
.is.to.auto
matically
.detec
t
.sensor.erro
rs
.in.a.runn
ing
.auto
mation
.syst
em
.[SBR
05,FS94].
.It.does.so.
by.obser
ving
.the.data.owi
ng
.thro
ugh
.the.syst
em
.and.thus.lear
ns
.abou
t
.the.beha
vior
.of.the.auto
mation
.
syst
em.
.e.diag
nostic
.syst
em
.buil
ds
.a.mode
l
.of.the.sensor.data.in.the.unde
rlying
.auto
mation
.syst
em,
.
based.on.the.data.ow..From.the.opti
mized
.mode
l,
.the.diag
nostic
.syst
em
.can.iden
tify
.abno
rmal
.sensor.
and.actu
ator
.value
s.
.e.diag
nostic
.syst
em
.can.eith
er
.anal
yze
.hist
orical
.data
,
.or.direc
tly
.acces
s
.live.data
.
We
.use.a.set.of.stat
istical
.gene
rative
.mode
ls
.to.repr
esent
.know
ledge
.abou
t
.the.autom
ation
.syst
em.
.
A.stat
istical
.gene
rative
.mode
l
.take
s
.inpu
ts
.like.a.sens
or
.valu
e,
.a.stat
us
.indi
cator,
.time.of.day,.etc.,.and.
retu
rns
.a.pro
bability
.bet
ween
.zer
o
.and.one
.
© 2011 by Taylor and Francis Group, LLC

Processing Data in Complex Communication Systems 68-5
Using.SGMs.has.several.advantages..First,.because.the.model.encodes.the.probability.of.a.sensor.
valu
e,
.it.prov
ides
.a.quan
titative
.meas
ure
.of.“nor
mality,”
.whic
h
.can.be.moni
tored
.to.dete
ct
.abno
rmal
.
even
ts.
.Seco
nd,
.the.mode
l
.can.be.quer
ied
.as.to.what.the.“nor
mal”
.stat
e
.of.the.syst
em
.woul
d
.be,.give
n
.
an.arbi
trary
.subs
et
.of.sens
or
.read
ings.
.In.othe
r
.word
s,
.the.mode
l
.can.“ll.in”.or.pred
ict
.sens
or
.valu
es,
.
whic
h
.can.help.to.iden
tify
.the.sour
ce
.of.abno
rmal
.syst
em
.beha
vior.
.ird
,
.the.mode
l
.can.cont
inuously
.
be.upd
ated
.to.ada
pt
.to.sen
sor
.dri
.
68.5.1 Error Detection
Given.an.SGM,.implementation.of.this.functionality.is.straightforward..e.system.assigns.a.probabil-
ity
.to.each.newl
y
.obse
rved
.data.valu
e.
.When.this.prob
ability
.is.high
,
.the.syst
em
.retu
rns
.that.the.new.
data.value.is.a.“nor
mal”
.value..When.the.prob
ability
.fall
s
.belo
w
.a.speci
c
.thre
shold,
.the.syst
em
.rate
s
.the.
valu
e
.as.“abn
ormal.”
.e.SGM.syst
em
.gene
rates
.alar
m
.even
ts
.when.it.obse
rves
.abno
rmal
.sens
or
.valu
es.
.
is.leav
es
.open.the.ques
tion
.of.how.to.assig
n
.the.thre
shold
.for.norm
ality.
.In.prac
tice,
.the.user.sets.the.
thre
shold
.using.a.grap
hical
.inte
rface.
.Init
ially,
.befo
re
.the.syst
em
.has.lear
ned
.norm
al
.syst
em
.beha
vior,
.
many.alar
ms
.are.gene
rated,
.and.the.user.may.deci
de
.to.set.the.thre
shold
.to.a.valu
e
.near.zero
.
.As.the.
syst
em
.acqu
ires
.a.bett
er
.mode
l
.of.the.sens
or
.syst
em,
.the.thre
shold
.can.be.rais
ed.
.In.any.case
,
.the.thre
sh-
old
.para
meter
.tell
s
.us.how.impr
obable
.an.even
t
.shou
ld
.be.to.rais
e
.an.alar
m.
.e.syst
em
.can.also.use.a.
log-
probability
.sca
le,
.so.tha
t
.the.thr
eshold
.can.easi
ly
.be.set.to.onl
y
.reg
ister
.ext
remely
.unl
ikely
.eve
nts.
68.5.2 Statistical Generative Models
e.BASE.system.implements.a.number.of.SGMs.(see.Table.68.1).
e
.more.comp
lex
.mode
ls
.add.addi
tional
.capa
bilities,
.or.rela
x
.assu
mptions
.in.comp
arison
.to.a.simpl
e
.
Gaus
sian
.mod
el
.[GL
S+00].
Histogram:
.is.is.a.very.gene
ral
.mode
l
.that.is.appr
opriate
.for.disc
rete
.sens
or
.valu
es,
.as.well.as.real
-
valued
.sens
ors
.with.an.arbi
trary
.numbe
r
.of.mode
s.
.One.draw
back
.is.that.a.histo
gram
.requ
ires
.a.rath
er
.
larg
e
.qua
ntity
.of.dat
a
.bef
ore
.it.bec
omes
.usa
ble
.or.acc
urate.
Mixture of Gaussians:
.is.mode
l
.rela
xes
.the.Gaus
sian
.assu
mption
.that.the.dist
ribution
.has.only.one.
mode
.
.A.mixt
ure
.of.Gaus
sians
.is.comp
osed
.of.a.numbe
r
.of.Gaus
sian
.mode
ls,
.and.each.data.valu
e
.is.
attr
ibuted
.to.the.Gau
ssian
.mod
es
.wit
h
.a.wei
ghting
.giv
en
.by.a.“po
sterior
.pro
bability.”
