Li S.Z., Jain A.K. (eds.) Encyclopedia of Biometrics
Подождите немного. Документ загружается.


protection, primarily against secondary use of biomet-
ric images [5] It would also reduce the vulnerability of
network protocols based on biometrics [7]. Biometri-
cally enabled computers and mobile phones currently
must hide passwords and keys in software; biometric
encryption would protect against this vulnerability.
Another interesting application is for control of access
to digital content with the aim of preventing copyright
infringement. Biometric encryption systems are not
widely deployed; research systems still suffer from
high error rates and slow processing speed. However,
such systems offer some compelling benefits for many
applications, and research is active.
Cancelable biometric features (see Cancelable Bio-
metrics) are encoded with a distortion scheme that
varies from application to application. The concept
was developed to address the privacy and security
concerns that biometric features are not secret and
cannot be canceled. During enrollment, the input bio-
metric image is subjected to a known distortion con-
trolled by a set of parameters. The distorted biometric
sample can, in some schemes, be processed with stan-
dard biometrics algorithms, which are unaware that
the features presented to them are distorted. During
matching, the live biometric sample must be distorted
with the same parameters, which must be security
stored. The cancelable nature of this scheme is pro-
vided by the distor tion, in that it is not the user’s
‘‘actual’’ biometric which is stored, but simply one of
an arbitrarily large number of possible permutations.
The concern with cancelable biometric features is
the security of the storage and transmission of the
distortion parameters.
Biometric cryptosystems (
▶ Encryption, Biometric)
are designed to overcome many security issues in
traditional biometric schemes by avoiding template
storage and the match stage of biometric processing.
Instead, the biometric features are bound to a secret
key that is designed to be recoverable only with a
biometric image from the enrolled indiv idual. Clearly,
the key difficulty in the design biometric encr yption
systems is the variability in the biometric image be-
tween measurements; the presented biometric image
cannot itself be treated as a code, since it varies with
each presentation.
The earliest biometric encryption system was pro-
posed by Soutar et al. [18]. Enrollment creates a tem-
plate binding a secret code to the multiple sample
images. During decryption, an error correcting scheme
based on Hamming distance is used to allow for vari-
ability in the input image. Similar schemes were
proposed for voice passwords (in which a vector of
features is calculated, and each value is used to sele ct
a fraction of the key bits from a table)and iris images.
A significant body of work on biometric encryp-
tion has been done in the cryptograp hy community,
much based on the fuzzy vault construction of Juels
and Sudan [19]. This scheme allows a cryptographic
encoding with a variable number of un-ordered data
points, which makes it suitable for fingerprint minu-
tiae. Clancy et al. [20] designed a fingerprint algorithm
that encodes the secret as the coefficients of a Galois
field polynomial. Minutiae points are encoded as
coordinate pairs, and numerous ‘‘chaff ’’ points are
added. During key release, the points closest to the
new minutiae are chosen, and the key estimated
using an error correcting scheme.
Encoded biometric schemes potentially offer some
important advantages in security and privacy, since the
template does not need to be available in unencrypted
form. However, little work has been done to study the
security of biometric encryption schemes. Uludag
et al. [21] note that most proposed biometric encryp-
tion systems only appear to account for a ‘‘limited
amount of variability in the biometric representation.’’
They suggest that many biometric encr yption systems
can be attacked simply via the FAR, by presenting
biometric samples from a representative population.
A cryptographic attack of biometric encryption was
developed by Adler [22], based on using any ‘‘leaked’’
information to attempt a hill-climbing of the bio-
metric template. Overall, while biometric encryption
offers signific ant promise, there is little understand-
ing of the practical applicability and security of these
systems.
Performance of Biometrics Security and
Liveness
In order to quantify and compare the security and
liveness performance of biometric systems, it is neces-
sary to have appropriate figures of merit. There exists
well understood measures of biometric performance
under zero-effort impostor attempts: the false accept
(FAR) false reject rates (FRR), failure to acquire, and
transaction time among others. It is conceptually rea-
sonable to extend these measures to the active attackers
1150
S
Security and Liveness, Overview

considered here (although there are clear experimental
difficulties in per forming the measurements).
In general, a securit y protection measure is created
to protect against a particular active attacker. Using the
example of a liveness (L) detectio n system, the follow-
ing measures are defined:
L false reject ratio (LFRR): the number of times a
legitimate attempt is rejected as an attack, divided
by the total number of legitimate attempts.
L false accept ratio (LFRR): the number of times
an active attack against L (a spoof, in the case of
liveness) is accepted as legitimate divided by the
total number of attack attempts.
L failure to acquire: The number of times the L
module to is unable to collect information to
make a decision, divided by the total number of
attempts.
L mean transaction time: The average time required
by the L module to make a decision.
