Li S.Z., Jain A.K. (eds.) Encyclopedia of Biometrics
Подождите немного. Документ загружается.

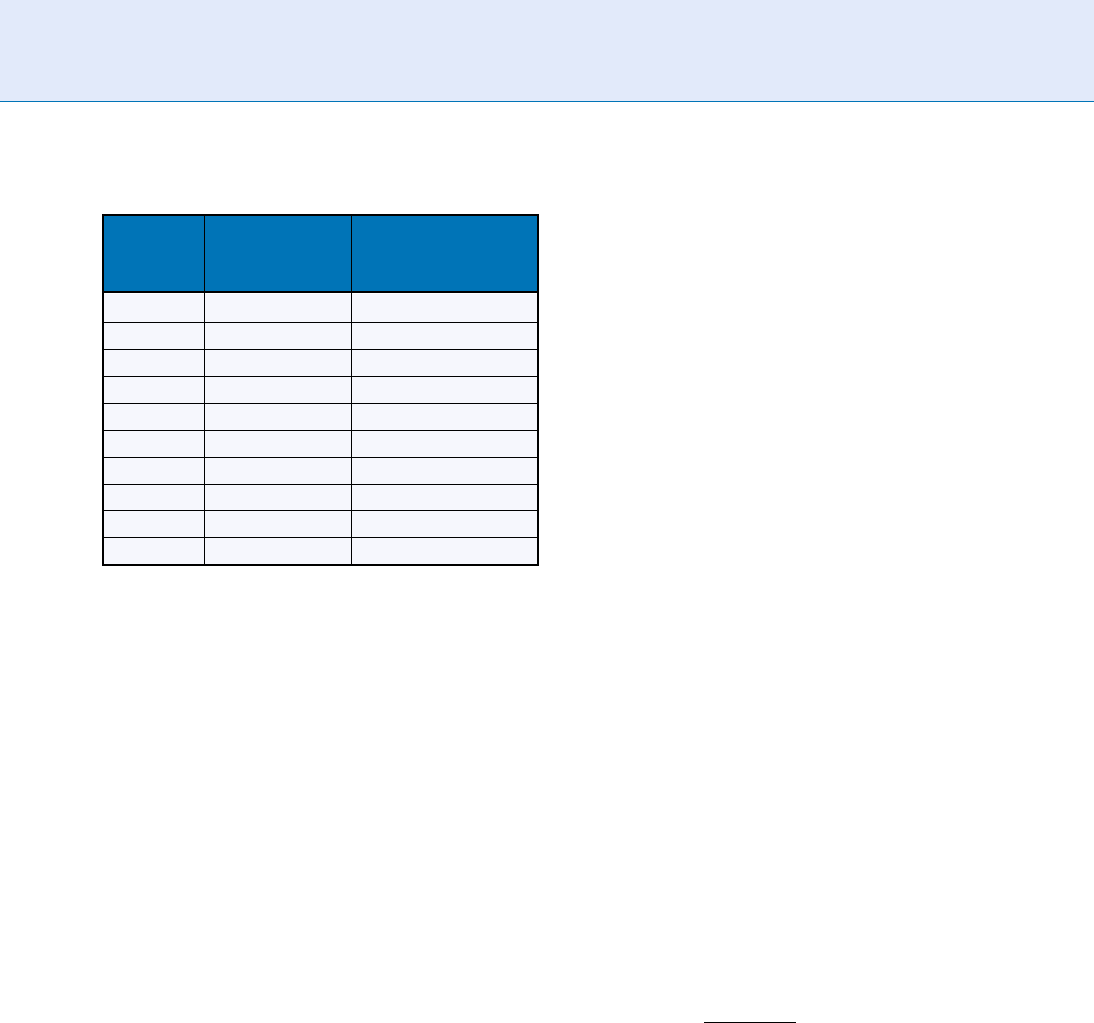
False Match Rate, such a s 0.001, which was the basis
for NIST ICE (Iris Challenge Evaluation 2006) report-
ing. The ICE iris database contained many very diffi-
cult and corrupted images, often in poor focus, and
with much eyelid occlusion, with motion blur, raster
shear, and sometimes with the iris par tly outside
of the image frame. As ROC curves require False
Matches, NIST used a much more liberal decision
criterion than is used in any actual deployments of
iris recognition. As seen in Figure 4, using liberal
thresholds that generate False Match Rates (FMR)
in the range of 0.001–0.00001, score normalization
adversely impacts on the ROC curve by increasing
the False nonMatch Rate (FnMR) . The Equal Error
Rate (where FnMR = FMR, indicated by the solid
squares) is about 0.001 without score normalization,
but 0.002 with the normalization. Similarly at other
nominal points of interest in this region of the ROC
curve, as tabulated within Figure 4, the cost of score
normalization is roughly a doubling in the FnMR,
because marginal valid matches are rejected due
to the penalty on fewer bits having been available
for compariso n. In conclusion, whereas Table 1, and
Figures 2 and 3 document the important benefit of
score normalization when operating with very large
databases that require several orders of magnitude
higher confidence against False Matches, Figure 4
shows that in scenarios which are much less demand-
ing for FMR, the FnMR is noticeably penalized by
score normalization, and so the ROC curve suffers.
