Yanushkevich S.N., Wang P.S.P., Gavrilova M.L., Srihari S.N. (eds.) Image Pattern Recognition. Synthesis and Analysis in Biometrics
Подождите немного. Документ загружается.


April 2, 2007 14:42 World Scientific Review Volume - 9in x 6in Main˙WorldSc˙IPR˙SAB
388 Synthesis and Analysis in Biometrics
(confidence interval for training). Note that the difference ∆t = t
2
− t
1
corresponds to the cost-function of training.
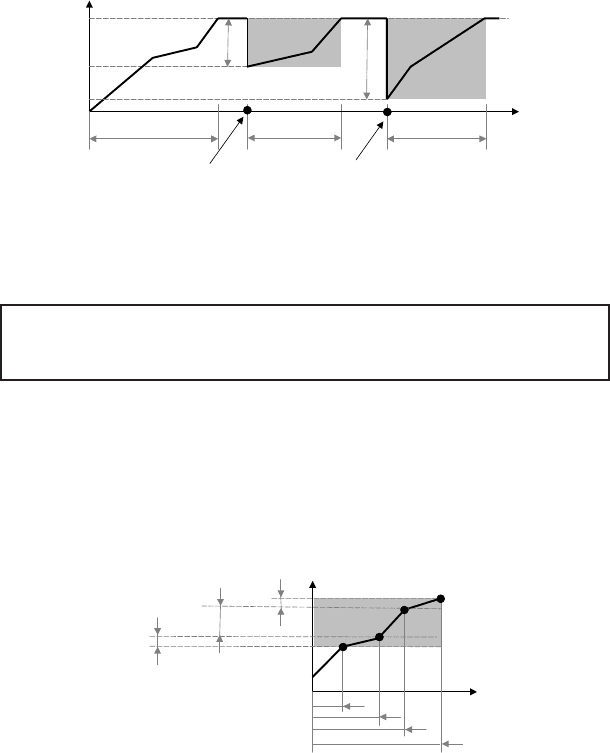
A-strategy of training
T(t)
Time t
Effect '=t
2
-t
1
Confidence
interval for
training
B-strategy of training
t
1
t
2
Fig. 15.9. Training function T (t) for estimation of A and B strategies of training.
The training function T (t) is useful for the estimation of the impact of
various modifications and installations of new devices and systems on the
personnel’s skills. In terms of Bayesian statistics, the effect of a new device
installation can be expressed as
P (Skills) × P (New device|Skills)=P(Skills|New device),
that is,
The prior-to-data probability of the HQP skills revised with
the probability model of additional devices gives the updated
probability of skills.
The training function T (t) is useful for the estimation of the impact
of various modifications and installations of new devices on the quality of
personnel.
Example 30. Assume that two new devices have been installed in t
1
and t
2
(Fig. 15.10). Without training, personnel are not able to use these devices,
and the training function drops.
15.3.4. Evolution Function
A function that shows how additional information can improve decision
making is called an evolution function I(t) in our approach. This is a non-
decreasing function of time t. In terms of Bayesian statistics, the efficiency
of installation of new biometric devices can be expressed as
P (New device) × P (Data|New device)=P (New device|Data),
April 2, 2007 14:42 World Scientific Review Volume - 9in x 6in Main˙WorldSc˙IPR˙SAB
Fundamentals of Biometric-Based Training System Design 389
Acceptable level of qualification
Initial training Re-training
Re-training
T(t)
Time t
New device A
installation
New device B
Installation
Motivation
for training
t
1
t
2
Fig. 15.10. Installation of the new devices A and B at t
1
and t
2
, respectively, require
re-training of personnel.
The prior-to-data probability of the new biometric devices
revised with the probability model of any additional device
gives the updated probability of the new devices.
Example 31. The evolution function I(t) is interpreted in Fig. 15.11
as a function of the number of newly installed biometric devices. They
provide additional information about the authorized individual. The effect
of installing new devices is an increase in the probability of making the
correct decision.