In a general biometric system, one or more security
protection measures (L) will function in addition to
the core biometric (B) decisions. The performance of
the combination of a security measure and a biometric
matcher is defined a s the combined system performance,
with the following measures:
System false reject ratio (SFRR): the number of
times a legitimate attempt is rejected as an attack
(by L) or an impostor (by B), divided by the total
number of legitimate attempts. Here, false rejects
are the combined set of errors from the biometric
stage (false reject of the correct person) and errors
from the liveness stage (L false reject). Thus, the
SFRR is the union of the FRR and the LFRR. In
general, SFRR FRR þ LFRR, because some
transactions may be rejected by both L and B.
System false accept ratio (SFAR): the number of
times an active attack or an impostor is accepted
as legitimate divided by the total number of attack
or impostor attempts. This definition is more com-
plicated, since the measure must combine evalua-
tions of spoof accepts (against L) and traditional
false accepts (against B). This measure is modified
by the expected frequency of impostor and attack
attempts, and thus by the relative weight of these
events in the test database.
System failure to acquire ratio: The number of times
the L module or the biometric system B is unable
collect information to make a decision divided by
the total number of attempts.
System mean transaction time: The average time
required by the entire system to make all decisions
(including the liveness and match decisions).
Clearly, the main difficulty in making these mea-
surements is developing a databas e or procedures for
the active attacks, which are somehow reflective of
their expected frequency in the target operational con-
ditions. Nevertheless, such measures are important to
clarify how security measures impact on the overall
system performance. For example, a biometric system
with very good performance (1% EER) will be greatly
impacted by a liveness algorithm that has a liveness equal
error rate of 5%. In this case, the system false reject ratio
is equal to the union of the two measures, that is between
5% and 6%. This would represent a dramatically worse
system in terms of the experience of its users.
Summary
The security of a biometric system is its resistance
to active attack. Such attacks may be classified as
Presentation attacks (spoofing), in whi ch the appear-
ance of the biometric sample is physically changed
or replaced; Biometric processing attacks, in which an
understanding of the biometric algorithm is used to
cause incorrect processing and decisions; Software and
networking vulnerabilities, based on attacks against
the computer and networks on which the biometric
systems run; and Social and presentation attacks,in
which the authorities using the systems are fooled.
In this article, a survey of issues in biometric security
and liveness (anti-spoofing) have been presented,
including frameworks to classify and measure bio-
metric security performance. In addition, encoded
biometric schemes are reviewed to clarify their promise
to to counter these securit y threats. Overall, in the
design of security and liveness systems, it is impor-
tant to consider the operational requirements of the
application and the specific security threats against
which it will be tested.
Related Entries
▶ Encryption, Biometric
▶ Biometric Security, Overview
Security and Liveness, Overview
S
1151
S
▶ Biometric System Design
▶ Biometrics and Security, Standardization
▶ Biometric Vulnerabilities, Overview
▶ Cancelable Biometrics
▶ Fraud reduction
▶ Liveness Detection: Face
▶ Liveness Detection: Fingerprint
▶ Liveness Detection: Iris
▶ Liveness Detection: Voice
▶ User Interface, System Design
▶ Zero-effort Forgery Test
References
1. Ferguson, N., Schneier, B.: Practical Cryptography. John Wiley &
Sons, NJ, USA (2003)
2. Schneier, B.: The Uses and Abuses of Biometrics. Communica-
tions of the ACM vol. 42, pp. 136 (1999)
3. Maltoni, D., Maio, D., Jain, A.K., Prabhakar, S.: Handbook of
Fingerprint Recognition. Springer, Berlin (2003)
4. The Guardian (17 Nov. 2006) Cracked it!
5. Cavoukian, A.: Privacy and Biometrics, In Proceedings of
the Intertnational Conference on Privacy and Personal Data
Protection, Hong Kong, China (1999)
6. Ratha, N.K., Connell, J.H., Bolle, R.M.: Enhancing security
and privacy in biometrics-based authentication systems. IBM
Syst. J. 40, 614–634 (2001)
7. International Committee for Information Technology Standards
(INCITS) Study Report on Biometrics in E-Authentication,
Technical Report INCITS M1/06-0693 (2006)
8. Thalheim, L., Krissler, J.: Body Check: Biometric Access Protec-
tion Devices and their Programs Put to the Test, ct magazine,
November (2002)
9. Schuckers, S.A.C.: Spoofing and anti-spoofing measures, Infor-
mation Security Technical Report, vol. 7, pp. 56–62 (2002)
10. International Biometric Group, (2007) Spoof, Test underway of
fingerprint and iris recognition systems’ resistance to spoofing
http://www.biometricgroup.com/spoof/ 2007. Accessed 7 April,
2009
11. Matsumoto, T.: Gummy Finger and Paper Iris: An Update,
Workshop Inform Security Research, Fukuoka, Japan, October
(2004)
12. International Biometric Group, Liveness Detection in Bio-
metric Systems, http://www.ibgweb.com/reports/public/reports/
liveness.html
13. Schuckers, S.A.C., Derakhshani, R., Parthasardhi, S., Hornak, L.A.,
(2006) Liveness Detection in Biometric Devices, in Electrical
Engineering Handbook, 3rd edition, CRC Press, Chapter 26,
ISBN: 084932274X
14. Coli, P., Marcialis, G.L., Roli, F.: Vitality Detection from Finger-
print Images: A Critical Survey, Advances in Biometrics, Spring-
erlink, vol. 4642, pp. 722–731 (2007)
15. Antonelli, A., Cappelli, R., Maio, D., Maltoni, D.: Fake Finger
Detection by Skin Distortion Analysis. IEEE Trans. Inf. Forensics
Secur. 1(3), 360–373 (2006)
16. Biel, L., Pettersson, O., Philipson, L., Wide, P.: ECG analysis: A
new approach in human identification. IEEE Trans. Instrum
Meas. 50, 808–812 (2001)
17. Davida, G.I., Frankel, Y., Matt, B.J.: On enabling secure applications
through off-line biometric identification. In Proceedings of the
IEEE Symposium on the Privacy and Security. pp. 148–157 (1998)
18. Soutar, C., Roberge, D., Stoianov, A., Gilroy, R., Vijaya Kumar, B.:
Biometric Encryption using image processing. In Proc. SPIE Int.
