Wilamowski B.M., Irwin J.D. The Industrial Electronics Handbook. Second Edition: Industrial Communication Systems
Подождите немного. Документ загружается.

Prosafe 46-15
. 5.. IEC.61784,.Industrial.communication.networks—Proles—All.parts.
. 6.. IEC.61784-3,.Ind
ustrial
.communic
ation
.netw
orks—Proles—Part
.3:.Func
tional
.saf
ety
.eldb
uses—
General
.ru
les
.an
d
.pr
ole
.denit
ions.
. 7.. IEC. 617
84-3-3,
. Indu
strial
. com
munication
. net
works—Proles—Part
. 3-3
:
. Fun
ctional
. saf
ety
.
el
dbuses—Additional
.sp
ecications
.fo
r
.CPF.3.
. 8.. W..Str
ipf
.and.H..Bar
thel,
.Com
prehensive
.saf
ety
.wit
h
.PRO
FIBUS
.DP.and.PRO
FINET
.IO—Tra
ining
.
for.“P
ROFIsafe
.cert
ied
.design
ers”.
. 9.. Spe
cication
.PRO
FIsafe—Prole
.for.saf
ety
.tec
hnology,
.Versio
n
.1.30,.June.2004,.Order.No:.3.092,.
PRO
FIBUS
.In
ternational.
. 10.. IEC. 61000-1-1,. Elec
tromagnetic
.comp
atibility
.(EMC)—Pa
rt
.1:. Genera
l—Section
.1:. App
lication
.
and.int
erpretation
.of.fun
damental
.denit
ions
.an
d
.ter
ms.
. 11.. IEC. 61000-2-5,. Elec
tromagnetic
. comp
atibility
. (EMC)—Pa
rt
. 2:. Envir
onment—Section
. 5:.
Cla
ssication
.of.ele
ctromagnetic
.env
ironments,
.Ba
sic
.EMC.pu
blication.
. 12.. IEC. 613
26-3-1,
. Ele
ctrical
. equ
ipment
. for. mea
surement,
. con
trol
. and. lab
oratory
. use
—EMC
.
req
uirements—Part
. 3-1
:
. Imm
unity
. req
uirements
. for. saf
ety-related
. sys
tems
. and. for. equ
ip-
ment
. int
ended
. to. per
form
. saf
ety-related
. fun
ctions
. (fu
nctional
. saf
ety)—General
. ind
ustrial
.
app
lications.
. 13.. IEC.61511,.Func
tional
.saf
ety—Safety
.inst
rumented
.system
s
.for.the.pro
cess
.indu
stry
.sec
tor—All
.
par
ts.
. 14.. IEC.60204-1,.Safety.of.machinery—Electrical.equipment.of.machines—Part.1:.General.requirements.
. 15.. PRO
FINET
.Se
curity
.Guide
line,
.Ver
sion
.1.0,.Ma
rch
.2005.
. 16.. EN.999,.Safet
y
.of.machin
ery—e
.posit
ioning
.of.pro
tective
.equi
pment
.in.resp
ect
.of.app
roach
.spe
ed
.
of.pa
rts
.of.th
e
.hum
an
.bo
dy.
© 2011 by Taylor and Francis Group, LLC

47-1
47.1 Introduction
SafetyLon.is.a.safety-related.automation.technology.based.on.LonWorks.used.to.realize.a.safety-related.
comm
unication
.sys
tem.
.e.ide
a
.is.to.int
egrate
.saf
ety
.mea
sures
.into.the.exi
sting
.Lon
Works
.to.ens
ure
.a.
high.lev
el
.of.int
egrity.
e
.type.and.impl
ementation
.of.the.safe
ty
.meas
ures
.is.spec
ied
.by.the.requ
irements
.of.the.inte
r-
national
.stan
dard
.IEC.6150
8.
.It.is.nece
ssary
.that.a.malf
unction
.of.the.syst
em
.does.not.lead.to.seri
ous
.
cons
equences,
.such.as.inju
ry
.or.even.deat
h
.of.peop
le,
.with.a.very.high.prob
ability.
.Requ
irements
.and.
the.corr
esponding
.meas
ures
.have.a.grea
t
.impa
ct
.on.the.vari
ous
.enti
ties
.of.the.comm
unication
.syst
em:
.
the.node.hard
ware,
.the.comm
unication
.proto
col,
.the.node.rmw
are,
.and.the.deve
lopment,
.inst
allation,
.
comm
ission,
.and.mai
ntenance
.pro
cess.
In
.shor
t,
.in.a.safe
ty-related
.comm
unication
.syst
em
.inte
grity
.of.data.(man
agement
.or.proc
ess
.data
)
.exch
anged
.
amon
g
.node
s,
.or.betw
een
.a.node.and.a.mana
gement
.unit
,
.must.alwa
ys
.be.ensu
red
.with.a.high.prob
ability.
.For.
that.reas
on,
.the.node
s
.proc
essing
.the.data.must.meet.disti
nct
.safe
ty
.requ
irements.
.e.hard
ware
.is.ther
efore
.
enha
nced
.with.addi
tional
.inte
grated
.circ
uits,
.and.onli
ne
.sow
are
.self.tests.are.exec
uted.
.Apr
otocol
.used.to.
exch
ange
.data.is.inte
grated
.into.the.exis
ting
.prot
ocol.
.e.tool
s
.appl
ied
.to.exch
ange
.mana
gement
.data.that
,
.
in.turn
,
.are.the.base.for.proc
ess
.data.exch
ange
.are.also.enha
nced
.with.a.safe
ty-related
.proc
ess.
e
.resu
lt
.is.a.safe
ty-related
.autom
ation
.tech
nology
.that.meet
s
.the.requ
irements
.of.IEC.6150
8
.safe
ty
.
inte
grity
.leve
l
.3.(SIL.3).[1]..It.can.be.inte
grated
.into.an.exis
ting
.LonW
orks
.and.allo
ws
.safe.and.non-
safe
.
comm
unication
.wit
hin
.a.sing
le
.com
munication
.net
work.
47.2 the General SafetyLon Concept
A.common.way.to.realize.a.safety-related.automation.technology.is.to.use.a.standard.technology—in.
case.of.Safe
tyLon
.LonW
orks—and
.enha
nce
.it.with.safe
ty
.feat
ures.
.Such.a.tech
nology
.can.be.real
ized
.
by.two.die
rent
.appr
oaches:
.inte
gration
.of.safe
ty
.meas
ures
.dire
ctly
.into.the.exis
ting
.tech
nology
.like.
CANo
pen
.Safe
ty;
.or.trea
ting
.the.non-
safe
.tech
nology
.as.a.blac
k-box
.and.base.the.safe
ty-related
.mea-
s
ures
.log
ically
.tota
lly
.iso
lated
.fro
m
.the.rem
ainder
.on.the.sta
ndard
.tec
hnology.
