Yanushkevich S.N., Wang P.S.P., Gavrilova M.L., Srihari S.N. (eds.) Image Pattern Recognition. Synthesis and Analysis in Biometrics
Подождите немного. Документ загружается.

April 2, 2007 14:42 World Scientific Review Volume - 9in x 6in Main˙WorldSc˙IPR˙SAB
368 Synthesis and Analysis in Biometrics
in applications where high confidentiality and reliable decision making are
critical.
Most of today’s physical access control systems extensively utilize the
information collected during the authorization check itself, but make limited
or no use of the information gained in the conversation with individual
during the authorizing procedure. The officer must make a decision in a
limited time based on authorization documents, personal data from the
databases, and his/her own experience. This may not be sufficient to
minimize the probability of mistakes in decision making.
Consider, for example, the Defense Advanced Research Projects Agency
(DARPA) research program, HumanID, which is aimed at the detection,
recognition and identification of humans at a distance in early warning
support systems for force protection and homeland defense
[
45
]
.Existing
screening systems exclusively utilize visual appearance to compare against
“lookout checklists” or suspected activity, and do not effectively use the
time slot before/during registration to collect biometric information (body
temperature, surgical changes) about an individual. In addition, they do
not arm the officer with decision-making support (such as modeling of
the aging face, artificial facial accessories, and other features, for further
comparison against the information available in databases.
The job of a customs or security officer becomes complicated if
submitted documents do not match the appearance of an individual. In
order to draw firm conclusions, additional information is needed. This
information is available in the next-generation PASS system, which uses
both pre-screening and check-point biometric information. The skilled
PASS user possesses an ability to manipulate and efficiently utilize various
sources of information in the decision making process. Hence, a training
system is needed to implement the PASS in practice
[
51,52
]
. However,
personnel training cannot keep pace with rapid changes in technology for
physical access control systems. This is the driving force behind developing
novel training paradigms to meet the requirements of security policy.
Traditionally, training is implemented on a specifically desqigned
training system. For example, training methodologies are well developed for
pilots
[
13
]
, astronauts, surgical applications
[
27
]
, and in military systems.
These are expensive professional simulation systems, which are difficult
to modify or extend, since they are unique in architecture and functions.
For example, the traditional flight simulator is a large domelike structure
placed on a motion platform and housing an identical replica of an airplane
cockpit. Such training is very realistic (including effects such as engine
sounds, airflow turbulence, and others) but expensive. An example of the
newer generation of simulators is the networked simulation environment
in
[
7
]
. Mission team level training is based on networked nodes of several
April 2, 2007 14:42 World Scientific Review Volume - 9in x 6in Main˙WorldSc˙IPR˙SAB
Fundamentals of Biometric-Based Training System Design 369
fighter simulators, air warning system (AWACS) simulators, and synthetic
computer-aided designed enemy forces. The whole simulation is taped,
allowing postmission debriefing either at the local or global level. Typically,
pilots fly two 1-hour missions each day, with a debriefing after each mission.
The debriefing analyzes the mission mistakes, which pilots can learn to
avoid in a repeat simulation. The pilot’s performance is assessed by
instructors using monitoring stations.
This methodology is partially acceptable for training PASS users. In
our approach, the design of a expensive training system is replaced by
an inexpensive extension of the PASS, already deployed at the place of
application. In this way, an important effect is achieved: modeling is
replaced with real-world conditions. Furthermore, long term training
is replaced by periodically repeated short-time intensive computer-aided
training.
The PASS and T-PASS implement the concept of multi-target platforms, that
is, the PASS can be easy reconfigured into the T-PASS and vice versa.
We propose a training paradigm utilizing a combination of various
biometrics, including visual-band, IR, and acoustic acquisition data for
identification of both physical appearance (including natural factors such
as aging, and intentional (surgical) changes), physiological characteristics
(temperature, blood flow rate, etc.), and behavioral features (voice). Other
biometrics can be used in pre-screening and at check-points: gait biometrics
are used between the points of the appearance of an individual and near-
distance, non-contact and contact biometrics at the check-point. Note that
gait can be thought of as learned motor activity of the lower extremities,
which when performed, results in the movement of the subject in the
environment. By changing various parameters of a gait (stride length,
velocity, heel and toe strike, timing, etc.) one can perform an infinite
variety of gaits
[
15,31
]
.