I(t)
Time t
New biometric devices
provide extra information
Effect '
1
Effect '
1
Effect '
1
Fig. 15.11. The function of insufficiency of information I(t) vs. time of installation for
new biometric devices.
Example 32. The IR image indicates that there is no drug or alcohol
consumption. However, through conversation with a person, the officer
suspects that drugs and alcohol have been consumed. His decision may
include testing of this individual’s iris, or a pupil analyzer. The evolution
April 2, 2007 14:42 World Scientific Review Volume - 9in x 6in Main˙WorldSc˙IPR˙SAB
390 Synthesis and Analysis in Biometrics
function is also useful for predictive analysis both in the PASS and the
training system.
15.4. Training System Design
Prototyping a training system is based on functional analysis, which
includes design analysis and system synthesis. Design analysis aims at
establishing requirements, specifications, and design evaluation criteria
for the designed system. System synthesis is the translation of system
requirements and functions into hardware and software specifications.
15.4.1. Desired Characteristics
T-PASS is distinguished from existing training systems by many features,
which can be grouped with respect to architectural, topological, functional,
communication, cost, and other criteria. To minimize cost, T-PASS
utilizes PASS architectural principles and related characteristics and
functionalities. Below, a sample of components and desired characteristics
of T-PASS are given:
Screening, which is widely used in applications such as airport checkpoints,
facilities access, etc.
Decision making support. A knowledge intensive technique can be useful.
However, alternative techniques can be applied to achieve the same
but more cost-efficient result (we used multi-valued logic and decision
diagram techniques
[
49
]
)
Real-world conditions of training, which is accomplished by the reconfigu-
ration of PASS into the training system using minimal extra tools.
Flexibility, the extent to which the system can accommodate changes to
the tasks and environments beyond those first specified.
Expandability and adaptibility. In the proposed training system, the basic
configuration includes tools for generation of early warning data using
visible and IR images, and tools for generation of other synthetic
biometrics. The first will model the pre-screening process, and the
second will model the authorization process at the check-desk.
Early warning, that is, the ability to get preliminary information about
an individual, and in this way to reserve extra time for analysis of data
before authorization.
Multiprocessor and distributed configuration. Three main information
streams should be processing in real time: pre-screening data, screening
data, and data from local and global databases.

April 2, 2007 14:42 World Scientific Review Volume - 9in x 6in Main˙WorldSc˙IPR˙SAB
Fundamentals of Biometric-Based Training System Design 391
Mobile configuration. T-PASS inherits this property from PASS which
can be deployed at any public place where authorization is needed
(important public events, exhibitions, and other social meetings or high
profile settings where VIP security is required on a temporary basis).
These characteristics were the desired aims at the various phases of the
system design.
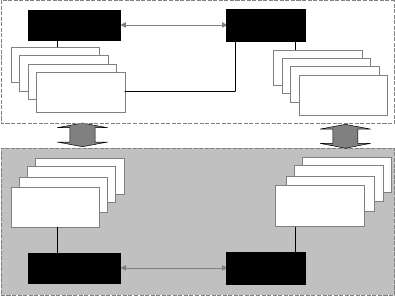
15.4.2. Architecture
In the development of the training system T-PASS, most of the features
of PASS are inherited. In Fig. 15.12, the topological and architectural
properties of both of these systems are shown. It follows that the T-PASS
architecture uses the PASS platform. However, T-PASS is different from
PASS in the following features:
(a) Biometrics of pre-screened and screened individuals are simulated by
the system,
(b) The appearance of biometric data can be modeled by the user using
modeling tools,
(c) Local and global databases are simulated.
Phase 1
(unknown person)
Processing
preliminary
data
Phase 2
(specified
individual)
Dialogue
support
Knowledge domain
converter
Forming
the
person’s
file
Global
database
Phase 3:
Decision
making
Visible
band
camera
Visible
band
camera
IR ban
d
camera
IR band
camera
Voice
analyzer
On-line
processing
10-20 meters distance
Gait biometric
Individual
Officer
Pre-screened
individual
PASS
Processing
preliminary data
Dialogue
support
Knowledge domain
converter
Voice
analyzer
Trained
person
Temperature
templates
Synthetic
faces
generator
Speech
tracing
Scenario
database
T-PASS
Synthetic
biometric data
generation
(a) (b)
Fig. 15.12. The PASS (a) and T-PASS (b) architecture.