47
SafetyLon
47.1. Introduction.....................................................................................47-1
47.2
. e.Gen
eral
.Saf
etyLon
.Con
cept.................................................... 47-1
47.3
. e.Saf
ety-Related
.Lif
ecycle........................................................... 47-2
47.4
. e.Har
dware...................................................................................47-4
47.5
. e.Saf
ety-Related
.Fir
mware......................................................... 47-7
47.6
. e.Saf
etyLon
.Too
ls......................................................................47-10
Acronyms................................................................................................... 47-13
References................................................................................................... 47-13
Thomas Novak
SWARCO Futurit
Verk
ehrssignalssysteme
GmbH
Thomas Tamandl
SWARCO Futurit
Verk
ehrssignalssysteme
GmbH
Peter Preininger
LOyTEC Electronics GmbH
© 2011 by Taylor and Francis Group, LLC

47-2 Industrial Communication Systems
e.second.strategy.is.pursued.not.only.in.ProSafe.but.also.in.SafetyLon..It.uses.standard.LonWorks.
hard
ware
. to. acce
ss
. the. netw
ork.
. Henc
e,
. safe. and. non-
safe
. node
s
. can. be. conn
ected
. to. the. same.
netw
ork.
.Only.safe.node
s
.can.comm
unicate
.by.mean
s
.of.the.Safe
tyLon
.proto
col.
.But.all.devi
ces
.are.able.
to.exc
hange
.mes
sages
.tha
t
.are.non
-safety
.rel
ated.
Following
.the.seco
nd
.appr
oach,
.the.comm
unication
.chan
nel
.is.spli
t
.in.the.blac
k
.and.yell
ow
.chan
nel.
.
e.blac
k
.chan
nel
.comp
rises
.all.stan
dard
.LonW
orks
.tech
nology
.incl
uding
.the.netw
ork
.chip.(Neu
ron
.
Chip.or.LC30
20)
.and.the.netw
ork
.(cf..dark.gray.part.in.Figu
re
.47.2
).
.ese.comp
onents
.allo
w
.the.com-
m
unication
.of.two.or.mor
e
.net
work
.nod
es
.in.a.non
-safe
.man
ner.
.In.the.bla
ck
.cha
nnel,
.it.is.not.gua
ran-
teed
.tha
t
.the.rec
eived
.mes
sage
.is.cor
rect.
.A.mes
sage
.can.be.del
ayed,
.cor
rupted,
.ins
erted,
.or.los
t.
In
.cont
rast
.to.the.blac
k
.chan
nel,
.the.yell
ow
.chan
nel
.is.asso
ciated
.with.the.safe
ty
.rela
ted
.meas
ures.
.
It.uses.the.feat
ures
.of.the.blac
k
.chan
nel
.to.tran
sport
.mess
ages,
.but.addi
tional
.eor
t
.is.made.to.ensu
re
.
the.inte
grity
.of.the.safe
ty-related
.payl
oad.
.In.addi
tion,
.spec
ial
.hard
ware
.oer
s
.the.requ
ired
.hard
ware
.
inte
grity
.nec
essary
.to.ens
ure
.a.hig
h
.lev
el
.of.int
egrity
.of.dat
a
.pro
cessing.
e
.tools.for.the.non-
safe
.inst
allation,
.comm
issioning,
.and.main
tenance
.of.LonW
orks
.are.also.used.
in.Safe
tyLon.
.Wher
eas
.the.rmw
are
.on.node.side.is.real
ized
.to.be.safe
ty
.rela
ted,
.the.tools.are.not.made.
safe
.
.Howe
ver,
.safe
ty-related
.proc
esses
.are.supp
orted
.by.the.tools.bein
g
.an.exte
nsion
.to.the.stan
dard
.
tools.and.the.use
r
.is.tak
en
.as.aut
hority
.to.ens
ure
.a.hig
h
.lev
el
.of.int
egrity.
Applying
.the.blac
k-channel
.conc
ept
.(i.e
.,
.sett
ing
.up.Safe
tyLon
.on.the.basis.of.LonW
orks)
.allo
ws
.safe.
and.non-
safe
.node
s
.to.be.in.the.same.syst
em.
.In.deta
il,
.ever
y
.safe.node.can.hand
le
.non-
safe
.and.safe.
messages..Hence,.even.safe.and.non-safe.network.variables.can.coexist.on.the.same.node.which.leads.to.
a.tigh
t
.inte
gration
.of.non-
safe
.and.safe.appl
ications.
.In.addi
tion,
.Safe
tyLon
.is.comp
liant
.to.the.Euro
pean
.
stan
dard
.EN.149
08
.[2].sinc
e
.it.doe
s
.not.cha
nge
.the.sta
ndard
.Lon
Works
.in.any.way
.
In
.the.foll
owing,
.the.thre
e
.part
s
.to.be.enha
nced
.due.to.safe
ty
.reas
ons
.are.outl
ined:
.the.node.hard
-
ware,
.the.node.rmw
are,
.and.the.tools
.
.Deve
lopment
.and.use.of.all.the.devi
ces
.is.embed
ded
.into.the.
safe
ty-related
.Saf
etyLon
.lif
ecycle
.pre
sented
.rs
t
.and.in.acc
ordance
.wit
h
.IEC.615
08.
47.3 the Safety-related Lifecycle
SafetyLon.is. not.only.developed.according.to.the.requirements. of. IEC.61508. but.it.also.species.a.
Safe
tyLon
.life
cycle
.in.whic
h
.it.supp
orts
.the.whol
e
.appl
ication
.duri
ng
.the.die
rent
.phas
es
.of.the.safe
ty-
related
.life
cycle
.[3]..e.Safe
tyLon
.life
cycle
.can.be.consi
dered
.as.an.impl
ementation
.of.the.IEC.6150
8
.
life
cycle
.wit
h
.reg
ard
.to.Lon
Works.
e
.safe
ty-related
.comm
unication
.(e.g
.,
.how.to.addr
ess
.comm
unication
.faul
ts
.with.adeq
uate
.mea-
s
ures)
.is.just.one.part
.
.In.addi
tion
.to.this
,
.proc
esses
.rela
ted
.to.deve
loping
.a.user
-application,
.or.con
gur-
ing
.and.mai
ntaining
.the.net
work
.hav
e
.to.be.spe
cied.
e
. proc
esses
. pres
ented
. in. the. foll
owing
. must. be. docu
mented
.in. a.coor
dinated
.way. with
in
. the.
func
tional
.safe
ty
.mana
gement
.that.is.base
d
.on.the.safe
ty
.plan.cove
ring
.all.proc
esses
.and.acti
vities
.to.
impr
ove
.safe
ty.
.e.safe
ty
.plan.incl
udes
.topic
s
.such.as.orga
nization
.and.resp
onsibilities,
.docu
mentation
.
requ
irements,
.or.ver
ication
.and.val
idation
.act
ivities
.[4]
.
