Desurvire E. Classical and Quantum Information Theory: An Introduction for the Telecom Scientist
Подождите немного. Документ загружается.

24.4 Hadamard–Steane code 517
x Code word
0000 000 0111 001 1011 010 1100 011 1101 100 1010 101 0110 110 0001 111
Coset Equals
0
0000 000
0000 000 0111 001 1011 010 1100 011 1101 100 1010 101 0110 110 0001 111
0 + C2
1
0001 111
0001 111 0110 110 1010 101 1101 100 1100 011 1011 010 0111 001 0000 000 1 + C2 2 + C2
1 + C2 2 + C2
2
0010 011
0010 011 0101 010 1001 001 1110 000 1111 111 1000 110 0100 101 0011 100
2 + C2
3
0011 100
0011 100 0100 101 1000 110 1111 111 1110 000 1001 001 0101 010 0010 011
4
0100 101
0100 101 0011 100 1111 111 1000 110 1001 001 1110 000 0010 011 0101 010
5
0101 010
0101 010 0010 011 1110 000 1001 001 1000 110 1111 111 0011 100 0100 101
6
0110 110
0110 110 0001 111 1101 100 1010 101 1011 010 1100 011 0000 000 0111 001 6 + C2 0 + C2
7
0111 001
0111 001 0000 000 1100 011 1011 010 1010 101 1101 100 0001 111 0110 110
7 + C2 0 + C2
8
1000 110
1000 110 1111 111 0011 100 0100 101 0101 010 0010 011 1110 000 1001 001
9
1001 001
1001 001 1110 000 0010 011 0101 010 0100 101 0011 100 1111 111 1000 110
10
1010 101
1010 101 1101 100 0001 111 0110 110 0111 001 0000 000 1100 011 1011 010 10 + C2 0 + C2
11
1011 010
1011 010 1100 011 0000 000 0111 001 0110 110 0001 111 1101 100 1010 101 11 + C2 0 + C2
12
1100 011
1100 011 1011 010 0111 001 0000 000 0001 111 0110 110 1010 101 1101 100 12 + C2 0 + C2
13
1101 100
1101 100 1010 101 0110 110 0001 111 0000 000 0111 001 1011 010 1100 011 13 + C2 0 + C2
14
1110 000
1110 000 1001 001 0101 010 0010 011 0011 100 0100 101 1000 110 1111 1111
15
1111 111
1111 111 1000 110 0100 101 0011 100 0010 011 0101 010 1001 001 1110 000
Dual code C2
= (
7
,
3
)
Code C1 =
(
7
,
4
)
14 + C2 2 + C2
15 + C2 2 + C2
9 + C2 2 + C2
8 + C2 2 + C2
5 + C2 2 + C2
4 + C2 2 + C2
3 + C2 2 + C2
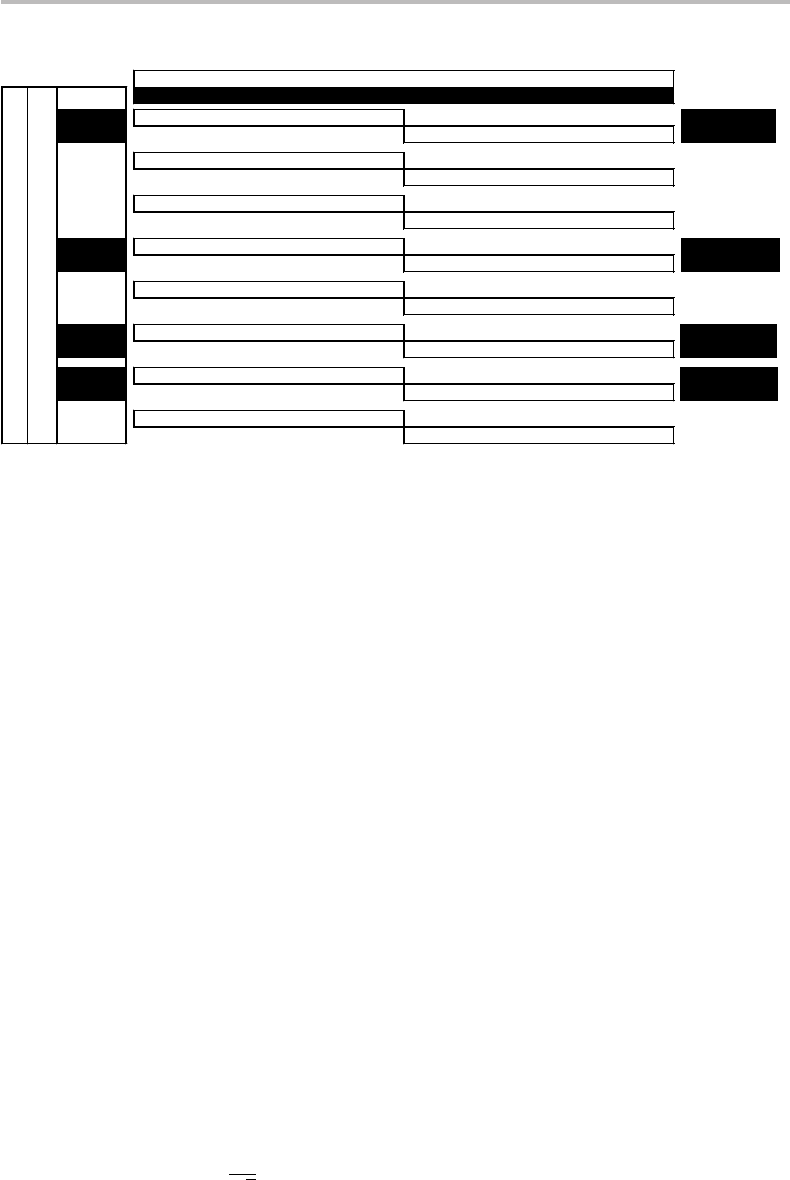
Figure 24.6 Cosets of C
2
= (7, 3) in C
1
= (7, 4). The codewords of C
2
are listed in the top row,
while the codewords of C
1
(called x = 0, 1, 2,...,15) are listed in the left column. The
elements of C