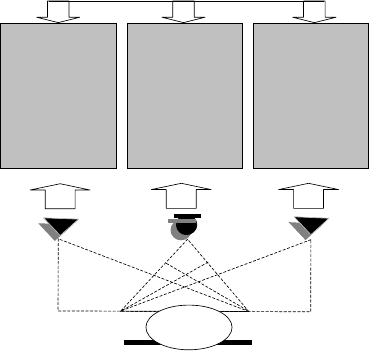
The following distribution of biometric devices is related to the screening
discipline (Fig. 15.13):
April 2, 2007 14:42 World Scientific Review Volume - 9in x 6in Main˙WorldSc˙IPR˙SAB
392 Synthesis and Analysis in Biometrics
Distance, or non-contact biometrics (facial image in visible and IR
bands), used to provide early warning information about a pre-screened
individual. Gait biometrics is a good candidate for obtaining the
additional information when individuals move from pre-screened to
screened positions.
Contact biometrics, used to provide information about an individual
(fingerprints, palmprint, hand geometry, signature, stroke dynamic,
etc.) Correlation between various biometrics in semantic form provide
a useful interpretation of biometric patterns.
PRE-
SCREENING
Gait biometric
(
1
0
-
20 meter
s
)
CHECK-
POINT
Distance
(non-contact)
biometrics
Contact
biometrics
Synthetic
biometrics
SIMULATION
OFFICER
PASS
T-PASS
Gait biometric
simulatio
n
Synthetic
biometrics
Fig. 15.13. The topological properties of PASS and the distribution of various types
of biometric: distance (non-contact) biometrics are used to obtain early warning
information and near distance and contact biometrics are used in real time authorization.
Our approach to T-PASS design is related to virtual modeling
techniques
[
5
]
. Virtual environments refer to interactive systems that
provide the user with a sense of direct physical presence and direct
experience. These systems include visual and feedback techniques, and
allow natural interaction by manipulation of computer-generated objects.
In T-PASS, synthetic biometric data are used that can be understood as
virtual biometric data.
Example 33. Surgeons and security personnel do not prefer immersion-
based training systems since it makes them feel isolated from the real
operation scene.
April 2, 2007 14:42 World Scientific Review Volume - 9in x 6in Main˙WorldSc˙IPR˙SAB
Fundamentals of Biometric-Based Training System Design 393
15.4.3. Training Scenarios
Humans form mental models through experience, training and instruction.
Important human factors that are studied through the mental model are
the prioritization of events and their sequence of occurrence. In PASS,
scenarios are developed using architectural and topological characteristics.
Possible scenarios are divided into three groups: regular, non-standard, and
extreme. Most scenarios in each group are generated automatically using
computer-aided design tools.
Scenarios based on distance IR images
Let us consider an example of a training scenario, in which the system
generates the following data about the screened person:
Time 00.00.00:
Protocol of pre-screening person 45
Warning, level 04
Specification: Drug or alcohol consumption, level 03
Possible action:
1. Direct special inspection
2. Register with caution
It follows from this protocol that the system evaluates the fourth level
of warning using automatically measured drug or alcohol consumption for
the screened individual. A knowledge-based sub-system evaluates the risks
and generates two possible solutions. The officer can, in addition to an
automatic analysis, analyze the acquired images in the visible and IR
spectra.
Scenarios corresponding to the results of matching
We distinguish scenarios that correspond to the results of the matching of
an individual’s data with data in local and global databases. This process
is fully automated for some stationary conditions, for example:
Time 00.00.00:
Protocol of screening person 45
Warning, level 04
Specification: Drug or alcohol consumption, level 03
Local database matching: positive
Possible action:
1. Register
2. Clarify and register
April 2, 2007 14:42 World Scientific Review Volume - 9in x 6in Main˙WorldSc˙IPR˙SAB
394 Synthesis and Analysis in Biometrics
Note that data may not always be available in a database — this is the
worst case scenario, and knowledge-based support is vital in this case.
