Desurvire E. Classical and Quantum Information Theory: An Introduction for the Telecom Scientist
Подождите немного. Документ загружается.


25.5 Public-key cryptography and RSA 537
But what about n = 15 773 077? The answer (p = 2383, q = 6619) is less immediate,
since it takes 200 division tests to find q in this first-thousand-prime list, but this is still
within reach of a home computer having this list as a database. Assume next that we
select ( p, q) from a huge list of known primes, for instance up to 10
9
, yielding numbers
of the order of 10
18
. Even at a rate of 10
9
division tests per second (a computing power
that only a few states are able to afford), this would take about 10
9
seconds or 31.7 years
to check!
With large PKC and RSA key sizes (e.g., n ≈ 2
64
≈ 10
19
, n ≈ 2
128
≈ 10
38
), the prob-
lem of factorization is no longer within easy reach, and rather requires both extended
computing facilities and time effort. To promote the advancement and security of cryp-
tography, the company RSA Security offers challenges to the public, which take the form
of huge modulus numbers to factorize (namely, given n, find the two primes p and q
such that n = pq).
7
The current challenges concern different numbers with lengths from
704 to 2048 bits. Here is the RSA-2048 number, which has 617 decimal digits:
8
2519590847565789349402718324004839857142928212620403202777713783604366202070
7595556264018525880784406918290641249515082189298559149176184502808489120072
84499268739280728777673597141834727026189637501497182469116507761337985909570
00973304597488084284017974291006424586918171951187461215151726546322822168699
8754918242243363725908514186546204357679842338718477444792073993423658482382
42811981638150106748104516603773060562016196762561338441436038339044149526344
32190114657544454178424020924616515723350778707749817125772467962926386356373
28991215483143816789988504044536402352738195137863656439121201039712282
2120720357
Two of the earlier challenges, named RSA-140 (140 decimal digits, 465 bits) and
RSA-155 (155 decimal digits, 512 bits), were successfully met by inter national teams of
researchers from both academy and industry in February and August 1999, respectively.
Note that RSA-155 was renamed RSA-512 so that the number defines bit size rather
than decimal-digit size.
Factorizing RSA-140 required 125 workstations (175 MHz) and 60 personal comput-
ers (300 MHz) to r un for about one month, a combined 8.9 years of CPU time.
Including the preparation work, the total elapsed time was actually 2.2 months.
Factorizing RSA-512 (previously RSA-155) required 160 workstations (175–400
MHz) and 120 personal computers (300–450 MHz) to r un for 3.7 months, repre-
senting a combined 35.7 years of CPU time. The total elapsed time was about 7.4
months.
The two latest challenges, which were successfully met in 2003 and 2005, concerned
RSA-576 and RSA-640, respectively. The latter took a combined 30 CPU years, repre-
senting 5 months of elapsed time at a 2.2 GHz computing rate per machine! As for the
RSA-2048, it may remain unchallenged not only in this current decade (2008–2020),
but possibly over this century, as the estimates below illustrate.
7
See: www.rsa.com/rsalabs/node.asp?id=2093.
8
Exact reproduction in the printed form of this book is not guaranteed.

538 Classical and quantum cr yptography
The general method of “attack” for the factorization problem (and also finding log-
arithms A from a = m
A
mod n) is known as GNFS (general number field sieve), or
NFS. The word “sieve” comes from Erathosthenes (240 BC). This is the same person
who estimated the circumference of the Earth (tens of centuries before the Earth was
proven to be a sphere), based on the observation that, at the same time of year, the
sun casts shadows with different angles for different latitudes. His nonintuitive “sieving
algorithm” for sorting out prime numbers can be described as follows: “List all integers
less than n and remove multiples of all primes less than or equal to the square root of n;
the numbers that are left are the primes below n.” The NFS algorithm is implemented
in two stages.