Adapting Decision Thresholds to the Size
of a Search Database
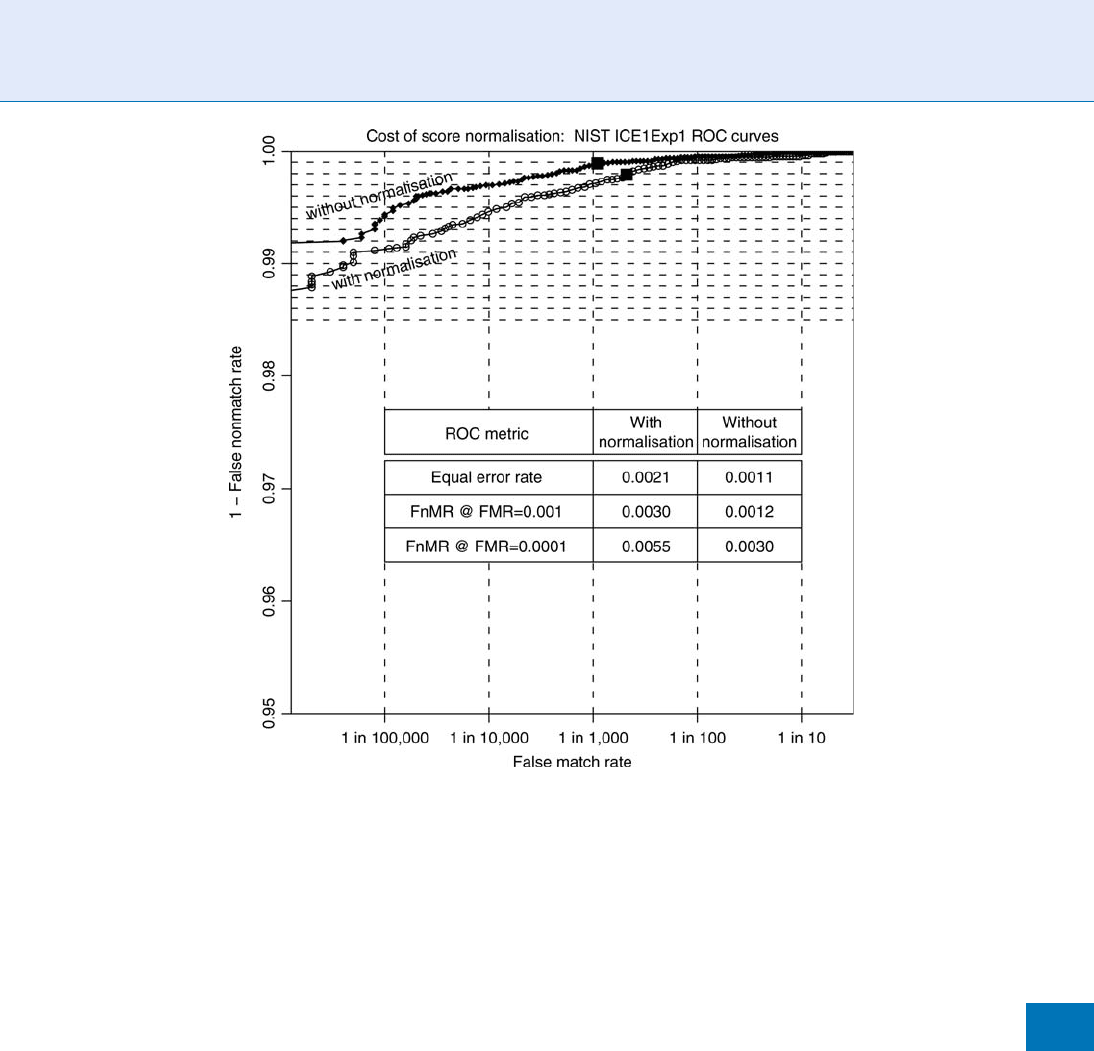
Using the SQRT normalization rule, Figure 5 presents
a histogram of all 200 billion cross-compariso n simi-
larity scores HD
norm
among the 632,500 different irises
in the Middle Eastern database [3]. The vast majority
of these IrisCodes from different eyes disagreed in
roughly 50% of their bits as expected, since the bits
are equiprobable and uncorrelated between different
eyes [2, 1]. Very few pairings of IrisCodes could dis-
agree in fewer than 35% or more than 65% of their
bits, as is ev ident from the distribution. The form of
this distribution needs to be understood, assumi ng
that it is typical and predictive of any other database,
in order to understand how to devise decision rules
that compensate for the scale of a search. Without this
form of score normalization by the scale of the search,
or an adaptive decision threshold rule, False Matches
would occur simply because large databases provide so
many more opportunities for them.
The solid curve that fits the distribution data very
closely in Figure 5 is a binomial probability density
function. This theoretical form was chose n because
comparisons between bits from different IrisCodes
are Bernoulli trials, or conceptually ‘‘coin tosses,’’ and
Bernoulli trials generate binomial distributions. If one
tossed a coin whose probability of ‘‘heads’’ is p in a
series of n independent tosses and counted the number
m of ‘‘heads’’ outcomes, and if one tallied this fraction
x ¼ m ∕n in many such repeated runs of n tosses, then
the expected distribution of x would be as per the solid
curve in Figure 5:
f ðxÞ¼
n!
m!ðn mÞ!
p
m
ð1 pÞ
ðnmÞ
ð3Þ
The analogy between tossing coins and comparing
bits between different IrisCodes is deep but imperfect,
because any given IrisCode has internal correlations
arising from iris features, especially in the radial direc-
tion [2]. Further correlations are introduced because
the patterns are encoded using 2D Gabor wavelet fil-
ters, whose lowpass aspect introduces correlations in
amplitude, and whose bandpass aspect introduces cor-
relations in phase, both of which linger to an extent
that is inversely propor tional to the filter bandwidth.
The effect of these correlations is to reduce the value of
the distribution parameter n to a number significantly
smaller than the number of bits that are actually
Score Normalization Rules in Iris Recognition. Table 2
Effect of score normalisation on the match quality required
with various amounts of iris visibility
Number
of bits
compared
Approximate
percent of iris
visible (%)
Maximum acceptable
fraction of bits
disagreeing
200 17 0.13
300 26 0.19
400 35 0.23
500 43 0.26
600 52 0.28
700 61 0.30
800 69 0.31
911 79 0.32
1,000 87 0.33
1,152 100 0.34
1140
S
Score Normalization Rules in Iris Recognition
compared between two IrisCode s; n becomes the num-
ber of effectively independent bit comparisons. The
value of p is very close to 0.5 (empirically 0.499 for
this database), because the states of each bit are equi-
probable a prior i, and so any pair of bits from different
IrisCodes is equally likely to agree or disagree.
