ACCA F1 Accountant in Business - 2010 - Study text - Emile Woolf Publishing
Подождите немного. Документ загружается.


Chapter 6: Functions of accounting and internal financial control
© EWP Go to www.emilewoolfpublishing.com for Q/As, Notes & Study Guides 215
the design and application of internal controls
information and communication
monitoring
A control environment
A control environment is the control culture within the organisation, and the
attitude of its employees toward ensuring that controls are adequate and properly
applied. Individuals within an organisation will not take control seriously unless
they are given direction form their bosses. The company’s directors are therefore
responsible for the control environment, and the board of directors must establish
policies on internal control. There should be a culture of control throughout the
organisation, from the board down to all employees, but the leadership must come
from the board, which sets the ‘tone at the top’.
Within this general control environment, an internal control system consists of four
elements. These can be seen as four sequential stages in a control system.
Risk identification and assessment
There should be a system for the regular review of risks, identifying new risks and
re-assessing existing risks. Risks that have been identified should be measured, to
assess their significance (in terms of probability of an adverse event and the amount
of loss that might be incurred if an adverse event happens).
Risk assessment can be carried out by means of a systems audit. Tests of control in
the external audit are also a form of risk assessment of current risks and existing
internal controls
Control activities (internal controls)
Controls for reducing risks should be designed and implemented. In financial
reporting, the main risks are risks of error and fraud. Controls should be designed
to eliminate a risk, but before effective controls can be designed, they must first be
identified and assessed. Management need to know what the risk is and how
serious it might be if it is not controlled.
Internal controls are a part of normal day-to-day operational activities and
procedures. The features of internal financial controls are explained in more detail
later.
Information and communication
An effective internal control system must have effective channels of communication,
to ensure that all employees understand their responsibilities for control and that all
relevant information reaches the individuals who need it. Controls cannot be
applied effectively unless the individuals responsible for the controls are kept
properly informed.