On
.deve
loping
.a.Safe
tyLon
.user
-application,
.vari
ous
.char
acteristics
.of.Safe
tyLon
.must.be.take
n
.into.
consi
deration:
•
. e.func
tionality
.of.the.safe
ty-related
.rmw
are
.(see.Figu
re
.47.6.and.for.deta
ils
.Sect
ion
.47.5
),
.espe
-
cially
.of.the.app
lication
.lay
er
.int
erface
•
. Safe.and.non-
safe
.netw
ork
.vari
ables
.on.the.same.node.(desi
gn
.requ
irements
.as.ment
ioned
.in.
Sect
ion
.47.
2)
•
. Con
guration
.of.the.saf
ety-related
.net
work
.via.a.sing
le
.man
agement
.uni
t
.(se
e
.Sec
tion
.47.
6)
e
.codi
ng
.and.comp
ilation
.of.a.Safe
tyLon
.user
-application
.is.perf
ormed
.by.using.regu
lar
.non-
safety-
related
. tools
.
. Howe
ver,
. the. sour
ce
. code. of. the. user
-application
. writ
ten
. in. ANSI. C. must. adhe
re
. to.
deta
iled
.prog
ramming
.guid
elines
.as.ment
ioned
.in.[5]..e.bina
ry
.rece
ived
.aer.the.comp
ilation
.proc
ess
.
© 2011 by Taylor and Francis Group, LLC
SafetyLon 47-3
is.linked.to.the.safety-related.rmware.and.the.output.is.another.binary..Such.a.binary.is.ashed.into.a.
node.and.must.reside.unchanged.in.the.node..A.change.of.the.binary.in.the.eld.is.explicitly.not.allowed.
and.requires.safe.tools.for.development.
Aer
.making.the.node.ready.for.operation,.they.are.installed.in.the.eld.and.standard.tools.are.used.
to.setup.a.network..e.next.step.is.to.congure.the.nodes,.so.that.a.safety-related.application.can.be.
performed..e.following.parameters.are.required.to.congure.SafetyLon.
•
. Safe.address.(node):.Each.node.is.assigned.a.safe.address.to.prevent.a.node.from.masquerade..
e.safe.address.identies.a.SafetyLon.uniquely.so.that.parameters.are.sent.to.the.intended.node.
•
. Binding*.parameters:.is.allows.exchange.of.a.safety-related.data.
•
. SafetyLon.user-application.identier:.Each.user-application.gets.a.unique.ID..According.to.the.
ID.it.is.possible.to.get.detailed.information.on.the.functionality.and.the.set.of.safety-related.data.
points.to.be.congured.
e
.parameters.are.transferred.to.the.corresponding.node.in.a.three-step.process:
. 1..e.management.unit.sends.a.request.to.a.node..e.node.returns.its.safe.address.and.a.transac-
tion
.ID..e.management.unit.veries.the.safe.address.
. 2.. e.management.unit.uses.the.safe.address.and.the.transaction.to.send.the.conguration.param-
eter
.to.the.node..e.node.stores.the.conguration.parameter.temporarily,.reads.the.data.back.
and.returns.it.to.the.management.unit.
. 3..e.management.unit.checks.if.the.sent.and.received.data.are.equal..If.so,.it.sends.a.request.to.the.
node.to.store.the.parameter.permanently.and.use.it.for.communication.purpose.
Following
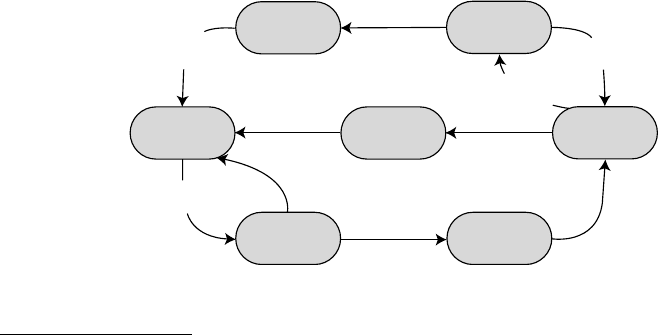
.a.successful.conguration.(idle.mode.as.shown.in.Figure.47.1),.the.nodes.have.to.be.com-
missioned
.in.order.to.get.them.ready.for.performing.safety-related.applications.[3]..First,.the.congura-
tion
.parameters.are.validated..is.refers.to.checking.if.the.nodes.used.in.the.safety-related.application.
perform.as.expected.(test.mode)..In.case.of.a.successful.validation,.the.user.has.to.conrm.it.(pre-run.
and.wait.mode)..Next,.the.nodes.are.waiting.to.be.activated..Such.a.mode.is.implemented.to.allow.a.
coordinated.start-up.of.a.network..In.run.mode,.the.node.performs.its.functionality.according.to.the.
safety-related.rmware.and.SafetyLon.user-application..In.that.mode,.the.safety-related.data.transfer.
among.the.nodes.is.handled.
e
.mode.is.le.in.two.cases:.rst,.if.a.safety-critical.failure.has.occurred..en.the.safe.mode.is.
entered..In.case.of.a.recoverable.failure,.the.node.leaves.the.safe.mode,.otherwise.the.node.remains.in.
that.state.until.an.operator.checks.the.failure.cause.
*
.
Binding.means.that.a.logic.connection.between.two.or.among.many.network.variables.is.established.
Operator
confirmation
DSF
compared
Modification finished
DSF compared
Communication
failure solved
Failure
detection
Device reset
Operator
confirmation
Device reset or
PC confirmation
Modification
of data
Operator
confirmation
Idle Safe
Run
Wait
Pre-run
ModifyTest
FIGURE 47.1 Safety-related.overall.state.diagram.
© 2011 by Taylor and Francis Group, LLC
47-4 Industrial Communication Systems
Maintenance.(e.g.,.removing.a.safe.address.of.a.network.variable).and.decommissioning.of.the.
node.is.performed.when.the.node.is.in.modify.mode..e.node.is.set.to.that.mode.explicitly.by.the.
management.unit..e.same.three-step.process.as.described.before.on.outlining.the.conguration.
process.is.used.
Such
.detailed.processes.for.conguration,.commissioning,.maintenance,.and. decommissioning.
are.required.and.several.steps.have.to.be.authorized.by.a.user.because.the.tool.running.at.the.man-
agement
.unit.is.a.non-safety-related.tool..e.advantage.is.that.a.standard.PC.with.COTS.soware.
can.be.used.
