Wilamowski B.M., Irwin J.D. The Industrial Electronics Handbook. Second Edition: Industrial Communication Systems
Подождите немного. Документ загружается.

13-1
13.1 Introduction
e.past.two.decades.have.brought.tremendous.advances.in.network.technology,.both.in.the.oce.world.
and.in.all.eld
s
.of.auto
mation.
.Two.obvi
ous
.indi
cators
.for.this.are.on.the.one.hand.the.stun
ning
.succe
ss
.
of.the.Inte
rnet,
.whose.techn
ological
.prin
ciples
.have.also.wide
ly
.been.adop
ted
.in.smal
l-size
.loca
l
.area.net-
w
orks
.(LAN
s).
.On.the.othe
r
.hand
,
.the.leng
thy
.and.erc
e
.stru
ggle
.for.an.accep
table
.comp
romise
.in.eld
bus
.
stan
dardization
.show
s
.that.the.auto
mation
.doma
in
.is.seen.as.an.impo
rtant
.mark
et
.by.the.big.play
ers.
.
Conse
quently,
.as.netw
orking
.in.both.worl
ds
.has.reac
hed
.a.matu
re
.poin
t,
.the.recen
t
.year
s
.have.seen.many.
atte
mpts
.to.brin
g
.the.two.side
s
.toge
ther
.and.to.nal
ly
.achi
eve
.somet
hing
.that.had.rema
ined
.wish
ful
.thin
k-
ing
.for.a.long.time
:
.the.idea.of.vert
ical
.inte
gration,
.mean
ing
.a.seaml
ess
.inte
gration
.of.auto
mation
.data.into.
a.high
er
.leve
l
.info
rmation
.techn
ology
.(IT).cont
ext
.beyo
nd
.mere.data.acqu
isition
.[WV0
3].
e
.term.“ver
tical
.inte
gration”
.has.beco
me
.tren
dy
.in.the.last.year
s
.and.has.been.used.as.a.mark
eting
.
argu
ment
.for.a.numbe
r
.of.autom
ation
.solu
tions.
.Stric
tly
.spea
king,
.howe
ver,
.vert
ical
.inte
gration
.is.not.
a.conc
ept
.pecu
liar
.to.autom
ation.
.In.fact
,
.it.has.seve
ral
.conn
otations
.in.die
rent
.doma
ins
.that.may.be.
dist
inguished:
•
. In.an.econ
omical
.cont
ext,
.it.deno
tes
.the.exte
nt
.to.whic
h
.a.comp
any
.has.cont
rol
.of.the.proc
esses
.
invo
lved
.in.the.manu
facturing
.of.its.prod
ucts.
.Full.vert
ical
.inte
gration
.in.this.case.mean
s
.full.
cont
rol
.over.the.enti
re
.valu
e
.chai
n
.from.raw.mate
rial
.prod
uction
.unti
l
.the.asse
mbly
.of.the.nal.
prod
uct
.[RO
03].
•
. In.a.busi
ness
.and.orga
nizational
.cont
ext,
.it.conc
erns
.the.info
rmation
.exch
ange
.betw
een
.the.vario
us
.
mana
gement
.leve
ls
.in.a.comp
any
.or.an.aggl
omerate
.of.comp
anies.
.e.rele
vant
.prop
erty
.here.is.the.
cont
rol
.of.the.decis
ion
.ow.acro
ss
.the.hier
archies.
•
. In.an.auto
mation
.cont
ext,
.nal
ly,
.it.mean
s
.the.data.exch
ange
.betw
een
.all.auto
mation
.leve
ls
.insi
de
.a.
plan
t.
.In.part
icular,
.it.deno
tes
.the.inte
rconnection
.of.auto
mation
.and.oce.netw
orks
.on.a.techn
o-
logical
.leve
l,
.and.the.link
age
.of.eld
-level
.cont
rol
.and.plan
ning
.tool
s
.on.an.appl
ication
.leve
l
.[S07
].
is
.chapt
er
.will.focu
s
.on.the.latt
er
.aspe
cts
.of.vert
ical
.inte
gration,
.and.ther
e
.agai
n
.espe
cially
.on.
the.tech
nological
.issu
es.
.It.will.shed.some.ligh
t
.on.the.evol
ution
.of.the.inte
gration
.idea.from.the.rst.
13
Vertical Integration
13.1. Introduction.....................................................................................13-1
13.2
. Histo
rical
.Bac
kground....................................................................13-2
13.3
. Netw
ork
.Int
erconnections.............................................................13-4
13.4
. Appl
ication
.Vie
w.............................................................................13-7
13.5
. Secu
rity
.Asp
ects
.in.Ver
tical
.Int
egration......................................13-8
13.6
. Tren
ds
.in.Ver
tical
.Int
egration.....................................................13-10
Abbreviations.............................................................................................13-11
References...................................................................................................13-12
Thilo Sauter
Austrian Academy
of Sci
ences
Stefan Soucek
LOyTEC electronics GmbH
Martin
Wollschlaeger
Dresden University
of Tec
hnology
© 2011 by Taylor and Francis Group, LLC
13-2 Industrial Communication Systems
attempts.to.today’s.situation..A.section.is.devoted.to.the.network.interconnection.problem.that.is.a.
cornerstone.for.integration..e.application.view.of.vertical.integration.will.be.briey.sketched,.and.the.
question.of.how.to.achieve.security.will.be.discussed..Finally,.a.few.trends.of.the.ongoing.evolution.will.
be.highlighted.
13.2 Historical Background
Historically.speaking,.the.idea.of.achieving.a.data.ow.from.the.shop.oor.and.the.eld.level.to.the.
oce.level.together.with.proper.network.integration.is.not.new..What.is.new.is.the.current.focus.on.
Internet.technologies.as.upper.level.of.the.interconnection..However,.the.integration.idea.itself.was.
already.part.of.the.computer-integrated.manufacturing.(CIM).concept.suggested.in.the.1970s.[H73]..
e.approach.put.forward.then.was.to.create.a.transparent,.multilevel.network.to.structure.the.informa-
tion
.ow.required.for.factory.and.process.automation.[DSP88]..To.cope.with.the.expected.complexity,.
a.strict.subdivision.of.the.information.processing.into.a.hierarchical.model.was.devised.that.became.
to.be.known.as.the.automation.pyramid..e.model.exists.in.various.versions.with.dierent.naming.
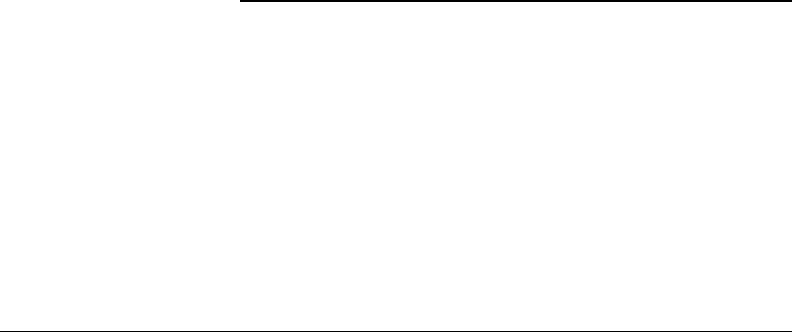
conventions.and.numbers.of.levels,.but.it.typically.comprises.four.to.six.functional.levels.as.depicted.
in.Figure.13.1..Along.with.the.denitions.of.functionalities—which.of.course.varied.according.to.the.
application.domain—networks.were.associated.to.the.individual.levels..Originally,.dierent.networks.
were.intended.for.these.purposes..In.recent.years,.however,.the.complexity.of.the.pyramid,.i.e.,.the.
number.of.levels.was.reduced.chiey.because.of.the.consolidation.process.that.took.place.in.the.eld.of.
networking.technologies..Today,.the.upper.levels.are.dominated.by.IP-based.networks.(mostly.on.the.
basis.of.Ethernet).and,.more.generally,.technologies.from.the.oce.domain,.whereas.the.lowest.level.is.
still.home.to.eld-level.networks.in.various.forms.