Soc. Opt. Eng. 3314, 178–188 (1998)
19. Juels, A., Sudan, M.: A fuzzy vault scheme, In Proceedings of
the IEEE International Symposium on the Information Theory.
pp. 408 (2002)
20. Clancy, T.C., Kiyavash, N., Lin, D.J.: Secure smartcard-based
fingerprint authentication. In Proceedings of the ACMSIGMM
2003 Multimedia, Biometrics Methods and Applications Work-
shop. pp. 45–52 (2003)
21. Uludag, U., Pankanti, S., Prabhakar, S., Jain, A.K.: Biometric
Cryptosystems: Issues and Challenges. Proceedings of the IEEE.
vol. 92, pp. 948–960 (2004)
22. Adler, A.: Vulnerabilities in biometric encryption systems. In
Proceedings of the AVBPA, Tarrytown, NY, USA, LNCS 3546:
1100–1109 (2005)
Security Block
▶ Common Biometric Exchange Formats Framework
Standardization
Security Issues, System Design
KARTHIK NANDAKUMAR
Institute for Infocomm Research A *STAR, Fusionopolis,
Singapore
Definition
Person authentication is one of the critical tasks in a
securing information technology (IT) systems and bio-
metric recognition is a natural and reliable solution
that can provide secu re authentication. However,
a biometric system is just one component of the over-
all IT security solution. To ensure the confidentiality
1152
S
Security Block

of the biometric information and the integrity of the
biometric system, several securit y issues must be
addressed in the design stage. Appropriate steps must
be taken to guard against the vulnerabilities at the
interfaces between the different components of the
security system and the threats introduced due to
improper implementation and administration of the
biometric system. Furthermore, the securit y of a bio-
metric system must be analyzed systematically based
on standard methodologies such as the Common
Criteria framework.
Introduction
In today’s digital world, a wide variety of information
technology (IT) systems is used by the government (e.g.,
e-governance) and private organizations (e.g., e-com-
merce) to deliver their products and services to the
society. The security of these IT systems is of vital im-
portance because any security breach c ould potentially
lead to adverse consequences such as terrorist attacks,
financial frauds and loss of privacy. In the context
of IT systems, security can be defined as ‘ ‘protection of
information and information systems from unautho-
rized access, use, disclosure, disruption, modification,
or destruction’’ [1]. In general, there are four major
aspects to be considered in IT system security.
Secure authentication – only legitimate/authorized
users should able to access the system and carry out
specific tasks.
Data confidentiality – prevent illegitimate access or
disclosure of sensitive data or information.
Integrity – guard against improper modification or
destruction of the system/data and ensure nonre-
pudiation and authenticity of information.
Availability – guarantee timely and reliable access
to and use of information.
Biometric recognition is one of the techniques
that can effectively address the secure authentication
problem. Since biometric traits cannot be easily lost,
stolen, misplaced or shared, biometric recognition
offers a natural and more reliable authentication solu-
tion compared to other techniques such as passwords
or physical tokens (e.g., ID cards). However, it is
important to realize that a biometric system is just
one component of the overall IT security solution
because it address only the secure authentication as-
pect. Other techn ologies such as encryption, digital
signature, etc. are needed to meet the confidentiality,
integrity, and availability requirements of the complete
IT system. Moreover, the biometric system can itself be
considered as an independent subsystem within the
complete IT system. If the biometric system (or subsys-
tem) is compromised or circumvented, the security of
the entire IT system gets affected. Due to this reason,
the security aspects involved in the design and imple-
mentation of a biometric system should be analyzed
independently [2–4].
