Wilamowski B.M., Irwin J.D. The Industrial Electronics Handbook. Second Edition: Industrial Communication Systems
Подождите немного. Документ загружается.

22-4 Industrial Communication Systems
locked.doors.to.the.shop.oor,.and.locked.cabinets.to.the.control..Figure.22.1.shows.a.three-zone.security.
model.optimized.for.industrial.communication.applications.as.also.introduced.by.[SC2,TR1,KHA1]..
Corresponding.to.the.interconnection.zones.in.the.company.network.three.zones.are.available..e.
inner.eldbus.zone.hosting.the.eld-level.communication.systems.mostly.located.at.the.shop.oor,.the.
intranet.zone.oen.build.upon.IP-based.LANs.inside.the.plant.(it.also.includes.demilitarized.zones.
(DMZs).and.checking.domains.or.inner.security.structures.to.strengthen.the.security),.and.nally.the.
Internet.zone.also.referred.to.as.company.or.entrance.domain.connecting.multiple.plants,.remote.main-
tenance
.sites,.customers,.etc..e.zones.are.separated.from.each.other.by.dedicated.security.measures.
oen.located.at.dedicated.network.nodes.that.can.be.used.as.anchor.points.for.the.security.strategy..
Typical.examples.are.rewalls.between.the.company.and.the.intranet.domain.or.application.gateways.
between.the.intranet.domain.and.the.shop.oor..As.there.is.only.a.limited.number.of.those.network.
nodes.(between.every.couple.of.zones),.it.is.possible.to.use.state-of-the-art.components.in.regard.to.secu-
rity
.without.straining.available.resources.too.much..In.this.way,.a.defense-in-depth.approach.is.installed.
preventing.that.an.adversary.has.access.to.all.zones.and.especially.to.the.most.inner.zone.forming.the.
core.of.production..Additionally,.focusing.most.of.the.eorts.to.those.anchor.points.of.the.network.
infrastructure.avoids.misconguration.that.may.happen.if.the.number.of.security-relevant.nodes.grows.
22.3 Security Measures to Counteract Network attacks
To.counteract.network.attacks,.two.possibilities.exist..First,.unauthorized.access.to.the.network.and.
thus.to.the.data.that.is.transmitted.over.the.network.can.be.avoided..One.approach.is.to.limit.the.physi-
cal
.access.to.the.network.medium.by,.for.example,.immuring.the.network.cable..Obviously,.preventing.
physical.access.is.not.always.possible..Consider,.for.example,.the.use.of.wireless.or.wide.area.networks.
where.public.access.cannot.be.avoided..erefore,.organizational.measures.that.limit.the.logical.access.
can.be.used.instead..Typical.examples.are.the.use.of.virtual.private.networks.(VPNs).(cf..Section.22.3.1).
and.rewalls.(cf..Section.22.3.2).
Second,
.the.transmitted.data.itself.can.be.protected.in.a.way.that.an.adversary.is.not.able.to.mali-
ciously
.interfere.with.it.even.in.cases.where.an.adversary.has.access.to.the.network..According.to.[GR1],.
the.following.security.objectives.can.be.guaranteed:.data condentiality.(against.interception.attacks),.
data integrity and authentication. (against. modication. attacks),. data freshness. (against. fabrication.
attacks),.and.data availability.(against.interruption.attacks)..Depending.on.the.security.requirements.
Shop oor
domain
(eldbus)
Intranet domain
(checking domain, DMZ)
Company or internet domain
(entrance domain)
Security
measure
Security
measure
Security
measure
Inner security structure
Trustworthy
entity
FIGURE 22.1 ree-zone.security.model.
© 2011 by Taylor and Francis Group, LLC
Security in Industrial Communication Systems 22-5
of.the.application,.it.is.not.always.necessary.to.guarantee.all.of.the.security.objectives.mentioned.above..
For.exa
mple,
.if.the.non
disclosure
.of.the.tra
nsmitted
.dat
a
.is.not.a.str
ict
.req
uirement,
.gua
ranteeing
.dat
a
.
int
egrity,
.ava
ilability,
.and.fre
shness
.may.be.su
cient.
.In.gen
eral,
.onl
y
.tho
se
.sec
urity
.mec
hanisms
.tha
t
.
are.abs
olutely
.nec
essary
.to.sat
isfy
.the.sec
urity
.dem
ands
.of.the.app
lication
.sha
ll
.be.imp
lemented
.(go
od
.
eno
ugh
.sec
urity).
.is.is.esp
ecially
.tru
e
.for.embe
dded
.net
works
.tha
t
.con
sist
.of.dev
ices
.wit
h
.lim
ited
.
sys
tem
.res
ources
.tha
t
.are.jus
t
.su
cient
.to.ful
ll
.the.dev
ices’
.tas
ks.
.is.con
cerns
.pri
marily
.pro
cessing
.
pow
er
.(pe
rsistent
.and.vol
atile),
.mem
ory,
.pow
er
.con
sumption,
.and.net
work
.ban
dwidth.
.Sin
ce
.sec
urity
.
mec
hanisms
.are.com
putationally
.int
ensive,
.the.rea
lization
.of.sec
urity
.obje
ctives
.is.a.cri
tical
.desi
gn
.ste
p
.
and.mu
st
.no
t
.ex
ceed
.th
e
.av
ailable
.de
vice
.re
sources.
Guaranteeing
.dat
a
.con
dentiality,
.int
egrity,
.and.fre
shness
.can.be.ach
ieved
.usin
g
.cry
ptographic
.tec
h-
niques
.(cf
.
.Sec
tion
.22.
3.3).
.How
ever,
.cou
nteracting
.int
erruption
.att
acks
.lik
e
.DoS.att
acks
.is.not.pos
-
sible
.usin
g
.a.cry
ptographically
.sec
ured
.dat
a
.tra
nsmission.
.er
efore,
.add
itional
.sec
urity
.mea
sures
.are.
req
uired
.to.gu
arantee
.da
ta
.av
ailability
.(c
f.
.Se
ction
.22
.3.4).
22.3.1 Virtual Private Networks
A.VPN.is.a.logical.secure.network.that.is.built.upon.a.possibly.insecure.network..A.VPN.is.transpar-
ent
.to.the.con
nected
.dev
ices.
.Usu
ally,
.a.dev
ice
.ope
ns
.a.sec
ure
.uni
cast
.con
nection
.to.a.tru
sted
.thi
rd
.
par
ty
.(e.
g.,
.cen
tralized
.VPN.ser
ver)
.whe
re
.the.who
le
.net
work
.tra
c
.to.and.fro
m
.the.dev
ice
.is.tun
neled
.
thr
ough.
.In.ind
ustrial
.sys
tems,
.VPN
s
.are.mos
t
.com
monly
.use
d
.to.con
nect
.eit
her
.two.dis
located
.el
dbus
.
seg
ments
.or.to.con
nect
.rem
ote
.mai
ntenance
.or.con
trol
.cen
ters.
.Sec
tion
.22.
5.3
.des
cribes
.the.ope
n
.VPN.
sol
ution
.an
d
.IP
sec
.ap
plication.
.Ch
apter
.15.is.fu
rther
.de
dicated
.to.Vi
rtual
.Au
tomation
.Ne
tworks.
22.3.2 Firewalls
A.rewall.is.a.network.entity.that.protects.a.trusted.network,.host,.or.service.against.unauthorized.
acc
ess
.by.ins
pecting
.the.inc
oming
.and.out
going
.net
work
.tra
c
.to.dec
ide
.whe
ther
.the.tra
c
.is.all
owed
.
or.not.[PF
L].
.e.dec
ision
.abo
ut
.all
owing
.or.den
ying
.net
work
.tra
c
.is.mad
e
.bas
ed
.on.the.re
wall’s
.
sec
urity
.pol
icy.
.Suc
h
.a.sec
urity
.pol
icy
.com
monly
.con
sists
.of.a.def
ault
.pol
icy
.and.a.set.of.app
lication-
specic
.rul
es
.tha
t
.spe
cify
.exc
eptions
.or.ame
ndments
.to.the.def
ault
.pol
icy.
.Con
sider,
.for.exa
mple,
.a.man
-
agement
.int
erface
.to.an.auto
mation
.con
troller.
.e.def
ault
.pol
icy
.to.tha
t
.int
erface
.may.be.set.to.“DE
NY”
.
whi
le
.a.spe
cic
.rul
e
.may.be.add
ed
.tha
t
.all
ows
.the.sys
tem
.ope
rator’s
.man
agement
.wor
kstation
.to.acc
ess
.
the.int
erface.
.A.sec
urity
.pol
icy
.is.nor
mally
.pre
dened
.acc
ording
.to.the.sys
tem’s
.pol
icy.
.How
ever,
.it.may.
als
o
.be.nec
essary
.to.dyn
amically
.cha
nge
.the.rul
e
.set.of.a.re
wall.
.For.exa
mple,
.if.an.int
rusion
.det
ection
.
sys
tem
.(ID
S)
.(cf
.