A
.critical.review.shows.that.the.CIM.approach.proposed.30.years.ago.practically.opped..ere.are.
niches.where.integration.became.tight.and.very.successful,.like.in.CAD/CAM.solutions.for.tooling.
machines.or.(micro)electronic.manufacturing..e.comprehensive.integration.of.all.levels.across.all.
possible.application.areas.however.failed,.and.still.today,.the.term.CIM.has.a.largely.negative.conno-
tation
.in.many.industries..e.reasons.for.the.spectacular.failure.of.a.basically.good.idea.are.mani-
fold:
.e.overall.concept.was.overloaded.and.far.too.ambitious..In.particular,.it.had.been.designed.
mostly.without.a.view.to.the.feasibility.of.implementation..In.fact,.the.concepts.did.not.show.much.
Process level
Shop oor level
Production level
Finance
controlling
Strategic
planning
Marketing
Development
engineering
Operative and
quality engineering
Stock
Production
Assembly
Shipping
Logistics
Control
Transport-
control
Cell
control
Machine
control
Packaging
control
Market
ERP SCM
Ethernet
Ethernet
Fieldbus/
industrial
ethernet
Fieldbus
Supplier
Production control
Company level
Field level
MES SCADA
FIGURE 13.1 Typical.functional.units.inside.a.contemporary.company.and.their.interrelation.with.the.automa-
tion
.hierarchy.as.well.as.associated.network.technologies.
© 2011 by Taylor and Francis Group, LLC
Vertical Integration 13-3
exibility.or.modularity.that.would.have.facilitated.their.adoption.by.industry..Rather,.it.was.more.
of.an.all-or-nothing.decision.to.be.taken..But.more.important,.critical.technological.elements.were.
simply.missing.or.in.a.premature.stage..Fieldbus.systems.as.low-level.networks.were.not.yet.widely.
known;.actually.the.CIM.concept.was.(also).a.stimulus.for.their.evolution..Microelectronics.had.not.
yet.produced.high.performance.and.aordable.processors.and.controllers,.and.IT.as.a.driving.force.in.
networking.was.not.yet.a.determining.factor.
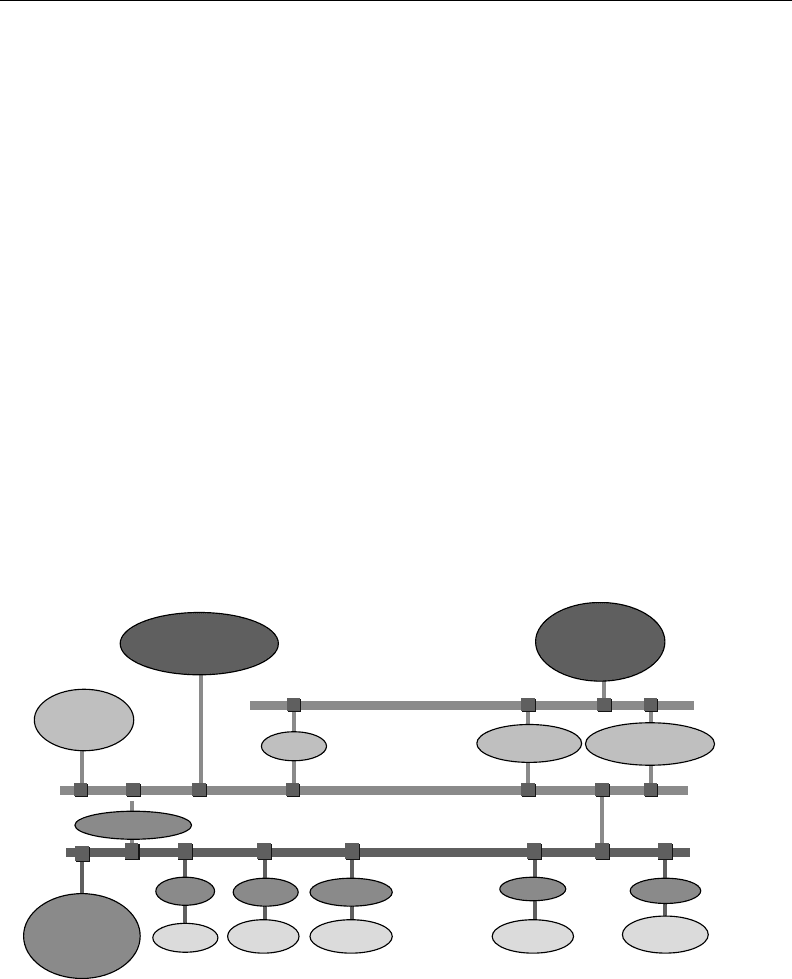
e
.timeline.in.Figure.13.2.presents.a.few.technological.milestones.in.the.evolution.of.IT.and.net-
working
.concepts.and.compares.them.with.the.introduction.of.various.application.concepts.relevant.
for.the.implementation.of.vertical.integration..It.reveals.that.one.of.the.most.decisive.factors.also.for.
automation.networks.was.the.denition.if.the.ISO/OSI.model.in.the.late.1970s..is.reference.model.
was.(and.still.is).the.starting.point.for.the.development.of.many.complex.communication.protocols..e.
rst.application.of.the.OSI.model.to.the.domain.of.automation.was.the.denition.of.the.Manufacturing.
Automation.Protocol.(MAP),.which.was.the.communication.technological.foundation.of.CIM..MAP.
was.intended.to.be.a.framework.for.the.comprehensive.control.of.industrial.processes,.and.the.result.of.
the.denition.was.a.powerful.and.exible,.but.overly.complex.protocol.that.was.not.accepted..e.tight-
ened
.standard.Mini-MAP.did.not.have.the.anticipated.success.either;.however,.it.introduced.a.reduced.
three-layer.communication.model.that.became.the.golden.model.for.most.eldbus.systems.[S05]..What.
did.have.success.was.Manufacturing.Message.Specication.(MMS)..It.dened.the.cooperation.of.vari-
ous
.automation.components.by.means.of.abstract.objects.and.services.and.was.used.as.a.starting.point.
for.other.eldbus.denitions.
What
.Figure.13.2.clearly.shows.is.that.CIM.in.its.original.denition.came.far.too.early..e.golden.
era.of.the.eldbus.was.the.late.1980s.and.especially.the.1990s.with.lots.of.dierent.systems.and.erce.
struggles.in.the.international.standardization.committees..Although.eldbus.systems.were.originally.
also.conceived.as.a.means.to.bridge.the.communication.gap.in.the.lower.levels.of.the.CIM.model,.
the.interconnection.aspect.was.gradually.le.aside.for.the.sake.of.simplicity..In.most.cases,.developers.
adopted.a.pragmatic.viewpoint.and.designed.eldbus.systems.as.isolated.networks.to.get.solutions.ready.
for.the.market..e.typical.end.point.for.vertical.communication.was,.therefore,.some.sort.of.control.
room,.located.on.the.cell.level.of.the.automation.pyramid.
e
.great.leap.forward—and.the.revival.of.the.integration.idea.under.a.new.name—came.with.the.
success.of.the.Internet.and,.in.particular,.with.the.invention.of.the.World.Wide.Web.(WWW)..Of.course,.
advances.in.microelectronics.provided.the.technological.backbone.for.the.processing.of.increasingly.