Scenarios based on the analysis of behavioral biometric data
The example below introduces scenarios based on the analysis of
behavioural biometric data.
Time 00.00.00:
Protocol of screening person 45
Warning, level 04
Specification: Drug or alcohol consumption, level 03
Local database matching: positive
Proposed dialog:
Question 1: Do you need medical assistance?
Question 2: Any service problems during the flight?
Question 3: Do you plan to rent a car?
Question 4: Did you meet friends on board?
Question 5: Do you prefer red wine or whisky?
Question 6: Do you have drugs in your luggage?
The results of automatically analyzed behavioral information are
presented to the officer:
Time 00.00.00:
Protocol of screening person 45
Warning, level 04
Specification: Drug or alcohol consumption, level 03
Local database matching: positive
Level of trustworthiness of Question 6 is 03: Do you have drugs in
your luggage?
Possible action:
1. Direct to special inspection
2. Continue clarification by questions
15.4.4. Decision Making Support
In the training system, decisions are generated by special tools and
various scenarios in PASS, instead of the local biometric device response
(Fig. 15.14).

April 2, 2007 14:42 World Scientific Review Volume - 9in x 6in Main˙WorldSc˙IPR˙SAB
Fundamentals of Biometric-Based Training System Design 395
Scenario 1
Scenario 2
Scenario 3
SIMULATION OF
AUTOMATIC DECISION
MAKING OF
BIOMETRIC DEVICES
OFFICER
Decision
making
KNOWLEDGE
BASED
SUPPORT
Local
level
Global
level
Analysis
Fig. 15.14. Automatic generation of decisions at local levels is replaced in the training
system by a simulator.
15.5. Training System Prototype
Prototyping of T-PASS is aimed at proving the basic concept of training
system design. In this section, we introduce some details of the platform,
data flows and their representations, computing of indirect characteristics,
conversion patterns from signal to knowledge domain, and estimations.
15.5.1. Platform
In prototyping we used an extended platform, that is, we implemented the
hardware and software tools without constraints on the cost and criteria of
optimal configuration. The following facilities were utilized in prototyping
[
52
]
:
Hardware platform: a network of four computers connected with cameras
in the IR and visible bands,
Software platform: about a dozen packages on biometric data processing
and simulation,
Local and global communication resources, and
Biometric devices: about a dozen contact and non-contact devices for the
acquisition and recognition of behavioral and physical biometrics.
15.5.2. Data Flow
In prototyping, we distinguish several levels of data flows. First of all, the
information flows are divided into the following streams:
Static document record and biometric data from local and global
databases.
April 2, 2007 14:42 World Scientific Review Volume - 9in x 6in Main˙WorldSc˙IPR˙SAB
396 Synthesis and Analysis in Biometrics
Dynamic biometric data obtained from surveillance facilities and conversa-
tion with an individual at the desk, including behavioural biometric
data (voice, facial expressions, signature).
We distinguish four forms of the individual’s information:
(a) File data from databases which are well structured and standard;
(b) Appearance, or visual data, acquired mainly in real-time;
(c) Other appearance information, such as IR images, which requires
specific skills for understanding and analysis;
(d) Various forms of behavioural biometrics (facial expressions, voice,
signature) that are acquired in real-time (during pre-screening or check-
in procedure).