In complex systems, such as PASS and its user training system —
T-PASS, several local levels and a global level of hierarchy are specified.
In our approach, biometric devices are distributed at the local levels.
The role of each biometric device is twofold:
(a) Their primary function is to extract biometric data from an individual and
(b) their secondary function is to “provoke” question(s).
April 2, 2007 14:42 World Scientific Review Volume - 9in x 6in Main˙WorldSc˙IPR˙SAB
370 Synthesis and Analysis in Biometrics
For example, if high temperature is detected, the question should
be formulated as follows: “Do you need any medical assistance?” The
key of the proposed concept of decision making support in PASS is the
process of generating questions initiated by information from biometric
devices. In this way, the system assists the officer in access authorization.
Additionally, by using an appropriate questionnaire technique, some
temporary errors, and the temporary unreliability of biometric data, can
be alleviated. The proposed approach can be classified as a particular
case of image interpretation technique, deploying case-based reasoning
using questionnaire strategies for acquisition and evaluation of knowledge
[
34
]
.
In our approach, experience gained from dialog system design is utilized.
In particular, PASS and T-PASS are based on architectural principles
similar to SmartKom
[
19
]
, i.e. sensor specific input processing, modality
specific analysis and fusion, and interaction management. The differences
follow from the target function: PASS and T-PASS aim to support an officer
in human-human interaction, while SmartKom aims to provide human-
machine interaction.
Training techniques and training system design use domain specific
terminology. An example of this terminology is given in Table 15.1 These
terms will be used in various combinations. For example, training scenarios
can be considered for real-world conditions, where hybrid biometric data are
used — that is, real and synthetic (simulated) data. Knowledge and signal
domains are considered in the context of the space of available information
and the space of decision making.
Our results are presented as follows. Section 15.2 formulates the
requirements for a training methodology using PASS and T-PASS. The
focus of Section 15.3 is a technique for estimation of training, including the
skills of personnel and the effectiveness of the training system. The basic
approaches to the design of the system are given in Section 15.4. The results
we obtained from prototyping the proposed system are given in Section 15.5
We summarize the results obtained and discuss open problems for further
research in Section 15.6.
15.2. Basics of Training Security System Design
In this section, we focus on fundamental requirements for training systems,
modeling of the biometric-based physical access control system, and
decision making support for security personnel.
April 2, 2007 14:42 World Scientific Review Volume - 9in x 6in Main˙WorldSc˙IPR˙SAB
Fundamentals of Biometric-Based Training System Design 371
Table 15.1. Terminology of training systems.
Term Comments
Simulation
Generation of artificial (synthetic) biometric data and/or
virtual environment (Figs. 15.4 and 15.13)
Training scenario
System configuration protocols that provide for the
particular goals of training (Section 15.4.3)
Real-world training Training of personnel in a real-world environment
Early warning paradigm
A scenario that provides data using distance surveillance
Knowledge and signal
domain
Data representation that is acceptable for human and
machine communication, respectively (Fig. 15.1)
Space of decision making
A set of biometric features acceptable for decision making
(Fig. 15.5)
Space of available
information
The set of biometric sources of information in the system
(Fig. 15.5)
Degradation, training, and
evolution functions
Functions that characterize loss of skill, efficiency of
training strategy, and improving decision making by
extending the space of available information, respectively
(Section 15.3)
15.2.1. Requirements of Training Systems
Flexibility
The development of PASS must be synchronized with the training of
its users. PASS is a dynamically developing system because of its
reconfigurable architecture and the capability of integration of new devices.
Hence, the training methodology and architectural properties of the
training system, T-PASS, must reflect the dynamic nature of PASS. This
property is called flexibility, that is, the capability of the training system
for extension, modification, and accommodation to changes in tasks and
environments beyond those first specified.