Industrial
ethernet
CIM Fieldbus and Internet
1970 1980 1990 2000
Information
technology
Fieldbus
systems
Planning
tools
Bitbus
MIL 1553
FIP
EN50170
IEC61158
Interbus
EN50254
ControlNet
CAN
WWW
ARPANET
Ethernet
FF
EN50325
IEC61784
DeviceNet
OPC
Powerlink
PROFINET
Modbus/TCP
MRP
IEEE488
GPIB
ISA SP50
MMS
MAP
ISO/OSI
Internet
Profibus
Modbus
Ethernet
EtherCAT
SCM
ERP
MRP II
MES
FIGURE 13.2 Selected.milestones.relevant.for.the.evolution.of.vertical.integration.
© 2011 by Taylor and Francis Group, LLC

13-4 Industrial Communication Systems
complex.communication.protocols..However,.from.the.user’s.point.of.view,.it.was.the.sheer.simplicity.
of.the.web.brow
ser
.conc
ept
.that.was.so.appe
aling.
.is.tool.is.easy.to.use,.plat
form
.inde
pendent,
.and.
allo
ws
.to.acce
ss
.dist
ant
.sites.and.data.in.a.near
ly
.triv
ial
.mann
er.
.It.is.no.wond
er
.that.the.easy.way.of.
navi
gating
.thro
ugh
.hype
rtext
.docu
ments
.in.the.Inte
rnet
.was.soon.take
n
.as.a.mode
l
.for.the.(rem
ote)
.
acce
ss
.to.autom
ation
.data
,
.and.actu
ally
.many.solu
tions
.avai
lable
.on.the.mark
et
.today.rely.on.WWW.
tech
nology
.and.web.brow
sers
.as.an.inte
rface.
.Still
,
.the.impr
ession
.that.“the.Inte
rnet”
.natu
rally
.enta
ils
.a.
unif
orm
.way.of.remo
te
.acce
ss
.to.autom
ation
.netw
orks
.is.dece
ptive.
.e.user.inte
rface
.is.only.one.aspe
ct,
.
the.unde
rlying
.mech
anisms
.and.data.stru
ctures
.are.anot
her.
.In.fact
,
.when.it.come
s
.to.impl
ementing
.an.
inte
rconnection
.betw
een
.IP-ba
sed
.netw
orks
.and.a.eld
bus,
.ther
e
.is.a.surp
rising
.vari
ety
.of.possi
bilities
.
even.in.the.so.much.“sta
ndardized”
.Inte
rnet
.envi
ronment.
.In.part
icular,
.the.web-b
ased
.appr
oach
.is.by.
no.mea
ns
.the.onl
y
.one
.
e
.very.rece
nt
.year
s
.brou
ght
.agai
n
.a.tech
nology
.push.in.eld
-level
.netw
orking.
.Toge
ther
.with.the.
last.phas
e
.of.eld
bus
.stan
dardization,
.Ether
net
.solu
tions
.for.indu
strial
.use.appe
ared
.at.the.turn.of.the.
cent
ury.
.One.of.the.main.argu
ments
.for.thei
r
.intr
oduction
.was.the.prom
ising—vertical—integration
.
possi
bility
.in.comp
any
.LANs
.
.Alth
ough
.mark
eting
.camp
aigns
.trie
d
.to.pain
t
.a.brig
ht
.futu
re
.of.Ether
net
.
solv
ing
.all.prob
lems
.in.vert
ical
.inte
gration,
.stan
dard
.Ether
net
.obvi
ously
.lack
s
.real
-time
.capa
bilities,
.
whic
h
.is.an.obst
acle
.for.eld
-level
.use..As.a.resp
onse
.to.thes
e
.dec
iencies,
.new.real
-time
.netw
orks
.base
d
.
on.Ethe
rnet
.were.deve
loped
.that.brok
e
.with.the.orig
inal
.den
ition
.and.can.be.expec
ted
.to.repl
ace
.sever
al
.
of.toda
y’s
.el
dbus
.sys
tems
.in.the.lon
g
.run
.
What
.does.all.this.mean.for.vertical.integration?.From.a.technology.point.of.view,.all.basic.elements.
need
ed
.are.nal
ly
.avai
lable—contrary
.to.the.situa
tion
.in.the.CIM.era..What.is.requ
ired
.today.is.to.put.
them.toget
her
.in.a.reas
onable
.way..e.tech
nological
.issu
es
.invo
lved
.are.consi
dered
.in.the.subs
equent
.
sect
ions.
.A.furt
her
.chal
lenge
.lurk
s
.in.the.appl
ication
.leve
l.
.Figu
re
.13.1.also.show
s
.how.typi
cal
.func
tional
.
unit
s
.are.asso
ciated
.with.the.indi
vidual
.leve
ls.
.It.appe
ars
.that.vert
ical
.inte
gration
.is.reas
onably
.adva
nced
.
in.both.the.uppe
r
.and.lowe
r
.laye
rs.
.is.is.not.surp
rising
.since.the.two.sect
ions
.mirr
or
.two.die
rent
.
worl
ds
.insi
de
.a.com
pany:
•
. Busin
ess-oriented
.appl
ications
.like.ente
rprise
.reso
urce
.plan
ning
.(ERP
)
.tools
,
.supp
ly
.chai
n
.man-
a
gement
.(SCM
),
.or.nan
cial
.tools.for.acco
unting
.and.book
keeping
.are.tigh
tly
.inte
grated
.today
.
.
e.users.as.well.as.the.developers.of.such.soware.tools.share.an.economics.background.and.are.
focu
sed
.on.a.str
ategic
.vie
w
.of.the.com
pany.
•
. Produ
ction-oriented
.appl
ications
.like.supe
rvisory
.cont
rol
.and.data.acqu
isition
.(SCA
DA),
.prod
uc-
tion
.cont
rol,
.assem
bly,
.or.to.a.cert
ain
.exte
nt
.also.manu
facturing
.execu
tion
.syst
ems
.(MES
)
.belo
ng
.
to.the.oper
ational
.worl
d.
.Agai
n,
.they.are.most
ly
.well.inte
grated,
.but.the.back
ground
.of.users.and.
deve
lopers
.is.typi
cally
.engi
neering,
.whic
h
.stip
ulates
.an.enti
rely
.die
rent
.view.on.the.over
all
.syst
em.
Figure
.13.1.demo
nstrates
.that.thes
e
.two.worl
ds
.are.also.sepa
rated
.by.die
rent
.netw
orking
.conc
epts.
.
In.the.busin
ess
.cont
ext,
.LANs.are.pred
ominant
.wher
eas
.the.cont
rol
.leve
l
.is.home.of.the.eld
bus.
.Agai
n,
.
this.is.not.surp
rising
.beca
use
.one.of.the.major.desig
n
.guid
elines
.for.eld
bus
.syst
ems
.was.the.reco
gni-
tion
.that.in.a.(rea
l-time)
.proc
ess
.cont
rol
.cont
ext,
.comp
letely
.die
rent
.netw
orking
.char
acteristics
.are.
requ
ired
.than.in.the.(str
ategic)
.oce.worl
d.
.Henc
e,
.the.gap.to.brid
ge
.today.not.only.conc
erns
.the.link
ing
.
of.two.di
erent
.net
work
.typ
es
.but.als
o
.the.int
erconnection
.of.two.di
erent
.min
dsets.
13.3 Network Interconnections
e.implementation.of.communication.networks.has.been.designed.for.particular.levels.of.the.commu-
nication
.hier
archy,
.using.dedi
cated
.I/O.buse
s
.and.eld
buses
.at.the.lowe
st
.leve
l.
.Typi
cally,
.inte
rmediate
.
leve
ls
.have.been.using.othe
r,
.tail
ored
.comm
unication
.syst
ems
.up.to.the.high
est
.leve
l.