Paper F1: Accountant in business
216 Go to www.emilewoolfpublishing.com for Q/As, Notes & Study Guides © EWP
Monitoring
There should be regular monitoring and review of the effectiveness of the system of
internal control. One way of monitoring internal control is to have an internal audit
department, for carrying out reviews and reporting to senior management.
3.3 The consequences of weak internal financial control
When internal financial control is weak, there is a high risk of errors and fraud in
the accounting records and the financial statements.
When there is a large error, or an accumulation of smaller errors, the financial
statements will not be reliable.
Weak internal control makes it easier for fraudsters to operate. Fraud is a
criminal activity, and is damaging to company, its shareholders and possibly
also its customers.
In extreme cases, companies might operate in a condition close to insolvency
without its management or its shareholders being aware of the problem. Weak
corporate governance and weak financial control have been identified as the
main causes of major corporate collapses in the past – and will probably be the
cause of more corporate failures in the future.
3.4 Risks and internal financial controls
Financial risks
Financial risks have been described so far as the risk of an error in the accounts or
deliberate fraud. It is useful to think about what types of error might occur in the
accounting system. (Fraud is described in more detail later.)
A transaction might be omitted from the accounts entirely. For example, a sale of
goods on credit to a customer for $25,000 might not be recorded. If not, total
sales will be under-stated by $25,000 and the amount owed by customers will
also be under-stated by the same amount.
A transaction might be recorded twice. For example a credit sale of $25,000 to
customer X might be recorded twice, so that total sales are recorded as $50,000.
A transaction might be recorded with the wrong value. For example, an item of
machinery that is purchased for $20,000 might be recorded in the accounts with
a value of $30,000.
Numbers might be added up incorrectly. For example the total amount of
money receivable from credit customers might be stated incorrectly in the
financial statements because the amounts owed by each customer are added up
incorrectly.
A transaction might be recorded as the wrong type of transaction. For example a
sale to a customer might be recorded as a purchase, or as a sales return.
Chapter 6: Functions of accounting and internal financial control
© EWP Go to www.emilewoolfpublishing.com for Q/As, Notes & Study Guides 217
Types of internal controls
Internal financial controls are designed and implemented to deal with financial
risks. There are two broad types of internal control.
Preventative controls. These are controls that are designed to prevent the error
(or fraud) from happening.
Detective controls. These are controls that are designed to identify an error (or
fraud) when it happens. When there are detective controls, there should also be
corrective measures for correcting the error or dealing with the fraud.
3.5 Features of effective internal financial controls
Effective internal financial controls are controls that provide a high level of
assurance that errors or fraud will be prevented or will be detected when they
happen.
In addition, the cost of an internal control should not exceed the benefits obtain
from implementing it. (The benefits are the losses that might otherwise occur if the
control did not exist.)
You will learn more about internal financial controls as you progress through your
accountancy studies. However, various types of internal control procedure are
explained below. The analysis of internal controls is based on a mnemonic that was
used some years ago by the UK Auditing Practices Committee. It is no longer used,
but is nevertheless a helpful introduction to the subject.
Internal financial control procedures can be divided into eight types or categories,
which might be remembered by the mnemonic SPAMSOAP.
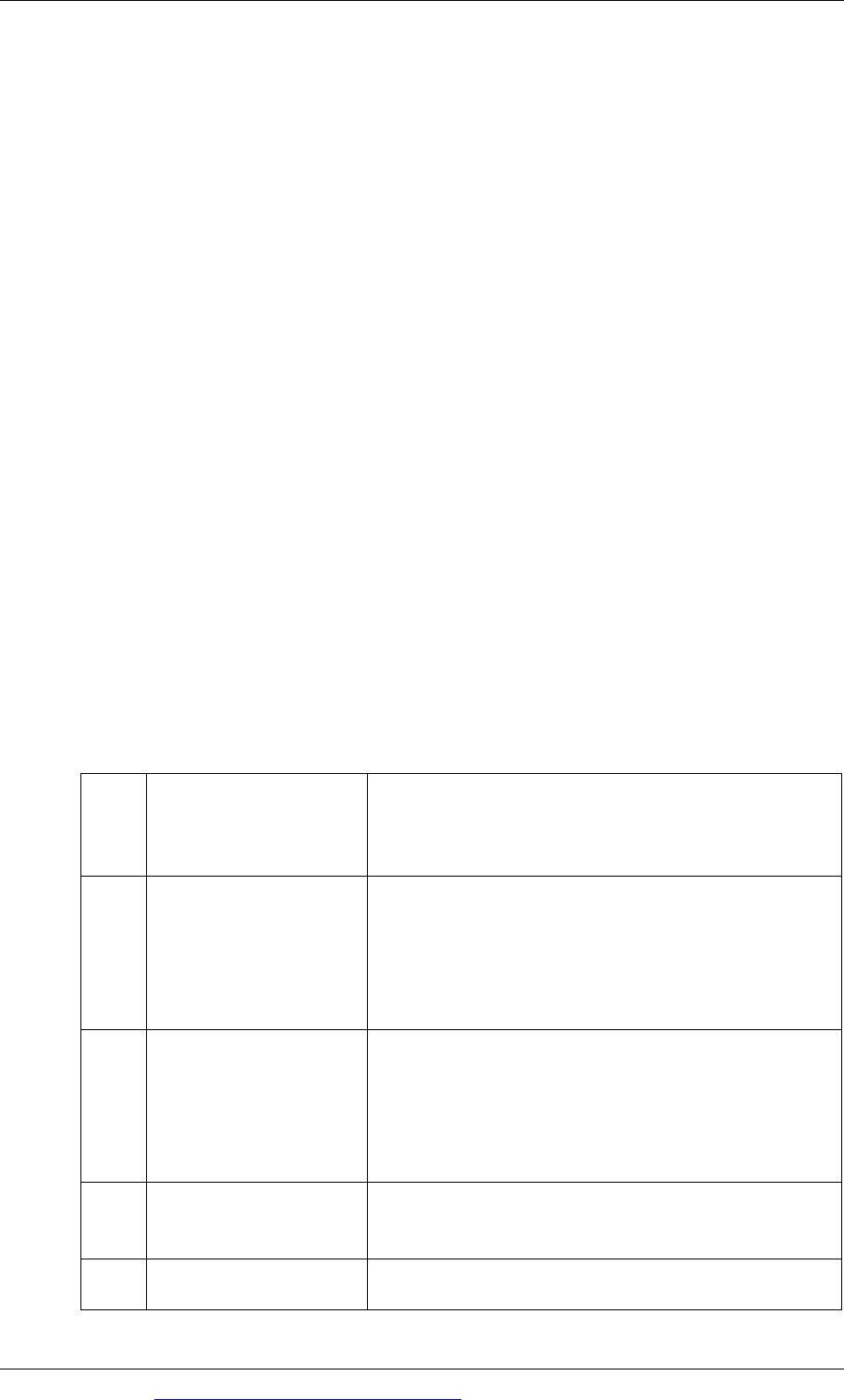
S
Segregation of duties Work should be divided between individuals
(segregated) so that work done by one individual
acts as a check on the work done by another. See
‘internal check’ below.
P
Physical controls
There should be controls to ensure the physical
safety or protection of assets. For example, cash
and valuable documents might be kept in a safe
and rooms containing valuable assets such as lap-
top computers should be kept locked when
unoccupied.
A
Authorisation and
approval
These are controls to ensure that transactions
should not go ahead unless they have been
properly authorised. For example, purchases and
other spending transactions above a certain value
might have to be authorised by a manager with
sufficient seniority.
M
Management Management have a responsibility for exercising
control on the basis of the information they
receive.
S
Supervision Work done by individuals might be monitored
and checked by a supervisor.