9
The first stage, called “sieving,” requires moderate computation power
(hence, the use of multiple personal computers and workstations in parallel), and leads to
a set of equations referred to as the “matrix.” The second stage requires a supercomputer
with massive internal CPU-memory use (e.g., 0.8 Mbytes for RSA-140 and 3.2 Gbytes
for RSA-155–RSA-512). Finding the solution of the matrix might take as much time as
the sieving stage, or just a fraction thereof. Once found, this solution leads to instant fac-
torization or logarithm definition. The two parameters of interest f or attacking a number
n (as defined by its bit length, also referred to as “field size”) are the requirements in
time (L) and memory space (S). It can be shown that these requirements are defined by
L(n) = exp
C ×
(
log n
)
1
3
(
log log n
)
2
3
, (25.1)
S(n) =
L(n), (25.2)
where C is a constant. Knowing these requirements for a smaller number n
, we get the
relative estimates
l
n/n
=
L(n)
L(n
)
= exp
const ×
(
log n
)
1
3
(
log log n
)
2
3
−
(
log n
)
1
3
(
log log n
)
2
3
, (25.3)
s
s/n
=
S(n)
S(n
)
=
L(n)
L(n
)
. (25.4)
Table 25.6 provides the numbers (l
n/n
, s
n/n
) corresponding to the different values of
(n, n
). The first row corresponds to the data provided by RSA,
10
i.e., where estimates
are relative to n
= 512. Analyzing these data, the constant C involved in the definition
in Eq. (25.1) is observed to follow a heuristic r ule C = 64.11 × (n/n
)
0.2542
. We can
use this rule to compute other estimates with n
= 576, 640, 704, 768, 1024, and 2048.
The new dataset we, thus, obtain heuristically provides some estimates for the time
and memory size increase factors required to reach larger-number sizes from the best
previous achievement. We, thus, see from the table that the time increase from RSA-
512 to RSA-576 represents about an 11-fold factor, corresponding to a raw computing
time of 11 × 7.4 months = 81.4 months, or 6 years and 9 months! But if about 1000
9
See RSA Bulletin 13 (2000), www.rsa.com/rsalabs/node.asp?id=2088.
10
See RSA Bulletin 13 (2000), www.rsa.com/rsalabs/node.asp?id=2088.

25.5 Public-key cryptography and RSA 539
Table 25.6 Relative time and memory space increases for factoring number n or solving a logarithm
problem of same field size (top row) in reference to the corresponding data for smaller number n
(left
columns). The numbers are expressed in bit size.
Time increase Memory-space increase
576 640 704 768 1024 2048 576 640 704 768 1024 2048
512 10.9 101 835 6000 7×10
6
9×10
15
3.3 10 29 77 2650 9×10
7
576 1.1 8.2 390 3×10
5
2×10
14
2.8 7.7 20 550 1×10
7
640 6.5 39 3×10
10
3×10
12
2.5 6 2×10
5
2×10
6
704 5.5 2400 1×10
11
2.5 50 4×10
5
768 335 9×10
9
20 9×10
4
1024 3×10
6
1750
workstations and personal computers were used along with (say) five supercomputers,
this delay could be reduced to a single year. The corresponding increase factor for
the CPU memory space is 3.3, corresponding to 3.3 × 3.2 Gbytes = 10.5 Gbytes.
Consider now that RSA-576 was solved in 2003. We see from our estimates that to
reach the ballpark of RSA-768, the time and memory-space requirements are increased
by about 400-fold and 20-fold, respectively. With the conventional approach, this would
require some 400 000 workstations and 100 supercomputers. As far as RSA-1024 and
RSA-2048 are concerned, it is hard to make any sense of the projections in both time
and memory space!
Another way to analyze time projections for the factorization or logarithm prob-
lem is to consider the progress actually realized over the last 30 years. Remarkably,
the progress in key size and time is very closely linear, like another Moore’s law. Note,
however, that Moore’s law is linear but in a logarithmic performance scale, unlike in the
present case. From the aforementioned reference, the law can be expressed using the
phenomenological formula
size
dec
= 4.23 ×
(
Y − 1970
)
+ 23, (25.5)
where Y is the current year and the modulus size is expressed in the number of decimal
digits. This linear law has been verified over the past 30 years. The projected years for
solving 1024-bit keys (309 decimal digits) and 2048-bit keys (617 decimal digits) are
2037 and 2110, respectively. Other investigators have suggested a model, according to
which the size should be dictated by a cubic law
size
dec
=
Y − 1928
13.25
3
, (25.6)
which gives the years 2017 or 2018 for reaching 1024-bit keys, and 2041 for reaching
2048-bit keys. We see that both laws predict that 1024-bit keys won’t be solved before
20 years at the very least. Keys as large as 2048 bits might take 40 years (2040) or
over a century (2110). It is important to note that such estimates are only based on
publicly available data. Throughout history, it has always been assumed that government

540 Classical and quantum cr yptography
agencies have always been ahead of any progress in this field, and the market implications
of cryptography do not exclude the possibility that private, yet unpublicized, efforts,
have already reached substantially higher performance. One final remark: there is no
mathematical proof that breaking RSA absolutely requires factorization of the modulus
n, it is just what is currently conjectured, until new breakthroughs may happen. But even
this remark represents a conjecture by itself.