.Proc
ess
.data.has.
been.abst
racted
.and.proc
essed
.from.leve
l
.to.leve
l.
.Netw
ork
.inte
rconnections
.usua
lly
.serv
ed
.hori
zontal
.
comm
unication,
.i.e.,.the.exch
ange
.of.data.on.the.same.leve
l
.in.the.hier
archy,
.most
ly
.with
in
.the.same.
tech
nological
.dom
ain.
© 2011 by Taylor and Francis Group, LLC
Vertical Integration 13-5
e.requirements.for.vertical.access.to.data.throughout.the.various.communications.levels.require.
a.higher.level.of.interconnection..Here,.dierent.communication.media,.dierent.networking.proto-
cols,
.and.dierent.topologies.have.to.be.connected..Among.other.technologies,.the.use.of.Ethernet.and.
IP-based.protocols.serves.as.the.major.integration.platform.of.today’s.automation.systems..IP-based.
systems.possess.the.special.appeal.that.communication.can.be.established.using.the.public.Internet.
infrastructure,.avoiding.costly.and.proprietary.phone.lines.or.data.links..A.set.of.approaches.are.imple-
mented
.that.lead.to.tighter.vertical.integration:
•
. Flat network hierarchy:.While.staying.within.the.same.technology.domain,.vertical.access.can.
still.be.limited.due.to.dierent.physical.media.and.network.partitioning.into.islands..A.at.net-
work
.hierarchy.eliminates.those.boundaries..Routers.and.tunneling.routers.are.used.today.for.
interconnecting.formerly.isolated.trunks.of.eldbus.networks.
•
. Cross-domain communication:.A.number.of.systems.have.been.designed.to.be.specic.to.their.
application.domain..It.is.common.that.separate.systems.are.found.for.heating,.ventilation,.and.
air-conditioning.(HVAC).and.emergency.lighting.in.building.automation..e.former.advantage.
of.separating.the.installation.and.engineering.tasks.is.now.becoming.a.burden.for.communica-
tion
.between.those.domains..For.gaining.access.to.dierent.domains,.proxies.are.used.
•
. Protocol convergence:.Providing.protocol,.service,.and.data.translation.between.dierent.network-
ing
.technologies.is.necessary.to.fully.distribute.services.around.the.automation.system..Vertical.
access.through.all.levels.requires.a.gateway.approach..ese.gateways.translate.the.high-level.
services.between.the.dierent.technologies.
ere
.is.a.tendency.to.eliminate.the.separation.between.the.automation.and.management.network,.
and.the.implied.dierences.in.network.media..In.some.cases,.even.the.eldbus.level.is.integrated.into.the.
same,.global.network.domain..e.technology.of.choice.today.is.the.IP.transport.over.Ethernet’s.struc-
tured
.cabling..It.also.brings.the.networks.of.building.automation.systems.(BAS).and.factory.automation.
networks.closer.to.the.IT.network,.which.has.formerly.been.separated..For.doing.so,.most.of.the.widely.
deployed.networks.have.specied.and.implemented.an.IP-based.transport.layer.(CEA-852.for.LonWorks.
[CEA852],.KNX/IP.[KNXIP],.BACnet/IP.[BACIP],.Modbus/IP.[ModIP]).
In
.general,.this.reduces.cabling.eorts.and.increases.maintainability..In.the.eld,.however,.the.advan-
tages
.of.special.eldbus.media.still.persist:.First,.for.the.ease.of.installation,.where.free.topology.allows.
to.install.cabling.tting.more.closely.to.the.nodes.in.a.room,.and.second,.for.better.extendibility..e.
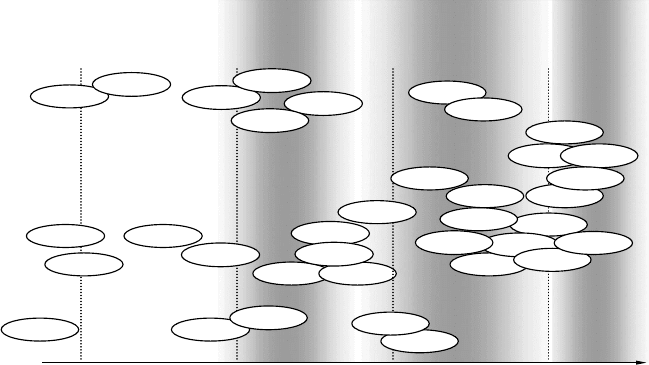
remaining. trunks. are.coupled. via.control.network/IP.(CN/IP). routers..ese.routers.are.tunneling.
routers,.which.encapsulate.the.native.frame.formats.into.IP.transport..is.architecture.is.depicted.in.
Figure.13.3..e.advantage.of.tunneling.is.that.eldbus.nodes.can.be.le.unmodied,.i.e.,.do.not.need.
to.implement.an.IP.stack..e.tunneling.routers.are.store-and-forward.routers,.which.can.additionally.
perform.selective.forwarding..is.means,.the.trac.is.not.broadcast.over.the.IP.network.but.routed.
precisely.to.the.designated.tunneling.routers.based.on.CN.addressing.information..Other.high-end.
nodes.such.as.powerful.building.controllers.or.SCADA.systems.can.implement.the.tunneling.protocol.
CN/IP
router
CN/IP
router
CN/IP
router
Intranet (Ethernet)
IP-based
control
node
Control network
Control network
Control network
FIGURE 13.3 System.with.tunneling.CN/IP.routers.
© 2011 by Taylor and Francis Group, LLC
13-6 Industrial Communication Systems
themselves.and.process.the.encapsulated.trac.as.a.node,.not.as.a.router..is.eectively.enables.purely.
IP-b
ased
.el
dbus
.nod
es,
.whi
ch
.can.com
municate
.dir
ectly
.to.leg
acy
.(no
n
.IP-b
ased)
.nod
es
.in.the.sys
tem.
.
e.tu
nneling
.ap
proach
.ha
s
.be
en
.ch
osen
.fo
r
.Lo
nWorks
.or.KN
X/IP.
Other
.el
dbus
.sys
tems
.imp
lement
.a.ded
icated
.IP.dat
a
.lin
k
.lay
er
.for.the.el
dbus
.pro
tocol
.nat
ively.
.
Nod
es
.in.the
se
.sys
tems
.can.be.con
nected
.dir
ectly
.onto.the.Ethe
rnet
.net
work
.wit
hout
.the.use.of.a.tun
nel-
ing
.tec
hnique.
.Exa
mples
.are.BAC
net/IP
.or.Mod
bus
.ove
r
.TCP
.
.To.acc
ess
.oth
er,
.non.IP-b
ased
.CN.nod
es,
.
rou
ters
.ar
e
.us
ed.
Notwithstanding
.the.eas
e
.of.IP.eve
rywhere,
.a.sep
aration
.of.el
d-level
.and.oc
e-level
.net
works
.is.sti
ll
.
rec
ommended
.for.per
formance
.and.sec
urity
.rea
sons,
.eve
n
.if—
as
.in.the.cas
e
.of.ind
ustrial
.Ethe
rnet—a
.
dir
ect
.int
egration
.of.bot
h
.net
works
.is.pos
sible.
.Ano
ther
.iss
ue
.in.usin
g
.IP-b
ased
.tra
nsport
.sys
tems
.for.
el
dbus
.pro
tocols
.is.tha
t
.the.ori
ginal,
.nat
ive
.com
munication
.med
ia
.had.par
tly
.di
erent
.pro
perties.
.
For.exa
mple,
.del
ay
.tim
es,
.del
ay
.var
iance,
.and.pac
ket
.ord
ering
.may.imp
air
.the.el
dbus
.pro
tocol
.sta
te
.
mac
hine
.its
elf.