Learnability
The use of each system requires specific skills. The T-PASS is a complex
system that requires certain skills of its personnel, therefore the personnel

April 2, 2007 14:42 World Scientific Review Volume - 9in x 6in Main˙WorldSc˙IPR˙SAB
372 Synthesis and Analysis in Biometrics
need time for learning the system. Learnability is measured by the time and
effort required to reach a specified level of user performance. This amount
should be minimized. In our approach,
The experience of the PASS user can be used in the T-PASS because they both
run on the same hardware and software platform, which minimizes learning
time.
Short-term, periodically repeated, and intensive training
Traditionally, training is a long-term and costly process and particular skills
(often not required of the trainee in practice) degrade over time. In contrast,
The concept of the mobile PASS requires short-term training in a new
environment.
Hence, the training methodology should be short-term, periodically
repeated,andintensive. In our approach, the security system can be used
as a training system (with minimal extension of tools) without changing of
the place of deployment. In this way we fulfill the criterion of cost-efficiency
and satisfy the above requirements.
Training for extreme situations
Simulation of extreme scenarios is aimed at developing the particular
skills of the personnel. The modeling of extreme situations requires
developing specific training methodologies and techniques, including virtual
environments.
Example 18. Severe Acute Respiratory Syndrome (SARS) is an illness
with a high infection and a high fatality rate
[
47
]
. At the early stage
of this disease, it appears as a high temperature spot in the IR image.
Early detection and immediate isolation of those infected are the keys to
preventing another outbreak of such an epidemic.
Example 19. Monitoring of the breathing function of a pre-screening
individual and one who is being screened can be used to predict heart
attacks, in particular. The breathing rate during the dialog is considered
as the individual’s response to questions, i.e. differences in breathing rates
correspond to different questions
[
36
]
.
Confidentiality
Confidentiality of data must be implemented at many levels of the security
system, including local biometric devices and databases, and information

April 2, 2007 14:42 World Scientific Review Volume - 9in x 6in Main˙WorldSc˙IPR˙SAB
Fundamentals of Biometric-Based Training System Design 373
from the global database. Processing biometric data such as IR images and
their interpretation in semantic form must addresses privacy and ethical
issues.
Interpretability
This issue is related to biometric-based security systems. Interpretability of
the biometric patterns encoded in biometric devices is often more important
than the predictive accuracy of these devices.
Example 20. The interpretation of data from medical devices is especially
important in medical applications, where not only the correct decision is
desired, but also an explanation of why that particular decision has to be
made. This is why systems which provide human-comprehensible results
are considered to be more acceptable than “black box” biometric devices.
The decision process should be easily followed and understood.
Ergonomic issues
The objective of ergonomics is to maximize an operator’s efficiency and
reliability of performance, to make a task easier, and to increase the feeling
of comfort and satisfaction. The work of the officer is very intensive:
he/she must minimize both the time of service and the risk of a wrong
authorization. Improvements to PASS during authorization could be made,
for example, using footpedals, a footmouse, several monitors, or a speech
interface. Some ergonomic problems are discussed in
[
11
]
.
15.2.2. Model of the Biometric-Based Access Control
PASS is a next generation security system.
PASS combines several basic approaches: early warning data fusion,
multimode sources of information, and authorization techniques.
The generic model of the PASS is given in Fig. 15.1, and details are
provided in Table 15.1. Two processes occur in the system simultaneously:
pre-screening of an individual-A (collection of information) and screening
of an individual-B (analysis of screened information). Early warning data
is the result of pre-screening analysis. This data belongs to the one of three
clusters:
Alarming cluster (extreme scenario),
Warning cluster (authorization with caution), and
Regular cluster (regular authorization).