The binomial functional form that describes so
well the distribution of normalized similarity scores
for comparisons between different iris patterns is key
to the robustness of these algorith ms in large-scale
search applications. The tails of the binomial attenuate
extremely rapid, because of the dominating central
tendency caused by the factorial terms in (3). Rapidly
attenuating tails are critical for a biometric system to
survive the vast numbers of opportunities to make
False Matches without actually making any, when ap-
plied in an ‘‘all-against-all’’ mode of searching for any
matching or multiple identities, as is contemplated in
some national ID projects. The requirements of bio-
metric operation in ‘‘identification’’ mode by exhaus-
tively searching a large database are vastly more
demanding than operating merely in one-to-one ‘‘ver-
ification’’ mode (in which an identity must first be
explicitly asserted, which is then verified in a yes/no
decision by comparison against just the single nomi-
nated template).
If P
1
is the False Match probability for single one-
to-one verification trials, then (1P
1
) is the probabili-
ty of not making a False Match in single comparisons.
The likelihood of successfully avoiding this in each of
N independent attempts is therefore (1P
1
)
N
, and
so P
N
, the probability of making at least one False
Match when searching a database containing N differ-
ent patterns is:
P
N
¼ 1 ð1 P
1
Þ
N
ð4Þ
Score Normalization Rules in Iris Recognition. Figure 4 Adverse impact of score normalisation in ROC regions where
high False Match Rates are tolerated (e.g., 0.00001 to 0.001 FMR). In these regions, the False nonMatch Rate is roughly
doubled as a result of score normalization.
Score Normalization Rules in Iris Recognition
S
1141
S
Observing the approximation that P
N
NP
1
for
small P
1
<<
1
N
<< 1, when searching a database of
size N an identifier needs to be roughly N times better
than a verifier to achieve comparable odds against
making False Matches. In effect, as the database
grows larger and larger, the probability of making
a False Match also grows almost in proportion.
Obviously the frequency of False Matches over time
also increases with the frequency of independent
searches that are conducted against the database. In
the Middle Eastern deployment [3] from which the
data of Figure 5 was taken, in which typically about
12,000 daily arriving passengers are each compared
with about a million stored IrisCodes, the total num-
ber of iris comparisons is about 12 billion per day. To
survive successfully so many opportunities to make
False Matches, the decision threshold policy must be
adaptive to both of these factors: the size of the database
and the frequency of searches throug h it (the quer y
rate). Fortunately, because of the underlying binomial
combinatorics, the algorithms with score normaliza-
tion generate extremely rapidly attenuatin g tails for the
HD
norm
distribution. The consequence is that extreme-
ly small adjustments to tighten the decision threshold
yield order-of-magnitude increases in robustness
against False Matches, and therefore in large-scale
search capability. But before specifying those rules, it
is first necesssary to understand the effect of the rota-
tion range over which repeated comparisons are done.
Factoring the Rotation Range into
Adaptive Decision Rules
Because cameras or heads may be tilted during iris
image acquisition, and indeed the eye itself can undergo
torsional (rotational) movements, it is necessary to
compare iris patterns at each of several relative orienta-
tions before deciding whether they match. Thus, when
searching a database of N enrollees and performing
each IrisCode comparison in each of k orientations,
the total number of comparisons effectively becomes
(k N). Since the best match (smallest score) found in
each set of k comparisons is the score that is retained,
the new distribution for comparisons between differ-
ent eyes is biased towards lower scores, has a lower
mean, and has asymmetric tails compared with the
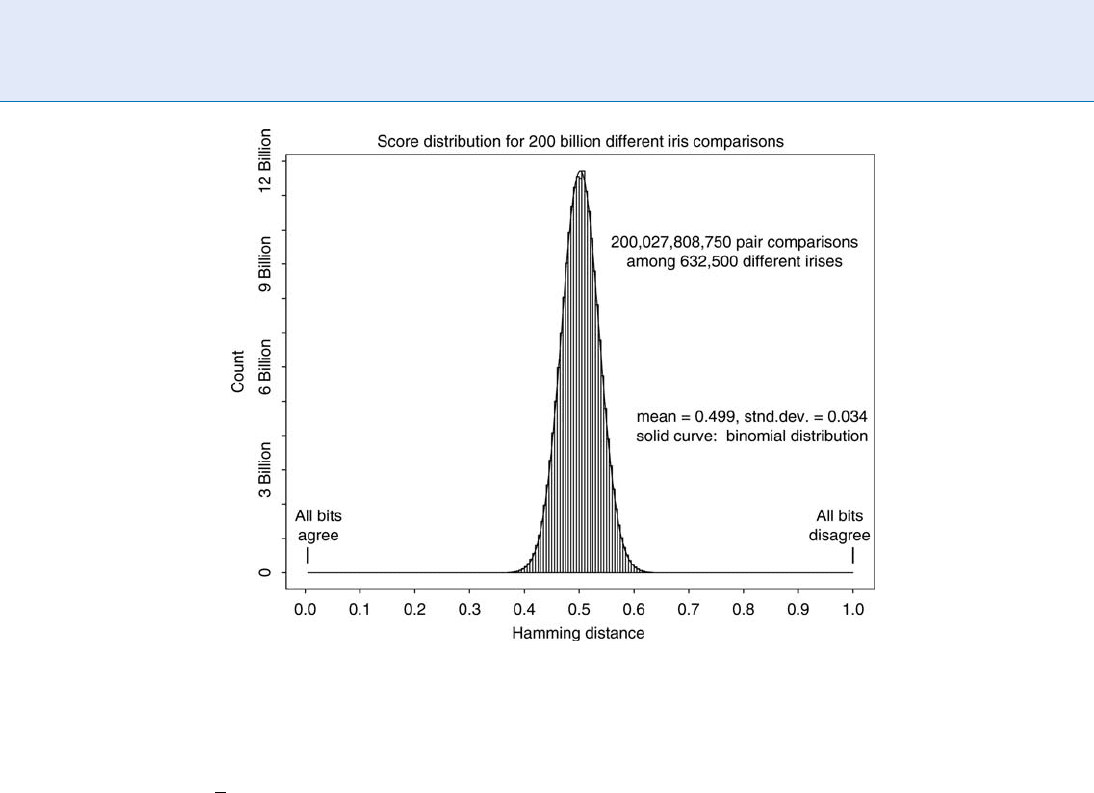
unrotated case seen in Figure 5. Using the same data-
base of IrisCodes but now performing all comparisons
Score Normalization Rules in Iris Recognition. Figure 5 Binomial distribution of normalised similarity scores in
200 billion comparisons between different eyes. Solid curve is (3).