.es
e
.ee
cts
.are.typ
ically
.comb
ated
.by.usin
g
.ext
ra
.seq
uence
.numb
ers
.and.syn
chronized
.
tim
e-stamping
.on.the.tun
nel.
.Onc
e
.the.pro
tocol
.sta
te
.mac
hines
.are.mai
ntained,
.the.app
lication
.on.
top.is.sti
ll
.in
uenced
.in.its.desi
gn.
.App
lication
.tim
ers
.or.fee
dback
.con
trol
.loo
ps
.mus
t
.be.awa
re
.of.the.
cha
nged
.ti
ming
.re
lations.
Once
.the.pro
blem
.of.mer
ging
.iso
lated
.net
work
.isl
ands
.into.a.at.net
work
.hie
rarchy
.is.sol
ved,
.log
ical
.
bou
ndaries
.wit
hin
.the.sam
e
.net
working
.tec
hnology
.sti
ll
.exi
st.
.es
e
.are.typ
ically
.imp
osed
.by.di
erent
.
app
lication
.dom
ains
.to.kee
p
.the.tra
c,
.add
ressing,
.and.ins
tallation
.tas
ks
.sep
arated.
.Whi
le
.com
munica-
tion
.would.be.enabled.over.the.at.network,.the.domain.boundary.bars.trac..e.use.of.proxy.devices.
sol
ves
.thi
s
.pro
blem.
.Pro
xies
.are.basi
cally
.dev
ices
.tha
t
.pas
s
.the.pro
cess
.dat
a
.and.exp
ose
.it.fro
m
.one.
dom
ain
.into.ano
ther.
.An.imp
lementation
.of.a.pro
xy
.is.pla
ced
.as.one.ins
tance
.in.eac
h
.dom
ain.
.Stri
ctly
.
spe
aking,
.a.pro
xy
.can.be.see
n
.as.a.gat
eway
.bet
ween
.the.sam
e
.tec
hnologies.
.An.exa
mple
.for.usin
g
.pro
xies
.
is.Lon
Works
.in.auto
mation
.sys
tems.
.In.thi
s
.sys
tem,
.add
ress
.spa
ces
.are.sep
arated
.by.add
ress
.dom
ains.
.
e.add
ress
.dom
ains
.are.set.up.acc
ording
.to.di
erent
.app
lication
.dom
ains,
.suc
h
.as.HVA
C
.or.eme
rgency
.
lig
hting.
.A.Lon
Works
.pro
xy
.can.exp
ose
.dat
a
.poi
nts
.of.one.dom
ain
.to.ano
ther
.dom
ain.
.Oth
er
.exa
mples
.
of.pro
xies
.are.HTT
P
.pro
xies.
.es
e
.are.fre
quently
.use
d
.to.iso
late
.loc
al
.fro
m
.pub
lic
.IP.tra
c
.for.sec
urity
.
rea
sons.
.For.ins
tance,
.the.oc
e-level
.net
work
.nee
ds
.acc
ess
.to.Web.ser
vices
.in.the.el
d-level
.net
work.
.
Whi
le
.it.is.com
mon
.pra
ctice
.to.kee
p
.tho
se
.two.IP.net
works
.sep
arate,
.an.HTT
P
.pro
xy
.can.est
ablish
.the.
Web.se
rvice
.li
nk.
Another
.are
a
.of.foc
us
.is.pro
tocol
.con
vergence.
.Tod
ay’s
.auto
mation
.sys
tems
.rep
resent
.hig
hly
.het
ero-
geneous
.sys
tems.
.Di
erent
.app
lication
.ser
vice
.dom
ains
.may.use.di
erent
.CN.tec
hnologies.
.e.goa
l
.
for.ver
tical
.acc
ess
.or.dis
tribution
.of.com
munication
.ser
vices
.is.cle
arly
.a.sea
mless
.com
munication
.als
o
.
bet
ween
.th
e
.ap
plication
.do
mains
.an
d
.ac
ross
.al
l
.la
yers
.of.th
e
.au
tomation
.sy
stem.
.e.cl
assical
.ap
proach
.
to.let.sys
tem
.A.com
municate
.wit
h
.sys
tem
.B.is.the.use.of.gat
eways.
.is.con
cept
.is.bei
ng
.ado
pted
.wid
ely.
.
Gat
eways
.abs
tract
.the.net
work
.ser
vice
.at.the.app
lication
.lev
el
.(e.
g.,
.dat
a
.poi
nt
.val
ues,
.tre
nd
.dat
a,
.sch
ed-
ules,
.and.ala
rms)
.and.rep
resent
.it.in.di
erent
.net
working
.tec
hnologies.
.Com
monly
.use
d
.gat
eway
.con
-
cepts
.toda
y
.are.bas
ed
.on.mon
olithic
.gat
eways.
.es
e
.are.dev
ices
.tha
t
.hav
e
.the.glo
bal
.vie
w
.of.one.sys
tem
.
and.exp
ose
.it.to.ano
ther
.sys
tem.
.is.con
cept,
.how
ever,
.pre
sents
.an.inh
erent
.pro
blem:
.e.com
plexity
.
to.int
egrate
.an.arb
itrary
.numb
er
.of.sys
tems
.is.of.qua
dratic
.ord
er.
.Ano
ther
.pro
blem
.is.tha
t
.the.gat
eway
.
is.a.sin
gle
.po
int
.of.fa
ilure
.(S
POF)
.in.th
e
.sy
stem.
In
.the.mov
e
.to.a.mor
e
.ser
vice-oriented
.mod
el,
.the.com
munication
.ser
vices
.suc
h
.as.dat
a
.poi
nts,
.
sch
eduling,
.tre
nding,
.or.ala
rming
.can.be.abs
tracted
.and.pre
sented
.in.a.sing
le
.int
erface,
.whi
ch
.is.tec
h-
nology
.ind
ependent
.[DP
AL].
.App
lications
.dev
eloped
.on.suc
h
.dev
ices
.use.the.abs
tracted
.int
erface
.and.
are.ess
entially
.mad
e
.ind
ependent
.fro
m
.the.und
erlying
.net
working
.sys
tem.
.It.is.imp
ortant
.to.not
e
.tha
t
.
thi
s
.app
roach
.is.onl
y
.fea
sible
.for.act
ual
.dat
a
.com
munication,
.not.the.con
guration
.of.suc
h
.dev
ices,
.
whi
ch
.st
ill
.re
mains
.te
chnology
.sp
ecic.
As
.com
puting
.pow
er
.is.rea
dily
.ava
ilable,
.dev
ices
.can.add.ano
ther
.net
work
.pro
tocol
.sta
ck
.to.pro
vide
.
nat
ive
.acc
ess
.to.cer
tain
.ser
vices
.to.the.sys
tem
.of.ano
ther
.tec
hnology.
.Fig
ure
.13.
4
.pre
sents
.an.exa
m-
ple
.for.thi
s
.sce
nario.
.A.con
troller
.imp
lements
.not.onl
y
.the.Lon
Works
.tec
hnology
.but.als
o
.the.BAC
net
.