1
that are in C
2
are highlighted with a dark background. The two rightmost
columns show the coset names and identify their equivalences, the only two different cosets
being captured in 0 +C
2
and 2 +C
2
.
the code C
2
has the same correction capability as C
1
, namely t = (d
min
− 1)/2 = 1bit
(see Section 11.2). Then comparing the codes listed in Table 24.4 (C
1
= (7, 4)) and Table
24.5 (C
2
= C
⊥
1
= (7, 3)), we observe that the second is included in the first, namely the
property C
2
⊂ C
1
, i.e., C
2
is a subgroup of C
1
. According to the previous section,
such a condition (along with the condition that C
2
must have the same error-correction
capability t as C
1
) makes the dual code C
2
fully eligible to construct a CSS(C
1
, C
2
)
quantum code of dimension 2
k
1
−k
2
= 2
4−3
= 2.
The construction of CSS(C
1
, C
2
) is made by applying the definition in Eq. (24.36),
which, given x ∈ C
1
, requires one to determine all the |C
2
|=8 binary codewords x + y
forming the cosets x +C
2
, and to sum up the
|
x + y
quantum states thus defined.
Figure 24.6 provides the full list of cosets of C
2
in C
1
. The top row lists the codewords
of C
2
, while the left column lists the codewords of C
1
(called x = 0, 1, 2,...,15) and
whose elements that are in C
2
have been highlighted with a dark background. From
the table information, it is readily observed that all the common elements x ∈ C
1
, C
2
belong to the same coset 0 +C
2
, while all elements x
∈ C
1
, x
/∈ C
2
belong to the same
coset 2 +C
2
(which could as well be called 15 + C
2
, for instance). Therefore, taking
any codeword pair x, x
with such properties is sufficient to generate and define the
two codewords of CSS(C
1
, C
2
), which we shall call |
0, |
1. For instance, we can use
x = 0000000 (x ∈ C
1
, C
2
) and x
= 1111111(x
∈ C
1
, x
/∈ C
2
). We, thus, obtain:
|
0≡
|
0000000 +C
2
=
1
√
8
3
|
0000000
+
|
0111001
+
|
1011010
+
|
1100011
|
1101100
+
|
1010101
+
|
0110110
+
|
0001111
4
,
(24.53)

518 Quantum error correction
Table 24.6 Defining a rule for the codeword bits of C
2
(Table 24.5); see text for description.
