Li S.Z., Jain A.K. (eds.) Encyclopedia of Biometrics
Подождите немного. Документ загружается.


clocks that imprint the time & date onto a time card.
To decrease data entry errors and administrative
overhead, compan ies have migrated to electronic TA
systems that use an ID card or ID number to identify
each employee. However, card-based and ID-based
systems leave open the loophole of buddy-punching,
where employees punch-in or punch-out for one an-
other to be paid for hours they did not work. This
loophole is being closed by biometric TA systems that
ensure all employees are paid for exactly the hours they
are physically at work.
References
1. Rowan L.: Workforce Management for SMB’s: Gaining Control
of Your Most Expensive Resource, IDC, February 2007
2. http://www.dol.gov/esa/whd/regs/compliance/whdfs22.pdf
3. http://www.dol.gov/compliance/guide/minwage.htm
4. http://recognitionsystems.ingersollrand.com/files/600.pdf
5. http://www.timeandtech.com/Docs/ttG-tt3-Datasheet.pdf
6. Rand, I.: Case Study #51 – HandPunch...McDonald’s is Lovin’
It!, February 16th, 2007. http://recognitionsystems.ingersoll-
rand.com/cs/cs.php?id=35
7. Simmons, N.J.: GeoSlavery: Big Brother. Black Star News, Septem-
ber 5th, 2007. http://www.blackstarnews.com/?c¼125&pa¼3660
8. Dir. Steven Spielberg.: Minority Report. Based on short story by
Philip K. Dick. Perf. Tom Cruise. Twentieth Century Fox and
Dreamworks SKG, 2002
9. Clarke, G.T.: Biometrics in the workplace – where to draw the
line? Personal Information Protection Act Conference 2006,
April 26 and 27, 2006. Calgary, AB. http://www.governmente
vents.ca/pipa2006/presentations/a1_gary_clarke_paper.pdf
10. O’Dell, R.: Buddy-punching of timecards is OK, union backers
tell council. Arizona Daily Star (Tucson, AZ), September 7, 2006.
http://www.azstarnet.com/metro/145557.php
Time and Attendance Terminal
A time and attendance terminal is a device that is more
sophisticated than a time clock. It uses electronic data
capture record to record a clock-in or clock-out transac-
tion when the employee presents an authorized creden-
tial to the clock. The credential may be an ID number,
proximity card, smartcard, biometrics etc. There are
three main time and attendance terminals, card or prox-
imity-based, fingerprint, and hand geometry.
▶ Time and Attendance
Time Clock
Time clock is a mechanical or electronic device that is
used to track employee hours. When interacting with
the device, employees either ‘‘punch-in’’ or ‘‘clock-in’’
when registering the start of the time, and ‘‘punch-out’’
or ‘‘clock-out’’ when leaving work or the assigned task.
▶ Time and attendance
Time Series
A time series is a sequence of data points, measured
typically at successive times, spaced at (often uniform)
time intervals. Learning on time series data attempts to
understand the relationship between data and time,
e.g., making forecasts. The order of the data points
along the time axis is an important factor to be con-
sidered in the learning methods.
▶ Incremental Learning
Tongue-Print Recognition
A biometric technology for automatically identifying
or verifying a person using information of tongues.
As the tongue can be protruded from the body for
inspection, the shape and texture information can be
acquired from its images as ‘‘tongue-print’’ for the rec-
ognition process. Unlike face and fingerprint, the tongue
is an internal organ and well protected in the mouth, so
it is basically immune to forgery. This is advantageous
for protecting user’s privacy and security.
▶ Biometrics, Overv iew
1340
T
Time and Attendance Terminal

Tooth Biometrics
▶ Dental Biometrics
Top and Secondary Choices
Every biometric matcher employed for user recogni-
tion compares the presented biometric with the stored
templates and generates the matching scores corres-
ponding to each of the possible user identities . The
top choice refers to the user identity corresponding to
user template generating the highest matching score.
The secondary choices refer to the remaining choices of
the possible user identities corresponding to the tem-
plates that do not generate the highest matching score.