Paper F1: Accountant in business
218 Go to www.emilewoolfpublishing.com for Q/As, Notes & Study Guides © EWP
O
Organisation Controls can be applied by the way in which work
is organised and authority is delegated, and how
the work of different groups is co-ordinated.
A
Arithmetic and
accounting controls
Checks on arithmetical accuracy and other checks
within the accounting system help to identify
errors.
P
Personnel controls There should be controls over the selection and
training of employees, to ensure that they are
aware of the need for accuracy and the need to
apply controls.
Internal check
An internal check is a type of internal control. An internal check is intended to
prevent errors or fraud, or to detect them quickly when they occur. In financial
accounting, an internal check involves arranging accounting tasks and duties so that
no single task is performed from beginning to end by just one person. In this way,
the work of each individual is subject to an independent check in the course of the
work that is done by somebody else.
Internal checks are included in the SPAMSOAP list above as ‘segregation of duties’.
Example
An example of segregation of duties is a purchase transaction.
A purchase transaction begins with a purchase requisition, which must be properly
authorised. A buyer checks that the purchase requisition is valid and had been
properly authorised, before sending a purchase order to the supplier.
A warehouse manager or goods inwards manager is responsible for checking that
purchase orders are delivered from the supplier, checks the items on receipt against
the purchase order and delivery note, and takes custody of the goods.
The purchase invoice is received by an accounts clerk and checked against a copy of
the purchase order and delivery note. The purchase invoice is then recorded in the
accounts.
The cashier is responsible for making the payment, and is responsible for ensuring
that the amount paid is the amount on the invoice.
The payment is recorded by the accounts clerk in the accounting system. The clerk
checks that the correct amount has been paid by the cashier.
Example
Another example of segregation of duties is a system in which the individual
responsible for sending out sales invoices and recording the sales and amounts
receivable in the accounting system should not be the same person who receives and
processes the payments from the customers.

Chapter 6: Functions of accounting and internal financial control
© EWP Go to www.emilewoolfpublishing.com for Q/As, Notes & Study Guides 219
Example
Internal controls can be categorised as preventative controls, detective controls and
corrective controls. Here are some examples:
Type of internal control Examples
Preventative
Segregation of duties helps to prevent fraud.
Authorisation controls help to prevent improper
spending.
Passwords in computer systems prevent unauthorised
access.
Detective
Segregation of duties helps to identify errors
Reports of unusual amounts, values or transactions in
exception reports can bring possible errors to the
attention of management.
Reconciliation checks within an accounting system can
detect errors (when figures do not reconcile properly).
Supervisory checks can detect errors by accounts clerks.
Corrective
Management action on receiving information about
errors or variances from plan.