.Sec
tion
.22.
3.4)
.ide
nties
.a.mal
icious
.hos
t
.wit
hin
.a.net
work,
.the.IDS.may.add.a.spe
cic
.
rul
e
.to.the.rul
e
.set.of.the.re
wall
.tha
t
.exp
licitly
.dro
ps
.all.tra
c
.ori
ginated
.fro
m
.the.ide
ntied
.mal
icious
.
hos
t
.(d
ynamic
.bl
acklist).
Depending
.on.the.cap
abilities
.pro
vided
.by.the.re
wall,
.thr
ee
.di
erent
.typ
es
.can.be.dis
tinguished:
.
Apac
ket ltering rewall
.is.the.simp
lest
.for
m
.of.re
wall.
.It.use
s
.par
t
.of.the.hea
der
.inf
ormation
.to.dec
ide
.
whe
ther
.a.pa
cket
.sh
all
.be.ac
cepted
.or.dr
opped.
.Fo
r
.ex
ample,
.to.l
ter
.IP.tr
ac,
.th
e
.ad
dress
.in
formation
.
(IP.add
ress,
.UDP
/TCP
.por
t
.numb
er)
.as.wel
l
.as.the.enc
apsulated
.app
lication
.pro
tocol
.typ
e
.(e.
g.,
.HTT
P,
.
FTP
)
.may.be.con
sidered
.for.ide
ntifying
.val
id
.tra
c.
.How
ever,
.the.sta
te
.of.con
nections
.(e.
g.,
.has.the.
con
nection
.alr
eady
.bee
n
.clo
sed?)
.as.wel
l
.as.det
ails
.abo
ut
.the.app
lication
.dat
a
.(e.
g.,
.dis
tinguish
.bet
ween
.
di
erent
.HT
TP
.me
thods)
.ar
e
.no
t
.co
nsidered.
A
.stateful ltering rewall,.on.the.other.hand,.additionally.maintains.the.state.of.a.connection..Using.
thi
s
.ext
ra
.inf
ormation,
.the.re
wall
.is.abl
e
.to.det
ect
.ill
egal
.con
nection
.sta
tes
.and.so.it.is.pos
sible
.to.
spe
cify
.a.mor
e
.adv
anced
.rul
e
.set
.
.For.exa
mple,
.to.avo
id
.uns
olicited
.con
nections
.wit
h
.a.pro
tected
.ent
ity,
.
the.r
ewall
.on
ly
.pe
rmits
.cl
ient
.pa
ckets
.a
er
.a.de
dicated
.co
nnection
.ha
s
.be
en
.es
tablished
.to.th
e
.se
rver.
Finally,
.an.app
lication proxy
.als
o
.insp
ects
.the.app
lication
.dat
a
.of.net
work
.pac
kets.
.To.ful
ly
.ana
lyze
.
the.ee
cts
.of.inc
oming
.and.out
going
.net
work
.pac
kets,
.an.app
lication
.pro
xy
.sim
ulates
.the.beha
vior
.of.the.
© 2011 by Taylor and Francis Group, LLC
22-6 Industrial Communication Systems
entire.application..erefore,.a.proxy.acts.as.a.man-in-the-middle:.to.the.outside.network,.a.proxy.behaves.
like.the.destination.device;.to.the.inside.network,.the.proxy.acts.as.the.request.origin;.and.vice.versa..
Sophisticated.application.proxies.are.completely.transparent.to.the.involved.communication.parties.
Due
.to.the.importance.of.rewalls,.they.have.to.be.reliable.and.robust.against.security.attacks..To.min-
imize
.vulnerabilities,.rewalls.are.oen.isolated,.stand-alone.devices.that.are.kept.as.simple.as.possible..
Furthermore,.access.to.rewalls.is.only.permitted.to.users.with.special.administrator.privileges.(if.at.all).
From
.a.security.point.of.view,.using.a.single.rewall.that.acts.as.a.single.wall.of.protection.may.
not.be.sucient..If.an.adversary.is.able.to.bypass.the.rewall,.he.has.full.access.to.the.entire.network..
erefore,.it.is.more.appropriate.to.separate.the.network.into.several.zones.where.each.zone.is.protected.
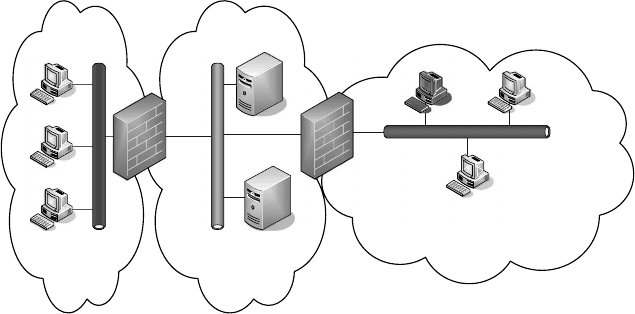
with.a.dedicated.rewall.and.a.corresponding.security.policy..A.typical.example.is.shown.in.Figure.22.2..
Besides.a.separation.between.an.outside.and.an.inside.network,.the.inner.network.is.further.divided.
into.a.local.network.that.is.home.for.the.dierent.client.workstations.and.a.so-called.DMZ..e.rewall.
between.the.outside.network.and.the.DMZ.is.responsible.for.ltering.the.incoming.network.trac.that.
is.intended.for.the.servers.as.well.as.the.client.workstations..However,.to.further.protect.the.clients,.a.
second.rewall.is.located.at.the.boundary.between.the.DMZ.and.the.local.network..is.rewall.is.able.
to.additionally.lter.trac.that.is.irrelevant.for.the.client.workstations.(e.g.,.HTTP.trac.to.the.Web.
server)..e.main.advantage.of.this.second.rewall.is.that.if.a.server.within.the.DMZ.gets.compromised,.
the.second.rewall.acts.as.an.additional.wall.of.protection.between.the.client.workstations.and.the.com-
promised
.server..Finally,.to.further.secure.the.client.workstations.against.compromised.clients,.each.
client.may.have.its.own.personal.rewall.that.provides.an.additional.layer.of.protection.
22.3.3 Cryptography
Cryptographic.algorithms.use.mathematical.techniques.to.guarantee.a.protection.of.data.against.unau-
thorized
.interference.[MEN]..In.industrial.communication.systems,.these.cryptographic.algorithms.
can.be.used.to.secure.data.while.it.is.transmitted.over.a.possible.insecure.network..Depending.on.the.
used.algorithms,.the.following.security.objectives.can.be.guaranteed:
•
. Data condentiality:.To.avoid.an.unauthorized.disclosure.of.condential.data,.the.producer.has.to.
transform.it.in.way.that.unauthorized.entities.are.not.able.to.interpret.the.data’s.meaning.while.it.
is.transmitted.over.the.network..To.achieve.this,.encryption algorithms.can.be.used..e.output.of.
the.encryption.(called.cipher.text).is.transmitted.over.the.network.where.the.consumer.receives.
it..To.retrieve.the.clear-text.version.again,.the.consumer.applies.the.inverse.operation.using.the.
corresponding.decryption algorithm.
Local network
DMZ
Web
server
Mail
server
Outside network
Client
workstations
FIGURE 22.2 Demilitarized.zone.
© 2011 by Taylor and Francis Group, LLC
Security in Industrial Communication Systems 22-7
•. Data integrity:.To.protect.the.transmitted.data.against.unauthorized.modication,.digital signa-
tures
.or.mes
sage authentication codes
.(MA
Cs)
.are.com
monly
.use
d.
.In.bot
h
.cas
es,
.the.pro
ducer
.cal
-
culates
.a.se
cure
.ta
g
.wi
th
.a.xe
d
.le
ngth.
.e.pr
oducer
.tra
nsmits
.it.tog
ether
.wit
h
.th
e
.me
ssage
.ov
er
.
the.net
work.
.e.con
sumer
.ret
rieves
.bot
h,
.cal
culates
.the.sam
e
.sec
ure
.tag
,
.and.ver
ies
.whe
ther
.
the.rec
eived
.tag.cor
responds
.to.the.cal
culated
.one
.
.If.the.ver
ication
.pro
cess
.was.suc
cessful,
.the.
con
sumer
.ha
s
.pr
oved
.th
e
.in
tegrity
.of.th
e
.me
ssage.
•
. Dat
a freshness:
.Dat
a
.fre
shness
.is.gua
ranteed
.by.inc
luding
.a.tim
e-variant
.par
ameter.
.Usu
ally,
.a.
num
ber used only once
.(non
ce)
.is.tak
en
.as.uni
que
.ide
ntier
.(e.
g.,
.ran
dom
.numb
er,
.mon
otonically
.
inc
reasing
.cou
nter,
.tim
e
.sta
mp).
.How
ever,
.to.avo
id
.a.mal
icious
.man
ipulation
.of.the.uni
que
.toke
n
.
dur
ing
.tra
nsmission,
.it.has.to.be.use
d
.in.comb
ination
.wit
h
.an.enc
ryption
.and
/or
.a.MAC.or.dig
ital
.
sign
ature
.al
gorithm.