1234 567
x
1
+ x
2
x
1
+ x
3
x
2
+ x
3
x
1
+ x
2
+ x
3
x
1
x
2
x
3
0000 000
0111 001
1011 010
1100 011
1101 100
1010 101
0110 110
0001 111
|
1≡
|
1111111 +C
2
=
1
√
8
3
|
1111111
+
|
1000110
+
|
0100101
+
|
0011100
|
0010011
+
|
0101010
+
|
1001001
+
|
1110000
4
.
(24.54)
To recall, to construct the Steane code {|
0, |
1}we have used a generator matrix
ˆ
G =
˜
H
T
in systematic form,asshowninEq.(24.52). As previously mentioned, there exist several
other possibilities for defining the parity-check matrix
˜
H
T
of the (7, 4) Hamming code.
It is left as an easy exercise to determine the Steane code {|
0, |
1}obtained with a matrix
ˆ
G
=
˜
H
T different from that used in this chapter. It does not matter that the resulting
codewords |
0, |
1 differ from those defined in Eqs. (24.53)or(24.54), because in any
(n, k) block code the choice of generator and parity-check matrices is only a matter of
convention.
How can we realize a quantum circuit capable of encoding the above-defined |
0, |
1
Steane codewords, which represent finely crafted superpositions of eight 7-qubits? Short
of a rule to predict the values of the individual qubits within each of these 7-qubit
superpositions, the task of designing such a circuit seems rather complex! But here
comes a bit of magic in the way we can define a rule for the two codewords. As a
starting point, we have seen that each 7-qubit |Y in the definition |
0 refers to the block
codeword Y , which is an element of the coset 0 +C
2
. To find the rule governing the
bit values of Y , we first list the codewords in seven columns, as shown in Table 24.6.
Because the code is in systematic form, the first four columns 1234 represent parity bits,
while the last three columns 567 represent the message bits. If we call x
1
, x
2
, x
3
these
three bits, we observe from the table that the parity bits in columns 1234 are defined by
the sums x
1
+ x
2
, x
1
+ x
3
, x
2
+ x
3
, and x
1
+ x
2
+ x
3
, respectively.
The Steane codeword |
0 is, thus, defined by the three message bits x
1
, x
2
, x
3
,as:
|
0=
1
√
8
y∈C
2
|
x + y
≡
1
√
8
x
1
,x
2
,x
3
|
x
1
+ x
2
|
x
1
+ x
3
|
x
2
+ x
3
|
x
1
+ x
2
+ x
3
|
x
1
|
x
2
|
x
3
.
(24.55)

24.4 Hadamard–Steane code 519
AsshowninEq.(24.54), the other Steane codeword |
1 is generated by the bitwise
addition of z = 1111111 to each of the elements in C
2
/0 + C
2
, which yields the alternate
definition:
|
1=
1
√
8
y∈C
2
|x + y + z
≡
1
√
8
x
1
,x
2
,x
3
=0,1
(|x
1
+ x
2
+ 1|x
1
+ x
3
+ 1|x
2
+ x
3
+ 1
⊗|x
1
+ x
2
+ x
3
+ 1|x
1
+ 1|x
2
+ 1|x
3
+ 1).
(24.56)
Letting the bit variable a = 0, 1 we finally obtain a common definition for the Steane
codewords:
|
a≡
1
√
8
x
1
,x
2
,x
3
=0,1
(|x
1
+ x
2
+ a|x
1
+ x
3
+ a|x
2
+ x
3
+ a
⊗|x
1
+ x
2
+ x
3
+ a|x
1
+ a|x
2
+ a|x
3
+ a). (24.57)
We may simplify the above definition even further by setting the bit variables y
1
=
x
1
+ a, y
2
= x
2
+ a and y
3
= x
3
+ a, which gives
|
a≡
1
√
8
y
1
,y
2
,y
3
=0,1
(|y
1
+ y
2
+ a|y
1
+ y
3
+ a|y
2
+ y
3
+ a
⊗|y
1
+ y
2
+ y
3
|y
1
|y
2
|y
3
). (24.58)
(where the modulo-2 addition property u + u = 0 is applied for any bit u = x
i
, y, a =
0, 1). As we shall see next, the general definition of |
ˆ
a in Eq. (24.57) represents the
“magic formula” needed to build a complete Steane encoder circuit!