47.4 the Hardware
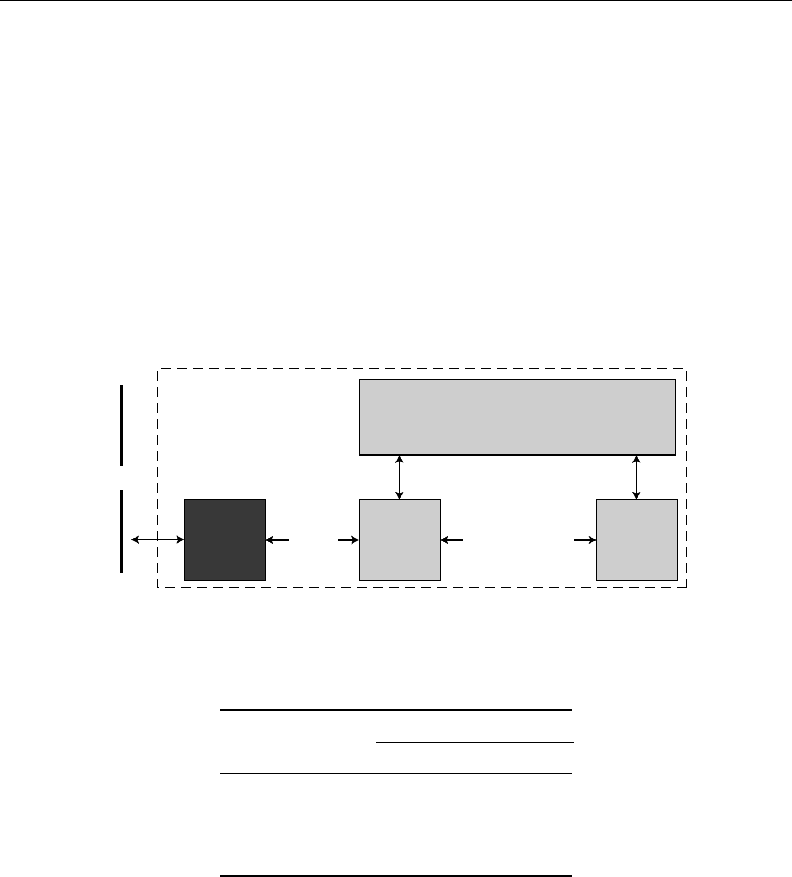
Node.hardware.designed.for.a.safety-related.automation.technology.has.to.follow.special.design.rules..
It.must.be.designed.in.a.way.to.satisfy.the.requirements.caused.by.a.SIL.dened.in.IEC.61508.[1]..As.
a.design.goal.of.SafetyLon.is.to.reach.a.SIL3.compliant.system,.a.two-channel.architecture.(1oo2).was.
chosen.for.the.node.hardware.additional.to.the.EN.14908.chip.(Neuron.chip.or.LC3020).as.illustrated.
in.Figure.47.2.[6].
e
.term.1oo2.(speak:.one.out.of.two).indicates.that.two.independent.channels.perform.the.same.
actions.and.nally.compare.the.result..In.case.of.SafetyLon,.the.1oo2.is.realized.by.two.hardware.chan-
nels.
.e.result.of.both.channels.must.be.equal.that.an.action.such.as.setting.an.output.can.take.place..
In.case.of.a.mismatch.of.both.channels,.the.system.has.to.take.predened.actions.such.as.discarding.
amessage.or.entering.a.safe.state.
IEC
.61508.[7].denes.dierent.ways.of.reaching.a.SIL.3.compliant.system.as.shown.in.Table.47.1..
ere.is.a.trade-o.possible.between.the.safe.failure.fraction.(i.e.,.number.of.failures.not.resulting.in.
adangerous.situation).and.the.hardware.architecture.
SafetyLon node
LON
EN 14908
chip
UART
Safety
chip 1
Safety
chip 2
Safety-related input/output unit
fail safe unit
Standard
communication
interface
FIGURE 47.2 SafetyLon.node.hardware.architecture.
TABLE 47.1 Safety.Integrity.of.Deployed.
Hardware
Safe.Failure.Fraction
Hardware.Fault.Tolerance
a
0 1 2
<60% Not
.possible SIL.1 SIL.2
60%
.to.<90% SIL.1 SIL.2 SIL.3
90%
.to.<99% SIL.2 SIL.3 SIL.4
≥99%
SIL
.3 SIL.4 SIL.4
a.
A.hardware.fault.tolerance.of.N.denotes.that.N.+.1.
faults.cause.a.loss.of.the.safety.status.of.the.system.
© 2011 by Taylor and Francis Group, LLC
SafetyLon 47-5
In.detail,.a.hardware.fault.tolerance.of.1.results.in.a.required.safe.failure.fraction.of.90%–99%..e.
safe.failure.fraction.(SFF).denes.the.percentage.of.failures.that.do.not.result.in.a.dangerous.situation..
It.is.dened.as.follows:
.
SFF =
SD SU DD
SD SU DD DU
λ λ λ
λ λ λ λ
+ +
+ + +
.
(47.1)
where
λ
SD
.is.the.safe.detected.failure
λ
SU
.is.the.safe.undetected.failure
λ
DD
.is.the.dangerous.detected.failure
λ
DU
.is.the.dangerous.undetected.failure
Hence,
.there.must.be.a.trade-o.between.the.quality.of.the.hardware.to.reduce.the.inherent.risk.and.the.
eort.performed.to.detect.dangerous.failures..As.dened.in.the.formula,.λ
DU
.reduces.the.SFF,.whereas.
dangerous.failures.that.can.lead.into.a.hazardous.state.can.be.used.to.increase.the.SFF.if.they.are.detected..
Hence,.it.is.reasonable.to.perform.hardware.self.tests.(i.e.,.detecting.dangerous.faults.that.therefore.result.
in.non-dangerous.failures).in.order.to.increase.the.SFF..e.impacts.of.the.above.described.facts.result.in.
extensive.testing.of.all.components.such.as.input.and.output,.or.volatile.and.nonvolatile.memory.[8]..In.the.
following,.an.example.is.given.on.how.to.design.and.test.the.safe.input.and.output.logic.
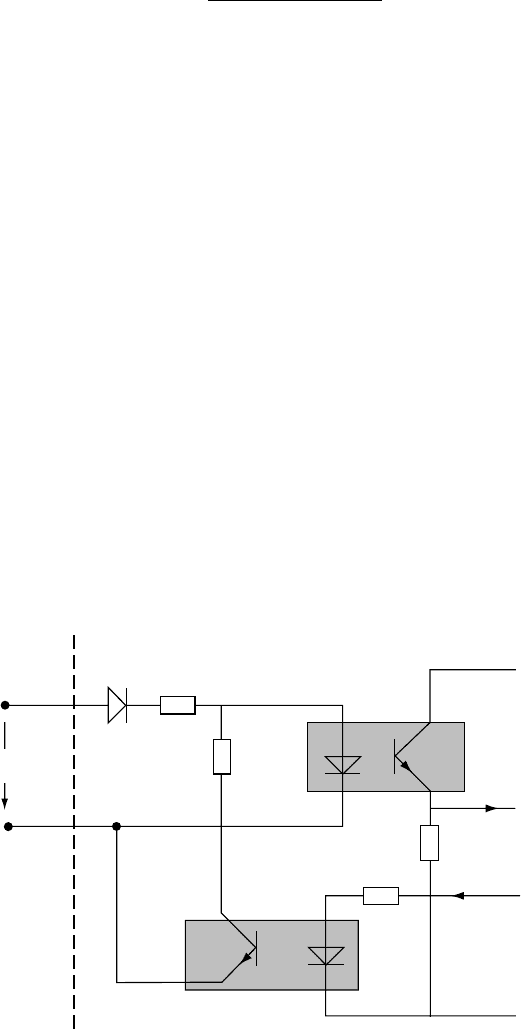
In
.a. standard,. non-safe. environment.a.digital. input.is.simply. connected.to.the. evaluating.device..
