Long L. Home Networking Demystified
Подождите немного. Документ загружается.

181
CHAPTER
10
Privacy and
Security
There are organizations charged with maintaining some semblance of order in
cyberspace, but the cybercops are ill-equipped and existing laws often are ambiguous
and diffi cult to enforce. For the most part, it is up to you to protect yourself, your
home network and its PCs, and your valuable information from the continual threats
and annoyances streaming over the Internet.
The Internet opens the door to the wonders of global sharing, but it also opens
doors for people whose interests are scams and malicious destruction. Crackers are
continually “cracking” through Internet security at the server and the PC levels to
disrupt the fl ow of information and, in general, wreaking havoc. Hate mongers,
stalkers, and the like have found a home on the Internet, too. Cyberthieves will even
steal your identity by surreptitiously gathering enough personal information about
you (without your knowledge) to assume your identity.
DSL, cable-modem, and satellite connections are “always on,” so the risk of
unauthorized access to your home network and PCs is ever present and must be
addressed. This chapter is intended to raise your awareness of the dark side of the
Internet and introduce you to the tools that can help you feel more secure in your
continuously linked home networking environment.
ch10.indd 181ch10.indd 181 2/22/2005 1:20:17 PM2/22/2005 1:20:17 PM
Copyright (c) 2005 by The McGraw-Hill Companies. Click here for term of use.

182
Home Networking Demystifi ed
NOTE NOTE I want to remind you again how important it is that you keep your Windows
operating system current with the latest releases from Microsoft. Having the latest
Windows updates installed will give your system the best available protection
from Internet intruders. To install the latest Windows XP updates, click Start |
Help And Support | Windows Update.
The Firewall
An estimated 5 percent of all transactions on the Internet are fraudulent or an
attempt at theft. Scary, isn’t it? Unfortunately, we are forced by these Internet
realities to build a wall around our PCs and home networks, an electronic wall
called a fi rewall. A fi rewall is software that sets up a protective “wall” between a
home network or a particular PC (the private side) and the rest of cyberspace (the
public side). Having a fi rewall is a good starting point for the implementation of a
personal computing plan for Internet security.
A fi rewall is a system that enforces access control policy between your home
network (or PC) and the Internet. All home gateways have built-in fi rewalls. In fact,
fi rewall protection is built into the Window operating system. However, the front-
end protection provided by your home gateway’s (router/AP/modem) built-in
fi rewall is preferable to the PC-level fi rewall within Windows.
Firewalls differ widely in methods and levels of sophistication, but all of them
have essentially two tasks—to block traffi c and to permit traffi c. A fi rewall’s access
control policy can be set up to screen electronic traffi c in both directions. It restricts
unwanted access to a home network or a PC, and it can block certain types of
outgoing communications. Most fi rewalls automatically block unsolicited attempts
at communication from the public side of the electronic “wall” that stands between
your LAN and the Internet. They do this according to control policies set forth as a
group of rules for access. For example, one rule might be to permit e-mail traffi c
and another might be to deny unauthenticated logins from the public side.
The screening process can be adjusted to the desired level of security. A high
security setting may block all e-mail with attachments or embedded graphics. Most
people choose a lower fi rewall setting to permit the fl ow of legitimate traffi c. Of
course, this small opening is enough for some undesirable transmissions to pierce
your PC’s armor. I would suggest that you choose nothing less than a medium level
of security.
Crackers and hackers use port scanner software to search the Internet for
unprotected networks and PCs so that they can hijack and use them to distribute
pornography, send spam, gather personal information, or carry out some other illicit
ch10.indd 182ch10.indd 182 2/22/2005 1:20:19 PM2/22/2005 1:20:19 PM
CHAPTER 10 Privacy and Security
183
activity. Port scanners comb the Net 24/7 at electronic speeds seeking servers or
home gateways with public IP addresses that respond to connection requests to
specifi c ports of entry to a network.