.See
,
.e.g
.,
.[Bi
s95].
Hidden Markov Model:
.is.mode
l
.is.the.equi
valent
.of.the.mixtu
re
.of.Gaus
sians
.mode
l
.or.the.histo
gram
.
mode
l,
.but.with.the.addi
tion
.that.the.curr
ent
.sens
or
.valu
e
.can.be.depe
ndent
.on.prev
ious
.valu
es
.[RJ8
6,Sal00].
e
.diag
nostic
.syst
em
.uses.SGMs.of.autom
ation
.data.poin
ts.
.For.any.give
n
.data.valu
e
.x,.mode
l
.M.
assig
ns
.a.pro
bability
.to.x: P
M
(x)→[0,1].
Note
.that.for.disc
rete
.dist
ributions
.such.as.a.hist
ogram,
.the.valu
e
.assi
gned
.to.x.by.the.mode
l
.P
M
(x).
is.a.well
-dened
.proba
bility,
.sinc
e
.the.set.of.poss
ible
.assi
gnments
.to. x. is. nit
e.
.For.a.proba
bility
.
dens
ity,
.such.as.a.Gaus
sian
.or.mixt
ure
.of.Gaus
sians,
.the.proba
bility
.valu
e
.assi
gned
.to.x.by.the.mode
l
.
is.the.proba
bility
.dens
ity
.at.that.valu
e.
.In.orde
r
.to.conv
ert
.this.dens
ity
.to.a.proba
bility,
.the.prob-
a
bility
.of.gene
rating
.a
.
valu
e
.with
in
.a.neig
hborhood
.±δ.arou
nd
.x.is.comp
uted
.as.
P x d
M
( )+
−
∫
φ φ
δ
δ
,.and.
TABLE 68.1 Statistical.Generative.Models
Model Variable.Type Parameters
Gaussian Real
μ,
.σ
2
Histogram Discrete,.Real Bin.counts
Mixture
.of.Gaus
sians Real
µ σ π
i i i
, ,
2
Hidden.Markov.model Real
T
ij i i
µ σ,
2
Hidden.Markov.model Discrete T
ij
,.Bin.counts
© 2011 by Taylor and Francis Group, LLC
68-6 Industrial Communication Systems
approximated.as.2δP
M
(x)
.
for.small.δ..Alternatively,.the.probability.under.the.model.of.equaling.or.
exc
eeding
.the.obs
erved
.val
ue
.can.be.com
puted:
.
P x x P x d
M M
′
≥
( )
= +
∞
∫
( φ) φ
0
.
(68
.1)
e
.dat
a
.x.can.be.a.sen
sor
.rea
ding
.suc
h
.as.an.air.pre
ssure
.sen
sor,
.con
tact
.sen
sor,
.tem
perature
.sen
sor,
.
and.so.on..Giv
en
.a.new.dat
a
.val
ue,
.the.sys
tem
.assi
gns
.a.pro
bability
.to.thi
s
.val
ue.
.Whe
n
.the.pro
bability
.
is.ab
ove
.a.gi
ven
.th
reshold,
.th
e
.sy
stem
.co
ncludes
.th
at
.th
is
.da
ta
.va
lue
.is.“n
ormal.”
Given
.a.seq
uence
.of.sen
sor
.rea
dings
.x.=.{x
1
,.….,x
T
}.from.times.1.to.T,.the.system.must.create.a.model.
of.“no
rmal”
.sen
sor
.rea
dings.
.e.sys
tem
.use
s
.an.onl
ine
.ver
sion
.of.the.exp
ectation
.max
imization
.alg
o-
rithm
.for.max
imum-likelihood
.par
ameter
.est
imation.
.Giv
en
.a.mod
el
.M.wit
h
.par
ameters
.θ,.the.log
-
likelihood
.of.th
e
.mo
del
.pa
rameters
.gi
ven
.th
e
.da
ta
.x.is.gi
ven
.by
:
.
L P x
M
( ) log ( | )θ θ=
.
(68.2)
where
.the. not
ation
.P(x|θ). den
otes
. the.con
ditional
.prob
ability
.of.x.giv
en
. the.cur
rent
. val
ues
.of. the.
par
ameters
.θ.
e
.max
imum-likelihood
.par
ameters
.are.de
ned
.as.the.par
ameter
.val
ues
.tha
t
.max
imize
.the.log
-
likelihood
.ov
er
.th
e
.ob
served
.da
ta:
.
θ θ
θ
ML M
P x=
{ }
arg max log ( | )
.
(68
.3)
68.5.3 Online Parameter Updates
In.order.for.the.system.to.continually.adapt.the.model.parameters,.the.parameter.update.algorithm.
mus
t
. inc
rementally
. cha
nge
. the. par
ameters
. bas
ed
. on. new
ly
. obs
erved
. sen
sor
. val
ues.
. Suc
h
. “on
line”
.
upd
ates
.hav
e
.the.adv
antage
.tha
t
.the
re
.is.no.tim
e
.dur
ing
.whi
ch
.the.sys
tem
.is.in.an.“opt
imization”
.pha
se,
.
and.un
available
.fo
r
.di
agnostics
.[K
al60].
For
.the.tes
ts
.des
cribed
.her
e
.we.use
d
.mix
ture
.of.Gau
ssians
.mod
els.
.For.the
se
.mod
els,
.the.BAS
E
.sys
tem
.
use
s
.a.simp
le
.stoc
hastic
.est
imation
.met
hod,
.bas
ed
.on.an.exp
ectation–maximization
.alg
orithm
.[NH
98].
.
As.eac
h
.new.dat
a
.val
ue
.x
i
.is.observed,.the.parameters.are.adjusted.in.a.two-step.process..First,.the.poste-
rior
.pro
bability
.of.eac
h
.ele
ment
.of.the.mix
ture
.giv
en
.the.dat
a
.val
ue
.is.com
puted.