Connecting.a.digital.IO.directly.to.a.microcontroller.is.oen.not.suitable.for.safety-related.devices..First,.
the.hardware.inside.the.device.must.be.protected.against.hazardous.eects.from.outside,.therefore.mostly.
a.galvanic.isolation,.an.optocoupler,.is.used..Second,.additional.components.are.added.to.setup.a.testable.
input..e.input.is.tested.only.if.it.is.active,.which.means.that.a.dened.voltage.is.applied.to.the.input.ter-
minal.
.It.is.not.necessary.to.test.an.input.that.is.in.an.inactive.state.because.it.is.per.denition.the.safe.state.
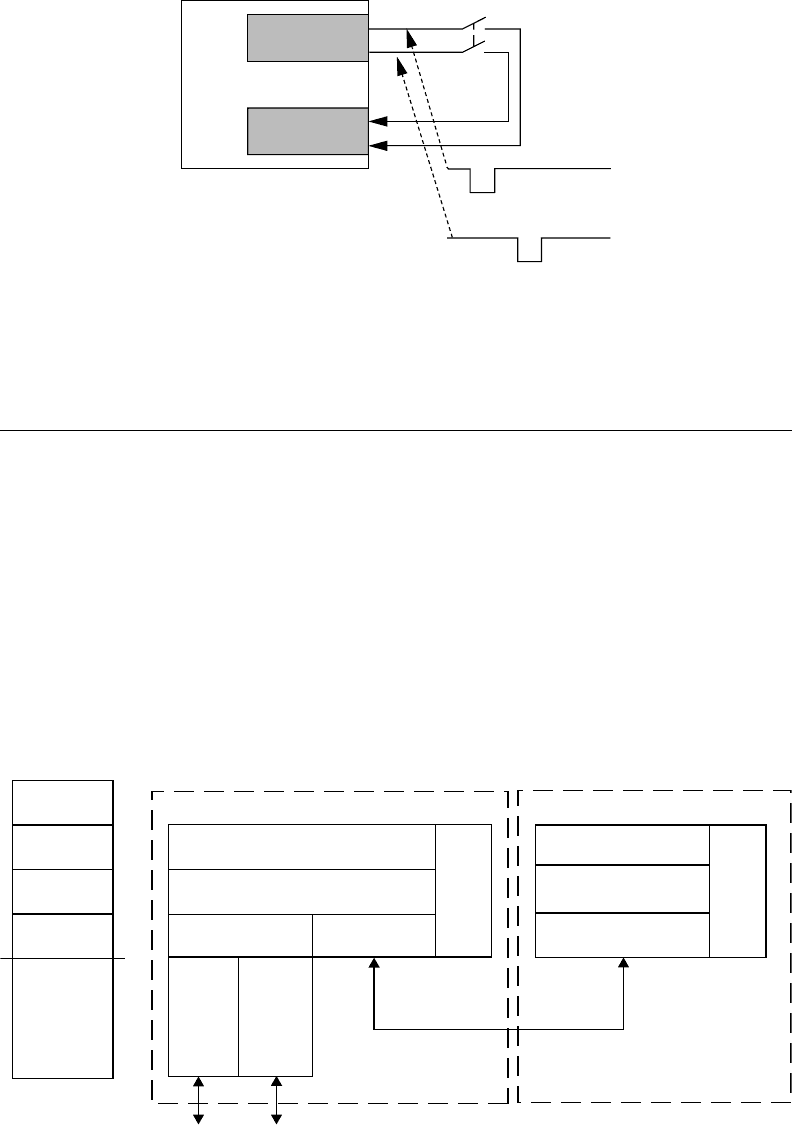
Figure
.47.3.depicts.the.principles.of.a.testable.input;.several.elements.were.omitted.in.the.picture.in.
order.to.focus.on.the.functionality..In.addition.to.the.rst.optocoupler,.a.second.one.is.added..For.test-
ing
.purpose,.this.device.is.able.to.switch.o.the.signal.transmission.to.the.microcontrollers.for.a.very.
short.period.of.time..is.interruption.of.the.input.signal.must.be.detected.by.the.microcontroller..
Input to
CPU
Internal
power
supply
Opto coupler 1
Opto coupler 2
Safe input internals
Field side
Ground
extern
Test input
from
CPU
Ground
intern
Field input
signal
FIGURE 47.3 Schematic.of.safety-related.input.
© 2011 by Taylor and Francis Group, LLC
47-6 Industrial Communication Systems
By.performing.this.procedure,.the.microcontroller.is.able.to.check.the.switching.capability.of.the.input.
optocoupler.and.the.functional.connectivity.of.all.components.
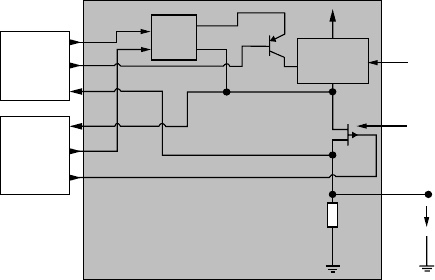
According
.to.the.two-channel.architecture,.the.output.stage.is.split.into.two.switching.elements.as.
shown.in.Figure.47.4..Only.if.both.stages.switch.on,.the.output.is.activated..It.is.preferable.that.both.
switching.elements.use.dierent.technologies.in.order.to.avoid.common.cause.failures..Hence,.the.deci-
sion
.to.switch.on.must.be.done.from.both.channels.together..Only.then.the.output.is.switched.on..For.
testing.purpose.the.state.of.the.two.stages.is.read.back.and.additional.in.one.state.the.output.is.switched.
o.for.a.short.period.of.time.in.order.to.test.the.switching.capability..Obviously,.the.o-time.must.be.
shorter.than.the.reaction.time.of.the.switched.element.
Even
.if.there.are.two.stages.that.are.able.to.switch.o,.there.is.the.possibility.that.both.channels.are.not.
able.to.perform.any.actions.but.are.stuck.at.on.state.(e.g.,.due.to.a.common.cause.of.power.supply.fail-
ure).