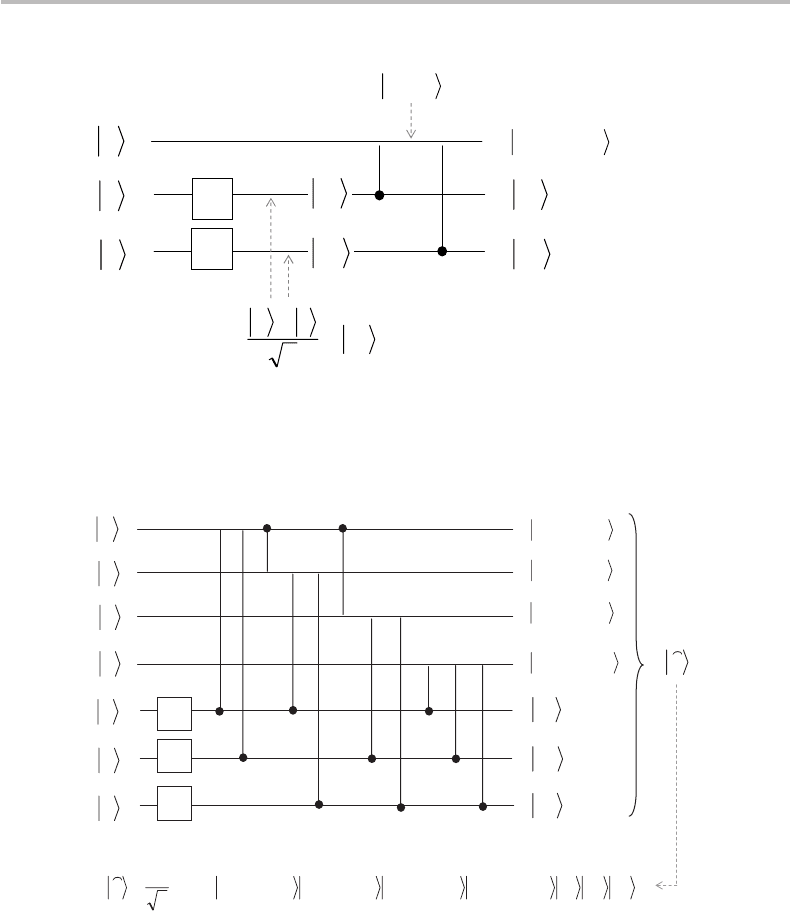
Indeed, consider the first qubit in |
ˆ
a, namely |y
1
+ y
2
+ a. The most elementary
subcircuit that can be implemented to generate |y
1
+ y
2
+ awith y
1
, y
2
= 0, 1isshown
in Figure 24.7. It is seen from the figure that the two Hadamard gates produce two
|y
i
=|+states that can act as control qubits on the target qubit
|
a
through CNOT
gates (recalling that
|
y
CNOT|x=
|
y ⊕ x
≡
|
x + y
). We observe that
|
a
, which
represents the originator’s message qubit to be encoded, is not limited to the basis states
|0 or |1; most generally, it can be of the form
|
a
= α|0+β|1, where, as usual, α, β
are complex amplitudes satisfying
|
α
|
2
+
|
β
|
2
= 1.
Based on the above, it is not at all difficult to conceive the full Steane-code encoding
circuit shown in Fig. 24.8, which represents only one possible implementation out of
many other variants, let alone the flexibility associated with the many other choices
for generator matrix
ˆ
G in the (7, 4) code. Note that the same circuit, as traversed
from right to left, can be used for decoding, i.e., retrieving the message qubit |a=
α|0+β|1from the 7-qubit |
ˆ
a, as obtained from the recipient after implementing error
correction.