If the difference between the highest matching score
and the second highest matching score is large, there is
high probability that the top choice represents the
correct user identity. However, if this difference is
small, the top choice may not represent the correct
user identity and secondary choices become important
in generating the decision s.
▶ Fusion, Rank-Level
Total Transaction Time
▶ Operational Times
Touch Tablet
▶ Digitizing Tablet
Touch-Screen
A touch-screen is an electronic display that locates and
captures the contact of objects within the display area.
Touch-screens can be divided in two main ty pes: those
oriented to finger-input and the on es oriented to
styles. Touch-screens of stylus oriented hand-held
devices are based on a resistive principle and are not
oriented to operation with the user fingertips. Two
separated metallic layers are connected when the screen
is pressed. The position of the contact point can be
accurately detected, bu t only when the stylus is in
contact with the surface, contrary to pen tablets.
▶ Signature Databases and Evaluation
Tracing
The following of adjacent parallel ridges over a certain
length in the vicinity of the supposed event and by
calculating whether the count of ridges in between
increases or decreases, thus defining the beginning or
ending of a ridge in between.
▶ Fingerprint Matching, Manual
Training
A process used to determine the values of the classifier
parameters with the help of the prototypes of the data
to be recognized. The data used during this step con-
stitute the training set.
▶ Support Vector Machine
Training Data, Sufficiency
A training data set is sufficient for a learning task if all the
knowledge required for correct future predictions is
Training Data, Sufficiency
T
1341
T
contained in the data set. In practice, it is hard to judge
whether a training set is sufficient for a given task.
Generally, if the distribution estimated from the training
data covers all possible examples that may appear in the
task, then the training data is sufficient for the task.
▶ Incremental Learning
Training Signature
Signature used in the enrollment phase.
The training signatures are used for enrollment of a
reference template, reference model parameter estima-
tion, decision threshold estimation, and the like.
▶ Signature Recognition
Transfer Learning
▶ Incremental Learning
Transformation
The transformation refers to the process of normalizing
the output (score) for a matcher to a desired range. The
range of output matching scores generated from the
different biometric matchers can vary significantly.
This variation can be attributed to the different distance
criteria used to generate matching scores or the differ-
ent biometric features employed by different matchers.
▶ Fusion, Rank-Level
Transmission-Based Touchless
Finger Imaging (TTFI)
TTFI refers to tou chless fingerprint sensor.
▶ Fingerprint, Palmprint, Handprint and Soleprint
Sensor
Transportable Asset Protection
ANTHONY P. RUSSO
Atrua Technologies, Inc, New York, NY, USA
Synonym
Asset protection
Definition
Transportable Asset Protection is a means by which
personal user secrets and privileges, stored in digital
form on a portable device such as a smart card or a
mobile handset, are secured from unauthorized access
and/or use. The assets, being carried on one’s person,
are highly prone to theft or loss, making the need for
security that much greater. The unique challenge posed
by Transportable Asset Protection is to provide ade-
quate security and performance using the lightweight
processing resources available on the mobile device in a
portable and interoperable way.
Introduction
The nature of a transportable asset is that it is carried
from place to place and therefore prone to theft or loss.
Once lost or stolen, the vessel (or vault) holding the
asset is subject to relentless physical attack by a hacker,
possibly for an indefinite period of time. As our society
grows more mobile, our transported assets become
more valuable and our thieves more sophisticated,
hence the need for greater security and privacy is
increasing ra pidly. Transportable asset protection in
the modern sense was ushered in with the invention
of smart cards. Incorporating biometric authentica-
tion into such systems is a relatively new application
and research areas designed to address the unique
needs of mobile users for whom the standard methods
of authentication are either too cumbersome or not
secure enough.
A transportable asset protection system that uses
biometrics will incorporate at least one mobile com-
puting device or host capable of storing the asset.
Examples of mobile devices include smar t cards,
SIM cards, PDAs, mobile handsets, FLASH storage
tokens, notebook computers and other such relatively
1342
T
Training Signature

small lightweig ht items that can store data and/or
access services. Except for the notebook computer,
these devices are all examples of embedded systems,
and therefore include some limited – typically very
limited – dynamic memor y and compute power.