1142
S
Score Normalization Rules in Iris Recognition
in each of k ¼ 7 orientations generates the new score
distribution seen in Figure 6.
The new distribution after k rotations of all Iris-
Codes in the search process still has a simple analytic
form that can be derived theoretically. Let f
0
(x) be the
raw density distribution obtained for the HD
norm
scores between different irises after comparing them
only in a single relative orientation; for example, f
0
(x)
might be the binomial defined in (3). Then F
0
(x), the
cumulative of f
0
(x) from 0 to x, becomes the probabil-
ity of getting a False Match in such a test when using
HD
norm
acceptance criterion x :
F
0
ðxÞ¼
Z
x
0
f
0
ðxÞdx ð5Þ
or, equivalently,
f
0
ðxÞ¼
d
dx
F
0
ðxÞð6Þ
Clearly, then, the probability of not making a False
Match when using decision criterion x is 1F
0
(x)
after a single test, and it is [1F
0
(x)]
k
after carrying
out k such tests independently at k different relative
orientations. It follows that the probability of a False
Match after a ‘‘best of k’’ test of agreement, when using
HD
norm
criterion x, regardless of the actual form of the
raw unrotated distribu tion f
0
(x), is:
F
k
ðxÞ¼1 1 F
0
ðxÞ½
k
ð7Þ
and the expected density f
k
(x) associated with this
cumulative is:
f
k
ðxÞ¼
d
dx
F
k
ðxÞ
¼ kf
0
ðxÞ 1 F
0
ðxÞ½
k1
ð8Þ
It is prudent to allow for at least a 20 deg orienta-
tion uncertainty, and so k ¼ 7 relative rotations in
2.81deg intervals were performed when arriving at
each best comparison HD
norm
score plotted in the
Figure 6 distribution. As expression (8) in the deriva-
tion shown earlier for postrotation probability density
Score Normalization Rules in Iris Recognition. Figure 6 Distribution of normalised similarity scores from the same set
of 200 billion iris comparison plotted in Figure 5, but now keeping only the best match after k ¼ 7 relative rotations to
compensate for unknown degrees of tilt in image acquisition. Solid curve is the f
k
(x) density function in (8), using the
binomial (3) as the f
0
(x) density prior to rotations.
Score Normalization Rules in Iris Recognition
S
1143
S
indicates, this means that the left tail of the distribu-
tion in Figure 6 is essentially k ¼ 7 times higher than
the one in Figure 5. The new functional form (8)
derived gives an excellent fit to this new distribution,
as shown by the solid curve that closely matches the
Figure 6 data.
The cumulatives (up to various thresholds) under
the left tail of the distribution of normalized similarity
scores for different irises compared at k ¼ 7 relative tilts,
reveal the False Match Rates among the 200 billion iris
comparisons if the identification decision policy used
each such threshold. These FMR rates are provided in
Table 3. Although the smallest observed match was
around 0.26, the Table has been extended down to 0.22
using the theoretical cumulative (7) of the extreme
value distribution (8) of multiple samples from the
binomial (3) plotted as the solid curve in Figure 6,
in order to extrapolate the theoretically expected
False Match Rates for such decision policies. These
False Match Rates, whether empirical or theoretical,
also serve as confidence levels that can be associated
with a given quality of sample using the score normali-
zation rule (2). In this analysis, only a single eye
is presumed to be presented. Under the assumption
of independence between right and left eye IrisCodes,
which is strongly supported by the available data
(see Figure 6 of [2]), the confidence levels in Table 3
could be multiplied together for matches obtained
with both eyes.
Now it is finally possible to state a general rule for
adaptively selecting a decision criterion threshold on
HD
norm
normalized similarity scores, given the
empirical cumulatives shown in Table 3 under the dis-
tribution of postrotation scores plotted in Figure 6.
If one is performing iris identifications by exhaustive
search through an enrolled database of size N, using
k ¼ 7 relative rotations for every comparison and
normalizing raw Hamming Distance scores by the
amount of available data as per (2), then the recom-
mended strategy is this:
Calculate the total number of iris comparisons that
will be performed in a given period of time, i.e., the size N
of the enrolled database times the number of queries
against it during that time. Decide the risk tolerance for
False Matches during such a period of time, and find the
corresponding entry in the second column of Table 3.
Then the first column gives the recommended decision
threshold on HD
norm
scores.