© 2011 by Taylor and Francis Group, LLC
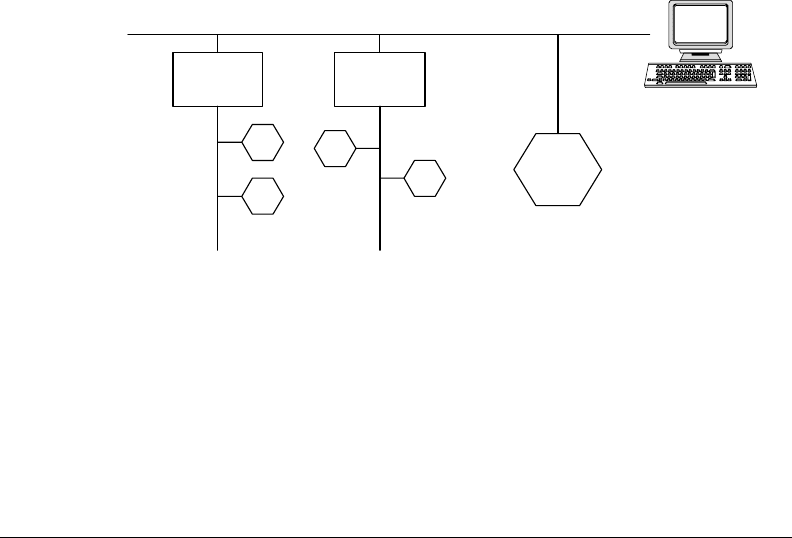
Vertical Integration 13-7
technology.(multi-protocol.device)..is.way,.the.eldbus.node.A.can.directly.retrieve.process.data.from.
the.controller..Nodes.B.and.C,.which.do.not.need.access.to.the.respective.other.network.technology,.can.
still.be.accessed.by.the.operator.workstation’s.native.protocol..No.additional.gateway.is.needed.as.the.
area.of.overlap.does.contain.the.needed.technologies..A.given.number.of.those.multi-protocol.devices.
can.be.seen.as.a.distributed.gateway..is.means.the.SPOF.has.been.eliminated..Also,.the.complexity.of.
gateway.conguration.is.reduced.as.the.nodes.know.already.about.their.data.points.natively..Clearly,.not.
all.nodes.can.be.equipped.with.an.arbitrary.number.of.networking.technologies.
13.4 application View
An.important.aspect.of.vertical.integration.is.the.interconnection.of.the.soware.application.frame-
works
.that.are.needed.for.the.individual.levels.of.the.automation.hierarchy..From.today’s.view,.the.link.
between.the.top-level.strategic.planning.and.administration.tools.usually.comprised.in.ERP.systems.
and.the.distributed.control.systems.on.the.factory.oor.is.to.be.seen.in.the.MES.concepts.that.translate.
the.overall,.mainly.long-.and.mid-term.plans.into.short-term.work.and.production.orders..To.achieve.
this.integration,.there.is.still.work.to.be.done.[V02]..In.the.context.of.enterprise.engineering,.the.current.
focus.is.on.ecient.modeling.languages.and.techniques,.on.analysis.methods,.and.advanced.computer-
based
.tools.[MPZM03].
An
.eminent.role.is.played.by.standardization..e.more.CIM.and.its.successors.found.the.approval.of.
industry,.the.more.it.became.apparent.that.only.concerted.actions.could.nally.produce.results.with.a.high.
application.potential..Standards.generally.provide.the.basis.for.durable.solutions.and.nally.products,.
which.is.particularly.important.in.such.complex.areas.as.the.integration.of.rather.diverse.functions.inside.
an.enterprise..Aer.all,.the.problems.of.enterprise.integration.in.actual.practice.are.not.so.much.the.func-
tional
.modules.as.such.(the.ERP,.MES,.SCADA.systems.in.all.their.varieties).but.the.interfaces.between.
them..Only.standardized.interfaces.together.with.appropriate.functional.models.for.the.application.pro-
cesses
.and.their.data.objects.ultimately.allow.for.interoperability.between.solutions.from.dierent.vendors.
Consequently,
.work.being.done.in.various.standardization.groups.covers.all.aspects.ranging.from.
the. provision. of. modeling. frameworks. and.languages. through. concrete. reference. and.data. models.
for.enterprise.systems.or.subsystems.down.to.standards.for.IT.services.and.infrastructures.[CV04]..
Among.the.many.standards.developed.in.this.context,.the.two.most.relevant.for.this.chapter.are.the.
Manufacturing.Execution.Systems.Association.(MESA).model.and,.in.particular,.the.ISA.S95.Standard.
for.Enterprise-Control.System.Integration,.both.of.which.have.already.been.widely.adopted.as.a.refer-
ence
.for.the.implementation.of.vertical.integration.on.the.higher.level.of.the.automation.hierarchy.[S07].
MESA
.provided.a.denition.of.11.distinct.functional.areas.of.MES.that.cover.the.basic.informa-
tion
.needed.to.run.any.type.of.plant—much.in.contrast.to.ERP.systems.that.have.no.clearly.dened.
functionalities..is.model.has.become.an.essential.starting.point.for.many.MES.tools.currently.on.the.
market..e.purpose.of.ISA.S95,.on.the.other.hand,.is.to.dene.the.interface.between.control.functions.
Field
level
Operator
workstation
CEA-852 and BACnet/IP
BACnet
LonWorks
C
B
A
Network 1
Network 2
IP backbone
Management
level
Multi-
protocol
device
LonWorks +
BACnet
BACnet
router
CEA-852
router
FIGURE 13.4 Protocol.convergence.using.multi-protocol.gateways.
© 2011 by Taylor and Francis Group, LLC
13-8 Industrial Communication Systems
and.other.enterprise.functions,.eectively.between.the.ERP.and.MES.levels.of.an.enterprise..e.scope.
of.the.standardization.work,.as.seen.by.the.committee,.is
•
. Dene.in.detail.an.abstract.model.of.the.enterprise,.including.manufacturing.control.functions.
and.business.functions,.and.its.information.exchange.
•
. Establish.common.terminology.for.the.description.and.understanding.of.enterprise,.including.
manufacturing.control.functions.and.business.process.functions,.and.its.information.exchange.
•
. Dene.electronic.information.exchange.between.the.manufacturing.control.functions.and.other.
enterprise.functions.including.data.models.and.exchange.denitions.
ISA
.S95.addresses.exclusively.the.information.ow.between.the.control.domain.and.the.enterprise.
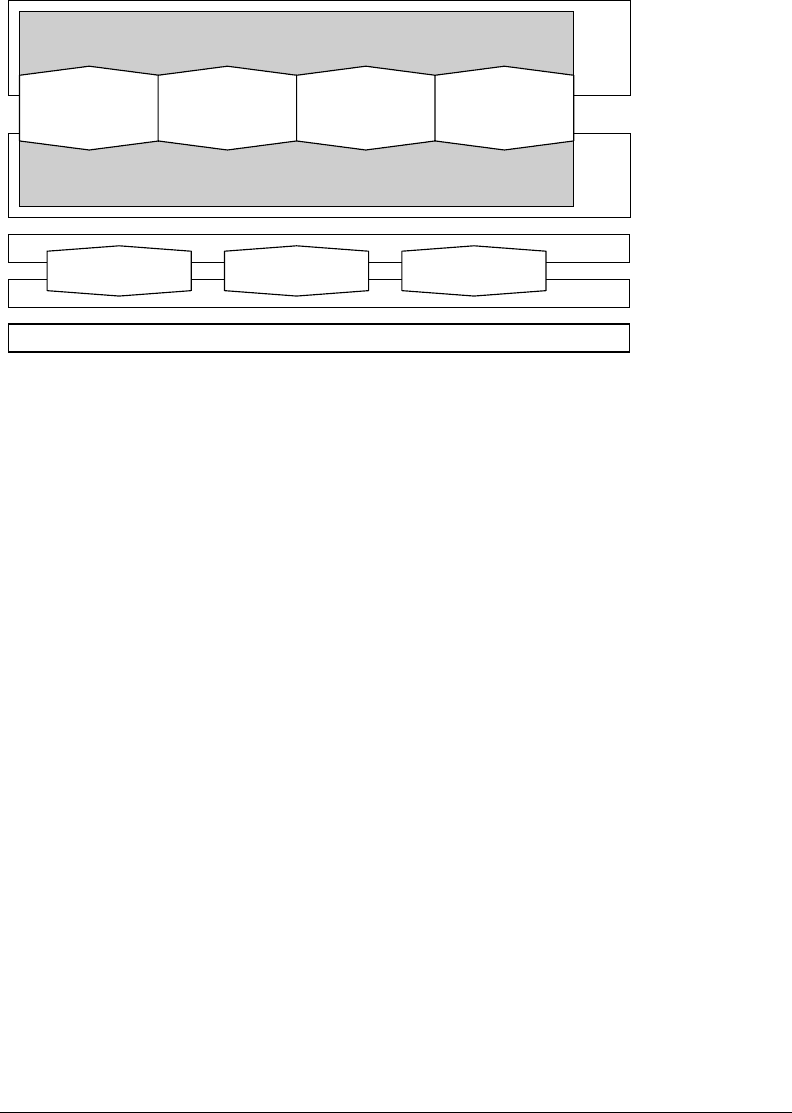
domain.of.a.company..Consequently,.in.the.model.adopted.by.ISA,.the.MES.functionality.is.explicitly.