The above facts, data, and estimates help one to grasp (at the very least) what the
problem of factorization of large numbers (or finding logarithms) mean in terms of
resource, time, and effort. The fact that teams were able to complete the factorization of
RSA-140 and RSA-155/512 does not mean that the RSA cryptosystem is now broken
or “cracked.” Instead, these successful experiments provided valuable information on
the state of the art in factorization, from algorithms and methods to hardware and time
requirements. It is still safe for Alice and Bob to use 512-bit RSA keys (even more so with
1024-bit keys), knowing the costs in personnel, capital investment, and time that Eve
would have to support. Another important consideration is the lifetime of the data to be
protected. This lifetime can range from the scale of a single day (e.g., certified signature,
restricted-access broadcast, stock-exchange instructions) to several years (e.g., business
and financial contracts, long-term strategy).
With very large scale integration (VSLI), integ r ated components (IC) technology has
produced chips capable of performing RSA encryption and decryption with various
modulus sizes (namely 32, 120, 256, 272, 298, 512, 593, 1024). Compared with DES
(see the next section), RSA is 1000 times slower from the hardware perspective. From
the software perspective, RSA is only 100 times slower. Encryption is always faster
than decryption. Using a workstation, the encryption and decryption tasks require 30
ms and 160 ms, respectively, for 512 bits and 80 ms and 930 ms for 1024 bits.
11
The
process can be speeded up by an appropriate choice of public key. Appropriate values
are those which have binary words of value 2
N
+ 1, which in binary have the form
(100 . . . 01) with N + 1 bits and only two 1 bits. This choice reduces the operation of
exponentiation to only N + 1 successive multiplications. Referring back to the PKC
parameters introduced in Section 20.7, the standard recommendations are e = 3(11),
e = 17(10001), and e = 65537(100001). Such a selection avoids e = 5(101) and e =
9(1001) because of the fact that the public key must be relatively prime with φ. And as it
nicely turns out, the numbers 3, 17, and 64 537 are all primes, therefore, more likely to
be relatively prime with φ. To complicate Eve’s task, the recommendation is also that the
private key be sufficiently large and that the choice of modulus be broad (“sufficiently”
and “broad” being here left to professional appreciation). It is not recommended to
use the same private key for encrypted signature and authentication. It can be shown
that malicious Eve can retrieve Alice’s private key by sending her a specially prepared
document and asking her candidly to sign or certify it with her private key! Several
variants and extensions of PKC and asymmetric-key cryptography can be also found in
the footnote reference.
11
See B. Schneir, Applied Cryptography, 3rd edn. (New York: John Wiley and Sons, 1996).

25.6 Data encryption standard (DES) and advanced encryption standard (AES) 541
25.6 Data encryption standard (DES) and advanced encryption standard (AES)
The previous sections have introduced the reader to some aspects of cryptography
standardization, which concern the encryption and decryption algorithms as well as the
formats to be used for keys and ciphers. In this section, I shall briefly describe two
leading standard cryptosystems, referred to as DES (data encryption standard) and AES
(advanced encryption standard).
As we have seen, the story began in the 1960s under IBM’s Lucifer initiative, which
set the grounds for the adoption, in the 1970s, of DES. The initial DES version had a
56-bit key, a reduction from the proposed 128-bit format, which was meant to facili-
tate cracking the code should government authorities need access for national-security
reasons. Rumors have circulated about the existence in DES of embedded trapdoor
functions, which could enable direct decryption by state-class par ties, but such rumors
did not prevent its eventual standardization and widespread adoption. At the time, it was
considered that cracking DES by brute-force attack, i.e., trying all possible keys at ran-
dom over the entire 2
56
− 1 keyspace, would require about 1000 years of CPU time. The
rapid progress in computer speed proved this belief utterly wrong. In 1997, the company
RSA Security issued a public challenge to crack DES. The challenge was successfully
met that same year after only 96 days of computation, using a network of no less than
14 000 computers. In the two following years, other teams succeeded in cracking DES
in 41 days, then in 56 hours, then in 22 hours and 15 minutes! The machine used for the
56-hour record, nicknamed Deep Crack, used 27 parallel motherboards, each one with
64 processor chips (1728 total) capable altogether of performing 90 billion key tests per
second.