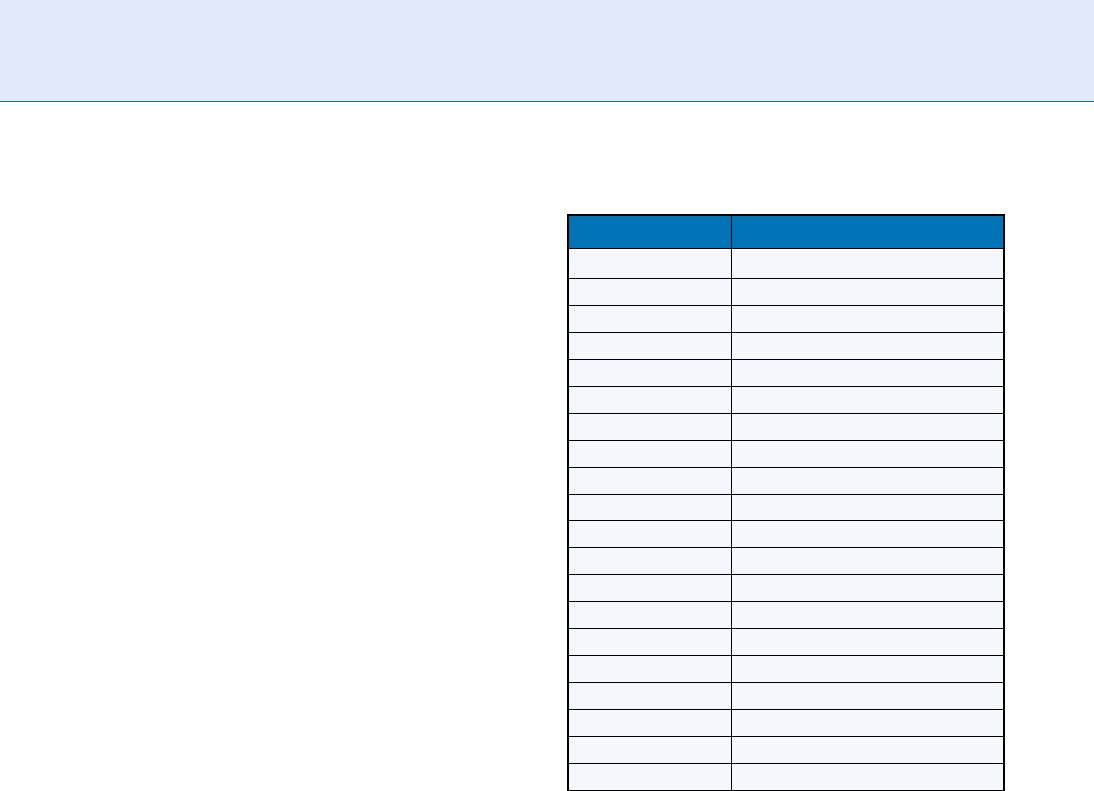
Example: If every month 100,0 00 passengers are
each compared to 1 million enrolled IrisCodes by
exhaustive search, generating 10
11
comparisons per
month, and no more than one False Match can be
tolerated per month, then Table 3 indicate s that the
recommended single-eye decision criterion to use
would be around 0.265 for HD
norm
similarit y scores.
Related Entries
▶ Iris Encoding and Recognition using Gabor Wavelets
References
1. Daugman, J.G.: The importance of being random: Statistical
principles of iris recognition. Pattern Recognit. 36, 279–291
(2003)
2. Daugman, J.G.: How iris recognition works. IEEE Trans. Circuits
Syst. Video Technol. 14, 21–30 (2004)
Score Normalization Rules in Iris Recognition. Table 3
False match rates with HD
norm
score normalisation:
dependence on criterion (200 Billion cross comparisons)
HD Criterion Observed False Match Rate
0.220 0 (theor: 1 in 5 10
15
)
0.225 0 (theor: 1 in 1 10
15
)
0.230 0 (theor: 1 in 3 10
14
)
0.235 0 (theor: 1 in 9 10
13
)
0.240 0 (theor: 1 in 3 10
13
)
0.245 0 (theor: 1 in 8 10
12
)
0.250 0 (theor: 1 in 2 10
12
)
0.255 0 (theor: 1 in 7 10
11
)
0.262 1 in 200 billion
0.267 1 in 50 billion
0.272 1 in 13 billion
0.277 1 in 2.7 billion
0.282 1 in 284 million
0.287 1 in 96 million
0.292 1 in 40 million
0.297 1 in 18 million
0.302 1 in 8 million
0.307 1 in 4 million
0.312 1 in 2 million
0.317 1 in 1 million
1144
S
Score Normalization Rules in Iris Recognition
3. Daugman, J.G.: Probing the uniqueness and randomness of
IrisCodes: Results from 200 billion iris pair comparisons. Proc.
IEEE 94(11), 1927–1935 (2006)