Biometric System Architecture
The general architecture of a biometric system is
shown in Fig . 1. There are four majo r modu les in a
generic biometric system, namely, sensor, feature ex-
tractor, matcher, and decision module. Sensor is a part
of the interface between the user and the biometric
system and its function is to scan the biometric trait of
the user. The biometric user interface may also have
other functionalities such as collecting the identity
claim from the user and providing feedback or guid-
ance to the user on how to present the biometric data.
Feature extraction module processes the scanned bio-
metric data to extract the salient information (feature
set) that is useful in distinguishing between different
users. During enrollment, the extracted feature set is
stored in a database as a template, which is generally
indexed by the user’s identity information. The tem-
plate database is usually considered as a component of
the complete IT system. The creation and maintenance
of the template database is handled by the security ad-
ministrator of the IT system. The matcher module is
usually an executable program, which accepts two bio-
metric feature sets (one from the template and the other
from the query) as inputs, and outputs a match score
indicating the similarity between the two sets. Finally,
the decision module makes the identity decision based
on the threshold set by the system administrator. Based on
the recognition results, the user is granted or refused
access to the ITapplication or service by the administrator .
From Fig . 1, it is clear that there are five main
vulnerable areas in a biometric system, where security
is of critical importance. These areas include (1) the
interface betw een the user and the biometric system,
Security Issues, System Design
S
1153
S
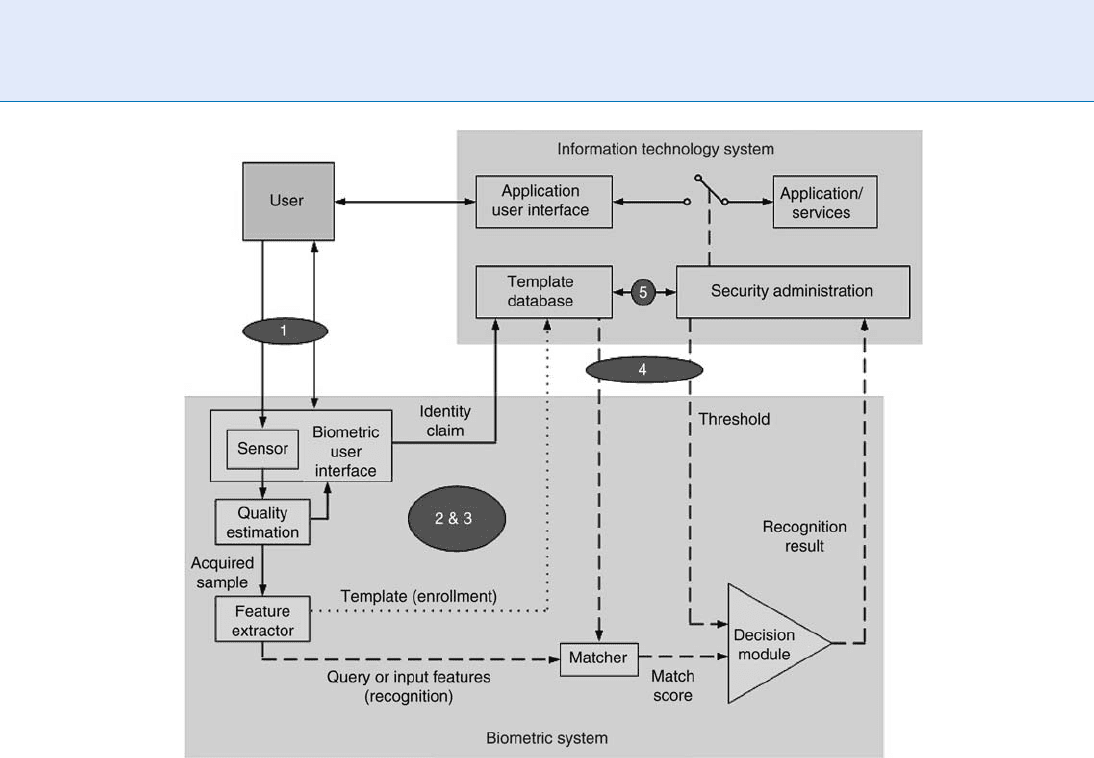
(2) the four modules of the bio metric system, (3) the
interconnection between the modules within the bio-
metric system, (4) the interface between the biometric
system and the IT system, and (5) the administration of
the template database. The various threats and counter-
measures that need to be considered in the design of a
biometric system are presented in the subsequent sec-
tions. The threat agents (attackers) could either be insi-
ders (authorized users, operators or administrators) or
external adversaries. For insider threats, the cause for
the threat could be (1) unintentional (inadvertent)
error, (2) collusion between attackers, and (3) coercion
by external adversaries.
Threats at the Interface between
User and Biometric System
In general, any attempt by an attacker to break into
the system by presenting a biometric trait can be
considered as a threat at the user-biometric system
interface level. At this level, the following threats and
countermeasures are possible.