April 2, 2007 14:42 World Scientific Review Volume - 9in x 6in Main˙WorldSc˙IPR˙SAB
374 Synthesis and Analysis in Biometrics
BIOMETRIC
DEVICES
Support
Officer
BIOMETRIC
DEVICES
CONVERTER OF
SIGNAL DOMAIN INTO
KNOWLEDGE DOMAIN
Feedback loop 2
Feedback loop 3
Feedback loop 1
Question
Answer
Pre-screening
individual
Information about
authorized
individua
l
A
Individual
B
Individual
Pre-screening
data
Screening
individual
Screening
data
Signal domain of biometric features
Time T
1
for early warning
Time T
2
for decision making
on authorization
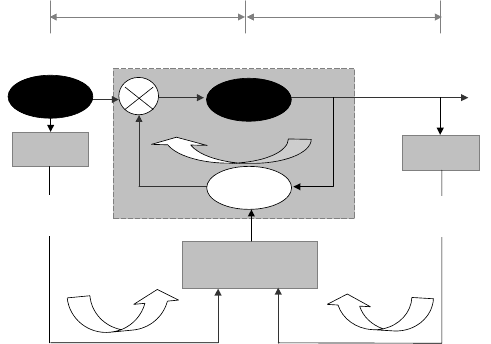
Fig. 15.1. Model of the PASS: a semi-automatic system with three feedback loops.
The PASS consists of the following modules: cameras in the
visible and IR bands placed at two levels of observation, processors of
preliminary information and online data, the knowledge domain converter
for interpretation of data from the signal domain and manipulation of
data in semantic form, and a personal file generating module. Two-level
surveillance is used in the system: pre-screening and the screening of
an individual. The protocol of a personal file includes (a) preliminary
information using surveillance during pre-screening of individuals in a
line/gate in the visible and IR bands, and (b) information extracted from
observation, conversation, and available additional sources during screening
itself, or authorization procedure.
Note that biometrics such as iris and retinal patterns, ear and face
recognition require high resolution images. A typical surveillance camera
often captures poor quality, low resolution images. From this point of view,
gait biometrics prove convenient.
In PASS, each of the biometric devices automatically generates a local
decision making outcome corresponding to local levels of the hierarchy of
decision making. These decisions are stored and processed by knowledge-
intensive techniques to support the officer. This biometric information
should be simulated in the training system. To this end, so-called hybrid
data are used; that is, real, synthetic, and mixed biometric data
[
48,50
]
.

April 2, 2007 14:42 World Scientific Review Volume - 9in x 6in Main˙WorldSc˙IPR˙SAB
Fundamentals of Biometric-Based Training System Design 375
Two groups of biometric devices are used in the system: devices
for the collection and processing of early warning biometric data about
the individual-A, and devices for processing of biometric data from the
individual-B. These data are represented in the signal domain. The
converter transforms biometric features from the signal domain to the
knowledge domain and generates supporting questions for the officer. The
officer follows his/her own scenario of authorization (question/answer). The
questions generated by the convertor are defined as supporting data, and
can be used or not by the officer in the dialogue.
Three feedback loops address the three main data flows: the main flow
(loop 1), where the professional skills of personnel play the key role, and
supporting flows (loops 2 and 3), where biometric data are processed and
decisions on detection or recognition of various patterns are automated.
Table 15.2. Functions of feedback loops in the PASS model.
LOOP DESIGN AND IMPLEMENTATION
1
Experience of the officer in interviewing supported by
knowledge-based technology
2
Non-contact biometrics in visible and IR bands, representation
of pattern in semantic form.
3
Non-contact and contact biometrics; representation of
patterns in semantic form.
The following properties of the screening procedure of service are utilized
in the PASS and in the training system (Fig. 15.2):
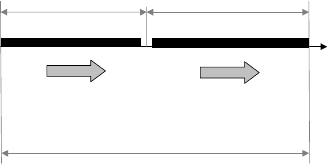
Property 1. Two phase service, where the interval of service T can be
divided into two subintervals T
1
and T
2
. The first phase T
1
(pre-screening)
is suitable for obtaining early warning information using surveillance. At
the second phase, T
2
, available sources of information are used to identify
and authorize an individual.
Property 2. There is a distance between the individual and the
registration desk. This distance can be used to obtain extra information
using video and IR surveillance, and, thus, facial, IR, and gait biometrics.
The above model can be interpreted from various perspectives in
complex system design, in particular, from learning knowledge-based
systems, adaptive knowledge-based systems, and cognitive systems
[
14,10
]
.