.Sec
ond,
.the.par
ameters
.
are.adj
usted
.so.as.to.inc
rease
.the.exp
ected
.join
t
.log
-probability
.of.the.dat
a
.and.the.Gau
ssian
.mix
ture
.
com
ponent.
.Se
e
.Se
ction
.2.
6
.of.[B
is95]
.fo
r
.de
tails.
68.5.4 results
e.model.log-likelihood,.given.by.Equation.68.1,.is.a.measure.of.model.quality..As.the.parameter.val-
ues
.are.opt
imized
.onli
ne,
.the.log
-likelihood
.of.the.sen
sor
.mod
els
.incr
eases.
.e.log
-likelihood
.doe
s
.
not.cons
istently
.incr
ease,
.how
ever,
.due.to.the.onli
ne
.tt
ing
.of.par
ameters,
.whi
ch
.hap
pens
.sim
ultane-
ously
.wit
h
.rep
orting
.of.abno
rmal
.sen
sor
.val
ues.
.If.sen
sors
.rec
eive
.abno
rmal
.val
ues,
.the.log
-likelihood
.
dec
reases,
.unt
il
.the.val
ues
.ret
urn
.to.the
ir
.nor
mal
.ran
ge
.or.the.sen
sor
.mod
el
.ada
pts
.to.the.new.ran
ge
.
of.val
ues.
.Figu
re
.68.
2
.sho
ws
.an.exa
mple
.fro
m
.a.sin
gle
.sen
sor.
.e.upp
er
.gu
re
.sho
ws
.the.sen
sor
.val
ue;
.
the.low
er
.gu
re
.sho
ws
.the.cor
responding
.log
-likelihood
.as.a.func
tion
.of.tim
e.
.e.lar
ge
.dis
turbance
.
in.the.cen
ter
.(a.pow
er
.uct
uation)
.reg
isters
.an.ala
rm,
.jus
t
.lik
e
.the.two.sma
ll
.“sp
ikes”
.nea
r
.the.end.of.
the.gra
ph.
© 2011 by Taylor and Francis Group, LLC

Processing Data in Complex Communication Systems 68-7
68.6 Intelligent Surveillance Systems
Today,.surveillance.has.become.a.relevant.means.for.protecting.public.and.industrial.areas.against.
malicious.subjects.like.burglars.or.vandals..For.both.keeping.privacy.of.irreproachable.citizens.as.well.
as.enabling.automated.detection.of.potential.threats,.computer-based.systems.are.needed.that.support.
human.operators.in.recognizing.unusual.situations..A.suitable.approach.for.that.purpose.is.to.utilize.
a.hierarchical.architecture.of.semantic.processing.layers.distributed.in.a.network.of.nodes..e.goal.of.
these.layers.is.to.learn.the.“normality”.in.the.environment.of.the.network,.in.order.to.detect.unusual.
situations.and.to.inform.the.human.operator.in.such.cases..e.SENSE.project.[WSe06,BKV+08].imple-
ments
.such.an.architecture..erefore,.we.will.briey.cover.it.here.as.an.example.of.how.hierarchical.
semantic.processing.can.be.used.for.surveillance.systems.
SENSE
.consists.of.a.network.of.communicating.sensor.nodes,.each.equipped.with.a.camera.and.a.
microphone.array..ese.sensor.modalities.observe.their.environment.and.deliver.streams.of.mono-modal.
events.to.a.reasoning.unit,.which.derives.fused.high-level.observations.from.this.information..ese.
observations.are.exchanged.with.neighbor.nodes.in.order.to.establish.a.global.view.about.the.commonly.
observed.environment..Detected.potential.threats.are.nally.reported.to.the.person(s).in.charge.
ough
.most.of.the.methods.used.in.the.particular.layers.are.widely.used.in.many.applications,.the.
benet.lies.in.the.combination.of.them.in.order.to.let.the.messages.of.the.system.really.appear.meaning-
ful
.to.the.user.
68.6.1 architecture
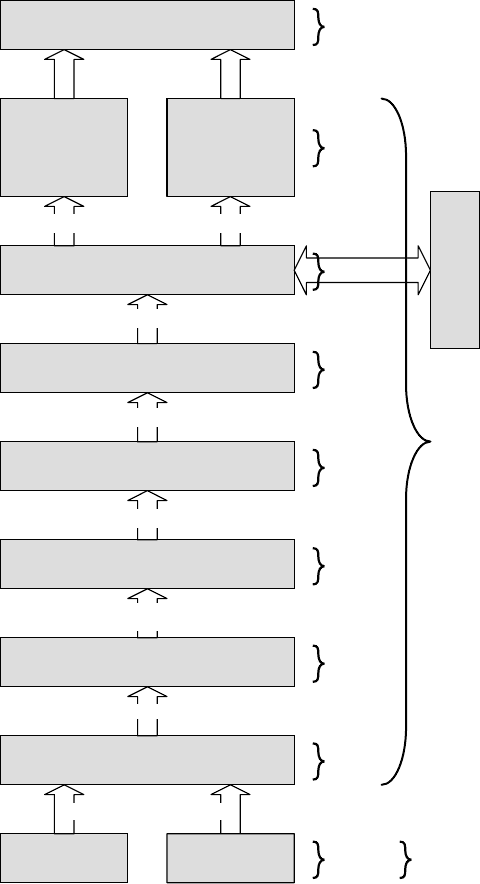
In.this.case,.an.eight-layer.data.processing.architecture.is.adopted,.in.which.the.lower.layers.are.responsible.
for.a.stable.and.comprehensive.world.representation.to.be.evaluated.in.the.higher.layers.(Figure.68.3).