Casual impersonation: An impostor attempts to fool
the system by presenting his/her biometric trait and
impersonating as an authorized user. In this case,
the identity to be attacked is chosen randomly and
the impostor does not modify his/her own biomet-
ric identifiers in any way. The probability of success
in such an attack is measured by the false accept rate
(FAR) of the biometric system. Since this threat is
due to the
▶ intrinsic failure of the biometric sys-
tem and does not require any explicit effort by the
attacker, it is referred to as zero-effort attack. This
attack can be countered by selecting a very low
value of FAR and by restricting the number of
failure attempts allowed within a time-frame.
Targeted impersonation: Same as casual impersona-
tion, except that the impostor attacks a specific
Security Issues, System Design. Figure 1 General architecture of a biometric system. The major areas of vulnerability
are (1) user-biometric system interface, (2) biometric system modules, (3) interconnections between biometric
modules, (4) biometric system-IT system interface and (5) security administration.
1154
S
Security Issues, System Design

identity, which is known to be easier to imperson-
ate (also known as lambs [5]). This attack exploits
the fact that FAR is not uniform across all users.
The impostor may a lso target an identity whose
biometric characteristics are known to be similar
to his/her traits (also known as ‘‘Evil Twin’’ [6]).
The same countermeasures used against casual im-
personation may be employed to limit the success
of this attack.
Mimicry : The impostor may be able to modify his
biometric characteristics to match that of the iden-
tity under attacks. Examples of this attack include
changing one’s voice, forging a signature or mim-
icking a gait pattern. This threat is more common
in systems using behavioral biometric traits and
in unattended applications. Countering this attack
requires biometric systems that have low FAR
under skilled forgery.
Spoofing: This is the most common attack at user
interface level and it involves the presentation of
a spoof (fake or artificial) biometric trait (e.g.,
dummy finger, recorded voice, etc.). If the sensor
is unable to distinguish between fake and genuine
biometric traits, the adversary easily intrudes the
system under a false identity. This attack requires
knowledge of the biometric trait corresponding to
the identity to be attacked. This knowledge could
be obtained in one of the following three ways:
(1) directly colluding with or coercing an author-
ized user, (2) covert acquisition (e.g., lifting resid-
ual fingerprint impressions covertly from the
sensor or any surface touched by the authorized
user) and (3) stealing the biometric template from
a database and reverse engineering the template.
The solution to counter this threat is to incorporate
liveness detection capability in the biometric sen-
sor. A number of efforts have been made in devel-
oping hardware as well as software solutions that
are capable of performing liveness detection.
Presentation of poor image: This threat is mainly
applicable to screening applications, where the
attacker may attempt to hide his true identi ty by
presenting a poor imag e or noisy biometric sam-
ple that may not be matched to his/her template in
the database. However, it may also be applicable
in verification systems that employ a fall-back
mechanism to handle false rejects. In this scenario,
the impostor may attempt to bypass the biometric
system by providing noisy samples and exploit the
loopholes in the exception procedures. This attack
can be countered by configuring the biometric sys-
tem in such a way that the False Nonmatch Rate
(FNMR) or False Reject Rate (FRR) is very low.
Illegal enrollment: The impostor may enroll himself
into the system illegally (under a false identity) by
producing his biometric traits along with false cre-
dentials (e.g., fake passports, birth certificates, etc.).
It must be emphasized that the secure authentication
functionality provided by a biometric system is only
as good as the integrity of the enrollment process.
Threats at the Biometric System Modules
Though the sensor, feature extractor, matcher, and deci-
sion modules logically constitute a single unit (known as
the biometric system or device) within the IT system,
there is a variety of possibilities in the physical configu-
ration of these modules. For example, it is possible to
place all the four modules and the interfaces between
them on a single smart card (or more generally a secure
processor). In such systems, known as system-on-card
technology, sensor, feature extractor, matcher, and even
the templates reside on the card or the chip [7]. The
advantage of this technology is that the biometric in-
formation never leaves the card and only the recogni-
tion results are transmitted to the IT system. It is much
easier to design a trusted or secure biometric system
based on the system-on-card technology. On the other
extreme, consider a large Automated Fingerprint Iden-
tification System (AFIS) used in forensic applications.
In the AFIS scenario, the modules of the biometric
system are typically distributed across different physi-
cal locations (sensor may be at the crime scene, feature
extractor and decision module may be at the regional
investigation office, matcher and database at a national
center, etc.). Other intermediate configurations where
the sensor and feature extractor may reside together at a
remote location, while the matcher and database reside
on the server (or a smart card (match- on-card technol-
ogy)) are also possible. Despite the wide ranging physi-
cal configurations, four common attacks can be
mounted on the biometric system modules.