Today,
.man
y
.di
erent
.cry
ptographic
.alg
orithms
.tha
t
.are.sui
table
.to.gua
rantee
.the.sec
urity
.obje
ctives
.
men
tioned
.abo
ve
.exi
st.
.Mos
t
.of.the
m
.are.bas
ed
.on.the.Ker
ckho’s
.pri
nciple
.([K
ER],
.see.Sec
tion
.22.
2):
.
Whi
le
.the.alg
orithm
.its
elf
.can.be.mad
e
.pub
licly
.ava
ilable,
.only.key.par
ameters
.mus
t
.be.kep
t
.sec
ret
.(se
cret
.
key
s).
.Gen
erally,
.suc
h
.a.cry
ptographic
.alg
orithm
.wor
ks
.as.fol
lows:
.the.pro
ducer
.tha
t
.wan
ts
.to.sec
urely
.
tra
nsmit
.dat
a
.via.an.ins
ecure
.com
munication
.cha
nnel
.(e.
g.,
.pub
lic
.net
work)
.gen
erates
.a.sec
ured
.ver
-
sion
.of.the.unp
rotected
.dat
a
.by.usin
g
.an.alg
orithm,
.sec
ret
.key
s,
.and.som
e
.oth
er
.kin
d
.of.pub
lic
.inp
ut
.
par
ameters.
.e.con
sumer
.on.the.oth
er
.side.of.the.com
munication
.cha
nnel
.rec
eives
.the.sec
ured
.dat
a
.
and.ap
plies
.th
e
.re
verse
.op
eration
.to.re
trieve
.th
e
.pl
ain
.ve
rsion
.of.th
e
.da
ta.
Depending
.on.the.sec
ret
.key
s
.use
d
.at.bot
h
.side
s,
.cry
ptographic
.alg
orithms
.can.be.cla
ssied
.into.sym
-
metric
.and.asy
mmetric
.alg
orithms.
.In.the.cas
e
.of.sym
metric algorithms,
.it.is.rel
atively
.eas
y
.to.der
ive
.the.
sec
ret
.at.the.con
sumer
.site.out.of.the.sec
ret
.on.the.pro
ducer
.site
.
.In.sym
metric
.alg
orithms,
.the.sec
rets
.on.
the.pro
ducer
.and.con
sumer
.site.are.the.sam
e.
.Typ
ical
.exa
mples
.of.sym
metric
.enc
ryption
.alg
orithms
.are.
DES.[DE
S],
.AES.[AE
S],
.Cam
ellia
.[R3
7],
.and.SAF
ER
.[SA
F].
.Pop
ular
.MAC.cal
culation
.alg
orithms
.tha
t
.
use.sy
mmetric
.al
gorithms
.ar
e
.CM
AC
.[R
44]
.an
d
.HM
AC
.[H
MA].
In
.asy
mmetric algorithms
.(al
so
.cal
led
.pub
lic
.key.alg
orithms),
.eac
h
.ent
ity
.has.a.so-
called
.pub
lic/
private
.key.pai
r
.whe
re
.the.pub
lic
.key.is.mad
e
.pub
licly
.ava
ilable
.and.the.priv
ate
.key.is.onl
y
.kno
wn
.to.
the.ent
ity
.its
elf.
.In.the.cas
e
.of.asy
mmetric
.enc
ryption
.alg
orithms,
.the.pub
lic
.key.of.the.con
sumer
.is.
used.to.encrypt.the.data.at.the.producer.site..e.consumer.is.able.to.decrypt.the.data.using.its.private.
key
.
.In.the.cas
e
.of.asy
mmetric
.sig
nature
.cal
culation
.and.ver
ication
.alg
orithms,
.the.prod
ucer
.sig
ns
.
the.tag.of.the.dat
a
.usi
ng
.its.priv
ate
.key.and.the.con
sumer
.is.abl
e
.to.ver
ify
.the.sig
nature
.usi
ng
.the.pub
-
lic
.key.of.the.prod
ucer.
.Asy
mmetric
.alg
orithms
.rel
y
.on.the.fac
t
.tha
t
.it.is.com
putationally
.inf
easible
.
to.der
ive
.the.priv
ate
.key.out.of.the.pub
lic
.key
.
.Pop
ular
.asy
mmetric
.enc
ryption
.alg
orithms
.are.RSA.
[RS
A],
.ElG
amal
.enc
ryption
.sys
tem
.[EL
G],
.and.ell
iptic
.cur
ve
.int
egrated
.enc
ryption
.sch
eme
.(EC
IES)
.
[HA
N].
.Typ
ical
.exa
mples
.of.dig
ital
.sig
nature
.gen
eration
.and.ver
ication
.alg
orithms
.bas
ed
.on.asy
m-
metric
.alg
orithms
.are.the.dig
ital
.sig
nature
.alg
orithm
.(DS
A)
.[DS
S],
.ElG
amal
.sig
nature
.sch
eme
.[EL
G],
.
and.ell
iptic
.cur
ve
.DSA.(EC
DSA)
.[HA
N].
In
.add
ition
.to.sym
metric
.and.asy
mmetric
.alg
orithms
.tha
t
.are.gen
erally
.ref
erred
.to.as.key
ed
.alg
o-
rithms,
.the
re
.are.cry
ptographic
.alg
orithms
.tha
t
.do.not.nee
d
.any.sec
ret
.par
ameters
.at.all
.
.es
e
.so-
called
.
unk
eyed algorithms
.do.not.dir
ectly
.gua
rantee
.any.of.the.sec
urity
.obje
ctives
.men
tioned
.abo
ve.
.Mor
eover,
.
the
y
.are.oe
n
.use
d
.in.comb
ination
.wit
h
.key
ed
.alg
orithms.
.A.typ
ical
.exa
mple
.is.a.cry
ptographic hash
function
.tha
t
.may.be.use
d
.in.comb
ination
.wit
h
.oth
er
.alg
orithms
.to.gua
rantee
.dat
a
.int
egrity.
.A.cry
pto-
graphic
.has
h
.fun
ction
.is.a.com
putationally
.ec
ient
.one
-way
.fun
ction
.tha
t
.map
s
.an.inp
ut
.of.arb
itrary
.
len
gth
.to.an.out
put
.of.xe
d
.len
gth.
.e.mai
n
.pro
perty
.of.suc
h
.a.fun
ction
.is.col
lision
.resi
stance:
.It.is.
computationally.infeasible.to.nd.two.distinct.inputs.that.have.the.same.hash.value.as.output..e.
mos
t
.com
monly
.use
d
.cry
ptographic
.has
h
.fun
ctions
.are.MD5.[R1
3]
.and.fun
ctions
.fro
m
.the.SHA.fam
ily
.
[SH
A].
.Cry
ptographic
.has
h
.fun
ctions
.are.use
d
.to.cal
culate
.the.tag.tha
t
.is.use
d
.in.MAC.and.dig
ital
.sig-
n
atures.
.Oth
er
.exa
mples
.of.unk
eyed
.alg
orithms
.are.pse
udo
.ran
dom bit generators
.whe
re
.the.gen
erated
.
pse
udo
.ra
ndom
.nu
mber
.ma
y
.be.us
ed
.as.no
nces
.to.gu
arantee
.da
ta
.fr
eshness.
© 2011 by Taylor and Francis Group, LLC
22-8 Industrial Communication Systems
22.3.4 DoS Prevention and Detection
Nevertheless,.there.are.security.attacks.that.cannot.be.prevented.using.cryptographic.methods..Typical.
rep
resentatives
.of.suc
h
.att
acks
.are.DoS.att
acks
.tha
t
.thr
eaten
.dat
a
.ava
ilability.
.DoS.att
acks
.can.be.cla
s-
sied
.into.hos
t-based
.and. net
work-based
.DoS.att
acks.
.Hos
t-based DoS attacks
.try. to. was
te
.sys
tem
.
res
ources
.(e.
g.,
.by.con
suming
.pro
cessor
.tim
e
.of.a.ser
ver
.by.sen
ding
.mul
tiple
.req
uests)
.to.pre
vent
.the.
tar
get
.fro
m
.per
forming
.its.exp
ected
.fun
ction.
.Net
work-based DoS attacks,
.on.the.oth
er
.han
d,
.try.to.
int
errupt
.the.com
munication
.in.a.net
work.
.A.com
mon
.exa
mple
.is.an.adv
ersary
.tha
t
.tri
es
.to.con
sume
.
the.net
work
.ban
dwidth
.(e.
g.,
.by.oo
ding
.the.net
work
.wit
h
.uns
olicited
.mes
sages).
.e.situ
ation
.is.fur
-
ther
.ag
gravated
.if.mu
ltiple
.so
urces
.at
tack
.a.sin
gle
.vi
ctim
.(d
istributed
.Do
S
.at
tack).