April 2, 2007 14:42 World Scientific Review Volume - 9in x 6in Main˙WorldSc˙IPR˙SAB
376 Synthesis and Analysis in Biometrics
Time for early warning T
1
Accumulated pre-
screening information
about the individual
Accumulated information
from all available sources
at the check point
Time for decision making T
2
Time of service T
1
+T
2
t
Fig. 15.2. Screening during time T : time of service includes of early warning time T
1
(pre-screening) and check-point time T
2
.
15.2.3. Biometrics
The most important feature of the PASS is the hierarchical distribution
of biometrics in the system; that is, various types of biometric devices
are embedded into PASS with respect to architectural, topological, and
functional properties. This is a necessary condition for implementation of
the early warning paradigm in the access control system.
Biometrics provide many sources of information that can be classified
with respect to various criteria; in particular, spectral criteria (visible,
IR, and acoustic), behavioural and inherent criteria, contact and non-
contact, correlation factors between various biometrics (multi-biometric)
[
22,23,42,53,54
]
, computing indirect characteristics and parameters such as
drug and alcohol consumption, blood pressure, breathing function, and
temperature using the IR band
[
16,33,46
]
,emotion
[
44
]
, psychological
features and gender
[
15,29
]
, and implementation. In T-PASS, these
criteria are used to satisfy the topological and architectural requirements of
the system, machine-human interaction, computing a correlation between
biometric patterns.
We also utilize the correlation between various biometrics. Traditionally,
the correlation is calculated in the signal domain, for example, between
facial images in the visible and IR bands
[
9,43,44
]
. The correlation between
biometrics can be represented in semantic form (knowledge domain). For
this, biometric features generated by different biometric devices in the signal
domain are converted into the knowledge domain, where their correlation
in semantic form is evaluated.
Example 21. The correlation between handwriting, signature, stroke
dynamics, facial features, and gait can be represented in semantic form
as some special conditions (for example, drunkenness or drug affection,
physical condition or disability, emotional state, gender, and others)
(Fig. 15.3). The advantages to this are: acceptability for humans,
April 2, 2007 14:42 World Scientific Review Volume - 9in x 6in Main˙WorldSc˙IPR˙SAB
Fundamentals of Biometric-Based Training System Design 377
adaptation for different biometrics, and the possibility of compensating
for the unreliability of biometric data by using fusion from several sources
combined with high-level description.
Handwritin
g
Signatur
e
Stroke-dynami
c
Facia
l
features
Gai
t
Physiological
condition
Gender
Emotional
state
Correlation
Biometric
features
Indirect
characteristics
Fig. 15.3. Correlation of biometric feature are described in semantic form using
knowledge representations and indirect computing.
Acoustic domain
In the acoustic domain (Fig. 15.4), the pitch, loudness and timbre of an
individual’s voice are the main relevant parameters. For analysis and
synthesis, the most important frequency range is 70 to 200 Hz for men,
150 to 400 Hz for women, and 200 to 600 Hz for children. Several
levels of speech description are used: representations in the acoustic,
phonetic, phonological (speech is described in linguistic units, phonemes),
morphological (phonemes combine to form words), syntactic (restricted
by the rules of syntax), and semantic (semantic features are attached to
words giving the sentence meaning) domains. Each of these levels can
be used to extract behavioural information from speech. Voice carries
emotional information by intonation.Thevoice tension technology utilizes
varying degrees of vibration in the voice to detect emotional response in
dialogue (certain languages require exceptional treatment, as for example,
in Chinese, intonation carries semantic information: four tones distinguish
otherwise identical words with different meanings from each other).
Infrared band
Early warning and detection using IR imaging is considered to be a key to
mitigating service time and incidents. Techniques of IR imagery have been
studied with respect to many applications, including tracking faces
[
12
]
,and
detecting inflamed regions
[
16,38,44
]
. It is well documented that the human
body generates waves over a wide range of the electromagnetic spectrum,
from 10
−1
Hz (resonance radiation) to 10
9
Hz (human organs) (Fig. 15.4).
The human face and body emit IR light both in the mid-IR (3–5 µm) and