Bypass: The attacker may completely bypass one or
more modules of the biometric system . For in-
stance, the attacker can bypass the sensor and pres-
ent the biometric image directly to the feature
extractor. In cryptography, this threat is known as
Security Issues, System Design
S
1155
S

‘‘man-in-the middle’’ attack. One method to over-
come this threat is to employ a trusted biometric
system. A trusted biometric system is one in which
the different modules are bound together physically
and/or logically using
▶ mutual authentication be-
tween the modu les.
Modification: The executable program at a module
can be modified such that it always outputs the
values desired by the adversary. Such attacks are
also known as Trojan-horse attacks. Secure code
execution practices or specialized tamper-resistant
hardware that can enforce secure execution of soft-
ware can be used to avoid modification of the
module functionalities.
Exploitation of vulnerabilities: The attacker may
identify and exploit the loopholes in the implemen-
tation of the biometric algorithms or insecure con-
figuration to circumvent the biometric system.
As an example, consider a matching module in
which a specific input value, say X
0
, is not handled
appropriately and whenever X
0
is input to the
matcher, it always outputs a match (accept) deci-
sion. This vulnerability mig ht not affect the normal
functioning of the system because the probability
of X
0
being generated from a real-biometric data
may be negligible. However, an adversary can ex-
ploit this loophole to easily breach the security
without being detected. Note that the attacker
may need to bypass one or more modules in the
biometric system to exploit such vulnerabilities.
Sabotage: Finally, an adversary can physically tam-
per with or damage the infrastructure of a biomet-
ric system thereby preventing legitimate users from
accessing the application. Examples of sabotage
include disabling the power supply, damaging the
sensor surface or introducing excessive noise (in-
terference) that prevents the normal operation of
the system. Apart from causing denial of service to
authorized users, this kind of attack may also be
used to gain unauthorized access by exploiting the
vulnerabilities in the fall-back system.
Threats at the Interconne ctions between
Biometric Modules
The following vulnerabilities are possible when an ad-
versary gains control of the communication interfaces
between different modules of the biometric system.
Juels et al. [8] outlined the security and privacy issues
introduced by insecure communication channels in an
e-passport application that uses biometric recognition.
Replay attacks: If the channels between the biometric
modules are not secured physically or cryptographi-
cally, an adversary may intercept the data being trans-
ferred and replay it at a later time. The raw biometric
data or extracted features can be intercepted and
replayed. Replay attacks are possible even if the data
are encrypted. A countermeasure against this attack
is to use time-stamps or a challenge/response mech-
anism. Mutual authentication between the modules
and use of one-time session keys during every trans-
action could also mitigate replay attacks.
Hill Climbing attacks: Hill climbing attacks are
possible when the adversary has the ability to inject
raw biometric data or features directly into the
channel by bypassing the sensor or feature extrac-
tor (or through Trojan-horse attacks) . This attack
also requires some feedback from the biometric
system such as the match score [9]. In this scenario,
an artificially generated biometric sample or fea-
ture set is first introduced into the system and the
response (match score) is noted. The adversary
then perturbs the initial sample or feature set, sub-
mits it to the system and records the new match
score. If the match score in the second iteration is
higher than the first one, the changes are retained;
else, they are discarded. This process is iterated
several times until the match score crosses the
threshold set by the system administrator. In each
iteration where the match score is higher than
before, the artificially generated sample or feature
set becomes more similar to the template that is
being targeted. Restricting the number of failure
attempts allowed within a time-frame, increasing
the granularity of the match score, the use of
trusted biometric systems, etc. are some techniques
that can counter the threat of a hill-climbing attack.
Sabotage: The adversary can also sabotage the bio-
metric system by physically damaging the commu-
nication interfaces between the modules or by place
an interfering source near the communication
channel (e.g., a jammer to obstruct a wireless inter-
face). This may cause the denial of ser vice or lead to
unauthorized access attempts that try to exploit
vulnerabilities in the fall-back system.
1156
S
Security Issues, System Design

Threats at the Interface between
Biometric and IT systems
The communication channels at the interface between
the biometric system and the ITsystem carry four main
types of information, namely, the user identi ty infor-
mation, the biometric template, the system parameters
such as threshold, and the recognition results. Since all
the four pieces of information are of vital importance,
careful attention needs to be given to secure these links.
As in the interfaces between the modules, the key
threat is the interception and/or modification of data.
For instance, if the recognition results can be inter-
cepted and modified by the adversary, the complete
biometric system gets bypassed and the security
provided by the biometric system is rendered useless.
The countermeasures against this type of threat are
essentially the same as those used to secure the links
between the biometric modules.
Administration Threats
Administration attack refers to all vulnerabilities intro-
duced due to improper administration of the biometric
system, which may occur due to the following causes.
Insider threat: Auth orized users or system adminis-
trators may ex cee d their authority either inadvertently
or w ith malicious intent. Steps such as security
awareness training and audit trails can minimize
the threats posed by the insider attacks. However, it
is important to ensure the integrity of the audit logs
themselves, because any unauthorized tampering of
audit logs can lead to undetected insider attacks.