DoS
.att
acks
.for
emost
.hav
e
.mas
sive
.eco
nomic
.imp
act.
.Con
sider,
.for.exa
mple,
.an.ass
embly
.lin
e
.tha
t
.is.
the.tar
get
.of.a.DoS.att
ack.
.A.shu
tdown
.of.the.lin
e
.lea
ds
.to.an.eco
nomic
.imp
act
.tha
t
.can.be.easi
ly
.com
-
pared
.to.the.imp
act
.of.a.suc
cessful
.att
ack
.on.the.com
pany
.Web.ser
ver.
.e.onl
y
.di
erence
.is.tha
t
.for.the.
Web.se
rver
.el
aborate
.IT.se
curity
.me
asures
.ar
e
.al
ready
.co
mmon
.pr
actice.
To
.cou
nteract
.DoS.att
acks,
.two.pos
sibilities
.exi
st.
.DoS
prevention,
.on.the.one.han
d,
.has.the.aim.to.
lim
it
.the.acc
ess
.to.sys
tem
.res
ources
.in.a.way.tha
t
.an.adv
ersary
.doe
s
.not.hav
e
.the.opp
ortunity
.to.suc
cess-
fully
.per
form
.DoS.att
acks.
.One.opp
ortunity
.to.ful
ly
.pre
vent
.DoS.att
acks
.is.to.lim
it
.the.phy
sical
.acc
ess
.
to.the.net
work
.med
ium
.and.to.the.dev
ices
.tha
t
.hav
e
.an.int
erface
.to.the.med
ium.
.(e.
g.,
.imm
uring
.the.
net
work
.cab
le
.or.by.loc
king
.the.dev
ices
.into.a.saf
e
.con
tainment.)
.Obv
iously,
.suc
h
.iso
lation
.is.not.alw
ays
.
eas
y
.to.ac
hieve.
Another
.pos
sibility
.to.pre
vent
.hos
t-based
.DoS.att
acks
.is.the.use.of.so-
called
.cli
ent puzzles
.[TU
O].
.e.
main.objective.of.a.client.puzzle.is.to.make.a.DoS.attack.at.least.as.expensive.for.the.adversary.as.for.the.
tar
get
.in.ter
ms
.of.com
putational
.cos
t.
.Con
sider,
.for.exa
mple,
.a.cli
ent
.(e.
g.,
.ope
rator
.wor
kstation)
.wan
ts
.
to.est
ablish
.a.con
nection
.to.a.ser
ver
.(e.
g.,
.con
troller).
.To.set.up.a.con
nection,
.the.cli
ent
.sen
ds
.an.ini
tial
.
req
uest
.to.the.ser
ver.
.If.the.ser
ver
.is.bus
y
.(e.
g.,
.the
re
.are.oth
er
.ope
n
.con
nections),
.the.ser
ver
.sen
ds
.bac
k
.a.
cli
ent
.puz
zle
.tha
t
.the.cli
ent
.has.to.sol
ve.
.A.typ
ical
.exa
mple
.of.suc
h
.a.cli
ent
.puz
zle
.wou
ld
.be.a.has
h
.val
ue
.
of.lim
ited
.len
gth
.[WE
I].
.e.cli
ent
.has.the.obje
ctive
.to.nd.the.inp
ut
.val
ue
.tha
t
.pro
duces
.thi
s
.has
h
.val
ue.
.
To.ach
ieve
.thi
s,
.the.cli
ent
.has.to.sol
ve
.thi
s
.pro
blem
.by.bru
te
.for
ce.
.As.it.is.ver
y
.eas
y
.to.ver
ify
.whe
ther
.the.
sol
ution
.is.val
id
.or.not
,
.the.cli
ent
.mus
t
.pay.mor
e
.com
puting
.cos
ts
.tha
n
.the.ser
ver.
.Ae
r
.the.cli
ent
.has.
sol
ved
.the.puz
zle,
.it.sen
ds
.the.sol
ution
.to.the.ser
ver.
.e.ser
ver
.ver
ies
.the.sol
ution,
.and.if.it.is.cor
rect
.
the.ser
ver
.acc
epts
.fur
ther
.req
uests.
.If.the.sol
ution
.is.not.val
id,
.acc
ess
.to.the.req
uested
.ser
vice
.is.den
ied
.
and.fu
rther
.re
quests
.ar
e
.te
mporally
.bl
ocked
.fr
om
.th
is
.cl
ient.
In
.situ
ations
.whe
re
.pre
vention
.met
hods
.are.ina
pplicable,
.DoS.att
acks
.sha
ll
.at.lea
st
.be.det
ected
.(DoS.
det
ection).
.In.gen
eral,
.the.aim.is.to.mak
e
.the.sys
tem
.int
rusion
.tole
rant
.and.lim
it
.the.ae
cted
.are
a.
.Aty
p-
ical
.exa
mple
.wou
ld
.be.the.use.of.an.IDS.[CH
R].
.An.IDS.tri
es
.to.det
ect
.abn
ormal
.sys
tem
.sta
tes
.by.com
-
paring
.the.act
ual
.beh
avior
.wit
h
.the.exp
ected
.one
.
.If.a.situ
ation
.tha
t
.may.lea
d
.to.a.sec
urity
.att
ack
.has.
bee
n
.de
tected,
.co
untermeasures
.ha
ve
.to.be.in
itiated
.to.mi
nimize
.th
e
.co
nsequences.
An
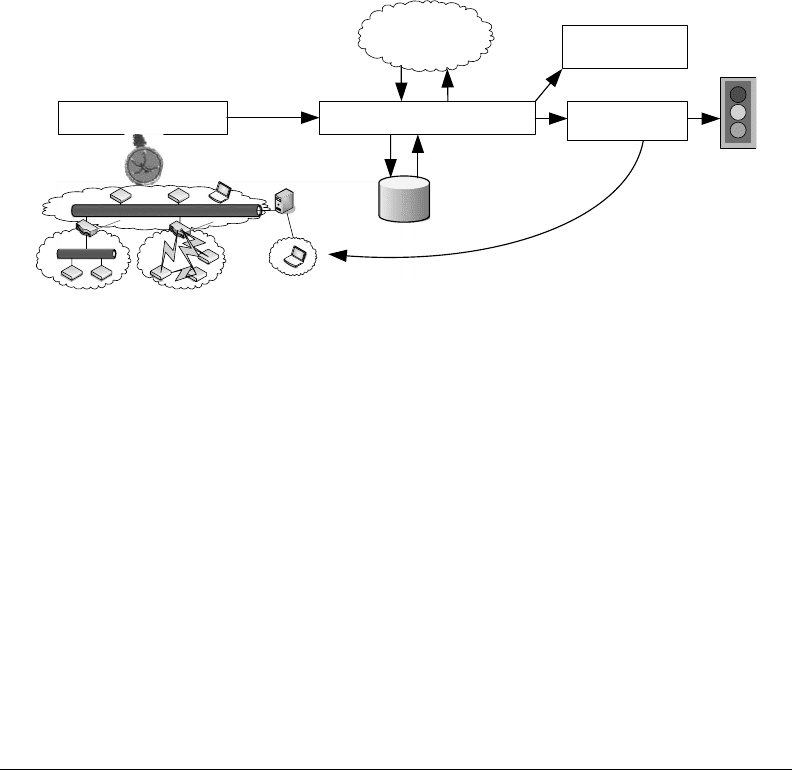
.IDS.com
monly
.con
sists
.of.fou
r
.com
ponents
.(cf
.
.Fig
ure
.22.
3).
.e.dat
a gathering component
.is.
res
ponsible
.for.col
lecting
.the.dat
a
.by.obs
erving
.the.net
work
.tra
c
.as.wel
l
.as.the.beh
avior
.of.the.di
erent
.
net
work
.dev
ices.
.IDS.are.cla
ssied
.acc
ording
.to.the.typ
e
.of.dat
a
.col
lection
.(i.
e.,
.the.loc
ation
.of.the.dat
a
.
gat
hering
.com
ponents).
.A.hos
t-based
.IDS.tri
es
.to.dis
cover
.abn
ormal
.act
ivities
.on.a.sing
le
.hos
t.
.es
e
.
met
hods
.obs
erve
.the.act
ivities
.on.a.sing
le
.dev
ice
.and.com
pare
.the.beh
avior
.pat
tern
.wit
h
.a.ref
erence
.pat
-
tern
.(pr
oling).
.Hos
t-based
.int
rusion
.det
ection
.is.esp
ecially
.app
licable
.for.sec
urity-critical
.dev
ices
.(e.
g.,
.
key.ser
vers).
.A.net
work-based
.IDS.obs
erves
.the.ent
ire
.net
work
.tra
c.
.er
efore,
.the
se
.sys
tems
.are.abl
e
.
to.di
scover
.an
omalies
.th
at
.a
ect
.mo
re
.th
an
.a.sin
gle
.ho
st.
e
.cor
e
.uni
t
.of.an.IDS.is.the.dat
a processing component.