The simple way to improve DES strength and security was t o achieve double and triple
encryption with two and three independent secret keys, respectively. These double-
DES (2DES) and triple-DES (3DES) approaches, which bring the effective key size
to 2 × 56 = 112 bits and 3 × 56 = 168 bits, respectively, were endorsed in 1999 by
NIST (National Institute of Standards and Technologies), the new name of the original
standardization body that launched DES.
12
In 2DES, the DES algorithm is implemented just twice in a row with two independent
secret keys, which brings the effective key length to 56 + 56 = 112. Note that doubling
the key length squares the complexity (the size of the keyspace), namely, (2
56
)
2
= 2
112
=
10
33.7
≈ 5 × 10
33
. Thus, Deep Crack, which is able to check out 10
9
keys per second
would now require 5 × 10
24
seconds of CPU time, corresponding to 1 × 10
17
years or
about 15 centuries! Even after an improbable increase of CPU power by one billionfold,
this brute-force attack would require 1 × 10
8
years or four centuries! But Diffie and
Hellman once proved that the effective number of keys is not given by the above figures;
the 2DES keyspace is merely doubled, namely 2
57
, which does not increase safety so
much with respect to standard DES.
12
Note that DES was also approved by ANSI (American Standards Institute) under the name of data encryption
algorithm (DEA) and by ISO (International Standards Organization) under the name of DEA-1.

542 Classical and quantum cr yptography
In 3DES, three independent secret keys are used; one can simply iterate DES with
three keys. A different approach, referred to by ANSI as TDEA (triple data encryp-
tion algorithm) is to use a combination of encryption and decryption with the three
keys: if K
1
, K
2
, K
3
are the three keys and E
K
and D
K
the encryption and decryp-
tion functions with a given key K , the cipher C and message M are defined by
C = E
K 3
{
D
K 2
[
E
K 1
(
M
)
]
}
and M = D
K 1
{
E
K 2
[
D
K 3
(
C
)
]
}
, respectively. With 3DES,
the complexity is really a whopping 2
112
.
In spite of the improvements introduced by double and triple encryption, DES further
evolved into the advanced encryption standard (AES), with the prospect of lasting use
in future decades. It is beyond the scope of this chapter to enter into the algorithmic
features of DES and AES. For a rapid but detailed introduction of the DEA and AES,
see, for instance, my earlier publication.
13
However, it is worthwhile highlighting here
some of the innovating features of AES. Basically, AES is a symmetric encryption
algorithm using blocks of 128 bit (twice the size of DES), and key sizes of 128, 192 or
256 bits (twice or four times the 64-bit DES key size). The ground-breaking innovation
in AES is the introduction of byte-to-byte multiplication, which comes as a supplemental
operation resource to the Boolean XOR addition of previous DES. For the bytes to keep
a constant size under multiplication, the operation requires the bytes to be expressed
in a polynomial representation, and the multiplication to be performed modulo some
irreducible polynomial. Although we will not have any use of polynomial multiplication
in this chapter, its principle is described in Appendix Y, for the sake of education and
also for the curious or demanding. The AES algorithm is completed by various stages
of mingling together the plaintext and key “sub-bytes,” shifting the result by rows and
columns, and effecting complex permutations thereof through an “S-box” look-up table.
Cryptanalysts have shown that with a 256-bit key, AES has a complexity of 2
100
(and
not 2
256
), which comes close, so to speak, to that of 3DES, which is about three orders
of magnitude greater (2
112
).
As a concluding statement, it should be stressed herewith that cryptography is hardly
limited to encryption, decryption and key exchange protocols. Indeed, to communicate
messages safely through any of the above-described cryptosystems is not all that mat-
ters in real cryptospace. There exists a broad catalog of other severe issues and more
immediate threats, which academics focusing on quantum alter natives generally tend
to overlook, while these represent far more serious exposures to attacks, even at basic
network layers. For instance, how can Bob be confident that Alice is the real Alice, and
the reverse? How are they confident that their messages, as received, are the ones they
intended to share? This is the realm of digital signatures and message authentication.