.To.overcome.that.static.issue,.a.frequently.triggered.control.element.is.added..e.fail.safe.unit.only.
enables.its.output.if.it.is.permanently.triggered.from.the.controlling.device..e.output.of.the.fail.safe.
unit.supplies.the.two.switching.elements.of.the.output.stage..Hence,.if.the.fail.safe.unit.is.not.triggered.
anymore,.there.is.no.supply.control.voltage.for.the.switching.elements.and.the.output.is.switched.o..So.
it.is.guaranteed.that.the.output.enters.the.safe.state.if.both.control.channels.are.stuck.at.one.state.and.are.
not.able.to.perform.any.more.operations..A.simple.way.to.design.the.fail.safe.unit.is.to.use.a.transformer.
in.combination.with.a.capacitor.on.the.output..In.order.to.charge.the.output.capacitor.the.input.signal.for.
the.transformer.must.periodically.change.the.signal..Both.controllers.are.involved.in.generating.the.input.
signal.of.the.transformer..One.controller.is.applying.the.supply.voltage.and.the.other.one.ties.the.trans-
former
.to.ground..us,.both.controllers.are.able.to.switch.o.the.fail.safe.unit.if.one.detects.a.failure..On.
the.other.hand,.if.the.controller.that.creates.the.periodical.signal.does.not.work.correctly,.the.periodical.
signal.fails.and.as.a.result.the.output.described.in.Figure.47.5.switches.o.automatically.
e
.1oo2.hardware.structure.also.aects.external.devices..Similar.to.the.internal.1oo2.structure.all.
external.devices.are.connected.via.two.channels..On.these.channels.short.test.pulses.are.applied.in.order.
to.detect.a.wiring.failure.(e.g.,.no.connection.or.a.shortcut.between.two.wires)..erefore,.test.pulses.
must.be.generated.in.such.a.way.that.one.channel.is.tested.at.a.time..If.the.emitted.test.pulse.is.not.
detected.or.detected.on.several.lines.a.failure.has.occurred..Intelligent.devices.that.are.not.supplied.by.
the.SafetyLon.node.have.to.send.their.own.test.pulses.which.are.detected.by.the.SafetyLon.node.
Figure
.47.5.shows.how.to.connect.a.simple.two-channel.switch..e.two-channel.switch.is.supplied.
by.the.SafetyLon.node..In.normal.operation.the.switch.is.closed.and.a.high.level.is.detected.on.the.
input.pins.of.the.SafetyLon.device..en.the.external.wiring.and.the.switch.are.tested..Periodically,.
one.of.the.two.channels.is.switched.o.for.a.very.short.time..So.all.failures.are.detected.that.occur.on.
the.external.wiring.from.and.to.the.switch..e.switch.itself.is.implicitly.checked.as.the.same.signal.
level.must.be.detected.on.both.inputs..In.case.of.an.opened.switch,.no.tests.are.necessary.because.
low.signals.on.both.inputs.are.dened.as.the.safe.state..In.that.state,.the.SafetyLon.device.has.to.enter.
First
switch
Second
switch
Output
Safe output
CPU1
CPU2
Fail
safe
unit
Integrated
silicon
switch
FIGURE 47.4 Schematic.of.safety-related.output.
© 2011 by Taylor and Francis Group, LLC
SafetyLon 47-7
asafe.state..eactivities.to.perform.when.entering.the.safe.state.depend.on.the.dened.application;.but.
it.is.mandatory.that.there.must.be.no.direct.danger.to.life.or.indirect.to.the.environment.
47.5 the Safety-related Firmware
e.rmware.of.a.SafetyLon.node.is.organized.in.a.three-layered.architecture.and.located.above.ISO/OSI.
layer.7—equal.to.the.approach.chosen.in.PROFIsafe—as.shown.in.Figure.47.6..Since.only.Safety.Chip.1.is.
connected.to.the.EN.14908.chip.(cf..Figure.47.2),.the.lower.layer.diers.between.the.chips..Shortstack.API.
and.Safety.Chip.Orion.Stack.API,.respectively,.are.third-party.ISO/OSI.layer.7.soware.located.below.the.
rst.layer.of.the.rmware..ey.care.for.the.transmission.of.data.from.and.to.the.chosen.EN.14908.chip..
eir.soware.is.not.part.of.safety.considerations..ey.are.already.part.of.the.“black.channel”.and.hence.
not.outlined.in.the.following.
On
.top.of.the.rmware.is.the.application.layer.interface..It.oers.the.application.programmer.func-
tions
.that.are.used.to.realize.safe.user-application.soware..Typical.functions.are.sending.and.receiving.
functions,.receiving.value.from.the.safety-related.input.or.setting.the.safety-related.output,.or.write.and.
read.access.to.the.sensor.and.actuator.data.stored.in.a.table.being.part.of.the.safe.soware..e.applica-
tion
.layer.interface.provides.a.convenient.way.of.programming.safety-related.user-applications.without.
taking.care.of.safety.functions.encapsulated.in.the.safety.layer.
Safety-related
user-application
Safety rmware
layer 3
Safety rmware
layer 2
Safety rmware
layer 1
Shortstack
microserver
ISO/OSI
layer 7
LC3020
Safety layer
Safety layer
Safety chip interface
Safety chip
interface
Scheduler,
state machine
Scheduler,
state machine
Network access layer
interface
Safety chip 1 Safety chip 2
Application layer interface
Application layer interface
Shortstack API
Orion stack API
FIGURE 47.6 Soware.design.of.SafetyLon.node.
SafetyLon node
Signal output
Input filter
FIGURE 47.5 Switch.connected.to.safety-related.output.
© 2011 by Taylor and Francis Group, LLC
47-8 Industrial Communication Systems
A.part.of.the.rst.safety-related.rmware.layer.is.called.network.access.layer.interface..It.is.an.abstrac-
tion
.lay
er
.tha
t
.mak
es
.acc
ess
.to.the.LON.pos
sible
.reg
ardless
.of.the.und
erlying
.thi
rd-party
.so
ware.
.
Fun
ctions
.of.the.net
work
.acc
ess
.lay
er
.are.dec
lared
.in.suc
h
.a.way.tha
t
.the
y
.enc
apsulate
.fun
ctions
.of.
the.thi
rd-party
.API
.
.Sin
ce
.onl
y
.Saf
ety
.Chi
p
.1.is.con
nected
.to.the.LON
,
.the.net
work
.acc
ess
.lay
er
.is.not.
imp
lemented
.on.Saf
ety
.Chi
p
.2..Ano
ther
.par
t
.of.the.rs
t
.saf
ety-related
.rm
ware
.lay
er
.is.the.saf
ety
.chi
p
.
int
erface
.tha
t
.han
dles
.dat
a
.exc
hange
.bet
ween
.bot
h
.saf
ety
.chi
ps.
.It.inc
ludes
.a.har
dware
.dep
endent
.dri
ver
.
and.a.so
ware
.API.tha
t
.int
erfaces
.wit
h
.the.saf
ety
.lay
er.