4. Daugman, J.G.: New methods in iris recognition. IEEE Trans.
Syst. Man Cybern. 37 , 1167–1175 (2007)
Sealed Local Biometric Identity
Verification Systems
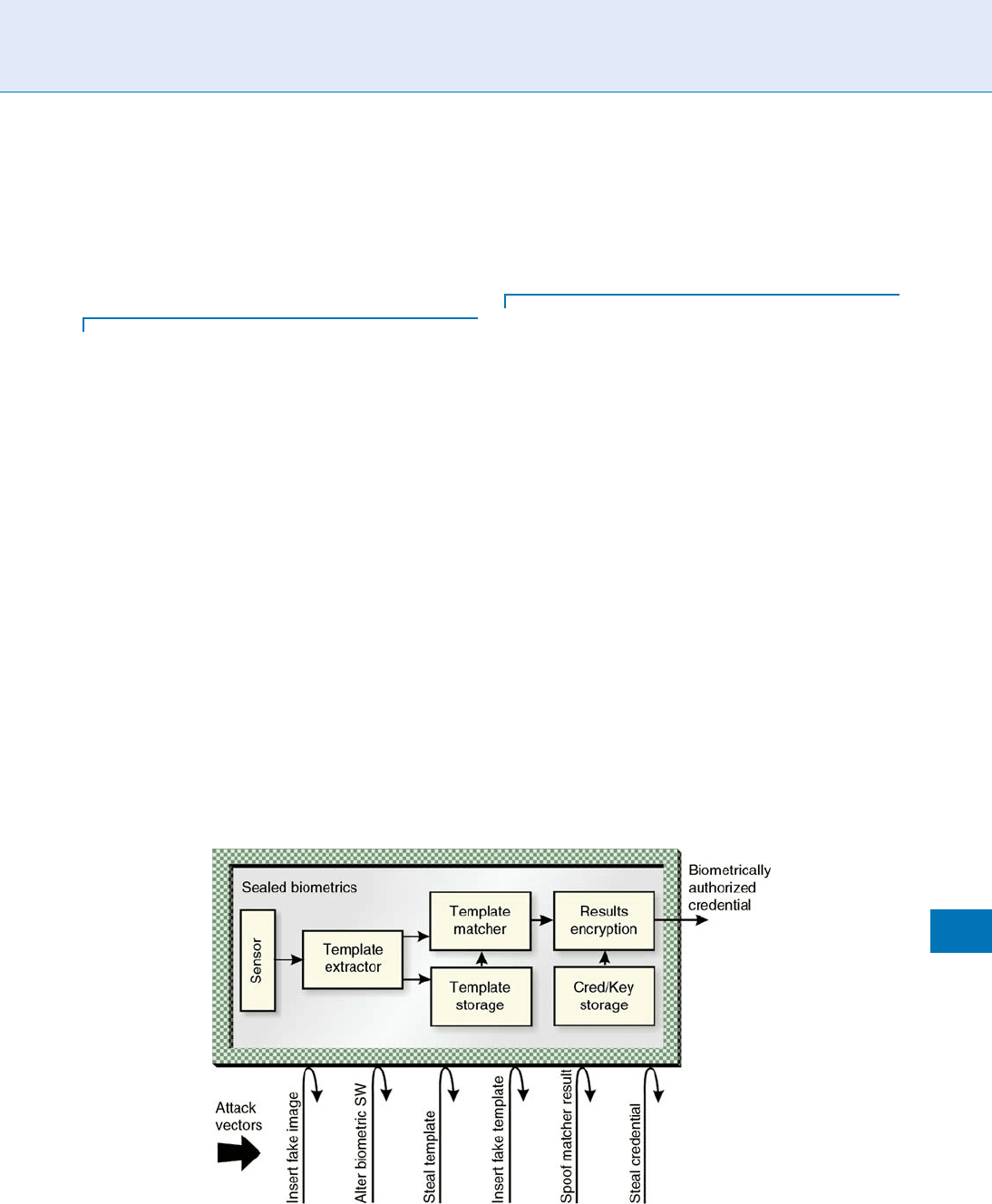
A sealed local biometric identity verification system is
a strong example of a trusted biometric identity verifi-
cation client. Sealed biometric systems are built around
the concept that the entire biometric acquisition and
matching process is ‘‘sealed’’ within a demonstrably
secure environment (see the following figure). No bio-
metric data can ever enter the system except via the
integrated biometric sensor, and no biometric data
ever leaves the system, period. In fact there is no way
to externally access the biometric data at all. The sealed
system securely stores cryptographic credentials for
each entity that registers its need to verify the user’s
identity, and releases those credentials only when that
entity has cryptographically identified itself, and the
correct user has been biometrically verified to be
present.
Figure 1 illustrates the concept of a sealed local
biometric identi ty verification system.
▶ Biometric Sample Acquisition
Second Level Detail
This refers to the occurrence of fundamental events
within the general ridge flow which disturb the regu-
lar and parallel flow of ridges. These events can
manifest themselves as ending/starting ridges, diverg-
ing/merging ridges ( bifurcations), and dots and com-
binations of these events such as short ridges, eyes,
spur, and islands. Thes e events are also referred to
as Galton characteristics, points or major ridge path
deviations.
Minutiae reflect events in a persistent system of
papillary ridges that once developed to their final
form during gestation remain unchanged throughout
life.
Minutiae in the latent keep their basic properties
such as relative location, direction, and relations to
other points even under adverse condi tions (Fig . 1).
This differentiates finge rprints from other types of
forensic evidence. Minutiae and their formation in
Sealed Local Biometric Identity Verification Systems. Figure 1
Second Level Detail
S
1145
S

sequence are the backbone of fingerprint identifica-
tion. Additional features that are also referred to as
level two are incipient ridges, scars, and creases.
▶ Fingerprint Matching, Manual
Secure Biometric Token Operating
System
▶ Tamper-proof Operati ng System
Secure Biometrics
▶ Biometric and User Data, Binding of
Secure Element
Synonyms
Security processor; Secure token
Definition
A closed, tamper-resistant, well-trusted, and usually
certified embedded system with a very lightweight
microcontroller and some FLASH storage. Typical se-
cure elements are single-chip entities designed to
achieve a black box nature for maximum security.
Smart cards, SIM cards, and NFC controllers are the
most prevalent examples . Most secure elements inter-
act with a host using a wired or wireless communica-
tion channel, but may be standalone systems as well.
▶ Transportable Asset Protection
Secure Sketch
▶ Encryption, Biometric
Security and Liveness, Overview
ANDY ADLER
1
,STEPHANIE SCHUCKERS
2
1
Carleton University, Ottawa, ON, Canada
2
Clarkson University, Potsdam, NY, USA
Definition
The security of a biometric system may be understood
to be its resistance to active attacks. Such attacks
may be classified as Presentation attacks (spoofing),
in which the appearance of the biometric sample is
physically changed or replaced; Biometric processing
attacks, in which an understanding of the biometric
algorithm is used to cause incorrect processing and
decisions; Software and networking vulnerabilities
based on attacks against the computer and networks
on which the biometric sy stems run; and Social and
presentation attacks, in which the authorities using the
systems are fooled. This article presents an overview of
the techniques used for classifying and assessing these
threats. Additionally, newer biometric schemes, such as
cancelable biometrics and bio metric encryption, that
are designed to counter these security threats are
reviewed.
Introduction
Security must be defined in the context of an attacker.