As the name indicates, a digital s ignature is a way of certifying, within reasonable
confidence, that the message originator Alice is really the person claimed, or that her
signature is technically unforgeable. Authentication is different. It ensures that nothing
in the message was altered, even to the level of a single punctuation mark. This protec-
tion is important in all matters per taining to official records, such as titles, patents, or
13
E. Desurvire, Wiley Survival Guide in Global Telecommunications, Broadband Access, Optical Components
and Networks, and Cryptography (New York: John Wiley and Sons, 2004), Ch. 3, pp. 345–477.

25.7 Quantum cryptography 543
tax declarations (contents and time stamping), contracts, authorizations, and confidential
orders, for instance. The key to these processes is the use of hash functions, which can be
viewed as one-way encryption. For short, and to convey a flavor, a 10 000-page plaintext
book can be “hashed” into a 512-bit signature (the “hash”). The same plaintext with a
single comma being altered would yield a fully different hash, immediately betraying
any forgery. The hashing algorithm also makes it extremely difficult for Eve to forge a
plaintext while yielding the same hash (referred to as hash attack). For a basic introduc-
tion to PKC-based signature, authentication, and hash algorithms, s ee my earlier book.
14
As also outlined in the reference, there exist many futuristic applications of cryptogra-
phy, which are likely to mark the next generations, starting with present times: certified
email, anonymous digital cash, simultaneous secret exchange, and contract signature
and global electronic polling or voting, to quote a few. Such not-so-distant applications
of cryptography are only a hint of the vastness and complexity of the subject, especially
when it comes to the border of individual rights and privacy protection issues. It would
be naive to trust that rights and privacy would be better protected if under the full control
of computing systems. The two examples of electronic voting and digital cash point to
future controversies and new f orms of potential abuse. A so-called perfect electronic
voting or digital cash system could be hacked, causing the nullity of elections or cash
transactions, and putting democracy and private rights at an unprecedented level of risk.
And this observation remains true and accurate despite any means of “provably secure”
transmission of data!
Quantum cryptography, to be described in the next section, should, therefore, be
addressed within the full scope of communications security and its applications, a
field that relies essentially on classical cryptoalgorithms. While quantum cryptography
represents a true revolution in the field, it only solves some of the many issues faced
by communications security. This is the correct perception I seek to convey here by
having made this chapter a comprehensive description of cryptography from classical to
quantum, rather than exclusively f ocusing on the second, which would have missed the
global application context.
25.7 Quantum cryptography
In this section, and the following ones, we shall venture into the intriguing and tricky
subject of quantum cryptography (QC). After having reviewed the vast array of possi-
bilities offered by classical cryptosystems (DES, AES, PKC) and being convinced that
a would-be “Eve” would face extreme difficulties in code-breaking attempts, we may
first wonder about or challenge the usefulness of QC approaches. It is possible to answer
such a question straight away. First, from any current knowledge, it must be stated that
QC is not a means of encrypting and decrypting information; rather, it is a means of
distributing secret keys over a public channel; moreover, such an approach, referred to
14
E. Desurvire, Wiley Survival Guide in Global Telecommunications, Broadband Access, Optical Components
and Networks, and Cryptography (New York: John Wiley and Sons, 2004), Ch. 3, pp. 345–477.

544 Classical and quantum cr yptography
as “quantum key distribution” (QKD), is provably, absolutely secure according to the
laws of quantum mechanics.
The above important statements will serve as a conceptual background for the fol-
lowing description of QC and QKD and avoid raising other expectations. Here, we
shall not venture into the debate of assessing whether or not absolute security (vs. that
offered by PKC, for instance) is at all required in any secret-key exchange, or its impact
on global communications security. The purpose of this chapter is only to convey the
principle of how QKD works and not to try measuring the pros and cons of the approach
from industrial and realistic network-environment standpoints. This being said, provable
absolute security in the process of key exchange may only be seen as a desirable “extra”
feature, especially if proven practical to implement and compatible with higher-layer
network standards. The main difficulty is that academics involved in PKC may fail to
recognize several other forms of network-security threats, particularly at the level of
Alice and Bob, who just manipulate classical bits at a bottom network-layer level. The
main argumentation in favor of PKC is the impossibility of Eve’s capturing the secret
key without Alice’s and Bob’s awareness, and this is true as long as Eve’s attack only
concerns the quantum channel over which the key is exchanged. It is assumed that Alice’s
and Bob’s computers and local networks cannot be approached by Eve and be physically
tapped, including by wireless means. This is the main assumption to keep in mind while
discovering the extraordinary elegance of QKD and accepting the “absoluteness” of its
security.