Port numbers are assigned to each packet of information traveling the Internet.
The packet’s port number associates it with a type of traffi c. For example, port 80
is for browser traffi c (HTTP services) and port 25 is for e-mails (SMTP services).
Windows fi le sharing is done through port 139, which is always a target for crackers.
Xbox Live uses ports 88 and 3074. The unique IP address and the port number
embedded in an Internet packet compose a socket that directs communication
between specifi c applications (Web Wide Web or e-mail) that run on specifi c host
computers.
Firewalls have a port fi ltering capability that selectively enables or disables
Transmission Control Protocol (TCP) ports and User Datagram Protocol (UDP)
ports (the latter used for messaging applications). Port fi ltering serves to insulate
home gateways and their networks from cracker/hacker attacks by blocking entry to
certain ports.
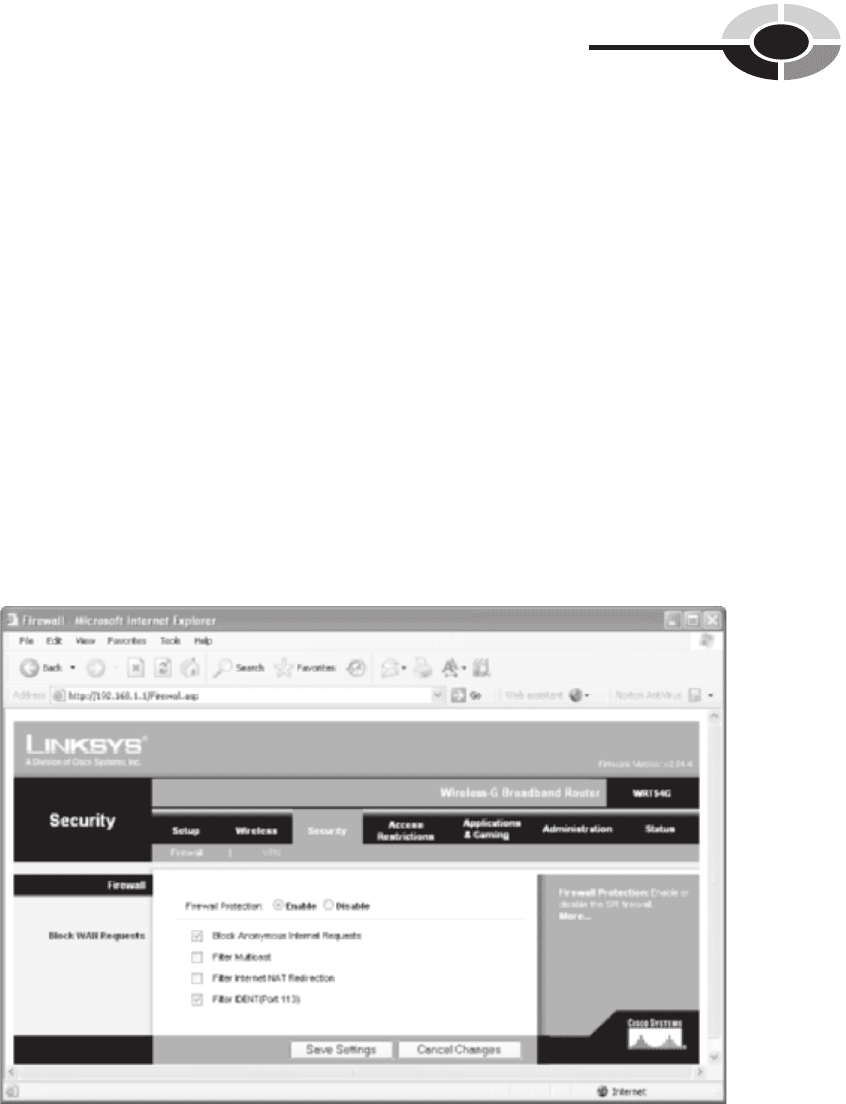
Your gateway has a fi rewall (see Figure 10-1). Windows has a fi rewall. And, you
probably will have Internet security software that offers fi rewall protection, too.