Template Modification: The template database could
be hacked or modified by an adversary to gain unau-
thorized access. This scenario is also applicable to the
case where the template is stored on a smart-card.
The card may be forged to contain the biometric
template of the impostor. Template protection
approaches such as encryption and
▶ biometric
cryptosystems can be used to prevent this attack.
Leakage of Biometric Information: Leakage of the
biometric template information may l ead to
the following consequences: (1) A physical spoof
can be created from the template (see [10, 11]) to
gain unauthorized access to the system (as well as
other systems that use the same biometric trait), (2)
the stolen template can be replayed to the matcher
to gain unauthorized access, and (3) the templates
can be used for cross-matching across different
databases to covertly track a person without his/
her consent. Template protection schemes like
encryption, feature transformation, and biometric
cryptosystems can be used to mitigate this threat.
Exception processing: User authentication systems
are usually riddled with exception processing pro-
cedures (or fall-back systems) to avoid inconve-
nience to genuine users. For example, when a user
suffers an injury to his finger, he may still be granted
access based on alternative authentication mechan-
isms without undergoing fingerprint recognition.
Such exception processing procedures can be easily
abused to circumvent a biometric system.
Common Criteria Framework
The Common Criteria (CC) for Information Tech-
nology Security Evaluation is an international stan-
dard (ISO/IEC 15408) for evaluating the security of
information technology systems [12]. This standard
provides the ability to compare independent security
evaluations of a product or system. The IT product
or system whose security properties are to be analyzed
is called the Target of Evaluation (ToE). The CC frame-
work classifies the IT security requirements into secu-
rity functionalities and assurance levels. It also defines
two ways of expressing these requirements, namely,
Protection Profile (PP) and Security Target (ST).
The protection profile (PP) can be used by consumers
and system designers to list the various threats and
vulnerabilities faced by the ToE and the desired security
features that will meet their needs. The security target
(ST) precisely specifies the security capabilities of the
ToE and the ST is used by the evaluators as the basis for
the security evaluation. The ST may also claim compli-
ance with a protection profile. The CC framework can
be used to systematically evaluate the security of a
biometric system. For example, biometric protection
profiles have been introduced in the U.K., U.S. and
Germany [6, 13, 14].
Summary
A biometric system is one of the key components in an
IT security system that provides the secure authen tica-
tion functionality. However, the biometric system itself
Security Issues, System Design
S
1157
S

is vulnerable to a number of security threats and a
systematic analysis of these threats is essential when
designing a biometric system. In this article, a high-
level categorization of the various vulnerabilities of a
biometric system was presented and countermeasures
that have been proposed to address these threats were
discussed. Public acceptance of biometric recognition
technolog y will depend on the ability of system
designers to demonstrate that these systems are robust,
have low error rates, and are tamper-proof. This can be
achieved by evaluating the biometric system security
using IT security standards such as the Common
Criteria framework.
Related Entries
▶ Biometric Matcher
▶ Biometric Vulnerabilities, Overview
▶ Feature Extraction
▶ Security and Liveness: Overview
▶ Sensor
▶ Template Security
References
1. Coordination of Federal Information Policy – Information Se-
curity. In: United States Code, 3532, chap. 35. Available at http://
www.law.cornell.edu/uscode/html/uscode44/usc_sec_44_00003
532——000-.html
2. Wirtz, B.: Biometric System Security – Part 1. Biometric Tech-
nology Today pp. 6–8 (2003)
3. Wirtz, B.: Biometric System Security – Part 2. Biometric Tech-
nology Today pp. 8–9 (2003)
4. Soutar, C.: Automatic Fingerprint Recognition Systems.
Springer, Berlin (2004)
5. Doddington, G., Liggett, W., Martin, A., Przybocki, M.,
Reynolds, D.: Sheep, Goats, Lambs and Wolves: A Statistical Anal-
ysis of Speaker Performance in the NIST 1998 Speaker Recognition
Evaluation. In: Proceedings of the Fifth International Conference
on Spoken Language Processing (ICSLP). Sydney, Australia (1998)
6. UK Government Biometrics Working Group: Biometric Device
Protection Profile (BDPP). Technical Report Draft Issue 0.82 (2001)
7. Jain, A.K., Pankanti, S.: A Touch of Money. IEEE Spectrum 3(7),
22–27 (2006)
8. Juels, A., Molnar, D., Wagner, D.: Security and Privacy Issues in
E-passports. In: Proceedings of First International Conference
on Security and Privacy for Emerging Areas in Communications
Networks, pp. 74–88. Athens, Greece (2005)
9. Adler, A.: Sample images can be independently restored from face
recognition templates. In: Proceedings of Canadian Conference
on Electrical and Computer Engineering, vol. 2, pp. 1163–1166.