This concludes this chapter on quantum error correction. An eerie feeling may rise
from realising that the above-described CSS codes only represent another conceptual
subspace within a grander space of the so-called stabilizer codes. Such codes, which
are, by and large, not limited to error correction but rather are at the root of advanced
520 Quantum error correction
a
0
0
H
H
x
i
y
=
+
2
10
1
y
2
y
ay
+
1
x
ayy
++
21
1
y
2
y
Figure 24.7 Elementary circuit to generate the quantum state |y
1
+ y
2
+ a given bit values
α, y
1
, y
2
= 0, 1, as based on H (Hadamard) and CNOT gates. The states obtained at
intermediate stages are shown and pointed to by dotted arrows.
)(
∑
=
++++++++≡
1
,
0
,,
321321323121
321
8
1
y
y
y
yyyyy
y
ayyay
ya
y
y
a
a
0
0
xx
ayy ++
21
1
y
2
y
0
3
y
H
H
H
0
0
0
ayy ++
31
xxx
x
x
x
a
y
y ++
32
x
xx
321
yyy ++
a
Figure 24.8 Possible circuit implementation for encoding the |
ˆ
a=|
ˆ
0, |
ˆ
1 Steane code example,
as defined in Eq. (24.58).
quantum computing, represent yet another field by itself. Within the framework of these
chapters, hopefully the reader has grasped the essentials to exercise his or her curiosity
towards this direction. If the reader has gone this far in these chapters, there are no more
conceptual difficulties involved, except for the never-ending work of specialization in
the field. The last chapter, concerning quantum cryptography should complete our basic
training towards the impossible or ill-defined grander picture, whether or not we elect to
become a specialist!
24.5 Exercises 521
24.5 Exercises
24.1 (B): Establish the following three operator definitions
Z
12
= Z ⊗ Z ⊗ I =
(
|0000|+|1111|
)
⊗ I −
(
|0101|+|1010|
)
⊗ I,
Z
23
= I ⊗ Z ⊗ Z = I ⊗
(
|0000|+|1111|
)
− I ⊗
(
|0101|+|1010|
)
,
Z
13
= Z ⊗ I ⊗ Z =|00|⊗I ⊗|00|+|11|⊗I ⊗|11|
−(|00|⊗I ⊗|11|+|11|⊗I ⊗|00|),
where Z is the Pauli matrix,
Z =
10
0 −1
.
24.2 (M): Given the 9-qubit quantum error-correction (Shor) code
|
ˆ
ˆ
0=
|000+|111
√
2
+
+
+
+
A
|000+|111
√
2
+
+
+
+
B
|000+|111
√
2
+
+
+
+
C
|
ˆ
ˆ
1=
|000−|111
√
2
+
+
+
+
A
|000−|111
√
2
+
+
+
+
B
|000−|111
√
2
+
+
+
+
C
,
show that a single qubit phase-flip error in any of the three blocks A, B, C can
be detected through the successive measurements
X
123456
= X
1
X
2
X
3
X
4
X
5
X
6
,
X
456789
= X
4
X
5
X
6
X
7
X
8
X
9
,
where X is the Pauli matrix,
X =
01
10
.
24.3 (M): Assuming a 3-qubit entangled block with the second qubit being flipped,
|
ˆ
ˆ
q=
|010+|101
√
2
,
show that the syndrome measurement Z
13
of the last two qubits yields the expec-
tation value
Z
13
=+1.
24.4 (T): Establish that the set C of 16 elements shown in Table 24.7 (underscore “–”
being for reading clarity), together with bitwise addition ⊕, form a group
(
C, ⊕
)
.
Then determine the different subgroups of
(
C, ⊕
)
and possible cosets of C
in C.

522 Quantum error correction
Table 24.7 Elements for Exercise 24.4.
Number Element Number Element
0 0000 000 8 1000 110
1 0001
111 9 1001 001
2 0010
011 10 1010 101
3 0011
100 11 1011 010
4 0100
101 12 1100 011
5 0101
010 13 1101 100
6 0110
110 14 1110 000
7 0111
001 15 1111 111
24.5 (T): Given the 2 × 2 matrix,
U =
u
11
u
12
u
21
u
22
,
with coefficients having the bit values u
ij
= 0, 1 and a 2-qubit state |x, where x is
a two-bit codeword, determine a quantum circuit that achieves the transformation
|x|0→|x
|
Ux
,
uniquely based on CNOT gates. Show that a more compact circuit can be elabo-
rated with CCNOT gates.