.is.com
ponent
.pro
cesses
.the.col
lected
.
dat
a
.and.det
ermines
.whe
ther
.abn
ormal
.beh
avior
.is.pre
sent.
.Aga
in,
.di
erent
.app
roaches
.exi
st.
.e.two.
mos
t
.imp
ortant
.one
s
.are.cal
led
.mis
use-based
.and.ano
maly-based.
.Mis
use-based
.sys
tems
.use.a.pri
ori
.
kno
wledge.
of
.
act
ivities.
tha
t.
for
m.
an
.
att
ack..
is
.
kno
wledge.
is
.
stor
ed.
in
.
a
.
dat
abase.
tha
t.
con
tains.
typ
ical.
pat
terns
.of.kno
wn
.att
acks
.als
o
.cal
led
.sign
atures.
.To.det
ermine
.whe
ther
.an.obs
ervation
.can.be.cla
ssied
.
© 2011 by Taylor and Francis Group, LLC
Security in Industrial Communication Systems 22-9
as.an.attack,.dierent.techniques.such.as.expert.systems.as.well.as.signature.detection.mechanisms.
can.be.used..Anomaly-based.intrusion.detection.tries.to.detect.abnormal.behavior.by.comparing.the.
observed.behavior.with.the.normal.and.expected.behavior.also.called.reference.pattern..To.achieve.such.
a.comparison,.a.system.model.must.be.specied..is.model.must.dene.the.default.reference.pattern.
(i.e.,.network.trac.or.device.behavior).that.represents.the.expected.and.normal.behavior.of.the.sys-
tem.
.Obviously,.this.default.behavior.is.not.static.since.it.can.change.during.the.life.time.of.the.system..
erefore,.self-learning.techniques.(e.g.,.neural.networks).are.usually.applied.
Collecting
.the.results.as.well.as.the.observed.data.(communication.traces).is.the.task.of.the.data stor-
age unit. e response unit,
.nally,.is.responsible.for.initiating.actions.to.minimize.the.consequences.of.a.
detected.security.attack..is.can.be.done.by.performing.a.direct.feedback.to.the.network..For.example,.
it.could.decouple.the.aected.network.segment(s).
Clearly,
.DoS.prevention.is.preferable.to.detection.since.prevention.mechanisms.avoid.even.the.occur-
rence
.of.an.attack..Since.a.full.prevention.is.not.always.possible,.a.combination.of.the.advantages.of.both.
methods.by.using.a.hybrid.approach.is.the.most.appropriate.solution.
22.4 Security Measures to Counteract Device attacks
So.far,.only.the.protection.of.network.trac.has.been.discussed,.yet.also.attacks.to.the.device.itself.have.
to.be.considered..ese.attacks.can.be.divided.into.two.categories:.physical.protection.of.the.device.and.
security.soware.environments.
22.4.1 Protected Hardware and Security token
Keys.used.for.authentication.and.encryption.of.messages.typically.are.condential.information.to.be.stored.
on.a.eldbus.node..Yet,.condential.information.is.not.limited.to.this.and.also.includes.application.data.
such.as.application.counters,.e.g.,.the.power.consumption.value.of.a.electricity.meter,.which.should.not.be.
altered.illegitimately..Countermeasures.on.a.rst.level.restrict.access.to.condential.data.as.oered.by.most.
cryptographic.units.in.today’s.communication.chips—keys.can.be.written.to.the.key.storage.but.only.be.
retrieved.by.the.crypto.engine,.and.hence.are.not.visible.to.the.other.applications.on.the.node.(cf..Section.
22.4.2)..Yet,.some.implementations.do.not.honor.this.fully,.and.in.some.eldbus.systems.the.key.data.can.
nevertheless.be.read.by.dedicated.management.commands.originally.designed.to.read.an.arbitrary.part.of.
the.nodes’.memory..For.application.data,.such.protected.memory.areas.do.not.exists.in.general.
If
.equipment.should.be.tamper.resistant.and.tamper.evident,.additionally.a.protected.security.token.
must.be.added..A.trade-o.between.security.and.costs.is.required..A.rst.level.measure.might.already.be.
Data gathering
Knowledge
base
Response
component
Data storage
component
Data processing component
Process model
FIGURE 22.3 Intrusion.detection.system.
© 2011 by Taylor and Francis Group, LLC
22-10 Industrial Communication Systems
a.seal.to.allow.visual.detection.of.direct.manipulation.and.to.disable.network.management.commands.
if.app
licable.
.A.sec
ond
.lev
el
.mig
ht
.be.a.sol
id
.cas
e
.tha
t
.can
not
.be.ope
ned
.wit
hout
.obv
iously
.dam
aging
.
the.cas
e
.or.com
ponents
.of.it..e.thi
rd
.lev
el
.of.phy
sical
.pro
tection
.is.the.usa
ge
.of.a.sec
urity
.toke
n
.tha
t
.
con
tains
.th
e
.se
crets.
In
.gen
eral,
.for.mos
t
.app
lications
.det
ecting
.the.ope
ning
.of.the.cas
e
.wou
ld
.inc
rease
.sec
urity,
.but.due.
to.cos
t
.res
trictions
.mea
sures
.can.onl
y
.be.ver
y
.simp
le,
.e.g
.,
.a.swi
tch
.or.a.simp
le
.lig
ht
.det
ector.
.Hen
ce,
.
the.ove
rall
.inc
rease
.of.sec
urity
.is.onl
y
.ver
y
.mar
ginal,
.sinc
e
.the.dev
ices
.do.not.hav
e
.ind
ependent
.pow
er
.
sup
ply
.(ba
ttery)
.tha
t
.mai
ntains
.the.sec
urity
.fun
ctions
.if.the.dev
ice
.is.unp
lugged.
.at.is,.an.att
acker
.can.
ana
lyze
.th
e
.tu
rned-o
.de
vice
.an
d
.ci
rcumvent
.th
e
.se
curity
.me
asures
.wi
th
.li
ttle
.e
ort.
Considering
.all.pos
sible
.att
acks,
.it.is.not.cos
t
.ee
ctive
.to.prot
ect
.the.who
le
.nod
e,
.rat
her
.a.sma
ll
.par
t
.
is.equ
ipped
.wit
h
.hig
h-security
.meas
ures,
.whi
ch
.is.cal
led
.sec
urity token.
.For.oth
er
.appl
ications
.in.com
-
merce
.and.for.bui
lding
.sec
urity,
.suc
h
.sec
urity
.toke
ns
.are.alr
eady
.on.the.mark
et
.and.sta
te
.of.the.art
.
.
e.most.kno
wn
.toke
n
.is.the.sma
rt
.car
d
.tha
t
.imp
lements
.wel
l-proven
.sec
urity
.meas
ures
.to.ful
ll
.the.
req
uirements
.de
ned
.bef
ore.
.es
e
.com
mercially
.ava
ilable
.sec
urity
.toke
ns
.oe
r
.an.adv
anced
.sec
urity
.
des
ign
.and.sat
isfy
.the.req
uirements
.of.hig
h-security
.appl
ications
.(e.
g.,
.ele
ctronic
.mone
y,
.dig
ital
.sig
na-
tures).
.Mea
sures
.lik
e
.scr
ambled
.RAM.pla
cement,
.pow
er
.supp
ly
.moni
toring,
.fai
l-safe
.ope
ration,
.and.
pow
er
.con
sumption
.cip
hering
.are.alr
eady
.inc
luded
.in.suc
h
.dev
ices.
.Com
mon
.prod
ucts
.oe
n
.hav
e
.a.
cer
ticate
.to.be.res
istant
.aga
inst
.mal
icious
.scr
utiny
.and.man
ipulation
.(e.
g.,
.com
mon
.cri
teria
.eva
lua-
tion
.lev
els).
In
.[SC1],.the.authors.already.implemented.such.an.approach.for.the.LonWorks.[LON].protocol.oer-
ing
.two.adv
antages:
.Fir
st
.the.sma
rt
.car
d
.pro
vided
.the.req
uired
.sec
ure
.dat
a
.stor
age
.for.the.nod
e,
.and.
sec
ond
.the.car
d
.als
o
.sup
ported
.sta
te-of-the-art
.cry
ptographic
.fun
ctions.
.e.sma
rt
.car
d
.was.con
nected
.
to.a.Lon
Works
.nod
e
.usin
g
.a.ser
ial
.int
erface
.and.int
egrated
.in.the.app
lication
.in.suc
h
.a.way.tha
t
.eac
h
.
mes
sage
.sen
t
.was.pro
tected
.by.an.HMA
C-SHA-1
.cry
ptographic
.che
ck
.sum.and.enc
rypted
.usin
g
.3-D
ES
.
ove
rcoming
.the.lim
itations
.of.the.Lon
Works
.sec
urity
.mec
hanisms
.wit
h
.res
pect
.to.str
ength,
.numb
er
.of.
sec
urity
.gro
ups
.(on
ly
.one.is.sup
ported
.by.Lon
Works),
.and.the.sup
port
.of.sec
urity
.ser
vices
.(Lo
nWorks
.
onl
y
.su
pports
.a.we
ak
.au
thentication
.fo
r
.un
icast
.se
rvices).