An asset can be any digital item of value to a user.
Asset types fall into three broad, somewhat overlap-
ping categories: (1) user secrets, (2) physical or logical
access to places or services and (3) rights. Secret data is
most commonly in the form of username and pass-
word data that can be used to access large amounts of
confidential information, such as corporate databases
or encrypted documents. In more secure systems the
secret may be the private key of a digital certificate,
used to cryptographically encode and sign data. Accor-
dingly, these types of assets have a hard-to-measure
value to all involved parties that depends on the con-
fidentiality of the secret.
Examples of privileged access include access to
wireless or corporate networks, use of services such as
internet access, online banking, or mobile-commerce
transactions. While passwords and keys are sometimes
used to access these services, many such system s
require a secure hardware token (e.g., smart card) for
multi-factor authen tication. These kinds of assets usu-
ally have a directly measurable monetary value to the
user and/or the service provider.
Finally, the last category of assets is the right to use
a device or a digital file. Devices with restricted use are
myriad, including automobiles, photocopy machines,
cell phones and firearms. However, digital rig hts are
also becoming increasingly important: the right to
listen to a downloaded song or watch a movie or
open a document. Digital Rights Management and
transportable asset protection are likely to become
increasingly coupled in the future. In most of these
cases the user has a reason to prevent third parties from
obtaining the asset; in other cases it is the serv ice
provider that the vested interest.
From an implementatio n perspective, of parti-
cular interest – due both to their importance and
popularity – are those systems composed of a host
(e.g., mobile handset) and a hardware token or other
▶ secure element (SE) used to store secrets and/or
provide access to services. The biometric sensor is
attached to the host, which usually offers little or no
physical protection from hackers and may provide
dubious overall security. In contrast, the secure ele-
ment – physically or wirelessly connected to the host
– is typically a closed, tamper-resistant, well-trusted,
standardized and usually certified system with a very
lightweight microcontroller and some FLASH memory
or EEPROM storage. Smart cards and SIM cards are
the most prevalent examples of SEs that are completely
separate entities from the host.
▶ Near Field Commu-
nication (NFC) controller chips, used for short ra nge
mobile transactions, are an example of a device that
can be permanently integrated into the host hardware
itself. The Trusted Platform Module (TPM) is the
secure element insid e the high-end notebook compu-
ters that incorporate them.
A well-designed secure element is a single-chip
entity designed to exacting specifications to achieve a
‘‘black box’’ nature. In the locked state, therefore, an SE
is fairly impenetrable. However, the vast majority of
these devices are unlocked by entering a 4-digit Per-
sonal Identification Number or PIN, which in itself is
not terribly secure, since a PIN entry can be observed
by onlookers and does not tie the unlocking process to
a person as would biometric authentication. Further-
more, when cryptography is employed in a system,
such as digitally signing a document, the expectation
is for a very high level of security and trust. However,
those having experience with such systems know that
the weakest link is often in protecting the private key,
something that most existing secure elements rely
upon and that a simple PIN can provide. Without a
biometric match, the system-wide security of a 256-
bit cryptographic key is reduced from 2
256
to 10
4
per break-in attempt. Hence the need for biome trics is
clear, not only for increased security but also
convenience.
Despite the drawbacks of the PIN, in the discussion
that follows the host is considered to be a non -secure
entity while the secure element is maximally trusted.
Therefore, the more processing done on the secure
element, the safer the system. As will become clear,
the most secure platforms are the ones in which the
host and the secure elements are the same physical
device.
System Architectures
Implementations of transpor table asset protection sys-
tems are varied. The most tr ivial, least secure architec-
ture employs only a host, with no secure element
connected to the system. Security risks abound, the
Transportable Asset Protection
T
1343
T

most important of which is the lack of any secure
element to protect the assets. While the host itself
might employ security features such as user locking,
those are easily circumvented by a thief who steals the
phone and accesses the filesystem through alternate
hardware means. In short, this architecture is too inse-
cure to constitute a useful asset protection system.