In the forthcoming sections, we shall consider several QKD approaches, referred to
as QKD protocols. Since QKD is about key exchange, the quantum channel must be a
communication channel involving physical distance. Thus, its implementation requires
one to use light and its quantum constituents, photons. It is important, therefore, to
describe beforehand the properties of electromagnetic waves and the associated quantum
measurements, which are both at the root of QKD. In the description, I shall also develop
the necessary parallels with QIT and qubit and operator formalism.
25.8 Electromagnetic waves, polarization states, photons, and quantum
measurements
In this section, we review the basic physical properties of light, and how these proper ties
can be conceptually, and quite nicely, related to that of quantum states.
The elementary particles of light, or equivalently, light energy quanta, are called
photons. The particle-like characteristics of light only appear at relatively low light
powers, where the number of quanta approaches the order of unity.
15
At macroscopic
scales, with large numbers of quanta, such photon granularity vanishes, and light appears
to the physical observer in the form of an electromagnetic (EM) wave.TheEMwaveis
15
More specifically, the average number of photons nemitted per second (units of photon/s) by a light source
of power P (units of W) at electromagnetic frequency ν (units of Hz or s
−1
)isdefinedasn=P/(hν),
where h = 6.62 × 10
−34
J/s is Planck’s constant.
25.8 Electromagnetic waves, polarization states, photons, and quantum measurements 545
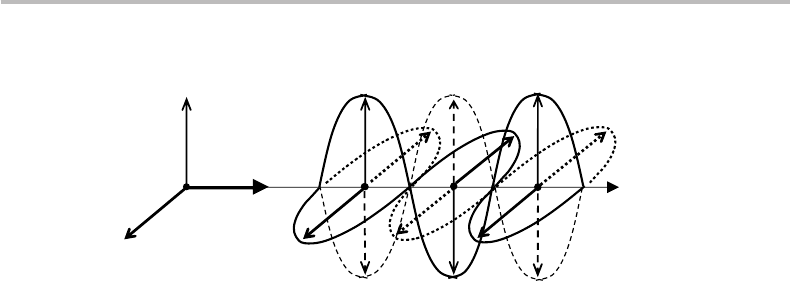
Ray
direction
E
(
t
)
M
(
t
)
Figure 25.2 Electromagnetic wave associated with a light ray, showing electric (E) and magnetic
(M) components oscillating in orthogonal planes
made up of two oscillating field components, one electrical (E) and one magnetic (M),
as illustrated in Fig. 25.2. The two EM field components oscillate in planes orthogonal
to the direction of the EM-wave propagation, which is that of the associated light ray.
The direction pointed to by either the E-field or the M-field oscillation is referred to
as light polarization. When the E-field direction is orthogonal to the ray direction, one
refers to the light beam as being transverse-electric,orTE-polarized. In the other case,
where the M-field is orthogonal to the ray, the light is called transverse-magnetic,or
TM-polarized. When the polarization is either TE or TM, light is said to be linearly
polarized. For short, we can say that linearly polarized light is either vertically (TE) or
horizontally (TM) polarized. As a first hint of quantum mechanics, one refers to the TE
and TM possibilities as polarization states. Consistently, the TE and TM polarization
states are said to be orthogonal. Occasionally, I shall designate the TE and TM states by
the symbols and ↔, respectively.