24.6 (T): Given a linear block code C with codewords x = x
1
x
2
...x
n
, show that for
any y such that y ∈ C
⊥
(dual of C), we have
(a)
x∈C
(−1)
x·y
=
|
C
|
,
and otherwise (y /∈ C
⊥
)
(b)
x∈C
(−1)
x·y
= 0,
where x · y = x
1
y
1
+ x
2
y
2
+···+x
n
y
n
is the binary scalar product.
24.7 (M): Given the parity-check matrix of the C = (7, 4) Hamming code,
˜
H =
0001111
0110011
1010101
,
determine the codewords of the corresponding C
⊥
= (7, 3) dual code, as gener-
ated by the matrix
ˆ
G =
˜
H
T
.
Then determine the two codewords |
0, |
1 of the CSS(C, C
⊥
) code.

25 Classical and quantum cryptography
This final chapter concerns cryptography, the principle of securing information against
access or tampering by third parties. Classical cryptography refers to the manipulation
of classical bits for this purpose, while quantum cryptography can be viewed as doing
the same with qubits. I describe these two approaches in the same chapter, as in my view
the field of cryptography should be understood as a whole and appreciated within such
a broader framework, as opposed to focusing on the specific applications offered by
the quantum approach. I, thus, begin by introducing the notions of message encryption,
message decryption, and code breaking, the action of retrieving the message information
contents without knowledge of the code’s secret algorithm or secret key. I then consider
the basic algorithms to achieve encryption and decryption with binary numbers, which
leads to the early IBM concept of the Lucifer cryptosystem, which is the ancestor of
the first data encryption standard (DES). The principle of double-key encryption, which
alleviates the problem of key exchange, is first considered as an elegant solution but
it is unsafe against code-breaking. Then the revolutionary principles of cryptography
without key exchange and public-key cryptography (PKC) are considered, the latter also
being known as RSA. The PKC–RSA cryptosystem is based on the extreme difficulty
of factorizing large numbers. This is the reason for the description made earlier in
Chapter 20 concerning Shor’s factorization algorithm. Here, the discussion is expanded
to qualify the difficulty of the factorization problem by classical computing means, with a
detailed analysis of the time and memory requirements, yielding predictions for solving
the various RSA challenges. I then briefly describe DES with its double- and triple-
implementation variants (2DES, 3DES), and the innovative features of the advanced
encryption standard (AES). Then follows a discussion of the other applications of
modern cryptography, including signature and authentication, which are based on the
principle of one-way encryption or hashing. I then move to quantum cryptography, which
is now placed in the global context of communication security, rather than addressed as
a separate field.
Quantum cryptography is widely believed to provide “provably secure” means to
exchange information, based on fundamental quantum-mechanics principles. This is the
introductory concept of secure communication channel. As we shall see in this chapter,
the concept boils down to that of quantum key distribution (QKD), solving the age-long
issue of key exchange, without interception risks, as an absolute, “quantum” competitor
to PKC–RSA. I then describe the three hero protocols, referred to as BB84, B92, and
EPR protocols for QKD. As it turns out, and contrary to widespread belief, none of

524 Classical and quantum cryptography
these protocols is provably safe unless extra security steps are implemented. Indeed,
classical-coding means, “esoterically” referred to as information reconciliation, privacy
amplification,orsecret key distillation (SKD), are necessary to achieve “ultimate”
(albeit exponential) security confidence in the protocol. The closing section discusses
the eventual vulnerability of quantum cryptosystems, when replaced in the realistic
network environment, with its various forms of attack. The conclusion is that assuming
all attacks are possible (as opposed to sheltering under “postulates” that these remain
out of the picture), quantum cryptography represents just another, albeit very elegant,
technique for key exchange. Despite its exponential degree of safety, QKD must be
situated within the grander domain of global network security, where there cannot be
“absolute” confidence in any cryptosystem.
25.1 Message encryption, decryption, and code breaking
This section reviews the elementary basics of cryptography principles, definitions, and
jargon.