First,
.the.visual.low-level.feature.extraction.(layer.0).processes.frame.by.frame.from.the.camera.in.
2D.camera.coordinates.and.extracts.predened.visual.objects..At.the.same.time,.the.audio.low-level.
extraction.scans.the.acoustic.signals.from.a.linear.eight-microphone.array.for.trained.sound.patterns.of.
predened.categories..Due.to.limited.processing.capabilities,.this.layer.can.deliver.signicantly.unstable.
data.in.both.modalities..In.case.of.unfortunate.conditions.for.the.camera,.detected.symbols.can.change.
their.label.from.one.category.to.another.and.back.for.the.same.physical.object.within.consecutive.frames..
e.size.of.detected.symbols.can.change.from.small.elements.to.large.ones.covering.tens.of.square.
70
60
50
40
30
20
5
0
–5
Log-likelihood Sensor values
FIGURE 68.2 Sensor.value.and.log-likelihood.for.a.single.sensor.from.the.system..Unusual.sensor.values.register.
as.drops.in.the.log-likelihood,.causing.alarms.
© 2011 by Taylor and Francis Group, LLC
68-8 Industrial Communication Systems
meters.and.including.previously.detected.and.other.objects..Consequently,.the.challenge.for.higher.
levels.is.to.lter.out.signicant.information.from.very.noisy.data.
e
.modality.events.of.layer.0.(low-level.symbols.in.Figure.68.3).are.checked.at.layer.1.for.plausibility—
e.g.,
.the.audio.symbols.with.respect.to.position.and.intensity,.the.video.symbols.with.respect.to.position.and.
size..In.the.second.layer,.symbols.that.pass.the.rst.spatial.check.are.subdued.to.a.further.check,.regarding.
their.temporal.behavior..e.output.of.this.layer.is.a.more.stable.and.comprehensive.world.representation.
including.unimodal.symbols..Layer.3.is.responsible.for.sensor.fusion.[BLS06].the.unimodal.symbols.are.
fused.here.to.form.multi-modal.symbols.
Layer
.4.is.the.parameter.inference.machine.in.which.probabilistic.models.for.symbol.parameters.and.
events.are.optimized..e.results.of.this.layer.are.models.of.high-level.symbols.(HLSs).and.features.that.
User notication lter
Detected alarms and
unusual behavior
Trajectories
Sensor fusion (audio, video)
Audio Video
Inter-node communication
Parameter inference
Tracking of LLSS
Pre-processing of LLSS
Predened
alarm
recognition
Unusual
behavior
recognition
Layer 8
Layer 7
Layer 6
Neighbor node
High-level layers
semantic processing
Layer 5
Layer 4
Layer 3
Layer 2
Layer 1
Layer 0
Low-level
layer
What does the node belief at time t
Audio and video object
instances at time t
High-level symbol (HLS) instances
HLS and feature models
Local trajectories map
Local and neighbors knowledge
Low-level symbols (LLS)
FIGURE 68.3 High.level.semantic.processing.soware.architecture.
© 2011 by Taylor and Francis Group, LLC

Processing Data in Complex Communication Systems 68-9
describe.their.behavior..In.layer.5,.the.system.learns.about.trajectories.of.symbols..Typical.paths.through.
the.view.of.a.sens
or
.node.are.store
d.
.Laye
r
.6.mana
ges
.the.comm
unication
.to.othe
r
.node
s
.and.esta
blishes
.
a.glob
al
.worl
d
.view
.
.e.traje
ctories
.are.also.used.to.corr
elate
.obse
rvations
.betw
een
.neig
hboring
.node
s.
.
In.laye
r
.7,.the.reco
gnition
.of.unus
ual
.beha
vior
.and.even
ts
.take
s
.plac
e
.using.two.appr
oaches:
.the.rst.one.
comp
ares
.curr
ent
.obse
rvations
.with.lear
ned
.mode
ls
.by.calc
ulating
.prob
abilities
.of.occu
rrence
.of.the.
obse
rvations
.with.resp
ect
.to.thei
r
.posit
ion,
.velo
city,
.and.dire
ction.
.It.also.calc
ulates
.the.prob
abilities
.of.
the.dura
tion
.that.symbo
ls
.rema
in
.in.an.area
,
.prob
abilities
.of.the.move
ment
.alon
g
.traje
ctories,
.incl
ud-
ing
.traje
ctories
.acro
ss
.node
s.
.Obse
rvations
.with.prob
abilities
.belo
w
.den
ed
.thre
sholds
.rais
e
.“unu
sual
.
beha
vior”
.alar
ms.
.e.seco
nd
.part.of.this.laye
r
.is.conc
erned
.with.the.reco
gnition
.of.pred
ened
.scen
ar-
ios
.and.the.crea
tion
.of.alar
ms
.in.case.pred
ened
.thre
at
.cond
itions
.are.met..Fina
lly,
.laye
r
.8.is.resp
onsible
.
for.the.comm
unication
.to.the.user
.
.It.gene
rates
.alar
m
.or.stat
us
.mess
ages
.and.lte
rs
.them.if.part
icular
.
cond
itions
.wou
ld
.be.ann
ounced
.too.oe
n
.or.the.sam
e
.eve
nt
.is.rec
ognized
.by.bot
h
.met
hods
.in.lay
er
.7.
68.7 the Human Mind as an archetype
for Cognitive
autom
ation
A.long-awaited.breakthrough.in.technology.is.the.ability.of.machines.to.operate.in.an.everyday.human.
envi
ronment.
.Bein
g
.able.to.sens
e
.the.worl
d
.in.whic
h
.they.are.imme
rsed,
.robo
ts
.may.act.in.a.way.that.is.
usef
ul
.for.huma
n
.user
s.