Figure 10-1 Firewall options for a Linksys wireless home gateway
ch10.indd 183ch10.indd 183 2/22/2005 1:20:20 PM2/22/2005 1:20:20 PM

184
Home Networking Demystifi ed
Your gateway’s fi rewall sets up a protective wall between the public Internet
and your private LAN. The gateway fi rewall will be enabled by default. Windows and
commercial Internet protection software provide protection at the PC level.
Commercial Net security products, such as Symantec’s Norton Internet Secur-
ity Professional and McAfee Security’s Personal Firewall Plus or Internet Security
Suite, offer excellent PC-level fi rewalls. So does Windows. These, plus your gateway,
offer a solid line of defense against unauthorized access, but you probably don’t need all
of that redundant protection in a home network environment. Your gateway’s fi rewall
should be suffi cient. PC-level protection is easily enabled or disabled. The Windows
fi rewall (see Figure 10-2) is enabled by default. To enable/disable the Windows fi rewall,
click Start | Control Panel | Network And Internet Connections | Windows Firewall. To
enable/disable the fi rewall that comes with your Net security software, turn it on/off in
the software’s main menu (see Figure 10-2).
CAUT IO N CAUTION Having a gateway with a fi rewall does not mean you are fully protected
from the bad stuff on the Internet. The fi rewall, with the help of NAT (Network
Address Translation), which is discussed in Chapter 3, does a good job of selectively
permitting authorized traffi c fl ow between your home network and the Internet.
It does not, however, evaluate the content of that traffi c. For example, all fi rewalls
let you send and receive e-mails, even those with attachments containing viruses.
For protection from viruses, you need antivirus software.
Figure 10-2 Enabling/disabling the fi rewalls for Windows and Norton Internet Security
Professional
ch10.indd 184ch10.indd 184 2/22/2005 1:20:22 PM2/22/2005 1:20:22 PM

CHAPTER 10 Privacy and Security
185
Security for Wireless Home Networks
Most home network security threats come from Internet hackers, but to get to your
network, they must fi nd a way to get past your fi rewall—not an easy task. With the
rapid acceptance of wireless home networking, a new breed of hackers has emerg-
ed. Wireless hackers tap directly into your wireless network, thus bypassing the
fi rewall. Wireless LANs are installed on the private side of the fi rewall, so the
fi rewall offers no protection from wireless hackers. Wireless hackers can tap into
your home network from the house next door or from a car parked at curbside in
front of your house. Unless you are constantly checking the status of the LAN, you
are probably unaware that your network is being violated. Once online, the wireless
hacker’s PC becomes just another peer node on your LAN.
WEP and WPA Encryption
Virtually all network gear supports a security feature called Wired Equivalent Privacy,
or simply WEP. WEP uses data encryption techniques to scramble information passed
between wireless devices. A hacker attempting to tap into your WEP-enabled wire-
less network would fi nd only meaningless bits. The AP and client device on the
home network shares an encryption key that is used to scramble and unscramble the
encrypted information sent via wireless links.
Wi-Fi Protected Access, or WPA, is an enhanced encryption technique that is
available on most modern network gear (after 2004). WPA employs authentication
via user ID and password and uses more sophisticated encryption. Once the
authorized client PC is authenticated, the AP sends a temporary encryption key that
is valid only during the current communications session.
WEP is not as secure as WPA, but having any encryption method in place is a
major deterrent to hackers. However, most systems are set up such that you must
activate WEP or WPA to enable wireless protection. Because WEP and WPA are
turned off by default, many, perhaps most, home networks are vulnerable to
intruders. WEP is not perfect, but with so many unprotected networks in your
neighborhood, simply having it enabled is enough to send hackers down the street
(or hall in an apartment building) to an easier target.