Yet,
.a.com
plete
.int
egration
.of.the.sec
urity
.toke
n
.in.the.chi
p
.is.oe
n
.fav
orable
.com
pared
.to.the.ext
er-
nal
.sma
rt
.car
d
.and.the.req
uired
.int
erconnection
.cir
cuit.
.Esp
ecially
.for.wir
eless
.net
works,
.man
y
.chi
ps
.
alr
eady
.hav
e
.a.sec
urity
.toke
n
.int
egrated
.for.cry
ptographic
.ope
rations
.red
ucing
.the.nec
essity
.for.an.add
i-
tional
.se
curity
.tok
en.
22.4.2 Secure Software Environments
A.common.approach.that.directly.manipulates.the.behavior.of.a.device.is.to.interfere.with.the.soware.
run
ning
.on.it..To.ach
ieve
.thi
s,
.an.adv
ersary
.may.try.to.cha
nge
.exi
sting
.pro
gram
.cod
e
.or.eve
n
.add.new.
cod
e
.fra
gments
.to.exi
sting
.one
s.
.us
,
.mod
ications
.tha
t
.hav
e
.nev
er
.bee
n
.the.int
ention
.of.the.so
ware
.
dev
eloper
.can.res
ult
.in.mal
icious
.so
ware
.beh
avior.
.is.cha
nged
.or.new
ly
.add
ed
.mal
icious
.cod
e
.is.
gen
erally
.cal
led
.mal
ware,
.an.abb
reviation
.for.mal
icious soware.
.Not
e
.tha
t
.uni
ntentional
.so
ware
.fau
lts
.
are.by.de
nition
.no
t
.ma
lware
.ev
en
.if.th
ey
.ma
y
.re
sult
.in.vu
lnerabilities
.th
at
.an.ad
versary
.ma
y
.ut
ilize.
Depending
.on.the.int
ention
.of.mal
ware
.and.on.the.dam
age
.it.may.cau
se,
.mal
ware
.can.fur
ther
.be.cat
-
egorized.
.In.the.lit
erature,
.di
erent
.de
nitions
.tha
t
.may.di
er
.to.eac
h
.oth
er
.exi
st.
.e.mos
t
.imp
ortant
.
kin
ds
.of.ma
lware
.ar
e
.th
e
.fo
llowing:
•
. Virus:.A.virus.is.a.self-replicating.piece.of.soware.that.inserts.itself.into.existing.program.
cod
e
.or.rep
laces
.par
t
.of.it..By.de
nition,
.a.vir
us
.nee
ds
.alw
ays
.a.hos
t
.pro
gram
.tha
t
.act
ivates
.it,.
sin
ce
.a.vir
us
.can
not
.run.by.its
elf.
•
. Wor
m:
.In.con
trast
.to.a.vir
us,
.a.wor
m
.is.a.mal
icious
.sta
nd-alone
.pro
gram
.tha
t
.pro
pagates
.a.com
-
plete
.cop
y
.of.its
elf
.usu
ally
.ove
r
.the.net
work.
.e.mai
n
.cha
racteristic
.is.tha
t
.a.wor
m
.doe
s
.not.nee
d
.
any.us
er
.in
teraction.
© 2011 by Taylor and Francis Group, LLC
Security in Industrial Communication Systems 22-11
•. Trojan horse:.A.Trojan.horse.obscures.its.malicious.intent.by.pretending.to.have.a.useful.func-
tion.
.How
ever,
.ae
r
.bei
ng
.act
ivated
.by.the.use
r,
.a.hid
den
.mal
icious
.fun
ction
.is.per
formed
.tha
t
.
all
ows
.a.rem
ote
.adv
ersary
.to.gai
n
.una
uthorized
.acc
ess
.to.the.hos
t
.tha
t
.exe
cutes
.the.Troj
an
.
hor
se.
•
. Log
ical bomb:
.A.log
ical
.bomb.is.mal
ware
.tha
t
.onl
y
.act
ivates
.itse
lf
.ae
r
.cer
tain
.con
ditions
.are.
met
.
.A.spe
cial
.kin
d
.of.log
ical
.bomb.is.a.tim
e
.bomb.whe
re
.a.spe
cic
.poi
nt
.in.tim
e
.is.use
d
.as.
tri
gger.
•
. Roo
tkit:
.A.roo
tkit
.is.a.spe
cial
.kin
d
.of.mal
ware
.tha
t
.inf
ects
.the.sys
tem
.in.a.way.tha
t
.it.rem
ains
.
inv
isible
.at.the.hos
t.
.To.ach
ieve
.thi
s,
.roo
tkits
.typ
ically
.rep
lace
.cor
e
.com
ponents
.of.the.sys
tem
.
so
ware
.li
ke
.ke
rnel
.mo
dules
.in.op
erating
.sy
stems.
•
. Bac
kdoor or trapdoor:
.is.kin
d
.of.mal
ware
.pro
vides
.an.alt
ernative
.way.to.acc
ess
.the.inf
ected
.
sys
tem
.th
at
.by
passes
.th
e
.no
rmal
.au
thentication
.pr
ocedure.
•
. Spy
ware:
.Spyw
are
.usu
ally
.doe
s
.not.cau
se
.dir
ect
.har
m.
.It.rat
her
.col
lects
.con
dential
.inf
ormation
.
on.the.hos
t
.bei
ng
.use
d
.for.fur
ther
.att
acks,
.e.g
.,
.pas
swords
.or.oth
er
.majo
r
.ass
ets
.(e.
g.,
.che
mical
.
rec
ipes).
Like
.any.oth
er
.sec
urity
.att
ack,
.mal
ware
.is.onl
y
.abl
e
.to.uti
lize
.exi
sting
.vul
nerabilities
.in.the.dev
ice
.to.
inf
ect
.it..To.cou
nteract
.att
acks
.on.so
ware
.two.pos
sibilities
.exi
t:
.Fir
st,
.met
hods
.can.be.use
d
.tha
t
.pre
vent
.
the.exi
stence
.of.vul
nerabilities.
.Sec
ond,
.if.a.ful
l
.pre
vention
.is.not.pos
sible,
.mal
ware
.or.the.att
empt
.to.
ins
ert
.it.into.the.dev
ice’s
.so
ware
.sha
ll
.at.lea
st
.be.det
ected.
.Cou
ntermeasures
.tha
t
.pre
vent
.and
/or
.det
ect
.
the.ex
istence
.of.ma
lware
.ca
n
.be.ca
tegorized
.as.fo
llows.
•
. Sta
tic soware methods
.try.to.avo
id
.the.exi
stence
.of.so
ware
.vul
nerabilities
.a.pri
ori
.dur
ing
.the.
so
ware
.dev
elopment.
.Typ
ical
.tec
hniques
.are.sta
tic
.cod
e
.ana
lysis
.met
hods
.tha
t
.try.to.det
ect
.pro
-
gramming
.aw
s
.(e.
g.,
.bu
er
.ove
rows)
.as.wel
l
.as.cod
e-signing
.met
hods
.whe
re
.the.dev
eloper
.sign
s
.
the.exe
cutables
.to.con
rm
.the.non
-modication.
.Ano
ther
.exa
mple
.is.pro
of-carrying
.cod
e
.whe
re
.
the.de
veloper
.pr
ovides
.a.pr
oof
.al
ong
.wi
th
.a.pr
ogram
.th
at
.al
lows
.ch
ecking
.wi
th
.ce
rtainty
.th
at
.th
e
.
cod
e
.ca
n
.be.ex
ecuted
.in.a.se
cure
.wa
y.
•
. Dyn
amic soware methods
.try.to.ide
ntify
.mal
ware
.by.det
ecting
.a.mal
icious
.beh
avior
.dur
ing
.run
-
time.
.A.com
mon
.app
roach
.is.to.use.a.hos
t-based
.IDS.tha
t
.det
ects
.mal
icious
.beh
avior
.or.act
ions
.
dur
ing
.run
time
.(cf
.
.Sec
tion
.22.
3.4).
.A.simi
lar
.tec
hnique
.is.cal
led
.so
ware
.mon
itoring,
.whe
re
.
pro
gram
.exe
cution
.is.obs
erved
.to.che
ck
.whe
ther
.the.so
ware
.beh
aves
.acc
ording
.to.a.spe
cied
.
sec
urity
.pol
icy.
.Ano
ther
.app
roach
.is.to.use.sel
f-checking
.cod
e.
.Her
e,
.the.so
ware
.its
elf
.ver
ies
.
the.pro
gram
.cod
e
.for.una
uthorized
.mod
ications
.dur
ing
.exe
cution.