.Deca
des
.ago,.autom
ation
.syst
em
.desig
ners
.star
ted
.to.foll
ow
.the.path.that.lite
ra-
ture
.had.dra
ed:
.int
elligence
.and.per
ception
.go.han
d
.in.han
d.
us,
.very.simp
le
.devi
ces
.can.only.carr
y
.out.task
s
.that.do.not.requ
ire
.sens
ing
.the.real.worl
d.
.For.inst
ance,
.
movi
ng
.a.certa
in
.piece.5.cm.ahea
d
.in.the.conv
eyor
.belt
.
.In.a.way,.this.is.like.driv
ing
.blin
d
.a.car:.if.the.piece.
falls.o.the.belt
,
.the.devi
ce
.won’
t
.know.the.reas
on
.and,.ther
efore,
.won’
t
.be.able.to.nd.a.prop
er
.answe
r.
Obviously,
.more.comp
lex
.acti
vities
.dema
nd
.more.comp
lex
.devi
ces
.and,.in.such.case
s,
.soph
isticated
.
perc
eption
.is.the.turn
ing
.poin
t
.that.allo
ws
.autom
ation
.syst
ems
.to.coll
ect
.the.info
rmation
.need
ed
.to.
cont
rol
.the
ir
.act
ions
.and.the.con
sequences
.of.the
m.
In
.the.foll
owing
.sect
ion,
.we.will.give.an.over
view
.on.how.mach
ine
.perc
eption
.has.been.addr
essed
.in.
the.past
,
.and.what.are.prom
ising
.appr
oaches
.for.perc
eption
.in.futu
re
.autom
ation
.syst
ems
.in.orde
r
.to.be.
able.to.ful
ll
.use
ful
.tas
ks
.in.mor
e
.gen
eral
.env
ironments—as
.hum
ans
.can
.
68.7.1 Perception in automation: a Historic Overview
e.term.perception.has.been.used.in.computer.and.automation.systems.from.the.1950s.onwards,.since.
the.foun
dation
.of.AI..It.mean
s
.acqu
iring,
.inte
rpreting,
.sele
cting,
.and.orga
nizing
.sens
ory
.info
rmation.
.
e.topic.itse
lf
.was.not.new.to.autom
ation,
.but.has.gain
ed
.a.new.qual
ity
.from.the.mome
nt
.info
rmation
.
proc
essing
.cou
ld
.be.sep
arated
.fro
m
.ene
rgy
.ow.and.per
formed
.in.com
pletely
.new.way
s.
e
.fore
seen
.time
frame
.for.revo
lutionary,
.huma
n-like
.appl
ications
.in.AI.(some
times
.refe
rred
.to.as.arti
-
cial
.gene
ral
.inte
lligences)
.has.been.esti
mated
.to.be.roug
hly
.10.year
s—for
.these.last.60.year
s.
.Alre
ady
.in.
earl
y
.phase
s
.of.resea
rch,
.engi
neers,
.psyc
hologists,
.and.neur
opsychiatrists
.coop
erated
.in.orde
r
.to.expl
oit
.
syne
rgies
.and.achi
eve
.mutu
ally
.frui
tful
.resu
lts.
.Unfo
rtunately,
.it.soon.turn
ed
.out.that.loose.coup
lings
.
betw
een
.scie
ntists
.from.die
rent
.eld
s
.woul
d
.not.be.enou
gh
.to.nd.comp
rehensive
.solu
tions.
.In.1961
,
.
E.E..Davi
d
.wrot
e
.in.his.intr
oductory
.word
s
.for.an.issu
e
.of.the.Tran
sactions on Information eory
.[Dav
61]:
Not
.to. say. that.cros
s-fertilization
.of. engi
neering
.and. the.life
-sciences
. shou
ld
.be.scor
ned.
. But.
ther
e
.must.be.more.to.thes
e
.atte
mpts
.than.mere
ly
.conc
octing
.a.name
,
.gene
rating
.well
-intentioned
.
enthusiasm,.speculating.with.the.aid.of.brain-computer.analogies,.and.holding.symposia.packed.
with.“pre
liminary”
.resu
lts
.from.inco
nclusive
.expe
riments.
.A.bona.de.“int
erdiscipline”
.draw
s
.its.
vita
lity
.from.peop
le
.of.demo
nstrated
.achi
evement
.in.the.cont
ributing
.disc
iplines,
.not.from.thos
e
.
who.mer
ely
.app
ly
.ter
minology
.of.one.el
d
.to.ano
ther.
© 2011 by Taylor and Francis Group, LLC

68-10 Industrial Communication Systems
e.authors.of.this.text.fully.agree.with.this.statement..It.is.of.great.importance.to.form.teams.with.
memb
ers
.fro
m
.bot
h
.sci
ences
.wor
king
.toge
ther
.on.a.dai
ly
.basi
s
.rat
her
.tha
n
.mee
ting
.reg
ularly
.pre
sent-
ing
.own.the
ories
.abo
ut
.the.oth
er’s
.pro
fession.
.An.ind
ication
.tha
t
.Dav
id’s
.sta
tement
.sti
ll
.rem
ains
.tru
e
.in.
man
y
.ar
eas
.is.th
at
.th
ere
.ar
e
.st
ill
.no.ex
amples
.of.hu
man-like
.in
telligence
.in.au
tomation.
e
.dev
elopment
.in.mac
hine
.per
ception
.has.tak
en
.two.way
s:
.one.rel
ated
.wit
h
.ind
ustrial
.pro
cess
.
con
trol,
.whe
re
.mac
hines
.are.des
igned
.and.bui
lt
.in.ord
er
.to.inc
rease
.pro
ductivity,
.red
uce
.cos
ts,
.as.wel
l
.
as.enh
ance
.qua
lity
.and.ex
ibility
.in.the.pro
duction
.pro
cess.