However even those implementations that use a
secure element can vary widely in effectiveness.
Figures 1, 2 and 3 show examples of transportable
asset protection system s that offer basic security
(Fig. 1), very good secu rity (Fig. 2) and maximal
security (Fig. 3). Referring to the basic security archi-
tecture, a secure element is used only to protect the
assets and nothing else. In this case, the biometric
sensor, template extraction algorithms, and matcher
all execute from the host CPU, and enrolled template
data is stored on the host’s filesystem. This imple-
mentation is the easiest to engineer because typically
the host has much more processing power and memo-
ry than a secure element. Assets are protected with
only a PIN, but putting aside that shortcoming for
the moment, a number of additiona l security risks
exist with such a system.
Transportable Asset Protection. Figure 1 Diagram describing a basic transportable asset protection system employing
a host and a Secure Element. The host is connected to a biometric sensor and performs all template extraction
tasks. The secure element is used only to store assets, and must be unlocked using a PIN. Once unlocked, the secrets
are accessible by the host.
Transportable Asset Protection. Figure 2 Diagram of a transportable asset protection system employing the MOSE
architecture. The host is connected to a biometric sensor and performs all template extraction tasks. Assets and enrolled
templates are saved on the secure element, which has the ability to perform a biometric match. The SE is unlocked via a
PIN or by sending it a live scan template that matches the stored enrolled template. Once unlocked, the secrets are
accessible by the host.
1344
T
Transportable Asset Protection
The first security hole is that templates must be
stored on the filesystem. This means these templates
are readable by anyone operating the host device, repre-
senting both a security and a privacy issue, as the tem-
plates themselves could be considered an asset. While the
natural inclination is to encrypt this data, the problem is
that encryption requires a private key, and that key must
be stored someplace for use later during decryption.
Usually the key is hidden somewhere on the filesystem
or in the code itself, but this kind of ‘‘security by obscu-
rity’’ is a major risk nonetheless [1]. If the host does not
guard against tampering, then it would be quite easy
for a hacker to access the data in unencrypted form by
tapping the memory bus during the match process,
where it must be in plaintext form prior to use. Even
easier hacks involve modifying the results of the
matching algorithm to force a match even when one
does not exist. [2]
A variation on this system uses the secure ele-
ment to simply store the enrolled templates, thereby
removing the need to store them on the host and
offering increased protection if the host is lost or
stolen. In this case, the templates are stored safely on
the tamper-proof secure element, where presumably
only very advanced hacking techniques could unlock
it. This approach offers only a marginal increase in
security, however, if the host and the secure element
are both lost, which can often be the case (e.g., a
mobile phone + SIM card). The memory tapping
techniques are still effective as the secrets must leave
the card before they are matched, and altering the
match results is still possible because the match occurs
on the host. Of note is that a PIN must still be used
to unlock the secure element before a biometric match
can be performed, and though this can be considered a
security feature, it removes the user convenience that is
a major selling point of biometric implementations,
since PIN entry, especially on a small mobile device, is
often cumbersome.
A much more secure approach is shown in Fig. 2,
where the matching algorithm is executed inside the
secure element itself, thereby eliminating the need for
PIN entry entirely. This configuration is commonly
referred to as
▶ Match-on-Card (MOC) when used
with a smart card or SIM card [3]. A more general
term is Match-on-Secure-Element (MOSE). In this
architecture, the sensor and templa te extraction are
still performed on the host, bu t during the verification
process, the template is sent to a locked secure element,
which only opens upon a successful match against the
enrolled templates stored there. This approach has a
number of important advantage s. Firstly, the enrolled
template data, once stored, never leaves the secure ele-
ment for any reason; it is well-protected under all cir-
cumstances. Secondly, it is not possible to simply alter
the match results because the matcher executes in a safe,
black box environment. One other important aspect of
this implementation is that it allows for secure replace-
ment of the PIN with a biometric. This preserves both
the convenience and security largely responsible for the
market success of biometric systems.