There exist several instances where some private, confidential, sensitive, or even
classified information must be conveyed through a communication channel. Examples
abound, from online tax declaration and business reports on company’s intranets to
military and government communications. The driving concept for protecting such
contents is cryptography, which comes from the Greek kryptos (secret) and graphein
(writing). Thus, cryptography is the art of transforming a message into a self-contained
secret, while ensuring a practical technique for the destinee to retrieve the information
contents.
The action of encryption is to transform an original text, or plaintext,intoaciphertext.
Nowadays, “plaintexts” are raw computer data, namely blocks of bits, but the spirit is
exactly similar. The word cipher refers to the coding algorithm or method of encryption.
An equivalent, fancier, definition of cipher is cryptosystem. The reverse operation, i.e.,
resolving a ciphertext into the original plaintext, is called decryption. Decryption is
based on the principle of a secret key. Throughout cryptographic history, the secret key
could have been any method of encryption and decryption based on correspondence
tables, squares,orgrids, kept secret between the corresponding parties. Alternatively,
the secret key could have been a codeword (named keyword), usually simple to pass on
and memorize, but more or less difficult to guess. Nowadays, full and public knowledge
of the algorithm used in cryptographic standards poses no threat whatsoever to security.
Rather, secrecy is based entirely on the secret key, its type, length, means of exchange,
and rapid renewal (the last two points to be addressed later).
A third party who may try to make sense of a ciphertext without the key must resolve
the enigma through more or less extensive labor. Such a task is referred to as cryptoanal-
ysis (or, for short, cryptoanalysis). The goal of cryptanalysis, also called code breaking,
is to “break” the cipher or ciphertext (familiarly called “code”), meaning recovering
the plaintext by practical, inexpensive, hopefully rapid, and effortless methods. Note

25.1 Message encryption, decryption, and code breaking 525
that code breaking should not be confused with the nobler, academic notion of code
cracking.
1
In any case, the task of trying either to “break” or “crack” a code is referred
to as an attack, giving a military flavor. Codes may be attacked either by sophisti-
cated cryptanalysis algorithms or, more directly, by sheer “brute force” (hence the name
brute-force attack in crypto jargon). This latter approach refers to various techniques of
guessing keys at random, exploring what is referred to as the keyspace. For an N -bit
key size, the keyspace corresponds to 2
N
possibilities. In code breaking, rapidity of
execution is essential, because the plaintext is generally not only content-sensitive but
also time-sensitive. This is the reason why successive generations of cryptosystems and
key sizes have been designed to make it virtually impossible to a third party, even a
state with powerful cryptanalysis and computing means, to break them. With a key size
of N = 64 bits, the keyspace is 2
64
= 10
64 log 2/ log 10
= 1.8 × 10
19
. At a rate of trying
out one billion keys per second, a brute-force attack would, thus, require 1.8 ×10
10
seconds, or some 570 years to explore the full keyspace! Clearly, each extra bit of key
size doubles the number of key possibilities. Nowadays, some cryptosystems may use
key sizes as large as N = 512 bits or N = 1024 bits, corresponding to huge keyspaces
of 10
154
and 10
308
, respectively. However, one should not conclude that cryptosystems
become absolutely safe against attacks when the key size is sufficiently large. This sub-
ject being beyond the scope of this chapter, suffice it to state here that one should not
underestimate the power of cryptanalysis, and also that the generation of truly random
keys is not technically simple. If a code breaker can guess the algorithm used to generate
the random keys, his or her task is simplified. But the most straightforward approach
is to intercept the key itself, at the time the communicating parties are doing what is
referred to as the key exchange.
Indeed, the weakness of cryptography lies in the fact that, in order to work, the secret
key must be communicated one way or another to the recipient. Such an exchange is
not without risk of interception, no matter how rapid and periodically changing. Clearly,
the worst situation is to be confident in the safety of a cryptosystem, while the channel
used to exchange the keys is in fact being wired! As a matter of fact, cryptography faces
a double security problem: transmitting the secret key without any measurable risk of
interception, and remaining virtually invulnerable to cryptanalysis.
The history of cryptography, or cryptology, represents a succession of increasingly
sophisticated cryptoalgorithms, which have invariably been broken at some point by
sheer cryptanalysis.