However, biometric systems, even when not under
active attack, should always be assumed to operate in
an (at least somewhat) hostile environment – after all,
why should one test identity if all can be trusted? The
ability of a biometric system to stand up to ‘‘zero-
effort’’ attackers is measured by the false accept rate
(FAR). Such measures are not typically considered to
measure biometric security, but rather biometric per-
formance. This article gives a broad overview of the
1146
S
Secure Biometric Token Operating System

security and liveness issues in biometric systems where
biometric security is understood to be the resistance of
a system to attackers prepared to take active measures
to circumvent the system. This article considers four
broad types of active attack:
Presentation attacks (spoofing): The appearance of
the biometric sample is changed either physically
or by replacement with a fabricated sample. For
physical biometrics, attackers may then change
makeup, facial hair and glasses, or abrade and cut
fingerprints in order to avoid being recognized; to
attempt to be recognized as another person, a
spoofed fingerprint or false iris contact lens may
be constructed and placed over the corresponding
body part.
Biometric processing attacks: A detailed understand-
ing of the biometric algorithm is used to cause
incorrect processing and decisions. The possible
attacks depend on the details of the biometric
algorithm (
▶ Biometric vulnerabilities, Overview).
Some examples are enrolling specially crafted
noisy images that artificially lower thresholds; re-
generation of sample images from stored templates;
and
▶ side-channel attacks based on ‘‘leaked’’ sys-
tem information such as from match scores or
timing of processing.
Software and networking vulnerabilities: Since bio-
metric systems are implemented on server compu-
ters, they are vulnerable to all cryptographic, virus,
and other attacks, which plague modern computer
systems [1]. Examples are databases security, denial
of service (DoS) attacks, and overriding the bio-
metric decision with compromised software. These
issues are not covered in detail in this article, since
they are not unique to biometric system security.
Social and presentation attacks: Security systems de-
pend on a chain of trust. Links in this chain between
systems are especially vulnerable [2]. Presentation
attacks involve the use of fraudulent identity docu-
ments, which may be legitimately issued; social
attacks focus on convincing an operator to override
or allow fraudulent exceptions. This article points
out the importance of these issues like software
vulnerabilities, but does not cover them in detail.
This article gives an overview of the security issues
in biometric systems, including classifications, security
performance measures, liveness and antispoofing and
novel biometric protection schemes.
Biometric Security Classifications
Several authors have developed classification schemes,
which provide a taxonomy of biometric security chal-
lenges. Maltoni et al. [3], classify biometric system
vulnerabilities as follows:
Circumvention is an attack by which one gains
access to the protected resources by a technical
measure to subvert the biometric system. Such
an attack may subvert the underlying compu-
ter systems (overriding matcher decisions, or repla-
cing database templates) or may involve a replay
of valid data.
Covert acquisition (contamination) is the use of
biometric infor mation captured from legitimate
users to access a system. Examples are spoofing
via capture and playback of voice passwords and
lifting latent fingerprints to construct a mold. This
category can also be considered to cover regener-
ated biometric images (
▶ Template Security). For
example, a fingerprint image can be regenerated
from the template stored in a database (and these
data can be captured covertly [4]). Covert acquisi-
tion is worrisome for cross-application usage (eg.,
biometric records from a ticket for an amusement
park used to access bank accounts).
Collusion and Coercion are biometric system vul-
nerabilities from legitimate system users. The dis-
tinction is that, in collusion, the legitimate user is
willing (perhaps by bribe), while the coerced user is
not (through a physical threat or blackmail). Such
vulnerabilities bypass the computer security sys-
tem, since the biometric features are legitimate. It
may be possible to mitigate such threats by auto-
matically detecting the unusual pattern of activity.
Such attacks can be mounted from both adminis-
trator and user accounts on such a system; attacks
from user accounts would first need to perform a
privilege escalation attack [1].
Denial of Service (DoS) is an attack that prevents
legitimate use of the biometric system. This can
take the form of slowing or stopping the system
(via an overload of network requests) or by degrad-
ing performance. An example of the latter would be
enrolling many noisy samples that can make a
system automatically decrease its decision thresh-
old and thus increase the FAR. The goal of DoS is
often to force a fall back to another system (such as
Security and Liveness, Overview
S
1147
S

operator override) that can be more easily circum-
vented, but DoS may be used for extortion or
political reasons.
Repudiation is the case where the attacker denies
accessing the system. A corrupt user may deny her
actions by claiming that her biometric data were
‘‘stolen’’ (by covert acquisition or circumvention)
or that an illegitimate user was able to perform the
actions due to the biometric false accept. Interesting-
ly, biometric systems are often presented as a solu-
tion to the repudiation problem in the computer
security literature [1]. One approach to help prevent
repudiation would be to store presented images for
later forensic analysis. However, this need must be
balanced against user privacy concerns [ 5].
Another class of biometric vulnerabilities are those
faced by the system user, developed by Ratha et al. [6].
These issues impact on the user’s privacy and can lead
to identity theft or system compromise.
Biometrics is not secret: Technology is readily avail-
able to capture images of faces, fingerprints, irises
and make recordings of voice or signature – with-
out subject consent or knowledge [2, 7]. From this
perspective, biometrics is not secret. On the other
hand, from a cry ptography or privacy [5] perspec-
tive, biometric data are often considered to be
private and secret. This distinction is important,
as our understanding of computer and network
security is centered around the use of secret codes
and tokens [1]. For this reason, cry ptographic pro-
tocols that are not robust against disclosure of
biometric samples are flawed.
Biometrics cannot be revoked: A biometric feature
is permanently associated with an individual, and
a compromised biometric sample will compro-
mise all applications that use that biometric
feature. Such compromise may prevent a user
from re-enrolling [2]. Note, however, that this con-
cern implies that biometrics is secret, as opposed
to the previous consideration. On e proposed solu-
tion is Cancelable biometrics, although the vulnera-
bility of such systems is not well understood.