The attacks on such systems tend to focus on the
host processing: both sensor data and extracted tem-
plates can be snooped and modified, allowing for
Transportable Asset Protection. Figure 3 Diagram of a transportable asset protection system employing a host that
is itself a secure element. All processing is performed on the secure host, making it the most trustworthy, albeit
the most costly design choice.
Transportable Asset Protection
T
1345
T

replay and denial-of-se rvice attacks. These issues are
addressable for the most part, as this class of hacks can
only be launched during the authentication process
and therefore will be useless if the device is stolen
afterward. Overall, this is the most cost-effective and
technologically feasible approach to transportable asset
protection.
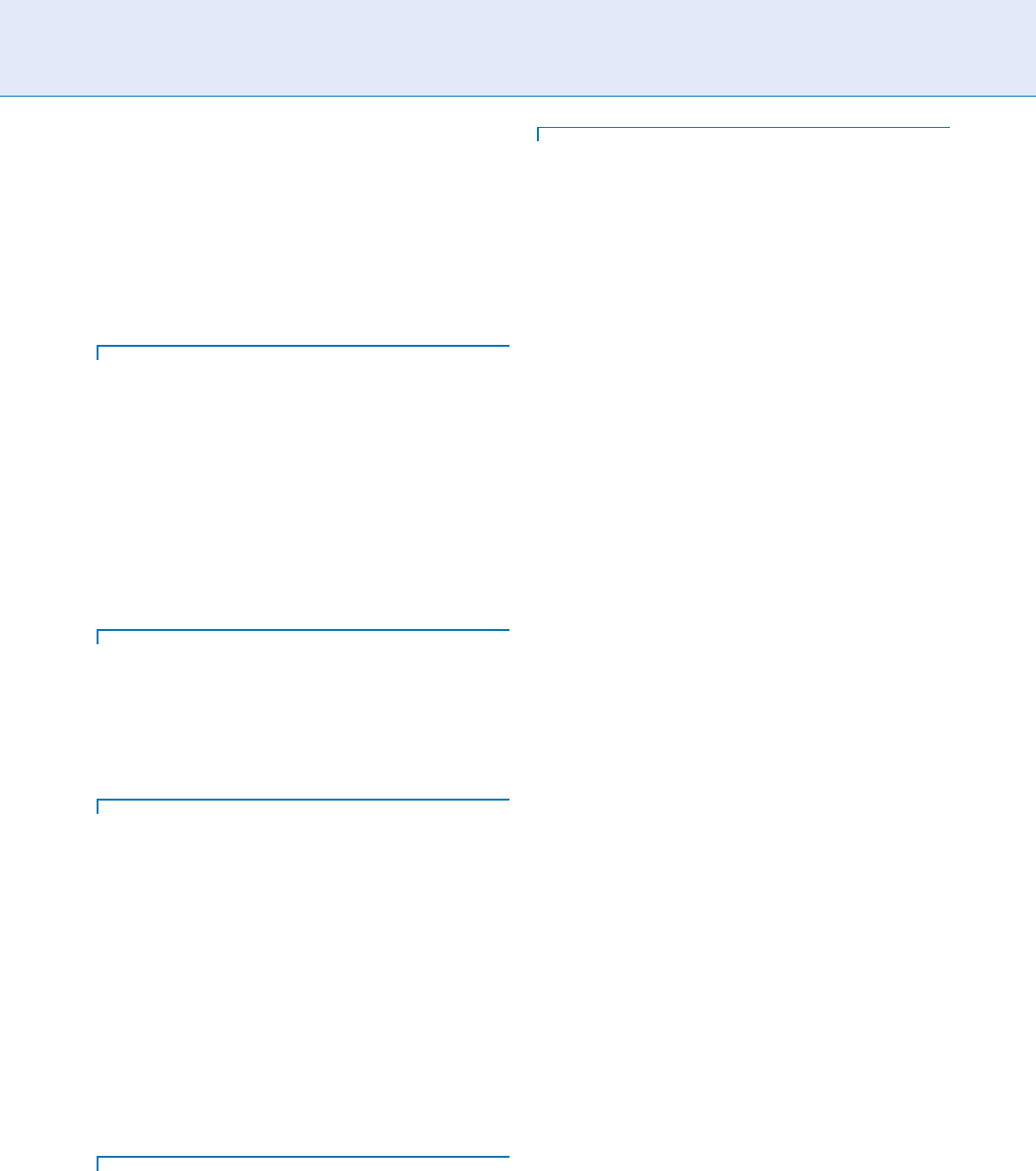
The least cost-effective approach, but offering the
highest level of security, is one in which the sensor,
template extraction, and matching are all located on
the secure element (see Fig. 3). In this case it is not
possible for a hacker to snoop or alter any biometric
data or algorithms. The most promising attacks on
such a system involve fake-finger spoofing, for which
there are countermeasures available. However, such a
system is costly, because the microcontroller on the
secure element can no longer be lightweight: much
more memory and computing power would need to
be available to process the raw biometric data into a
template and perform the match. Other considerations
involve powering such a secure element and addressing
the mechanical mounting issues presented by placing a
sensor on a smart card or other miniature dev ice,
where it must meet flexibility and height standards to
be universally adopted.