The primary difference between WEP and WPA is the handling of the encryption
key. WEP uses the same encryption key, whereas WPA constantly changes the
encryption key. With WPA, the hacker has very little time to break the key.
To turn on WEP or WPA encryption, navigate to the wireless setup screen on
your gateway and choose an encryption method. WPA has a higher overhead and
may slow the network more than the more straightforward WEP; however, WPA
ch10.indd 185ch10.indd 185 2/22/2005 1:20:27 PM2/22/2005 1:20:27 PM
186
Home Networking Demystifi ed
encryption offers a higher level of security. For WEP, you may need to choose
between levels of WEP security, either 64-bit or 128-bit. The 128-bit option provides
better security, but network speed is sacrifi ced at the higher bit level.
The information you enter to enable WEP or WPA encryption is similar but may
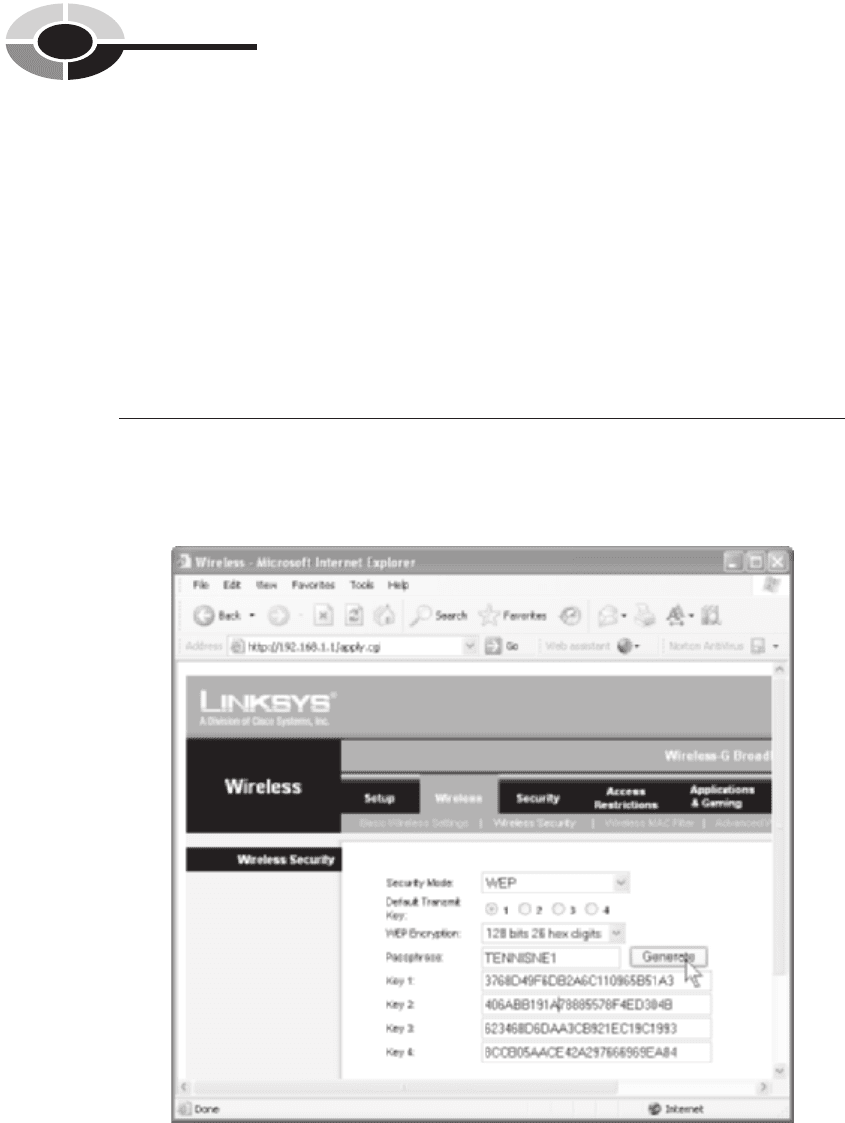
vary slightly among gateway vendors. The Linksys gateway’s wireless setup screen
lets you generate keys by entering an alphanumeric passphrase (see Figure 10-3). I
suggest doing this rather than entering a long string of hexadecimal numbers. For
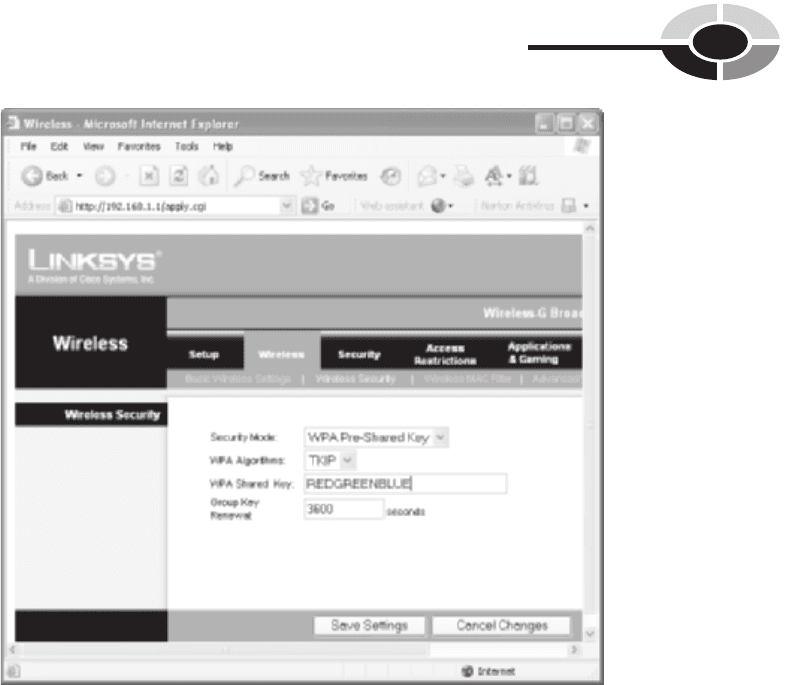
WPA encryption, you must enter a shared key password (see Figure 10-4). I
encourage you to enable one of these encryption methods, but if you do, be advised
that each device in your wireless LAN must use the same encryption method and
encryption key.
NOTE:NOTE: Hexadecimal is a base-16 numbering system that uses 0 through 9 plus A
through F for its numbers. Because a hex number can represent four bits (binary