Montreal, Canada (2003)
10. Ross, A., Shah, J., Jain, A.K.: From Templates to Images: Recon-
structing Fingerprints From Minutiae Points. IEEE Trans. Pat-
tern Analy. Mach. Intell. 29(4), 544–560 (2007)
11. Cappelli, R., Lumini, A., Maio, D., Maltoni, D.: Fingerprint
Image Reconstruction From Standard Templates. IEEE Trans.
Pattern Analy. Mach. Intell. 29(9), 1489–1503 (2007)
12. Evaluation Criteria for IT Security. In: ISO/IEC 15408-1. Inter-
national Standards Organization (2005)
13. Information Assurance Directorate: U.S. Government Biometric
Verification Mode Protection Profile for Basic Robustness Envir-
onments. Technical Report 1.1 (2007)
14. Security Evaluation of Biometrics. In: ISO/IEC CD 19792. Inter-
national Standards Organization (2008)
Security Threat Assessment
Security threat assessment is the use of available infor-
mation, including biographic and biometric data, to
perform of a series of investigations to determine
whether an individual poses (or is suspected of posing)
a threat to transportation or national security. It may
include name-based checks, criminal history back-
ground checks, and watch list checks.
▶ Registered Traveler
Segmentation of Iris Images from
Noncooperative Subjects
▶ Segmentation of Off-Axis Iris Images
Segmentation of Off-Axis Iris Images
LAUREN R. KENNELL,RYA N N. RAKVIC,
R
ANDY P. B RO US SA RD
The John Hopkins University, Applied Physics
Laboratory, Maryland, USA
Synonyms
Off-angle or Nonorthogonal segmentation; Segmenta-
tion of iris imag es from noncooperative subjects.
1158
S
Security Threat Assessment

Definition
Iris image segmentation is the process of finding the iris
region within an image of the subject’s eye area: dis-
tinguishing the iris ring from the sclera, eyelids, and
other regions, and also detecting obscurations caused
by eyelashes and specular reflection. Off-axis images
are those captured when the subject is not looking in
the direction of the camera.
Introduction
Iris recognition systems typically require that users
position themselves a few inches away from the
camera and look into the camera for a few seconds,
known as the ‘‘stop and stare.’’ More forgiv ing and
user-friendly interfaces in commercial systems may
facilitate the introduction of iris systems into a wider
range of applications. Tak ing it a step further, elim-
inating the user cooperation requirement entirely
would enable deployment of systems in which the
subject may not be aware of the image capture, such
as in a surveillance situation. The less user coopera-
tion that is expected, the more the systems depend
on recognition from off-axis images, namely those
taken when the subject is not looking in the direction
of the camera, such as in Fig. 1. The topic of this
chapter is the segmentation of off-axis iris images:
the task of determining which pixels from the captured
image belong to the iris, as opposed to the sclera, the
eyelids, eyelashes, etc.
Segmentation methods can incorporate certain
parameters, regarding the approximate size of the iris
as imaged through a given camera such as the approx-
imate pixel diameter. In addition, segmentation often
exploits the basic shape and proportions of a typical
eye, but to different degrees and in different ways.
Often the pupil (inner) boundary and limbic (outer)
boundary are conceptualized as nearly-concentric circles
(alternatively, the pupil mass may be thought of as a
disk and the limbic boundary as a circle), so one often
proceeds by searching for these shapes, for instance
with circular edge detection in the appropriate diam-
eter range, and then refining the search as needed
to account for irregularly shaped boundaries. Gener-
ally speaking, this is still true in the off-axis case, except
that the circular model must now be more flexible,
replaced with something like an oriented ellipse ,
to account for sideward and/or up- or downward
gaze (yaw and pitch). An off-axis segmentation pro-
cedure is hopefully rather robust, because reduced
user cooperation may result in lower image quality,
such as from blur, inconsistent illumination and sha-
dows, significant eyelid and eyelash obscuration, and
specular reflections intersecting the pupil or limbic
boundary.
Shape models may enhance robustness and save
some time by narrowing down what to look for, and
they are useful for other reasons too. A shape model of
the inner and/or outer boundary, such as an ellipse
with a certain center, axis lengths, and orienta-
tion, provides a means to determine the gaze angle,
e.g., using eccentricity-based computations, from
which the eye image may be projected to orthographic
(on-axis) view before feature encoding. Whatever
the assumed shape of the iris ring, in many on-axis
recognition algorithms the iris boundaries are often
identified as closed curves (projecting behind any
occluding eyelids), because this description of the
boundaries is used to ‘‘cut and unwrap’’ the iris ring
into a rectangle prior to feature extraction.
What follows is a summary of off-axis segmen-
tation techniques, many of them adapted from or
inspired by previous on-axis methods – clever con-
structions and combinations of morphology, contours,
filters, snakes, splines, trigonometry, transforms, and
plain brute force.
Segmentation of Off-Axis Iris Images. Figure 1 Off-axis
iris image from [1], Fig. 9a, p. 586. [Copyright U.S Naval
Academy]
Segmentation of Off-Axis Iris Images
S
1159
S