Role of Standards
As noted, the secure elements used to protect trans-
portable assets are t ypically standard-based tokens
such as smart cards and SIM cards. Being portable,
standards have evolved so that these tokens can inter-
operate with a variety of different host hardware, as
long as the token and the host support the same stan-
dard. For commercial deployments, it has become
increasingly difficult to attract interest in proprietary
solutions and formats due to this expectation of
interoperability.
A good example to illustrate the need for standards
is a GSM-based mobile handset, which uses a SIM
card to verify the user and provide wireless network
access. Let’s assume this is a MOC system where the
biometric sensor and template extraction algorithms
are on the handset, and the removable SIM card has
embedded in it a biometric matcher where the en-
rolled templates are stored on the SIM card. Given
that wireless network operators require that a SIM
card be usable in any GSM handset, it is prudent to
ensure that handsets adhere to the same template
format standard that the SIM card does, or else the
biometric matching would not work. While it is pos-
sible and sometimes necessary to fall back to having
the user enter a PIN instead, this scenario is undesir-
able from the operators’ point-of-view as it weakens
the value of deploying biometric SIM cards to their
network subscribers.
The ISO-7816 standard [4] is an example of
how smart cards interact with their hosts at both an
electrical, physical, and communication level, and ISO-
7816-11 even allows for biometric Match-on-Card
commands. But as the above example illustrates, stan-
dard commands are not enough to ensure compati-
bility. In a MOSE architecture the host and secure
element must agree on the nat ure and format of bio-
metric templates to be used for enrollment and
unlocking . Although some widely-accepted standards
exist for face recognition [5] and other biometrics [6],
fingerprints currently offer the most options in this
regard, and the only ones thus far designed to directly
address the requirements of a MOSE system [7].
Algorithmic Challenges and
Approaches
To fully appreciate the challenges involved with creating
a biometric matcher for use within a secure element, it is
necessary to understand the execution environment in
which it runs. The most common secure elements em-
ploy 8-bit or 16-bit microcontroller units (MCUs), hav-
ing available RAM from 500 bytes to 2KB, and 128KB or
less of ROM. Internal clock rates are typically below 30
MHz, often in the 7–15 MHz range. There is usually no
floating-point support, and sometimes no native hard-
ware support for signed integer math, as is the case with
an 8051-class MCU [8]. The computational power of
the Pentium-class CPU found on most PCs is roughly
3 orders of magnitude more than that of the MPU
found on most secure elements; available RAM is 6
orders of magnitude more. While the processing power
for secure elements does increase from year to year,
low-end security processors continue to dominate the
mass market due to its low cost. Therefore, it is impor-
tant to design it with these in mind.