numbers), “hex” has evolved as shorthand for representing bits. For example, a
hex A is a binary 1010 (or a decimal 10).
Figure 10-3 WEP wireless security setup screen for a Linksys gateway
ch10.indd 186ch10.indd 186 2/22/2005 1:20:28 PM2/22/2005 1:20:28 PM
CHAPTER 10 Privacy and Security
187
Other Wireless Security Precautions
Enable WEP or WPA encryption and follow these guidelines, and your private
home network should remain private:
• Change the default administrator password for access to the gateway. All
hackers know the manufacturers’ default passwords, and they routinely hack
into home networks via this password. Once in, they can change important
network settings, including the SSID and security keys. Change this password
to something of your choosing, preferably one that has both letters and
numbers and cannot in any way be associated with you. A password made
up of random characters, such as “8cexb43”, is superior to one formed from
your last name with address, “jones1583”.
Figure 10-4 WPA wireless security setup screen for a Linksys gateway
ch10.indd 187ch10.indd 187 2/22/2005 1:20:32 PM2/22/2005 1:20:32 PM

188
Home Networking Demystifi ed
• Change the wireless network name (SSID). Change the SSID (Service
Set Identifi er) from the manufacturer’s default (for example, “linksys”
for Linksys products). Each network node must be associated with this
case-sensitive name, so be sure to change it on all network devices by
running the Windows XP Wireless Network Setup Wizard (click Start |
All Programs | Accessories | Communications | Wireless Network Setup
Wizard). It’s a good practice to change the SSID every month or so.