Paper F1: Accountant in business
220 Go to www.emilewoolfpublishing.com for Q/As, Notes & Study Guides © EWP
IT system security and controls
Threats to IT system security
General controls and application controls
General controls in IT
Application controls in IT
IT system audits
4 IT system security and controls
4.1 Threats to IT system security
Business organisations rely on IT systems to function. For example, accounting
systems are often computerised, and might contain large amounts of confidential
data. Computer systems need to be kept secure from errors, breakdown,
unauthorised access and corruption. Maintaining system security, even for small
home computers linked to the internet, is a permanent problem and the risks must
be managed continually.
Some of the major risks to IT systems are as follows:
Human error. Individuals make mistakes. They may key incorrect data into a
system. In some cases, they may wipe out records, or even an entire file, by
mistake. Human error is also a common cause of lapses in system security –
leaving computer terminals unattended is just one example.
Technical error. Technical errors in the computer hardware, the software or the
communications links can result in the loss or corruption of data.
Natural disasters. Some computer systems may be exposed to risks of natural
disasters, such as damage from hurricanes, floods or earthquakes.
Sabotage/criminal damage. Systems are also exposed to risk from criminal
damage, or simply theft. Risks from terrorist attack are well-publicised. Losses
from theft and malicious damage are much more common.
Deliberate corruption. All computer systems are exposed to risk from viruses.
Hackers may also gain entry to a system and deliberately alter or delete software
or data.
The loss of key personnel with specialist knowledge about a system (for
example, the risk that a senior systems analyst will leave his job in the middle of
developing a complex new system)
The exposure of system data to unauthorised users (for example hackers) and
industrial espionage.
In addition, there are risks within the computer software itself:
The software might have been written with mistakes in it, so that it fails to
process all the data properly.

Chapter 6: Functions of accounting and internal financial control
© EWP Go to www.emilewoolfpublishing.com for Q/As, Notes & Study Guides 221
The software should contain controls as a check against errors in processing,
such as human errors with the input of data from keyboard and mouse. The
software might not contain enough in-built controls against the risk of input
error and other processing errors.
4.2 General controls and application controls
Controls in IT can be divided into two categories:
general controls, and
application controls.
General controls are controls that are applied to all IT systems and in particular to
the development, security and use of computer programs. Examples of general
controls are:
physical security measures and controls
physical protection against risks to the continuity of IT operations
general controls within the system software such as passwords, encryption
software, and software firewalls
general controls over the introduction and use of new versions of a computer
program
the application of IT Standards.
Application controls are specific controls that are unique to a particular IT system
or IT application. They include controls that are written into the computer software,
such as data validation checks on data input.
4.3 General controls in IT
Physical access controls
Physical controls in an IT environment are the physical measures to protect the
computer systems such as:
putting locks on doors to computer rooms and keeping the rooms locked when
there are no authorised staff in the room.
putting bars on windows, and shatterproof glass in computer room windows, to
deter a break-in.
Protection against physical disaster: protection against risks to business
continuity
Computer systems are vulnerable to physical disasters, such as fire and flooding.
Risk control measures might include:
locating hardware in places that are not at risk from flooding and away from
locations that are in low-lying areas

Paper F1: Accountant in business
222 Go to www.emilewoolfpublishing.com for Q/As, Notes & Study Guides © EWP
physical protection for cables (to provide protection against fire and floods)
back-up power generators, in the event of a loss of power supply
using shatter-proof glass for windows where the computer is located
installing smoke detectors, fire alarms and fire doors
regular fire drills, so that staff know what measures to take to protect data and
files in the event of a fire
obtaining insurance cover against losses in the event of a fire or flooding.
Note that in some organisations, risk measures have also been taken to counter the
risk to computer systems from terrorist attack, and ensure that the computer system
will continue to operate even if there is a damaging attack. For example, two
companies might agree to allow the other to use its mainframe systems to operate
key computer systems, in the event that one of them suffers the destruction of its
system in a terrorist attack.
Passwords
A computer password is defined as ‘a sequence of characters that must be presented
to a computer system before it will allow access to the systems or parts of a system’
(British Computer Society definition).
Typically, a computer user is given a prompt on the computer screen to enter his
password. Access to the computer system is only permitted if the user enters the
correct password.
Passwords can also be placed on individual computer files, as well as systems and
programs.
To gain access to a system, it may be necessary to input both a user name and a
password for the user name. For example, a manager wanting to access his e-mails
from a remote location may need to input both a user name and the password for
the user name.
However, password systems are not always as secure as they ought to be, mainly
due to human error. Problems of password systems include the following:
Users might give their passwords to other individuals who are not authorised to
access the system.
Users are often predictable in their choice of passwords, so that a hacker might
be able to guess, by trial and error, a password to gain entry to a system or
program or file. (Typically, users often select a password they can remember,
such as the name of their father or mother, or the month of their birth).
Passwords are often written down so that the user will not forget it. Copied
passwords might be seen, and used, by an unauthorised person.
Passwords should be changed regularly, but often-poor password control
management means that passwords go unchanged for a long time.