.es
e
.mac
hines
.mos
tly
.nee
d
.to.per
ceive
.
a.wel
l-known
.env
ironment
.and.the
refore
.con
sist
.of.a.sel
ected
.num
ber
.of.ded
icated
.sen
sors.
.e.sum.
of.sen
sor
.vie
ws
.com
poses
.the.mac
hines’
.vie
w
.of.the.wor
ld.
.Num
erous
.pub
lications
.hav
e
.bee
n
.wri
tten,
.
whi
ch
.exp
lain
.mat
hematical
.way
s
.to.cop
e
.wit
h
.sen
sor
.dat
a
.to.ful
ll
.the.nee
ds
.of.aut
omation
.in.the
se
.
res
pects
.[Is
e84].
e
.sec
ond
.dev
elopment
.pat
h
.was.and.is.con
cerned
.wit
h
.the.per
ception
.of.hum
ans
.[VL
S+08]
.and.
hum
an
.act
ivities,
.on.the.one.han
d,
.and.wit
h
.imp
lementing
.per
ception
.sys
tems
.imi
tating
.hum
an
.per
-
ception
.for.bro
ader
.app
lication
.are
as,
.on.the.oth
er.
.Inv
olved
.res
earch
.el
ds
.are
,
.amo
ng
.oth
ers,
.cog
nitive
.
sci
ences,
.AI,.ima
ge
.pro
cessing,
.aud
io
.dat
a
.pro
cessing,
.nat
ural
.lan
guage
.pro
cessing,
.use
r
.int
erfaces,
.and.
hum
an
.ma
chine
.in
terfaces.
Although
.the.goa
l
.of.per
ception
.sys
tems
.alw
ays
.was.to.cre
ate
.hum
an-like
.per
ception
.inc
luding
.all.
sen
sory
.mod
alities
.of.hum
ans
.[KB
S01],
.fro
m
.the.ear
ly
.beg
inning
.of.com
puter
.sci
ence
.unt
il
.now
,
.the.
use
r
.int
erface—the
.fro
nt
.end.of.the.com
puter,
.thr
ough
.whi
ch
.com
puters
.can.“pe
rceive”
.hum
ans—nor-
mally
.does.not.oer.very.human-like.communication.channels..User.interfaces.up.to.now,.including.
toda
y’s
.so-
called
.tan
gible
.int
erfaces
.are.sti
ll
.uni
ntuitive
.(ba
tch
.int
erfaces
.in.the.196
0s,
.com
mand-line
.
int
erfaces
.in.th
e
.19
70s,
.gr
aphical
.us
er
.in
terfaces
.fr
om
.th
e
.19
80s
.un
til
.tod
ay*).
e
.res
earch
.el
d
.con
cerned
.wit
h
.per
ceiving
.inf
ormation
.abo
ut
.hum
an
.use
rs
.is.cal
led
.con
text
.awa
re
.
sys
tems.
.Con
text-aware
.sys
tems
.are.use
d
.to.bui
ld
.dev
ices
.in.the.el
ds
.of.int
elligent
.env
ironments
.or.
ubi
quitous
.com
puting.
.e.com
mon
.vie
w
.in.the
se
.com
munities
.is.tha
t
.com
puters
.wil
l
.not.onl
y
.bec
ome
.
che
aper,
.sma
ller,
.and.mor
e
.pow
erful;
.the
y
.wil
l
.als
o
.mor
e
.or.les
s
.dis
appear
.and.hid
e
.by.bec
oming
.int
e-
grated
.in.nor
mal,
.eve
ryday
.obje
cts
.[Ha
i06,Mat04].
.Tec
hnology
.wil
l
.dis
solve
.embe
dded
.into.our.sur
-
roundings.
.Sma
rt
.obje
cts
.wil
l
.com
municate,
.coo
perate,
.and.vir
tually
.ama
lgamate
.wit
hout
.exp
licit
.use
r
.
int
eraction
.or.com
mands
.to.for
m
.con
sortia
.in.ord
er
.to.oe
r
.or.eve
n
.ful
ll
.tas
ks
.on.beh
alf
.of.a.use
r.
.
ey.wil
l
.be.cap
able
.of.not.onl
y
.sen
sing
.val
ues,
.but.als
o
.of.der
iving
.con
text
.inf
ormation
.abo
ut
.the.rea
-
sons,
.int
entions,
.desi
res,
.and.bel
iefs
.of.the.use
r.
.is.inf
ormation
.may.be.sha
red
.ove
r
.net
works
.lik
e
.the.
Int
ernet
.and.use
d
.to.com
pare
.and.cla
ssify
.act
ivities,
.nd.con
nections
.to.oth
er
.peo
ple
.and
/or
.dev
ices,
.
loo
k
.up.se
mantic
.da
tabases,
.an
d
.mu
ch
.mo
re.
One
.of.the.key.iss
ues
.in.con
temporary
.res
earch
.towa
rd
.thi
s
.visi
on
.is.sce
nario
.rec
ognition
.[GJ
07].
.
Sce
nario
.rec
ognition
.tri
es
.to.nd.seq
uences
.of.par
ticular
.beh
aviors
.in.tim
e,
.and.gro
ups
.it.in.a.way.
hum
ans
.wou
ld.
.is.can.ran
ge
.fro
m
.ver
y
.simp
le
.exa
mples
.lik
e
.“a.per
son
.wal
king
.alo
ng
.a.cor
ridor”
.up.
to.“t
here
.is.a.fo
otball
.ma
tch”
.in.a.st
adium.
references
[Bis95].Bishop,.C.M.,.Neural Networks for Pattern Recognition,.New.York,.Oxford.University.Press,.1995.