The simplest overall approach is to design the bio-
metric template so that it is a statistical feature vector,
allowing matching to be done via a linear or non-linear
1346
T
Transportable Asset Protection

classifier, which is more suitable for imple mentatio n
on low-end MCUs. Cer tain biome trics lend themselves
more easi ly to lig htwe ig ht matc hing algor ithms than
others. Iris match ing and DNA match ing are two
example s w here most of the comp utational effor t is
in the templa te extraction step, while the match ing
step is relatively straig htfor ward. Standard fing erprint
match ing does not fall into this categor y – it t y pi cally
req uires both local and g lobal geometric informati on –
which is unfor tunate given its populari t y w ith and
suitabili t y fo r mobile platfor ms.
Nonetheless, most of the implementation issues
have been overcome, and fingerprint-based MOSE sys-
tems are among the most popular, including Giesecke &
Devrient’s STARCOS 2.4 smart card Operating System
w ith On-card matcher [9]. The initi al FP-b ased MOSE
algor ithms, first introduced in 1999, used proprietar y
templa tes [10, 11] for which much of the data was
preprocessed on the ho st to minimize the compu ta-
tional load on the secu re elem ent. Second-generatio n
algor ithms use a standards-based templa te format [7]
but, due to the adde d burden this puts on the secure
elem ent, accurac y tra deoffs have been necessar y to
achieve acceptable match speed. Current work under-
way by the aut hor promises a more comple x third-
generati on, standards-based minu tiae matc hing
algor ithm w ith mu ch smalle r accuracy degradati on
and suit abilit y for execu tion on most secure elem ents.
Of note is that pattern match ing techn iques for
finge rprints, w ith their relatively l arge templa te size
and image-processing-b ased algorithms , are harder
to imp lement and in many cases simply not practical,
leaving the aforementioned stat istical featu re-vector
approach as the best alte rnative to minu tia-based
metho ds. Unfor tunately, in additi on to accuracy
issues , proprietar y stat istical approaches suff er from
lack of a ny w id ely-accepted tem plate standards, drasti-
cally reducing their suit abilit y for the marketplace.
Recent Trends
The overall trend for biome trics – esp ecially
finge rprints – is rapidly grow ing in the cons umer mar-
ket, most notably in noteboo k compu ters, mob ile
phone s, door locks a nd USB storage tokens. Whi le
some of these applicati ons focus on the convenience
aspec t of bio metrics (e.g ., password replacement) al-
most all of them perform some sor t of asset protection
functio nalit y, w ith var y ing levels of secu rit y depending
on the des ign and applicati on.
Simil arly, MOSE system s for asset protection con-
tinue to gain in populari t y, and dep loyments are
expecte d to grow quite ra pidly in the nex t 2–5 years.
Mobile handset applica tions, which employ N FC
chips and/o r SI M cards, are driv ing the commercial
need . Atrua Technolo gies, Inc ., by which the aut hor is
employed, has demo nstrated the first SIM card w ith
on-chi p fingerprint matchin g in 2007 as w ell as the
first NFC controller w ith on-chi p matchin g . It is
expecte d that variou s vendors w ill offer MOSE capabl e
system s in the near future and that mobile hand sets
w ith MOSE capabi lities w ill reach the mass market
worldw ide w ithin this timefr ame.
On the government side, the U.S. has recently put
together guidelines for t esting Personal Identit y Verifica-
tion (P IV ) c ards [12 ] withfingerprint-basedmatch-on-
card capabilit y using FIPS 201 minutiae format stan-
dards. A s PIV cards have become the standard w ay o f
identifying U .S. Government employ ees, the added secu-
rity and con venienc e of match-on-card will see a wide
deployment if the planned technology trials are
successful.
Related Entries
▶ Template Security
▶ Biometrics and Security, Standardization
▶ Common Biometric Exchange Formats Framework,
Standardization
▶ Fingerprint Matching, Automatic
References
1. Schneier, B.: Applied cryptography, Wiley, Inc., New York (1996)
2. Maltoni, D., Maio D., Jain, A.K., Prabhakar, S.: Handbook of
fingerprint recognition, Springer, New York (2003)
3. Russo, A.P.: ‘‘Fingerprint-based authentication and smart cards:
Issues and trends’’, E-Payments 2000 Conference. http://www.