Biometric features have secondary uses: If an indi-
vidual uses the same biometric feature in multiple
applications, then the user can be tracked if the
organizations share data. Another aspect of this
problem is secondary use of ID cards. For example,
a driver’s license is designed with the requirements
to prove identity and driver certification to a police
officer, but it is used to prove age, name and even
citizenship. Similarly, biometric applications will
be designed with a narrow range of security con-
cerns, but may be used in very different threat
environments.
Biometric systems form part of larger security
systems and their risks and vulnerabilities must be
understood in the context of the l arger system require-
ments. An excellent review of the security of biometric
authentication systems is [7]. Each assurance level
from ‘‘passwords and PINs’’ to ‘‘Hard cr ypto token’’
is analyzed to determine which biometric devices are
suitable. Since biometric systems are complex and
represent many interconnected subsystems, there are
many potential points for attack. Vulnerabilities in
Biometric Systems are considered in the article
▶ Bio-
metric Vulnerabilities: Overview.
Liveness and Spoofing
Clearly, biometric systems are vulnerable to artificial
changes to the biometric features. Such changes can be
of two types: to avoid detection as an enrolled user or
watch list candidate and to masquerade as another
legitimate user. The former is easier and can sometimes
be as simple as using glasses, makeup, or abrasions and
cuts to the finger. Masquerading or spoofing attempts
to gain unauthorized access at the biometric sensor
with artificial biometric features of authorized users,
called ‘‘spoofs.’’ This is widely publicized for finger-
print where it is possible to spoof a variety of fin-
gerprint sensors through relatively simple techniques
using casts of a finger with molds made of materials,
including silicon, Play-Doh, clay, and gelatin (gummy
finger). Such spoof molds can be scanned and verified
when compared with a live enrolled finger [8–11].
Masquerade is also possible in the scenario of dismem-
bered fingers; cadaver fingers can be scanned and ver-
ified against enrolled fingers [9]. It is also possible to
spoof other common biometric modalities: for iris and
face, using pictures or high resolution video, for iris
with contact lenses, with voice with recordings [8, 11].
There are several approaches to increase the diffi-
culty of spoofing: multiple biometric features, liveness,
and the use of biometrics in combination with a
1148
S
Security and Liveness, Overview

challenge response, passwords, tokens, smart cards.
The goal of liveness testing is to determine if the
biometric feature being captured is an actual measure-
ment from the authorized, live person, who is present
at the time of capture. Typically, liveness is a secondary
measure after biometric authentication, which must be
met in order to achieve a positive response. Liveness
and antispoofing methods are covered in detail in the
following summaries [12–14]. The need for protec-
tions from spoofing may be assessed on an application
basis, although there is a need to address the spoofing
vulnerability throughout the industry, as the reputa-
tion of biometric systems as a securit y measure must
be considered. Liveness detection adds an additional
layer of security that also can increase the users trust in
biometric technology.
Characteristics of Liveness Approaches: The follow-
ing characteristics for evaluating biometric systems
need to be considered in implementing a liveness
algorithm.
Ease of use: liveness approaches vary in the ease
of use. For example, a fingerprint deformation
approach, which requires a specific rotation proce-
dure, may be considered more difficult to use [15].
A fingerprint sensor using spectroscopy where
liveness inherent to the biometric feature may be
considered easier to use.
Collectability: liveness approaches vary in the ease
of collection. For example, electrocardiogram,
which requires two points of contact on opposite
sides of the body or pulse oximetry where the
finger must be enclosed to protect from ambient
light [16].
User acceptance: liveness approaches that may have
low user acceptance are teh ones that are more
likely to be linked with medical conditions (eg.,
electrocardiogram, DNA).
Universality: clearly, all authorized users must be
live when enrolling. However, the liveness method
may be difficult to measure in some subjects.
For example, perspiration in fingerprint images
may be difficult to measure in subjects with very
dry skin.
Uniqueness: For liveness approaches that are inher-
ent to the biometric feature, this is essential.
However, it is not clear that, for example, electro-
cardiogram or gait is unique to large data sets
of individuals. Thus, these biometric/liveness
approaches may be appropriate for applications
with a smaller number of individuals.
Permanence is important to liveness approaches
taht are inherent to the biometric feature and
where the biometric/liveness features may vary
over time. This will impact on the biometric and
liveness error rates.
Spoof-ability describes whether the liveness mecha-
nism designed to protect against spoofing can be
spoofed. For example, it may be possible to fool
pulse oximetry-based liveness, using a clear spoof
that allows transmission of the light need ed to
make the pulse oximetry measurement.
The terms liveness and antispoofing are not com-
pletely synonymous. Measurements that rule out spe-
cific spoofs do not absolutely measure liveness. For
example, a liveness measure to detect pupil movement
will detect attempts based on a simple photograph
of a face. However, a modified spoofing method,
such as cutting a hole in the picture and putting a
real pupil behind it, may result in a successful spoof
attempt. Such a spoof is partially alive (to fool the
liveness) and partially a spoof (fabricated user biomet-
ric feature).
Encoded Biometric Schemes
Classical biometric systems require access to enrolled
templates in unencoded form. This differs from tradi-
tional computer security systems where a raw pass-
word need never be stored. Instead, a cryptographic
hash (one-way function) of the password is stored, and
each new test password is hashed and compared with
the stored version. Since such cryptographic techni-
ques provide important protections, there is great in-
centive to develop analog ous methods for biometric
systems. Encoded biometric schemes are designed to
avoid these problems by embedding the secret code
into the template, in a way that can be dec rypted only
with an image of the enrolled individual [17, 18].
Since the code is bound to the biometric template, an
attacker should not be able to determine either the
enrolled biometric image or secret code, even if he
had access to the biometric software and hardware.
Such technology would enable enhanced privacy
Security and Liveness, Overview
S
1149
S