[BKV+08]
.Bruc
kner,
.D.,.J..Kasb
i,
.R..Veli
k,
.and.W..Herzner
,
.High-le
vel
.hierarc
hical
.sema
ntic
.pro
cessing
.
fram
ework
.fo
r
.sma
rt
.sen
sor
.net
works,
.In:.Pr
oceedings of the HSI,
.Kra
kow,
.Po
land,
.2008.
[BLS06]
.Bey
erer,
.J.,.F..Puente.Leo
n,
.and.K.-D..Somm
er
.(eds.),.Info
rmation
.fusio
n
.in.der.Mess-. und.
Sens
ortechnik,
.Uni
versitaetsverlag
.Ka
rlsruhe,
.Ka
rlsruhe,
.Ger
many,
.2006.
[Br
e02]
.Br
eazeal,
.C.,.De
signing Sociable Robots,
.Ca
mbridge,
.MA,.MIT.Pr
ess,
.2002.
[CR04]
.Cost
ello,
.M.C..and.E.D..Reich
le,
.LSDN
et:
.A.neural.netw
ork
.for.mul
tisensory
.percep
tion,
.In.Sixth
I
nternational Conference on Cognitive Modeling,
.Pi
ttsburgh,
.PA,.2004,.pp
.
.341–341.
*
.
http://en..wikipedia..org/wiki/User_interface
© 2011 by Taylor and Francis Group, LLC
Processing Data in Complex Communication Systems 68-11
[Dam94].Damasio,.A.,.Descartes’.Error:.Emotion,.Reason,.and the Human Brain,.New.York,.Penguine.
Boo
ks,
.1994.
[Da
v61]
. Dav
id,
. E.,. Bionics. or. elec
trology?
. An. intr
oduction
. to. the. sens
ory
. infor
mation
. iss
ue,
. IEEE
Tra
nsactions on Information eory,
.8(2),.74–77,.1961.
[Da
v97]
. Dav
is,
. J.,. Biolog
ical
. sens
or
. fusio
n
. insp
ires
. nov
el
. system. design,. In:. Joi
nt Service Combat
Identication Systems Conference,
.San.Diego
,
.CA,.1997.
[ENF07]
.Dietric
h,
.D.,.G..Fodo
r,
.G..Zuck
er,
.and.D..Bruc
kner
.(eds.),.Sim
ulating the Mind—A Technical
Neuropsychoanalytical Approach,
.Sp
ringer,
.Vienn
a,
.Au
stria,
.2009.
[FS94]
.Fas
olo,
.P..and.D.E..Seb
org,
.An.SQC.app
roach
.to.moni
toring
.and.faul
t
.detec
tion
.in.HVAC.cont
rol
.
system
s,
.In:.Pr
oceedings of the American Control Conference,
.Ba
ltimore,
.MD,.1994.
[GJ07]
.Ge
orge,
.D..an
d
.B..Ja
ros,
.e.HTM.lea
rning
.alg
orithms,
.Num
enta,
.Re
dwood
.Cit
y,
.CA,.2007.
[GLS+00]
.Gou
lding,
.P.,.B..Lenno
x,
.D..Sando
z,
.K..Smit
h,
.and.O..Mar
janovic,
.Fau
lt
.detec
tion
.in.cont
inuous
.
pro
cesses
.using.mul
tivariate
.sta
tistical
.meth
ods,
.Int
ernational Journal of Systems Science,
.31(11),.
1459–1471,.2000.
[Ha
i06]
. Hainic
h,
. R.R.,. e E
nd of Hardware,
. A No
vel Approach to Augmented Reality,
. Boo
ksurge,
.
Cha
rleston,
.SC,.2006.
[HG06]
.Haw
kins,
.J..and.D..Geo
rge,
.Hierar
chical
.temp
oral
.memo
ry—Concepts,
.the
ory,
.and.termin
ology,
.
Numen
ta,
.Re
dwood
.Cit
y,
.CA,.2006.
[HJ97]
.Hoo
d,
.C.S..and.C..Ji,.Pro
active
.netw
ork
.faul
t
.detec
tion,
.In:.Pro
ceedings of the INFOCOM,
.Vol
.
.3,.
Kobe,.Japan,.1997,.pp..1147–1155.
[HLS99]
.Hou
se,
.J.,.W.Y..Lee
,
.and.D.R..Shin,.Cla
ssication
.tec
hniques
.for.faul
t
.detec
tion
.and.diag
nosis
.of.
an.air
-handling
.unit,.AS
HRAE Transactions,
.105(1),.1987–1997,.1999.
[Is
e84]
.Iser
mann,
.R.,.Pro
cess
.faul
t
.detec
tion
.bas
ed
.on.mode
ling
.and.estim
ation
.meth
ods—A
.surv
ey,
.
Aut
omatica,
.20(4),.387–404,.1984.
[J
aa97]
.Jaak
kola,
.T.S.,.Var
iational
.meth
ods
.for.inferen
ce
.and.estim
ation
.in.grap
hical
.mode
ls,
.PhD.thesi
s,
.
Depa
rtment
.of.Bra
in
.an
d
.Cog
nitive
.Scien
ces,
.MIT,.Ca
mbridge,
.MA,.1997.
[J
GJS99]
.Jor
dan,
.M.I.,.Z..Gha
hramani,
.T.S..Jaak
kola,
.and.L.K..Saul
,
.An.intr
oduction
.to.vari
ational
.meth-
o
ds
.fo
r
.gra
phical
.mo
dels,
.Ma
chine Learning,
.37,.183–233,.1999.
[Ka
l60]
.Kalm
an,
.R.E.,.A.new.app
roach
.to.linea
r
.lt
ering
.and.pre
diction
.pro
blems,
.Tra
nsactions of the
ASME,
.Ser
ies D:
.Jo
urnal of Basis Engineering,
.82,.35–45,.Ma
rch
.1960.