Linear polarization, in fact, r epresents a special case where the E-field component
oscillates with a constant direction in space, meaning that its oscillation plane is fixed. In
the most general case, we may conceive of the E-field as resulting from the superposition
of two orthogonally polarized components E
1
, E
2
, each one being characterized by its
own phase, ϕ
1
,ϕ
2
. If the two components are in phase (ϕ
1
= ϕ
2
), then the resulting
E-field is linearly polarized. If not (ϕ
1
= ϕ
2
), the resulting E-field direction rotates over
time. To see this more clearly, define an orthonormal basis u
1
, u
2
associated with the
two E-field components. It is then possible to express the resulting E-field in this basis
as a vector with two complex coordinates E
k
e
iϕ
k
, k = 1, 2 according to:
E =
E
1
e
iφ
1
E
2
e
iφ
2
e
iωt
, (25.7)
where ω = 2πν is the oscillation frequency in radian/s. In the case ϕ
1
= ϕ
2
≡ ϕ,we
have from the above definition
E = e
iφ
E
1
E
2
e
iωt
, (25.8)
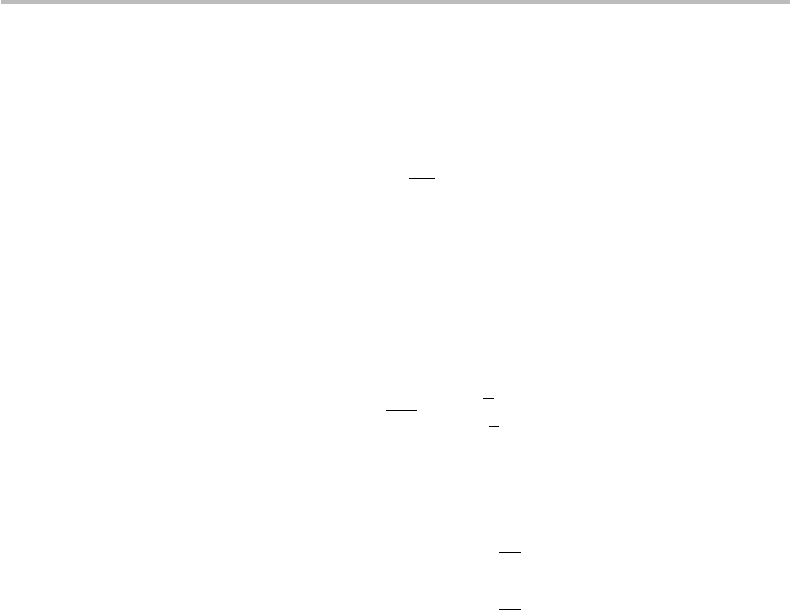
546 Classical and quantum cr yptography
which corresponds to a time-invariant direction, (or oscillation plane) of the E-field.
With the appropriate basis rotation (the choice being conventional), we may also
write
E =
e
iφ
|
E
|
1
0
e
iωt
, (25.9)
which corresponds to a TE-polarized state. Such a representation is immediately rem-
iniscent of a quantum state, namely here the qubit
|
0
from the basis
{
|0,
|
1
}
.We
may, thus, identify the TE polarization state with the quantum state
|
0
. Consistently,
we identify the TM polarization with the quantum state or qubit
|
1
, but with an E-field
relative phase to be determined later on.
Consider next the case ϕ
1
= ϕ
2
or δϕ = ϕ
1
− ϕ
2
= 0. Let us rewrite Eq. (25.7) as
E = e
i
ϕ
1
+ϕ
2
2
E
1
e
i
δϕ
2
E
2
e
−i
δϕ
2
e
iωt
, (25.10)
where we have overlooked the common phase factor e
i(ϕ
1
+ϕ
2
)/2
. Taking the real part of
the E-field, we obtain:
E =
⎡
⎢
⎢
⎣
E
1
cos
ωt +
δϕ
2
E
2
cos
ωt −
δϕ
2
⎤
⎥
⎥
⎦
. (25.11)
The result in Eq. (25.11) shows that the two E-field components alternatively reach maxi-
mal amplitudes at times t = 2nπ −δϕ/(2ω) and t
= 2nπ +δϕ/(2ω), respectively, with
n being an integer. The E-field direction, thus, periodically rotates about the light ray
axis at the frequency ω = 2πν. Consider the special case δϕ = π/2, and for simplicity
assume E
1
= E
2
= 1. From Eq. (25.11), and after basic trigonometry we obtain (within
an arbitrary phase ϕ):
E ≡
cos
(
ωt + ϕ
)
sin
(
ωt + ϕ
)
. (25.12)
The result in Eq. (25.12) shows that the E-field periodically rotates about the ray axis at
the frequency ω = 2πν, the vector end describing a corkscrew-like trajectory. It is easily
established that for an observer looking at an incoming light ray, the E-field appears to
rotate in the clockwise (cw) direction. In the case δϕ =−π/2, we obtain a similar
conclusion, except that the E-field rotates in the counterclockwise (ccw) direction. In
both cases, light is said, therefore, to be circularly polarized. Conventionally, one refers to
the ccw case as representing right-circular polarization and the cw case as representing
left-circular polarization.
16
As in the linear-polarization case, we may view the two
circular polarizations as representing two orthogonal states (orthogonality to be shown
16
This convention is easy to remember when looking at one’s right or left hands, the thumb pointing up and
the fingers bent. With the right hand, the fingers indicate a ccw direction, while with the left hand, they
indicate a cw direction.