• Disable SSID broadcast. When a wireless PC begins seeking a signal from
a wireless network, it detects the SSID broadcast by the gateway’s AP.
Router/gateways give you the option to enable or disable wireless SSID
broadcast. There is a convenience in permitting SSID broadcast, but doing
so makes it easier for hackers to log into your system. My recommendation
is to disable SSID broadcast in your gateway’s setup. This will thwart
attempts by the vast majority of wireless hackers, but the persistent, hard-
core hackers can still capture the SSID.
• Change the passphrase for WEP. If you use WEP wireless security, you
can increase your level of security by changing the WEP encryption key
periodically on the AP and its client PCs. This involves changing the
passphrase that generates the encryption key.
• Change your workgroup name. It’s a good idea to change your workgroup
name from the system default because it sets up one more hurdle for any
would-be hackers.
Internet Threats
Before the Internet, people who do dastardly deeds were limited by geography. The
Internet has lifted that constraint, and the seedier elements of our society are free to
traverse the globe at electronic speeds planting malware wherever they go. Malware
is short for malicious software, that is, software that is designed to damage your PC,
disrupt its operation, or in some way violate its security. Malware refers to a host of
hostile software, such as viruses, Trojan horses, worms, spyware, and so on.
Computer Viruses
The computer virus is a program or portion of a program that causes something
(usually something bad) to occur in your PC. A computer virus can cause anything
from a minor inconvenience to major devastation. A virus can take over your
ch10.indd 188ch10.indd 188 2/22/2005 1:20:34 PM2/22/2005 1:20:34 PM

CHAPTER 10 Privacy and Security
189
computer and cause a range of events to occur. Some viruses destroy the contents
of your hard disk. Others grow like a cancer, eating away at your fi les. Some are
virtual bombs that “explode” at a preset time (for example, Friday the thirteenth).
One strain of virus causes the Internet to be fl ooded with e-mail, each message with
an attached program that causes more infected e-mail to be sent out over the Internet.
This type of assault is referred to as a denial of service attack. Some viruses are
relatively benign. For example, the Cookie Monster virus displays “I want a cookie”
and then locks your PC until you enter “Fig Newton.”
Over 50,000 viruses fl ow freely through the Internet. Most are spread as
attachments to e-mails. However, they also can be passed by shared interchangeable
disks/discs and via PCs on a home network.
Types of Viruses
The two main types of virus are the macro virus and the worm virus. The macro
virus is a small program that might be embedded in an application document, such
as a Microsoft Word or PowerPoint fi le. This type of virus is spread via e-mail
attachments. The macro program is executed when the e-mail recipient opens an
infected attached fi le. A worm is a parasitic program that makes copies of itself.
Worms are separate entities and don’t attach themselves to programs, fi les, or
documents.
The Trojan horse isn’t actually a virus, because it doesn’t replicate itself. The
Trojan horse appears as a seemingly useful program. For example, one Trojan horse
announces that your PC is vulnerable and invites you to click OK if you want to
make your system more secure. When executed, it plants a malicious program in
your system. Many Trojan horses are “dialers” that use your dial-up modem and
phone line to make international calls or fee-based 900-number calls.