[KBS01]
.Kamm
ermeier,
.P.,.M..Bus
s,
.and.G..Schmid
t,
.A.system
s
.the
oretical
.mode
l
.for.huma
n
.percep
tion
.
in.mu
ltimodal
.pr
esence
.syst
ems,
.IEEE/AS
ME Transactions on Mechatronics,
.6(3),.234–244,.2001.
[L
DS01]
.Loy
,
.D.,.D..Die
trich,
.and.H..Sch
weinzer
.(ed
s.),
.Ope
n Control Networks:
.Lon
Works/EIA 709 Technology,
.
Klu
wer
.Aca
demic
.Pub
lishers,
.Bost
on,
.MA/
Dordrecht,
.the.Net
herlands/London,
.U.K
.,
.200
1.
[Mat04]
. Mat
tern,
. F.,. Ubiqui
tous
. Com
puting:
. Sch
laue
. Alt
agsgegenstnde—Die
. Visio
n
. von. der.
Info
rmatisierung
.des.Al
ltags,
.Bu
lletin des SEV/VSE,
.19,.9–13,.2004.
[NH98]
.Nea
l,
.R.M..and.G.E..Hint
on,
.A.view.of.the.EM.algo
rithm
.tha
t
.jus
ties
.increm
ental,
.spa
rse,
.and.
oth
er
.vari
ants,
.In:.Lea
rning in Graphical Models,
.M.I..Jor
dan
.(ed.),.Klu
wer
.Academic.Publi
shers,
.
Dor
drecht,
.th
e
.Net
herlands,
.1998,.pp
.
.355–368.
[Pa
l08]
.Palen
sky,
.B.,.Fro
m
.neuro-psy
choanalysis
.to.cognit
ive
.and.ae
ctive
.aut
omation
.system
s,
.PhD.the-
si
s,
.In
stitute
.of.Co
mputer
.Te
chnology,
.Vienn
a
.Uni
versity
.of.Te
chnology,
.Vienn
a,
.Au
stria,
.2008.
[P
L03]
.Pon
toppidan,
.N..and.J..Lar
sen,
.Uns
upervised
.con
dition
.cha
nge
.det
ection
.in.lar
ge
.die
sel
.eng
ines,
.
In:. IEE
E Workshop on Neural Networks for Signal Processing,
. Tou
louse,
. Fra
nce,
. C.. Mol
ina,
.
T.
Adali,
.J..Lar
sen,
.M.V
.
.Hul
le,
.S..Dou
oglas,
.and.J..Rou
at
.(ed
s.),
.IEE
E
.Pre
ss,
.Pis
cataway,
.NJ,.200
3,
.
pp..565
–574.
[RJ86]
.Rab
iner,
.L.R..and.B.-H..Jua
ng,
.An.intr
oduction
.to.hidden.Mar
kov
.mode
ls,
.IEEE ASSAP
Magazine,
.
3,.4–16,.Ja
nuary
.1986.
[Sal00]
.Sall
ans,
.B.,.Lea
rning
.facto
red
.repr
esentations
.for.par
tially
.obser
vable
.Mar
kov
.decisio
n
.pro
cesses,
.
In:.Adv
ances in Neural Information Processing Systems,
.S.A..Sol
la,
.T.K..Leen,.and.K.-R..Mül
ler
.(eds.),.
Vol
.
.12,.e.MIT.Pr
ess,
.Ca
mbridge,
.MA,.2000,.pp
.
.1050–1056.
© 2011 by Taylor and Francis Group, LLC
68-12 Industrial Communication Systems
[SBR05].Sallans,.B.,.D..Bruckner,.and.G..Russ,.Statistical.model-based.sensor.diagnostic.for.automation.
system
s,
.In:.Pr
oceedings of the IFAC FET,
.Pueb
la,
.Mexico
,
.2005.
[SH03]
.Sch
ein,
.J..and.J..Hou
se,
.App
lication
.of.cont
rol
.cha
rts
.for.detec
ting
.faul
ts
.in.vari
able-air-volume
.
box
es,
.AS
HRAE Transactions,
.109(2),.671–682,.2003.
[S
ol02]
.Sol
ms,
.M..and.Tur
nbull,
.O..e
Brain and the Inner World:
.An
Introduction to the Neuroscience of
Subjective Experience,
.Kar
nac/Other
.Pre
ss,
.Cat
hy
.Mil
ler
.For
eign
.Rig
hts
.Age
ncy,
.Lon
don,
.U.K
.,
.200
2.
[Vel08]
.Veli
k,
.R.,.A.bionic.mode
l
.for.huma
n-like
.machin
e
.percep
tion,
.PhD.thesi
s,
.Ins
titute
.of.Com
puter
.
Tec
hnology,
.Vienn
a
.Uni
versity
.of.Te
chnology,
.Vienn
a,
.Au
stria,
.2008.
[VLS+08]
.Vada
kkepat,
.P.,.P..Lim,.L.C..De.Sil
va,
.L..Jing
,
.and.L..L..Ling
,
.Mul
timodal
.app
roach
.to.huma
n-
face
.dete
ction
.an
d
.trac
king,
.IEEE Tr
ansactions on Industrial Electronics,
.55(3),.1385–1393,.2008.
[WS
e06]
. Tsa
halis,
. D.T.,. SENSE-S
mart
. Embe
dded
. Netw
ork
. of. Sensin
g
. Enti
ties,
. Univ
ersity
. of. Pat
ras,
.
Avai
lable
.at.ww
w.sense-ist.org
.SENS
E
.pr
oject
.we
b
.sit
e
© 2011 by Taylor and Francis Group, LLC