.It.oe
rs
.a.fun
ction
.to.sen
d
.dat
a
.to.and.rec
eive
.
dat
a
.fr
om
.th
e
.co
rresponding
.sa
fety
.ch
ip.
e
.saf
ety
.lay
er
.is.loc
ated
.in.the.mid
dle
.of.the.so
ware
.desi
gn
.and.com
prises
.all.so
ware
.fun
ctional-
ity
.dir
ectly
.ref
erring
.to.saf
ety.
.It.int
erfaces
.wit
h
.the.app
lication
.lay
er
.int
erface,
.and.the.net
work
.acc
ess
.
lay
er
.int
erface
.and.saf
ety
.chi
p
.int
erface.
.e.saf
ety
.lay
er
.is.sur
rounded
.by.two.oth
er
.lay
ers;
.in.oth
er
.
wor
ds,
.the.saf
ety
.rm
ware
.is.sep
arated
.into.thr
ee
.lay
ers,
.to.mak
e
.it.abs
olutely
.ind
ependent
.fro
m
.the.
thi
rd-party
.so
ware.
.Sec
ond,
.the.thi
rd
.lay
er
.is.spe
cied
.to.hid
e
.saf
ety
.fun
ctionality
.fro
m
.the.app
lica-
tion
.pro
grammer.
.Suc
h
.a.lay
er
.eas
es
.pro
gramming
.and.avo
ids
.mis
use
.of.saf
ety
.fun
ctions
.sinc
e
.it.mus
t
.
be.as
sumed
.th
at
.ap
plication
.pr
ogrammers
.ar
e
.no
t
.fa
miliar
.wi
th
.de
tails
.of.th
e
.r
mware
.fu
nctionality.
e
.saf
ety
.rm
ware
.lay
er
.2.con
sists
.of.mul
tiple
.par
ts
.rel
ated
.to.saf
ety,
.i.e
.,
.so-
called
.pri
mary
.fun
c-
tions:
.onl
ine
.sel
f
.tes
t
.mod
ule,
.saf
ety-related
.inp
ut/output
.mod
ule,
.so
ware
.mon
itoring,
.or.the.Saf
etyLon
.
pro
tocol
.sta
ck.
.Oth
er
.par
ts
.are.sup
porting
.the.desi
red
.fun
ctionality
.cal
led
.sup
porting
.fun
ctions
.lik
e
.the.
Saf
ety
.Chi
p
.int
erface.
.Alb
eit
.not.par
t
.of.lay
er
.2,.the.sch
eduler
.and.sta
te
.mac
hine,
.and.the.saf
ety
.chi
p
.
interface.are.also.supporting.functions.
e
.onl
ine
.sel
f
.tes
t
.mod
ule
.inc
ludes
.onl
ine
.tes
ts
.tha
t
.are.exe
cuted
.to.gua
rantee
.a.hig
h
.int
egrity
.of.
the.har
dware
.by.rev
ealing
.fau
lts
.in.the.di
erent
.par
ts
.of.the.har
dware.
.Tes
ts
.are.sep
arated
.into.vol
a-
tile
.mem
ory
.(RA
M),
.non
volatile
.rea
d
.onl
y
.mem
ory
.(FL
ASH),
.and.CPU.tes
ts.
.In.[8]
,
.imp
lementation
.
exa
mples
.ar
e
.pr
esented.
.In.[9
]
.di
erent
.te
st
.al
gorithms
.ar
e
.ou
tlined.
In
.gen
eral,
.vol
atile
.mem
ory
.tes
t
.alg
orithms
.di
er
.in.tes
t
.eo
rt
.and.dia
gnostic
.cov
erage.
.A.hig
h
.tes
t
.
eo
rt
.and.a.hig
h
.dia
gnostic
.cov
erage
.is.ens
ured
.whe
n
.usin
g
.the.gal
loping
.pat
tern
.tes
t,
.a.low.one.whe
n
.
imp
lementing
.the.mar
ching
.bit.tes
t
.[10
].
.e.lev
el
.of.the.dia
gnostic
.cov
erage
.dep
ends
.on.the.fau
lts
.
rev
ealed
.by.the.tes
t.
.Tes
t
.wit
h
.a.hig
h-level
.det
ect
.fau
lts
.acc
ording
.to.the.DC-
fault
.mod
el
.[1].oth
ers
.onl
y
.
det
ect
.st
uck-at
.fa
ults.
Tests
.of.the.non
volatile
.rea
d
.onl
y
.mem
ory
.rel
y
.on.par
ity
.bit
s,
.che
cksums
.or.CRC
s
.whe
reas
.dia
gnostic
.
cov
erage
.of.the.rs
t
.is.low.and.the.las
t
.is.hig
h.
.In.cas
e
.of.a.Saf
etyLon
.nod
e,
.the.non
volatile
.mem
ory
.is.
gro
uped
.in.blo
cks
.of.256.byt
es
.sinc
e
.CRC.pol
ynomials
.do.not.gua
rantee
.a.de
ned
.lev
el
.of.int
egrity
.for.
ind
enite
.dat
a
.len
gth.
.Eve
ry
.blo
ck
.is.use
d
.as.inp
ut
.to.cal
culate
.a.CRC
.
.e.CRC
s
.of.the.var
ious
.blo
cks
.
are.stor
ed
.in.the.non
volatile
.mem
ory
.at.a.pre
dened
.are
a.
.Dur
ing
.run.tim
e,
.the.CRC.of.eve
ry
.blo
ck
.is.
rec
alculated
.and.com
pared
.to.the.stor
ed
.one
.
.Suc
h
.an.app
roach
.is.an.ee
ctive
.mea
ns
.to.che
ck
.int
egrity
.
of.da
ta
.sto
red
.in.th
e
.no
nvolatile
.me
mory
.[8
].
Safety-related
.inp
ut/output
.mod
ule
.is.res
ponsible
.for.tes
ting
.the.inp
uts
.and.out
puts
.and.to.pro
vide
.
fun
ctionality
.to.set
/reset
.an.inp
ut
.and.to.get.the.val
ue
.of.an.out
put.
.Tes
ting
.of.the.saf
e
.I/O
s
.has.to.be.
syn
chronized
.bet
ween
.the.saf
ety
.chi
ps.
.In.con
trast
.to.the.afo
rementioned
.onl
ine
.sel
f
.tes
ts,
.saf
e
.I/O.tes
ts
.
are.per
formed
.in.clo
se
.coo
peration
.bet
ween
.the.saf
ety
.chi
ps.
.Har
dware
.sch
ematics
.are.desi
gned
.in.suc
h
.
a.way.tha
t
.inp
uts
.sign
al
.is.rec
eived
.and.out
put
.sign
al
.set.by.bot
h
.chi
ps
.and.tha
t
.tes
t
.sign
als
.can.be.sen
t
.
fro
m
.one.chi
p
.and.rec
eived
.and.eva
luated
.by.the.oth
er
.chi
p
.(cf
.
.Fig
ures
.47.
3
.and.47.
4).