epf.net/PrevMtngs/Sep00/Sep00Meeting.html. Accessed Oct 5,
2000
4. ISO/IEC 7816-4: ‘‘Information technology–Identification cards–
Integrated circuit(s) cards with contacts, Part 4: Interindustry
commands for interchange,’’ International Standard (1995)
5. ANSI-INCITS 385-2004: American National Standard for
Information Technology – Face Recognition Format for Data
Interchange (2004)
Transportable Asset Protection
T
1347
T

6. ANSI-INCITS 398-2005: American National Standard for Infor-
mation Technology – Common Biometric Exchange Formats
Framework (CBEFF) (2004)
7. ISO/IEC 19794-2: Information Technology—Biometric Data
Interchange Formats—Part 2: Finger Minutiae Data (2005)
8. MacKenzie, I.S., Phan, R.C.-W.: The 8051 Microcontroller, Pren-
tice Hall, (2006)
9. Giesecke & Devrient: STARCOS
1
2.4 Card Operating
System, Bio Version http://www.gdai.com/portal/page-_pageid=
42,70526&_dad=portal&_schema=PORTAL.htm. Accessed Dec
30, 2005
10. Russo, A.P.: Fingerprint matching algorithm for low-cost 8-bit
smart cards. RSA Conference Europe 2000 (2000)
11. Russo, A.P. (inventor): Method and system for fingerprint tem-
plate matching. U.S. Patent Number 6681034 (1999)
12. National Institute of Standards and Technology: FIPS Pub 201-1
Personal Identity Verification (PIV) of Federal Employees
and Contractors. Federal Information Processing Standards
Publication (2006)
Tread Pattern
The outsole or undersi de of a shoe can sometimes have
a complex pattern of ridges and various shapes which
provide traction for the wearer. For example, athletic
shoes may have a tread pattern composed of many
slanted ridges placed close together so as to give an
improved grip to the running surface, while hiking
shoes may have a thick and high profiled wedge-
shaped tread for easy walking in soft terrain. This
complex pattern is commonly referred to as a tread
pattern.
▶ Footwear Recognition
Trusted Biometric System
Biometric system with template protection, compared
to traditional biometric system, paying more attention
to security and privacy issues of the users.
▶ User Interface, System Design
Trusted Traveler
▶ Registered Traveler
1348
T
Tread Pattern
U
UBM
▶ Universal Background Models
ULW
▶ Universal Latent Workstation
Unauthorized Data Collection
In principle, all data collected must be backed by the
law, whether state legislation or contractual obliga-
tions. A data item may well be necessary for a particu-
lar purpose, but this does not mean that the purpose
itself is authorized, or that the agent (human or ma-
chine) collecting the data is empowered to do so.
▶ Privacy Issues
Unauthorized Data Disclosure
From a privacy perspective, the end-user owns his or
her own personal data, even if the data resides in an
organization’s computer system. Therefore, permission
should be sought from the end-user before data is
disclosed or shared. In practice, different jurisdictions
have different notions of data ownership, which may
result in disclosure without the end-user’s explicit con-
sent or even knowledge.
▶ Privacy Issues
Unification Framework
A unification framework includes a collection of fusion
algorithms and it uses the evidences obtained from the
input biometric probe data to dynamically select the
optimal fusion algorithm. The selected fusion algo-
rithm is then used to compute the fused biometric
information. The unifi cation or reconciliation should
satisfy most of the application requirements and yield
better recognition performance.
▶ Fusion, Sensor-Level
Universal Background Models
DOUGLAS REYNOLDS
MIT Lincoln Laboratory, Lexington, MA, USA
Synonyms
General model; Person-independent model; UBM;
World model
Definition
A Universal Background Model (UBM) is a model use d
in a biometric verification system to represent general,
person-independent feature characteristics to be com-
pared against a model of person-specific feature char-
acteristics when making an accept or reject decision.
For example, in a speaker verification system, the
UBM is a speaker-independent Gaussian Mixture
Model (GMM) trained with speech samples from a
large set of speakers to represent general speech char-
acteristics. Using a speaker-specific GMM trained with
speech samples from a particular enrolled speaker, a
#
2009 Springer Science+Business Media, LLC