included.in.the.control.domain.(Figure.13.5)..e.information.exchanged.between.the.levels.can.be.cat-
egorized
.in.information.about.the.product.itself.(its.denition),.the.availability.of.production.capabilities,.
and.the.production.of.the.product.itself.(scheduling.and.performance.information)..Functions.concerning.
only.the.ERP.level.or.the.control.level.are.beyond.the.scope.of.the.standard.and.are.therefore.not.covered.
ISA
.S95.should.be.regarded.in.connection.with.ISA.S88.(Batch.processing.model),.which.covers.the.
lower.levels.of.the.automation.model..Both.have.been.developed.in.parallel,.and.they.are.converging.in.
that.there.are.direct.mappings.between.the.two.standards.for.models.and.representations..Likewise,.
the.reference.model.suggested.by.MESA.has.inuenced.the.work,.and.cross.references.between.the.two.
approaches.are.given.in.order.to.facilitate.common.understanding.
e
.standard.does.not.describe.an.actual.implementation;.it.provides.only.terminology,.functional.
requirements,.and.formal.models..Yet,.inside.the.standardization.group,.the.common.belief.was.that.
XML.might.be.a.promising.approach..Consequently,.a.working.group.was.formed.under.the.umbrella.
of. the. World. Batch. Forum,. and. developed. the. XML. schema. “Business. to. Manufacturing. Markup.
Language”.(B2MML)..is.reference.implementation.was.released.in.a.rst.version.in.2002.and.is.con-
stantly
.being.updated.and.enhanced.
13.5 Security aspects in Vertical Integration
Vertical.integration.in.the.sense.of.connecting.automation.systems.to.a.more.open.environment.natu-
rally
.raises.security.questions..It.has.already.been.stated.that.even.though.network.interconnection.was.
an.essential.goal.of.the.old.CIM.idea,.fieldbus.systems.were.mostly.developed.as.isolated.solutions..
Level 1
Level 2
Level 3
MES
Level 4
ERP
Manufacturing operations management
Dispatching, detailed production scheduling, production tracking, etc.
Business logistics
Plant production scheduling, shipping, receiving, inventory, etc.
Production capability
information
(what is available
for use)
Product definition
information
(how to make
a product)
Production schedule
(what to make
and use)
Production
performance
(what was made
and used)
Batch production
control
Continuous
production control
Discrete production
control
ISA—IEC/ISO
interface standards
ISA 95.01
ISA 95.02
ISA functional model
ISA 95.03
IEC, OPC interface
standards
Level 0
FIGURE 13.5 Scope.of.ISA.95.and.ISA.88.
© 2011 by Taylor and Francis Group, LLC
Vertical Integration 13-9
As. the.timeline.in. Figure. 13.2.shows,. most.of. these. developments. were. concluded.long. before.the.
Internet.became.known.and.was.widely.employed.by.the.broad.public..It.is.thus.no.wonder.that.security.
considerations.never.played.a.prominent.role.in.automation.before.the.end.of.the.1990s.[D97,PS00].
e
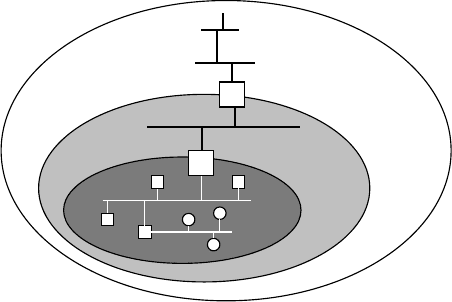
.most.promising.approach.to.cope.with.the.heterogeneity.of.the.networks.is.a.hierarchical.security.
model.following.the.defense-in-depth.approach..Figure.13.6.shows.the.three.typical.interconnection.
zones.in.the.company.network..e.zones.are.separated.from.each.other.by.dedicated.network.nodes.
that.can.be.used.as.anchor.points.for.the.security.strategy..e.inner.connection.node.(access.point).to.
the.actual.eldbus.is.the.gateway.or.proxy.already.discussed.in.Section.13.3.
As
.existing.standards.cannot.be.changed,.the.only.viable.option.for.the.eld.level.is.to.use.the.eld-
bus
.simply.as.a.transport.channel.and.to.tunnel.secure.packets.over.standard.eldbus.protocols.and.
services.[SS02]..Such.an.application-level.approach.could.easily.achieve.end-to-end.security,.which.is.
desired.in.most.applications,.anyway..Unfortunately,.it.is.likely.to.cause.problems.with.interoperability.
unless.all.nodes.in.the.network.adhere.to.this.enhanced.standard,.i.e.,.a.mixture.of.secure.and.insecure.
devices.would.normally.not.be.feasible..In.addition,.the.limited.messages.size.in.some.eldbuses.leaves.
only.little.room.for.the.additional.data.blocks.required.by.ecient.security.extensions..is.problem.is.
similar.to.the.one.encountered.in.IP.tunneling.discussed.in.Section.13.3.
e
.access.point.itself.has.so.far.been.the.focal.point.of.interest.for.most.researchers..Given.the.lack.
of.general.eld-level.security,.it.is.the.only.part.of.the.automation.system.(apart.from.the.Internet.side).
where.security.can.easily.be.applied..One.very.common.approach.is.to.combine.the.access.point.with.a.
rewall,.which.is.the.most.widely.employed.security.measure.in.the.design.of.network.interconnections.
today.even.in.the.eld.of.automation.[D97]..Indeed,.the.term.“rewall”.is.nowadays.frequently.used.as.a.
synonym.for.network.security..In.practice,.however,.their.application.is.not.so.straightforward..Owing.
to.the.inherently.asymmetric.operation.of.a.rewall.(transparent.from.the.private.network,.opaque.
from.outside),.it.is.dicult.to.place.a.standard.rewall.in.front.of.a.eldbus.access.point;.it.is.better.to.
tightly.integrate.the.rewall.into.the.access.point.and.use,.e.g.,.port.forwarding.to.control.the.trac.
[PS00]..On.top.of.this,.the.access.point.is.also.the.ideal.point.to.control.and.manage.access.to.the.eldbus.
zone..A.suitable.model.for.handling.access.rights.is.role-based.access.control,.where.all.communication.
partners.(users,.devices,.tools).are.associated.with.particular.roles.depending.on.the.context.of.the.data.
exchange..In.the.IT.world,.this.concept.is.widely.employed,.and.it.can.also.be.used.in.an.automation.
context.[WB04].