.As.a.con
sequence,
.
a.so
ware
.fun
ction
.of.the.mod
ule
.tri
ggers
.a.tes
t
.pul
se
.on.the.rs
t
.saf
ety
.chi
p
.and.a.so
ware
.fun
ction
.on.
the.ot
her
.sa
fety
.ch
ip
.ch
ecks
.if.th
e
.te
st
.pu
lse
.ha
s
.be
en
.re
ceived.
e
.obj
ective
.of.so
ware
.mon
itoring
.is.to.ens
ure
.so
ware
.int
egrity
.bei
ng
.par
t
.of.the.syst
ematic
.int
egrity,
.
in.con
trast
.to.sel
f
.tes
ts
.tha
t
.car
e
.for.the.har
dware
.int
egrity.
.It.is.a.mea
ns
.to.det
ect
.if.safe
ty
.fun
ctions
.loc
ated
.
in.the.vol
atile
.mem
ory
.wer
e
.exe
cuted
.acc
ording
.to.spe
cication
.or.hav
e
.bee
n
.alt
ered
.due.to.acc
idental
.
mod
ication.
.Suc
h
.mis
behavior
.is.pos
sible
.bec
ause
.of.so
ware
.fau
lts
.dur
ing
.the.des
ign
.or.imp
lementation.
Soware
.mon
itoring
.can.be.dis
tinguished
.bet
ween
.tim
e-based
.and.log
ic-based
.mon
itoring
.[11
].
.Bot
h
.
are.int
egrated
.into.the.saf
ety-related
.rm
ware.
.e.rs
t
.typ
e
.use
s
.a.tim
er
.wit
h
.an.ind
ependent
.tim
e
.
© 2011 by Taylor and Francis Group, LLC

SafetyLon 47-9
base..Typically,.such.a.timer.is.called.watchdog.timer.and.realized.in.hardware..So.soware.functions.
are.monitored.by.measuring.the.execution.time..Aer.completion.of.a.function.the.watchdog.is.reset.by.
a.soware.command..If.the.execution.takes.too.long,.the.watchdog.is.triggered.and.predened.actions.
are.taken..e.type.of.monitoring.is.integrated.to.check.if.the.system.is.blocked.or.modied.in.a.way,.so.
that.execution.takes.much.longer.than.expected.
Logic-based
.monitoring.is.used.to.check.if.functions.have.not.been.bypassed..erefore,.a.counter.
is.implemented.that.is.increased.every.time.the.function.has.been.executed..Such.a.counter.is.available.
for.every.safety.function..e.counter.values.are.exchanged.within.xed.periods.of.time.between.the.
safety.chips.to.detect.a.fault.in.the.rmware..If.the.counter.values.are.not.equal.on.both.safety.chips,.
predened.actions.are.taken.
e
.SafetyLon.protocol.stack.incorporates.functionality.to.send.and.receive.sensor/actuator.data.in.a.
safe.way..Additionally,.it.supports.network.management.activities.such.as.conguring.a.node.and.allows.
time.synchronization.[12]..e.message.structure.used.for.the.dierent.tasks.is.shown.in.Figure.47.7.
Every
.safe.message.starts.with.a.specic.header.called.ID..It.species.the.message.type.(data.or.com-
mand
.message).and.the.data.length.n..e.ID.follows.a.3.byte.address.eld..It.includes.the.safe.source.
address.of.a.node..Every.safe.node.holds.a.table.with.a.list.of.valid.sources..e.safe.address.(of.network.
variables.that.is.dierent.from.a.safe.node.address.mentioned.in.Section.47.3).guarantees.that.only.
safe.devices.(valid.sources).can.exchange.safety-related.messages..e.ID.and.safe.address.prevent.that.
unsafe.messages.look.like.safe.messages.
e
.next.eld.consists.of.the.upper.2.bytes.of.the.timestamp.in.the.rst.part.of.the.message.and.the.
lower.2.bytes.in.the.second.part.of.the.message..By.checking.the.timestamp.at.the.destination,.a.delay,.
repetition,.wrong.sequence,.and,.in.conjunction.with.safe.addresses,.an.insertion.of.messages.is.avoided.
In
.addition,.for.detecting.data.corruption.during.transmission,.two.CRCs.with.dierent.generator.
polynomials.are.used..In.case.of.a.payload.smaller.than.8.bytes.a.1-byte.CRC,.otherwise.a.2-byte.CRC.
is.appended..e.CRCs.and.the.comparison.of.the.duplicated.message.parts.(i.e.,.ID,.safe.address,.and.
data).nally.satisfy.the.requirements.for.a.safe.data.transmission.suciently.
In
.the.case.of.sending.a.sensor.value,.each.safety.chip.builds.message.part.1.and.message.part.2.and.
calculates.the.CRC..Safety.Chip.1.receives.the.complete.message.from.the.other.chip.and.compares.
the.whole.message..If.the.CRCs.and.the.two.message.parts.are.identical,.the.message.is.sent,.other-
wise
.discarded..Consequently,.faulty.messages.due.to.a.node.internal.failure.are.not.sent..at.avoids.
wastage.of.bandwidth.and.saves.computational.resources.on.receiver.side.since.it.need.not.process.
the.faulty.message.
On
.the.receiver.side,.the.message.is.forwarded.from.Safety.Chip.1.to.Safety.Chip.2.and.processed.by.
both.(two-channel.structure):.rst,.the.CRC.is.checked.in.order.to.verify.integrity;.second,.the.time-
stamp
.is.used.to.check.for.insertion,.repetition,.and.wrong.sequence.of.a.message;.third,.the.payload.
eld.is.compared.bit.by.bit.to.detect.other.integrity.failures.not.being.revealed.by.the.CRC..Results.on.
the.checks.are.exchanged.between.both.safety.chips..Only.if.both.agree.on.a.positive.result,.the.payload.
is.released.for.further.processing.for.example.by.the.user-application.soware.
Safety
.functions.must.be.called.and.executed.on.a.regular.base..For.that.reason,.a.scheduler.and.
a.state.machine.are.included.in.the.rmware..To.avoid.computational.overhead.and.to.ease.the.inte-
gration
.of.safety.requirements,.no.commercial.operating.system.is.used..However,.a.static.schedul-
ing
.mechanism.is.realized.with.a.xed.cycle.time.and.a.static.sequence.of.functions,.i.e.,.a.single-task.
scheduling..Such.an.approach.rst.of.all.ensures.a.deterministic.timing.behavior..It.guarantees.that.test.
pulses.are.sent.or.the.RAM.test.is.executed.in.xed.time.intervals.that.cannot.be.ensured.for.example.by.
ID ID
Safe address Safe address
Time stamp
MSWord
Time stamp
LSWord
Safety-related data:
n byte
Safety-related data:
n byte
CRC
a
CRC
b
FIGURE 47.7 SafetyLon.message.structure.
© 2011 by Taylor and Francis Group, LLC