2
Most ancient and pre-computer-era algorithms have been based
1
Theconceptofcode cracking is somewhat different. It could be defined as breaking a code for the first
time. Put simply, code crackers are “champion” code breakers. The goal of code crackers is not so much
to retrieve secret messages (for which they usually cannot care less) as to prove to history that they have
been able to “crack” a previously reputed “invulnerable” or “unbreakable” cipher. Code cracking may be
viewed as a noble academic attempt to explore the limits of cryptosystem security, with a view to improve
the algorithms, or just as an engineering challenge to test security and standards.
2
For fascinating accounts of cryptology, from ancient to modern times, see, for instance: D. Kahn, The
Code Breakers (New York: Scribner, 1967); S. Singh, The Code Book (New York: Anchor Books, 1999);
S. Levy, Crypto, (New York: Penguin Books, 2001).

526 Classical and quantum cr yptography
on the principle of alphabetic substitution.
3
We may simplistically view any alphabetic-
substitution code as representing a one-to-one table correspondence between plaintext
and ciphertext letter symbols. There exist 26! possible permutations between the 26
letters, namely 26! = 1 × 2 × 3 × ... × 25 × 26 = 4.0 × 10
26
. Assuming that each
code possibility could be checked every second, breaking the code would take some
13 billion billion years, i.e., about one billion times the age of our Universe! And with
a rate of one billion checks per second, we still have the age of the Universe. Hence
brute-force attack is not a code-breaking solution. Older cryptanalysis would, rather,
attempt to guess which table, square, or grid algorithm and keys were used, based on
the fact that human beings at the time needed to keep the encryption and decryption
process simple and practical (as done by paper and pencil!), and the secret keys easy
to memorize. No matter how sophisticated, however, with mainframe computer power,
such alphabetic-substitution codes may now be broken in milliseconds or seconds. This
is because all possible algorithms and table, square, or grid combinations of past history
can be systematically explored, and also mainly because the keyword sizes remain
relatively small. Overall, cryptanalysis is facilitated by the detection of frequencies,
the repeated occurrences of certain ciphertext symbols and associations. The frequency
properties of the English language were described in Chapter 9. We have seen that the
two most likely letter associations are TH and HE, making THE the most likely three-
letter word in English. Thus, any frequent two-symbol or three-symbol occurrence in a
ciphertext is likely to correspond to these plaintext letter associations. I n cryptography
jargon, the word fragments, identified are called cribs. Based on a few cribs, the rest of
the guess can progress very fast, should the context of the message (most likely words,
e.g., in wartime) also be known to the code breaker. Frequency analysis and identification
of cribs are basically the spirit of cryptanalysis as far as ancient (alphabetic-substitution)
cryptosystems are concerned.
Cryptography is over 2000 years old. The ingenuity and skills that were deployed
through the ages to conceive and then break ever-complex ciphers are both phenom-
enal and mind boggling. It is beyond the scope of this chapter to make even a brief
survey of cipher development. I shall just mention here the intriguing Enigma machine,
which was used by the German army during World War II.
4
It represented a major
turn in the history of cryptography, not solely because it was the first “cryptographic
computer,” but because of its highly sophisticated encryption and decryption algorithm.
Probably one had never believed so much in cryptosystem invulnerability! The Enigma
cipher used only 26 typewriter characters with a three-rotor system, yielding as many
as 10 586 916 764 424 000 or 10 million billion (or 10 peta) polyalphabetic substitution
3
For a detailed and illustrated review of historical alphabetic-substitution algorithms, see, for instance, my
previous work: E. Desur vire, Wiley Survival Guide in Global Telecommunications, Broadband Access,
Optical Components and Networks, and Cryptography (New York: J. Wiley & Sons, 2004), Ch. 3,
pp. 345–477.
4
There exist many excellent websites dedicated to the Enigma machine, see for instance:
http://en.wikipedia.org/wiki/Enigma
machine,
www.codesandciphers.org.uk/enigma/index.htm,
www.mlb.co.jp/linux/science/genigma/enigma-referat/enigma-referat.html,
www.enigmahistory.org/simulators.html.