Chapter 6: Functions of accounting and internal financial control
© EWP Go to www.emilewoolfpublishing.com for Q/As, Notes & Study Guides 223
A system of password controls should operate more successfully if certain control
measures are taken.
Passwords should be changed regularly frequently, and employees should be
continually reminded to change passwords.
Users should be required to use passwords that are not easy to guess: for
example, an organisation might require its employees to use passwords that are
at least 8 digits and include a mixture of letters and numbers.
A security culture should be developed within the organisation, so that the
user’s staff are aware of the security risks and take suitable precautions.
Encryption
Encryption involves the coding of data into a form that is not understandable to the
casual reader. Data can be encrypted (converted into a coded language) using an
encryption key in the software.
A hacker into a system holding data in encrypted form would not be able to read
the data, and would not be able to convert it back into a readable form (‘decrypt the
data’) without a special decryption key.
Encryption is more commonly used to protect data that is being communicated
across a network. It provides a protection against the risk that a hacker might
intercept and read the message. Encryption involves converting data into a coded
form for transmission with an encryption key in the software, and de-coding at the
other end with another key. Anyone hacking into the data transmission will be
unable to make sense of any data that is encrypted.
A widely-used example of encryption is for sending an individual’s bank details via
the Internet. An individual buying goods or services from a supplier’s web site may
be required to submit credit card details. The on-line shopping system should
provide for the encryption of the sender’s details (using a ‘public key’ in the
software for the encryption of the message) and the decryption of the message at the
seller’s end (using a ‘private key’ for the decryption).
Preventing or detecting hackers
Various measures might help to prevent hacking into a system, or to detect when a
hacker has gained unauthorised access. However, the fight against hacking is never-
ending, and computer users must be alert at all times.
Controls to prevent or detect hacking include:
physical security measures to prevent unauthorised access to computer
terminals
the use of passwords
the encryption of data
audit trails, so that transactions can be traced through the system when hacking
is suspected

Paper F1: Accountant in business
224 Go to www.emilewoolfpublishing.com for Q/As, Notes & Study Guides © EWP
network logs, whereby network servers record attempts to gain access to the
system
firewalls.
Firewalls
Firewalls are either software or a hardware device (between the user’s computer
and modem). Computer users might have both.
The purpose of a firewall is to detect and prevent any attempt to gain unauthorised
entry through the Internet into a user’s computer or Intranet system.
A firewall:
will block suspicious messages from he Internet, and prevent them from
entering the user’s computer, and
may provide an on-screen report to the user whenever it has blocked a message,
so that the user is aware of the existence of the messages.
In spite of the preventive measures that are taken, there is a very high risk that
computers attached to the Internet will suffer from unauthorised access. An
organisation would be well advised to carry out regular tests on its computers, to
search for items that have been introduced without authority and illegally, and to
get rid of them.
Firewalls can be purchased from suppliers. Some software is provided with in-built
firewall software. Some firewall software can be downloaded free of charge from
the Internet. There is no excuse for a computer user with Internet access not to have
a firewall.
Firewalls are necessary for computers with Internet access because:
they are continually exposed to corrupt messages and unauthorised access for as
long as they are connected to the Internet (which may be 24 hours a day) and
the volume of ‘suspicious’ messages circulating the Internet is immense.
Computer viruses
Viruses are computer software that is designed to deliberately corrupt computer
systems. Viruses can be introduced into a system on a file containing the virus. A
virus may be contained:
in a file attachment to an e-mail or
on a backing storage device such as a CD.