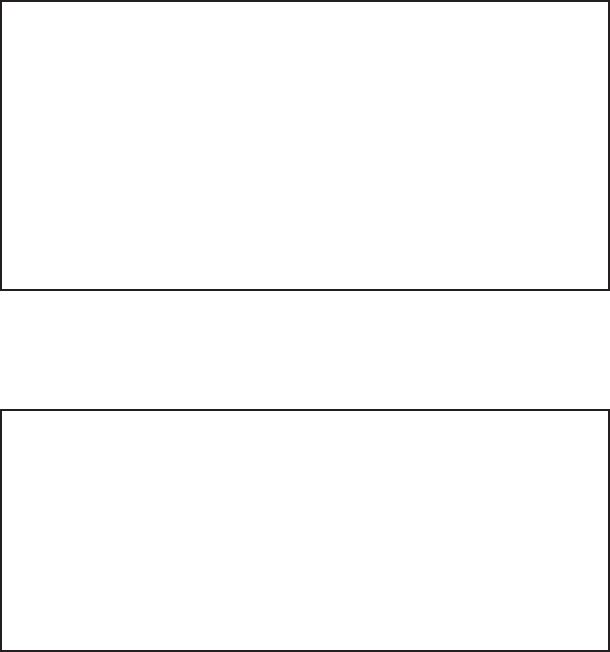
15.5.3. Indirect Characteristic Computing
In our experimental study, we focus on various aspects of indirect
characteristic computing, in particular (Fig. 15.15): interpretation of
biometric patterns in semantic form, initialization of questionnaires,
reliability of biometric data, and their improvement using correlation in
the knowledge domain.
Temperature
Alcohol and dru
g
s
consumption
Blood pressure
Pulse
Artificial
accessories
Plastic surgery
Information
source
from
3-12
P
m
Tension
Intonation
Phonetic level
Phonological
level
Morphological
level
Correlation with
physiological
parameters
Facial
expressions
Iris
Brow and lips
movements
Correlation with
speech and
physiological
parameters
Information
source
from
400-700
P
m
Information
source
from
70-600Hz
C o r r e l a t I o n
Authorized
individual
Fig. 15.15. Prototyping indirect biometric characteristics using correlation technique.
A fragment of this design is given in Fig. 15.16. The officer manipulates
and efficiently uses biometric data to make a decision according to various
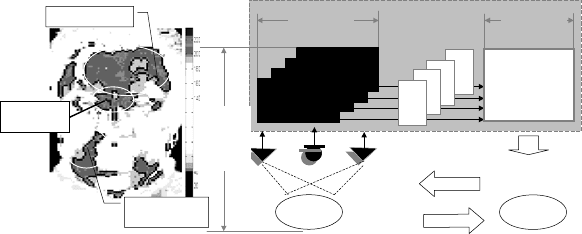
April 2, 2007 14:42 World Scientific Review Volume - 9in x 6in Main˙WorldSc˙IPR˙SAB
Fundamentals of Biometric-Based Training System Design 397
scenarios. Many factors render decision making a complex procedure. To
simplify this procedure, decision making is divided into several simple steps
with respect to time and levels.
Health problems
Alcohol or drug
consumption
Unexpected
question
Supporting
questions
BIOMETRIC
FEATURES IN
VISIBLE,
INVISIBLE, AND
ACOUSTIC
BANDS
Microphone
Camera
in IR
band
Camera
in visible
band
Non-
invasive
automatic
biometric
measures
Supporting
dialog
algorithms
Signal
domain
Knowledge
domain
Conversation
features to
knowled
ge
Question
Answer
Officer
Authorized
individual
(a) (b)
Fig. 15.16. Prototyping of T-PASS: interpretation of temperature regions in an IR
image (a) and generation of supporting questions in PASS (b).
15.5.4. Conversion of Data
The key component of a system is the converter from the signal domain
to the knowledge domain. The efficiency of the converter is critical in
decision making support. The converter implements a knowledge-based
technology. In the development of the converter and its prototyping, we
utilize properties of the system such as
(a) Limited sets of supported questions (biometric patterns of a given class
initialize 3–5 questions),
(b) Limited types of biometrics (about 10), and
(c) A limited number of possible correlation (about 20).
The example below explains our approach.
Example 34. Let us assume that there are three classes of samples
assigned to “Disability,” “Alcohol intoxication,” and “Normal,” and
denoted as values of the three-valued logic variable {0}, {1},and{2},
respectively. Let us also assume that feature patterns from facial IR
image and gait correspond to the above classes. Using a logic function
representation and decision diagram technique
[
35,49
]
, the following
semantic constructions can be generated by the system