.A.fur
ther
.app
roach
.tha
t
.is.
pop
ular
.in.env
ironments
.whe
re
.unt
rustworthy
.and.thu
s
.pos
sible
.mal
icious
.so
ware
.has.to.be.
exe
cuted
.is.cal
led
.san
dboxing.
.Usin
g
.thi
s
.tec
hnique,
.the.unt
rustworthy
.so
ware
.is.run
ning
.in.a.
so-
called
.san
dbox
.whe
re
.it.is.exe
cuted
.in.a.con
trolled
.way.wit
h
.res
tricted
.per
missions.
.e.mai
n
.
adv
antage
.of.thi
s
.sch
eme
.is.tha
t
.mal
icious
.so
ware
.is.not.abl
e
.to.lea
ve
.the.san
dbox
.and.inf
ect
.
oth
er
.par
ts
.of.the.sys
tem
.sinc
e
.an.int
eraction
.wit
h
.the.res
t
.of.the.sys
tem
.is.onl
y
.pos
sible
.usin
g
.
wel
l-dened
.an
d
.pr
otected
.in
terfaces.
•
. Har
dware supported methods
.use.har
dware-specic
.imp
lementations
.tha
t
.try.to.avo
id
.an.ins
er-
tion
.of.mal
ware.
.A.typ
ical
.exa
mple
.is. the. use. of. mic
rocontrollers
.tha
t
.are.imp
lementing
.the.
Har
vard
.arc
hitecture.
.Due.to.the.phy
sical
.par
titioning
.of.ins
truction
.and.dat
a
.mem
ory,
.cod
e
.
inje
ction
.is.not.pos
sible
.by.desi
gn.
.Ano
ther
.rec
ent
.tec
hnique
.is.the.no.exe
cute
.(NX
)
.bit.in.mod
-
ern
.CPU
s,
.whe
re
.mem
ory
.reg
ions
.can.be.desi
gnated
.as.bei
ng
.non
-executable.
.Ano
ther
.com
mon
.
app
roach
.is.the.use.of.a.cop
rocessor
.tha
t
.is.ded
icated
.to.per
form
.sec
urity
.che
cks
.dur
ing
.run
time.
•
. Hum
an-assisted methods:
.In.cas
es
.whe
re
.auto
matic
.met
hods
.can
not
.ful
ly
.pre
vent
.or.det
ect
.the.
existence.of.malware,.human-assisted.methods.can.additionally.be.used..Typical.examples.are.
man
ual
.ins
pection
.or.the.use.of.cer
ticated
.so
ware.
.Obv
iously,
.hum
an-assisted
.met
hods
.are.
tim
e
.con
suming
.and.req
uire
.ext
ensive
.kno
wledge.
.er
efore,
.it.is.rea
sonable
.to.use.the
m
.onl
y
.in.
comb
ination
.wi
th
.au
tomatic
.te
chniques.
© 2011 by Taylor and Francis Group, LLC

22-12 Industrial Communication Systems
Guaranteeing.a.secure.environment.for.the.execution.of.soware.is.a.typical.task.of.the.operation.
syst
em
.runn
ing
.on.the.devi
ce.
.Howe
ver,
.indu
strial
.comm
unication
.syst
ems
.cont
ain
.embed
ded
.devi
ces
.
with.limi
ted
.syst
em
.reso
urces.
.ere
fore,
.thes
e
.devi
ces
.are.oen.not.equi
pped
.with.an.oper
ation
.syst
em
.
that.prov
ides
.supp
ort
.for.adva
nced
.secu
rity
.serv
ices.
.ere
fore,
.prov
iding
.a.secu
re
.sow
are
.exec
ution
.
envi
ronment
.is.esp
ecially
.cha
llenging
.in.embe
dded
.net
works.
22.5 State of the art in automation Systems
is.section.will.give.an.overview.of.the.state.of.the.art.of.security.measures.in.industrial.communica-
tion
.syst
ems.
.ese.are.divi
ded
.into.eld
bus
.syst
ems
.orig
inally
.desig
ned
.for.buil
ding
.autom
ation,
.but.
also.used.in.indu
strial
.comm
unications,
.clas
sical
.indu
strial
.eld
bus
.syst
ems,
.and.IP-ba
sed
.netw
orks.
.
An.over
view
.of.the.supp
orted
.secu
rity
.mech
anisms
.can.be.foun
d
.in.Tabl
e
.22.1.at.the.end.of.this.sect
ion.
22.5.1 Security in Building automation Systems
Today,.many.dierent.protocol.standards.for.building.automation.systems.exist..e.most.important.
open.ones.that.span.more.than.one.appl
ication
.doma
in
.are.BACn
et
.[BAC
],
.KNX.[KNX
],
.LonW
orks
.
[LON
],
.and.IEE
E
.802
.15.4/ZigBee
.[IE
E,ZIG].
BACnet
.in.its.curr
ent
.vers
ion—version
.numb
er
.2008
—oers
.an.auth
entication
.serv
ice
.as.well.as.die
r-
ent
.secu
rity
.serv
ices
.that.guar
antee
.data.con
dentiality,
.data.integ
rity,
.and.data.fres
hness.
.ese.mech
a-
nisms
.use.the.symm
etric
.Data.Encr
yption
.Stan
dard
.(DES
)
.algo
rithm
.and.a.trus
ted
.key.serv
er,
.whic
h
.is.
resp
onsible
.for.gene
rating
.and.dist
ributing
.the.secr
et
.keys
.
.Howe
ver,
.due.to.seve
ral
.secu
rity
.aws.[GR2
],
.
ther
e
.are.inve
stigations
.under
way
.to.repl
ace
.thes
e
.secu
rity
.serv
ices
.by.new.ones
.
.e.new.secu
rity
.arch
i-
tecture,
.whic
h
.is.dene
d
.in.BACn
et
.Adden
dum
.g,.uses.AES.and.HMAC.in.comb
ination
.with.a.mess
age
.
ID.and.a.time.stam
p.
.At.the.time.of.writ
ing,
.BACn
et
.Adden
dum
.g.has.not.been.decla
red
.as.nal.yet.
K
NX,
.on.the.othe
r
.hand
,
.only.prov
ides
.a.basic.acce
ss
.cont
rol
.sche
me
.base
d
.on.clea
r-text
.pass
words.
.
Up.to.255.die
rent
.acce
ss
.leve
ls
.can.be.den
ed,
.each.of.them.asso
ciated
.with.a.die
rent
.(oth
erwise
.
unsp
ecied)
.set.of.priv
ileges.
.For.each.of.thes
e
.acce
ss
.leve
ls,
.a.4.byte.pass
word
.(key
)
.can.be.spec
ied.
.
Howe
ver,
.since.this.rudi
mentary
.acce
ss
.cont
rol
.mech
anism
.does.not.prov
ide
.stro
ng
.secu
rity
.[GR2
],
.it.
is.only.of.limi
ted
.use.in.secu
rity-critical
.envi
ronments.
.Furt
hermore,
.it.is.not.avai
lable
.for.proc
ess
.data.
exch
ange,
.whi
ch
.is.cal
led
.gro
up
.com
munication
.in.KNX
.
In
.LonW
orks,
.an.auth
entication
.mech
anism
.that.guar
antees
.data.inte
grity
.and.fres
hness
.is.avai
l-
able.
.Suppo
rt
.for.data.con
dentiality
.is.not.prov
ided.
.is.mech
anism
.is.base
d
.on.a.four
-step
.chal
lenge–
response
. proto
col.
. e. used. crypto
graphic
. algo
rithm
. calc
ulates
.a. 64. bit.hash. valu
e
. over. the. plai
n
.
TABLE 22.1 Security.Services.of.Common.Fieldbus.Systems
Fieldbus Security.Services
Foundation
.Fieldb
us 8
.access.gro
ups,
.8.bit.unencr
ypted
.pas
sword
ControlNet Connection
.aut
hentication,
.unencr
ypted
.pas
sword
PROFIBUS Access
.cont
rol
.for.pre
dened
.address
es
P-Net Simple
.wri
te
.pro
tection
.for.vari
ables
WorldFIP 8
.access.gro
ups,
.8.bit.unencr
ypted
.pas
sword
Interbus 8
.access.gro
ups,
.8.bit.unencr
ypted
.pas
sword
SwiNet None
LonWorks Challenge–response
.auth.,.integr
ity
.chec
k,
.MD5.for.IP
KNX Unencr
ypted
.pas
sword
.for.man
agement
.access
BA
Cnet
.Addend
um
.g AES.for.dat
a
.condent
iality,
.HMAC.for.dat
a
.integ
rity,
.
time.sta
mp
.+.mess
age
.ID.for.dat
a
.fres
hness
ZigBee CCM*
.algorithm.for.data.integrity,.freshness,.and.
condentiality
© 2011 by Taylor and Francis Group, LLC
Security in Industrial Communication Systems 22-13
message.and.a.random.number.using.a.shared.secret.key..However,.due.to.key.length.and.several.proto-
col
.aw
s,
.thi
s
.mec
hanism
.can
not
.be.con
sidered
.as.sec
ure
.[SC
1].