Security
.in.the.Internet.nally.is.a.well-researched.topic.with.a.large.number.of.meanwhile.very.
mature.solutions..In.fact,.for.nearly.all.Internet.application.layer.protocols,.secure.versions.exist,.or.
conventional.insecure.protocols.can.be.used.on.top.of.a.secure.transport.layer..is.standard.mecha-
nism
.of.rst.establishing.an.encrypted.channel.between.communication.partners.is.called.Transport.
Internet
Intranet
Fieldbus
AP
Firewall, network address translation
Firewall, role-based access
Reduced security, proprietary solutions
Controlled access (maintenance staff)
Frequent, automated attacks (port scans)
Standard IT solutions: VLANs, SSH, TLS
Main threat: malicious software
Restricted, controlled user group
FIGURE 13.6 Defense-in-depth.security.model.for.vertically.integrated.company.networks.
© 2011 by Taylor and Francis Group, LLC
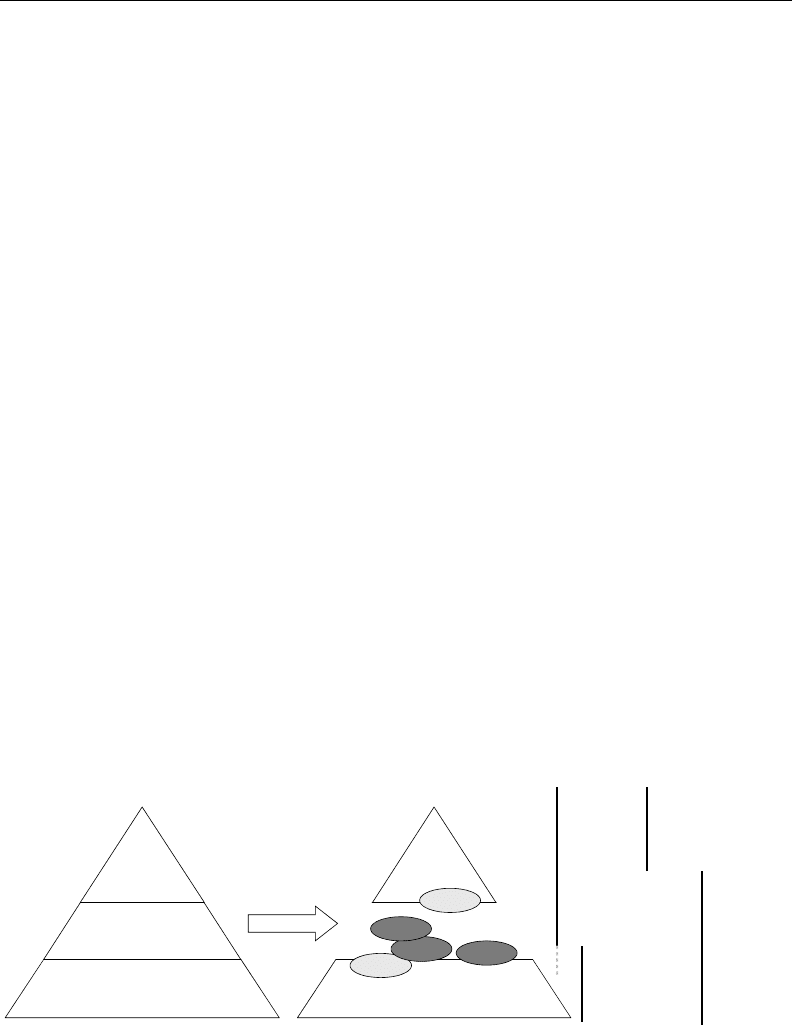
13-10 Industrial Communication Systems
Layer.Security.(TLS).and.is.transparent.to.the.application.protocol,.which.therefore.can.remain.mostly.
unchanged;.it.only.requires.the.initialization.of.a.secure.channel.by.negotiating.crypto.algorithms.and.
session.keys..As.soon.as.the.secured.connection.is.established,.the.application.protocol.can.start.
13.6 trends in Vertical Integration
Vertical.integration.has.come.a.long.way.since.its.rst.inception.in.the.CIM.era..is.chapter.tried.to.
shed.light.on.some.aspects,.by.far.not.all.of.them..An.important.recognition.is.that.the.recent.techno-
logical
.developments.not.only.stimulated.or.revived.the.old.idea,.they.accelerated.and.tightened.the.
integration..As.a.matter.of.fact,.the.large-scale.introduction.of.Internet.technologies.caused.the.multi-
level
.automation.pyramid.to.crumble.down.to.at.maximum.three.levels.(Figure.13.7)..e.company.level.
is.the.strategic.one;.a.further.subdivision.according.to.functional.domains.like.in.Figure.13.1.may.be.
useful;.from.a.technological.viewpoint,.however,.it.is.no.longer.necessary,.not.even.in.large.globalized.
enterprises..Internet.has.already.provided.the.means.to.fully.integrate.remote.branches.in.one.single.
corporate.network.with.one.common.management.or.planning.framework..From.the.many.operational.
levels,.only.two.remain:.the.actual.eld.level.with.the.process.control.devices.and.an.intermediate.level.
typically.for.controlling.purposes.
From
.the.networking.point.of.view,.there.are.in.fact.only.two.levels.le.today..In.the.oce.world.and.
the.upper.automation.level,.IP-based.networks.and.Ethernet.dominate..Even.if.eldbus.systems.still.
have.their.share.on.the.cell.level,.they.are.bound.to.vanish.within.the.next.few.years..It.is.the.eld.level.
that.will.still.belong.to.them,.maybe.with.some.additional.specialized.and.low-level.local.sensor/actua-
tor
.systems.integrated.via.controllers.acting.as.simple.gateways..Nevertheless,.the.recent.emergence.of.
real-time.Ethernet.extensions.already.sparked.new.competition.in.the.eld..In.the.long.run,.real-time.
industrial.Ethernet.will.oer.a.tempting.alternative.to.the.classical.eldbus.systems.and.will.most.prob-
ably
.make.one.or.the.other.obsolete.
But,
.also.from.the.application.point.of.view,.there.is.a.trend.toward.a.further.reduction.of.the.hierar-
chy.
.In.plant.automation,.which.was.traditionally.strictly.centralized.in.the.upper.two.levels,.modular.
concepts.are.becoming.popular..e.overall.goal.is.to.enhance.exibility.of.planning.systems.and.to.
allow.for.solutions.tailored.to.the.needs.of.the.customer..is.makes.ERP.and,.especially,.manufactur-
ing
.execution.tools.attractive.also.for.smaller.companies.that.so.far.could.not.benet.from.full-edged.
solutions..One.step.ahead.are.approaches.to.decentralize.essential.parts.of.the.planning.and.control.
functionality..Ideas.like.holonic.manufacturing.systems.or.agent-based.automation.practically.dissolve.
the.rigid.middle.layer.of.the.pyramid,.implementing.its.functionality.in.soware.agents.attached.to.the.
outer.levels.of.the.hierarchy.
is
.tendency.is.supported.by.complementary.trends.in.the.control.and.enterprise.eld:.In.the.long.
run,.control.devices.will.resemble.standard.PCs.in.terms.of.computing.resources.and.network.inter-
faces
.(Ethernet.and.IP)..us,.they.will.be.able.to.run.more.complex.planning.tasks..On.the.other.hand,.
MES and SCADA
(Cell level)
ERP
and SCM
(company level)
Control (PLCs, NCs)
(field level)
MES
MES and SCADA
(cell level)
ERP
and SCM
(company level)
Control (PLCs, NCs)
(field level)
IP-based
networks
Field area
networks
Strategic
level
Operational
levels
MES
MES
MES
MES
FIGURE 13.7 Decentralization.of.the.middle.level.in.a.typical.industrial.automation.context.
© 2011 by Taylor and Francis Group, LLC