Virus Protection
The fi rewall and a good antivirus program are your best protection against the
malicious people who hang out on the Internet. Modern antivirus programs do a
good job of keeping our PCs free from virus. However, they are not perfect but are
only as good as their list of virus defi nitions. The two biggest names in virus
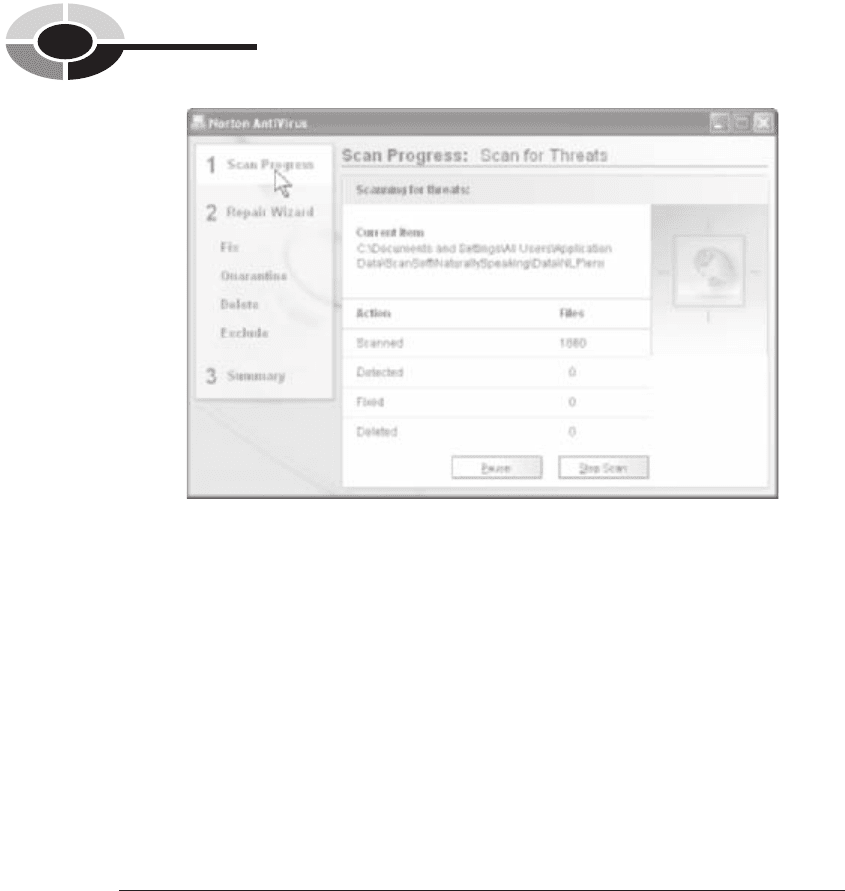
protection are the Norton AntiVirus program (Symantec Corporation), shown in
Figure 10-5, and the VirusScan program (McAfee Security). Most new PCs have
one of these programs installed or offer them as supplemental software. If you have
any networked PCs that do not have antivirus protection, I would recommend that
you get it at your earliest convenience. A PC without virus protection is a point of
vulnerability that could cause serious problems for other PCs on the network.
ch10.indd 189ch10.indd 189 2/22/2005 1:20:36 PM2/22/2005 1:20:36 PM
190
Home Networking Demystifi ed
Antivirus software is used in conjunction with a virus protection subscription
service that lets you download protection for recent viruses, including the virus du
jour. My software is preset to update virus defi nitions daily. Antivirus software and
protection service can cost from $25 to $50 (software included) a year. That cost is
small relative to the cost of a single fl ing with a virus-infected home network.
An antivirus program protects you against all kinds of viruses by checking all
material that streams into your PC from the Internet. It also checks for viruses when
you open a document fi le and when you insert any type of removable media. The
antivirus software also monitors your computer for indications that a virus may be
present. Table 10-1 lists some virus protection tips.
TI P TIP If your PC is without virus protection but you have Internet access, several
Internet security companies offer a free security check that includes a scan of your
PC for viruses. To check your PC for viruses, navigate to the Symantec (www.
symantec.com) or McAfee (www.mcafee.com) web sites and start the free scan.
Usually the free scan is available on the home/home offi ce page.
Figure 10-5 Scanning for viruses: Norton AntiVirus
ch10.indd 190ch10.indd 190 2/22/2005 1:20:38 PM2/22/2005 1:20:38 PM