.In.add
ition
.to.thi
s
.basi
c
.aut
hentication
.
mec
hanism,
.a.mor
e
.adv
anced
.one.bas
ed
.on.MD5.is.ava
ilable
.for.Lon
Works/IP.
.How
ever,
.sinc
e
.MD5.is.
not.co
llision
.re
sistant,
.it.is.al
so
.re
garded
.as.in
secure.
IEEE 802.15.4
.sup
ports
.sec
urity
.mec
hanisms
.at.the.dat
a
.lin
k
.lay
er.
.e.cur
rent
.ver
sion
.IEE
E
.802
.15.4-
2006
.use
s
.a.var
iant
.of.the.cou
nter
.wit
h
.CBC
-MAC
.(CC
M)
.alg
orithm
.cal
led
.CCM.to.gua
rantee
.dat
a
.
int
egrity,
.fre
shness,
.and.con
dentiality.
.Zig
Bee
.in.its.cur
rent
.ver
sion
.Zig
Bee
.200
7
.uti
lizes
.the.IEE
E
.
802
.15.4-2003
.tra
nsmission
.ser
vices
.of.the.dat
a
.lin
k
.lay
er.
.How
ever,
.Zig
Bee
.200
7
.doe
s
.not.use.the.sec
u-
rity
.mec
hanisms
.pro
vided
.by.IEE
E
.802
.15.4-2003—they
.are.com
pletely
.rep
laced
.by.a.mor
e
.adv
anced
.
sec
urity
.con
cept.
.is.con
cept
.sup
ports
.the.use.of.di
erent
.key.typ
es
.and.pro
vides
.adv
anced
.key.man
-
agement
.se
rvices.
.Ag
ain,
.CC
M*
.is.us
ed
.as.a.cr
yptographic
.al
gorithm.
Beside
.the.sec
urity
.fea
tures
.wit
hin
.the.pro
tocol,
.an.imp
ortant
.iss
ue
.is.the.con
nection
.of.the.bui
lding
.
to.rem
ote
.mai
ntenance
.cen
ters.
.For.suc
h
.con
nections,
.bui
ldings
.are.equ
ipped
.wit
h
.gat
eways
.tha
t
.all
ow
.
rem
ote
.acc
ess
.to.the.und
erlying
.el
dbus.
.Typ
ical
.sec
urity
.mea
sures
.for.the
se
.gat
eways
.are.IP.con
nec-
tions
.pro
tected
.by.tra
nsport
.lay
er
.sec
urity
.(TL
S)
.or.VPN.tha
t
.sec
urely
.tun
nel
.the.com
mands
.fro
m
.the.
rem
ote
.site.to.the.el
dbus
.(se
e
.Sec
tion
.22.
5.3).
.In.rar
e
.cas
es
.als
o
.Web.Ser
vices
.Sec
urity
.is.use
d.
.To.the.
el
dbus
.sit
e,
.th
e
.ga
teways
.us
ually
.pr
ovide
.no.se
curity
.or.th
e
.se
curity
.pr
otocols
.me
ntioned
.ab
ove.
22.5.2 Security in Industrial Communication
Although.almost.never.used,.some.industrial.automation.eldbusses.support.security..However,.these.
sec
urity
.mea
sures
.are.ver
y
.lim
ited
.in.sco
pe
.and.cap
abilities,
.and.the
refore
.can
not
.be.con
sidered
.as.
ser
ious
.pro
tection
.if.a.con
siderable
.thr
eat
.lev
el
.nee
ds
.to.be.ass
umed.
.e.el
dbus
.sys
tems
.for.ind
ustrial
.
and.pro
cess
.auto
mation
.cur
rently
.sta
ndardized
.by.the.IEC.in.the.sta
ndards
.IEC.617
84-1
.[IE
C1]
.and.the.
und
erlying
.IEC.611
58
.ser
ies
.[IE
C2]
.are.a.het
erogeneous
.col
lection
.of.sol
utions.
.ei
r
.sec
urity
.fea
tures
.
can.be.div
ided
.into.two.cat
egories:
.in.sys
tems
.lik
e
.Con
trolNet,
.P-N
et,
.and.Swi
Net,
.har
dly
.any.sta
te-of-
the-art
.sec
urity
.mea
sures
.are.use
d
.at.all
.
.Fou
ndation Fieldbus,
.Pro
bus,
.Wor
ldFIP,
.and.Int
erbus
.on.the.
oth
er
.han
d
.imp
lement
.ver
y
.simi
lar
.app
lication
.lay
er
.ser
vices
.and.pro
tocols
.mod
eled
.ae
r
.the
ir
.el
dbus
.
anc
estor
.MMS
.
.e.simp
le
.acc
ess
.pro
tection
.mec
hanism
.of.the
se
.sys
tems
.is.bas
ed
.on.acc
ess
.rig
hts
.man
-
agement
.simi
lar
.to.UNI
X-based
.sys
tems.
.Eve
ry
.obje
ct
.has.a.8.bit.lon
g
.pas
sword
.ass
ociated
.wit
h
.it.and.a.
lis
t
.of.8.di
erent
.acc
ess
.gro
ups
.cod
ed
.in.an.8.bit.wor
d.
.Bot
h
.pas
sword
.and.acc
ess
.gro
ups
.are.tra
nsmit-
ted
.in.pla
in
.tex
t.
.If.the
y
.mat
ch
.for.a.spe
cic
.req
uest,
.the.add
itional
.acc
ess
.rig
hts
.par
ameter
.de
nes
.the.
all
owed
.ope
rations.
.Usu
ally
.the.acc
ess
.rig
hts
.dep
end
.on.the.typ
e
.of.obje
ct
.and.all
ow
.rea
ding,
.wri
ting,
.
exe
cuting,
.de
letion,
.et
c.
Unfortunately,
.the
se
.sec
urity
.mea
ns
.are.not.man
datory
.for.imp
lementation,
.and.the.pas
sword
.its
elf,
.
add
itionally,
.has.no.exp
licit
.pro
tection.
.at.is,.it.is.tra
nsmitted
.in.cle
ar
.tex
t,
.and.hen
ce
.sho
uld
.not.
be.use
d
.at.all
.
.A.not
e
.in.IEC.611
58-5
.rev
eals
.the.act
ual
.int
ention
.of.the.sec
urity
.mec
hanisms:
.“i
s
.is.
not.a.pro
tection
.aga
inst
.int
entional
.mis
use
.of.the.com
munication
.fac
ilities
.of.a.el
d
.dev
ice
.but.hel
ps
.
to.pro
tect
.a.sys
tem
.for.acc
idental
.err
oneous
.use.of.pro
cess
.dat
a.”
.is.sta
tement
.is.in.fac
t
.tru
e
.for.all.
traditional.eldbus.systems.in.industrial.and.process.automation..Hence,.to.secure.data.trac.security.
mea
sures
.can.onl
y
.be.imp
lemented
.on.top.of.the.pro
tocol
.sta
ck.
.at.is,.the.el
dbus
.is.onl
y
.use
d
.as.a.
tra
nsparent
.tra
nsport
.cha
nnel
.to.tra
nsmit
.sec
ure
.mes
sages
.ove
r
.sta
ndard
.el
dbus
.pro
tocols
.and.ser
-
vices.
.Suc
h
.an.app
lication-level
.app
roach
.cou
ld
.easi
ly
.ach
ieve
.end
-to-end
.sec
urity,
.whi
ch
.is.the.goa
l
.
in.man
y
.app
lications,
.any
way.
.Sim
ilar
.app
roaches
.hav
e
.alr
eady
.bee
n
.imp
lemented
.for.saf
ety
.app
lica-
tions
.suc
h
.as.the.Pro
safe
.pro
le
.of.Pro
bus
.(IE
C
.611
58).
.Dra
wback
.of.add
ing
.suc
h
.an.app
lication-level
.
app
roach
.for.sec
urity
.is.to.cau
se
.pro
blems
.wit
h
.int
eroperability,
.sinc
e
.in.gen
eral
.the.int
eroperability
.
mec
hanism
.of.the.und
erlying
.el
dbus
.sys
tem
.can
not
.be.use
d.
.Exi
sting
.var
iable
.typ
es
.or.mes
sages
.can
-
not
.be.use
d
.sinc
e
.the
y
.de
ne
.no.pro
perties
.for.sec
urity
.mea
sures.
.Hen
ce,
.the.onl
y
.way.is.to.use.gen
eral
.
pur
pose
.mes
sages
.and.red
ene
.the
ir
.beh
avior.
.Alt
hough
.a.par
allel
.usa
ge
.of.sec
ure
.and.ins
ecure
.dev
ices
.
is.po
ssible
.wi
th
.th
is
.ap
proach,
.th
e
.pr
actical
.ap
plication
.de
mands
.a.joi
nt
.us
e.
.Ye
t
.co
nnecting
.se
cure
.an
d
.
© 2011 by Taylor and Francis Group, LLC
