FitzGerald J., Dennis A., Durcikova A. Business Data Communications and Networking
Подождите немного. Документ загружается.


QUESTIONS 65
Electronic Mail With email, users create and send messages using an application-layer software
package on client computers called user agents. The user agent sends the mail to a server running an
application-layer software package called a mail transfer agent, which then forwards the message
through a series of mail transfer agents to the mail transfer agent on the receiver’s server. Email is
faster and cheaper than regular mail and can substitute for telephone conversations in some cases.
Several standards have been developed to ensure compatibility between different user agents and
mail transfer agents such as SMTP, POP, and IMAP.
KEY TERMS
application architecture
application logic
client-based architecture
client-server architecture
cloud computing
cluster
data access logic
data storage
desktop videoconferencing
distributed computing
model
dumb terminal
email
green computing
H.320
H.323
host-based architecture
HTTP request
HTTP response
Hypertext Markup
Language (HTML)
Hypertext Transfer
Protocol (HTTP)
instant messaging (IM)
Internet
Internet Message Access
Protocol (IMAP)
mail transfer agent
mail user agent
mainframe
middleware
MPEG-2
Multipurpose Internet
Mail Extension (MIME)
network computer
n-tier architecture
peer-to-peer architecture
personal computer
Post Office Protocol
(POP)
presentation logic
protocol
request body
request header
request line
response body
response header
response status
scalability
server virtualization
Simple Mail Transfer
Protocol (SMTP)
SMTP header
SMTP body
Telnet
terminal
thick client
thin client
three-tier architecture
transaction terminal
two-tier architecture
uniform resource locator
(URL)
videoconferencing
virtual server
World Wide Web
Web browser
Webcasting
Web server
QUESTIONS
1. What are the different types of appli-
cation architectures?
2. Describe the four basic functions of an
application software package.
3. What are the advantages and disadvan-
tages of host-based networks versus
client-server networks?
4. What is middleware, and what does it do?
5. Suppose your organization was con-
templating switching from a host-based
architecture to client-server. What prob-
lems would you foresee?
6. Which is less expensive: host-based networks
or client-server networks? Explain.
7. Compare and contrast two-tier, three-tier, and
n-tier client-server architectures. What are the
technical differences, and what advantages
and disadvantages does each offer?
8. How does a thin client differ from a thick client?
9. What is a network computer?
10. For what is HTTP used? What are
its major parts?
11. For what is HTML used?
12. Describe how a Web browser and Web server
work together to send a Web page to a user.
13. Can a mail sender use a 2-tier architec-
ture to send mail to a receiver using a
3-tier architecture? Explain.
14. Describe how mail user agents and mail transfer
agents work together to transfer mail messages.
15. What roles do SMTP, POP, and IMAP play in
sending and receiving email on the Internet?

66 CHAPTER 2 APPLICATION LAYER
16. What are the major parts of an email message?
17. What is a virtual server?
18. What is Telnet, and why is it useful?
19. What is cloud computing?
20. Explain how instant messaging works.
21. Compare and contrast the application
architecture for videoconferencing and
the architecture for email.
22. Which of the common application archi-
tectures for email (two-tier client server,
Web-based) is “best”? Explain.
23. Some experts argue that thin-client client-server
architectures are really host-based architec-
tures in disguise and suffer from the same old
problems. Do you agree? Explain.
EXERCISES
2-1. Investigate the use of the major architectures by
a local organization (e.g., your university). Which
architecture(s) does it use most often and what does
it see itself doing in the future? Why?
2-2. What are the costs of thin client versus thick client
architectures? Search the Web for at least two differ-
ent studies and be sure to report your sources. What
are the likely reasons for the differences between the
two?
2-3. Investigate the costs of dumb terminals, network
computers, minimally equipped personal comput-
ers and top-of-the-line personal computers. Many
equipment manufacturers and resellers are on the
Web, so it’s a good place to start looking.
2-4. What application architecture does your university
use for email? Explain.
MINI-CASES
I. Deals-R-Us Brokers (Part 1)
Fred Jones, a distant relative of yours and president of Deals-R-Us Brokers (DRUB), has come to you for advice.
DRUB is a small brokerage house that enables its clients to buy and sell stocks over the Internet, as well as
place traditional orders by phone or fax. DRUB has just decided to offer a set of stock analysis tools that will
help its clients more easily pick winning stocks, or so Fred tells you. Fred’s information systems department
has presented him with two alternatives for developing the new tools. The first alternative will have a special
tool developed in C++ that clients will download onto their computers to run. The tool will communicate with
the DRUB server to select data to analyze. The second alternative will have the C++ program running on the
server, the client will use his or her browser to interact with the server.
a. Classify the two alternatives in terms of what type of application architecture they use.
b. Outline the pros and cons of the two alternatives and make a recommendation to Fred about which
is better.
II. Deals-R-Us Brokers (Part 2)
Fred Jones, a distant relative of yours and president of Deals-R-Us Brokers (DRUB), has come to you for advice.
DRUB is a small brokerage house that enables its clients to buy and sell stocks over the Internet, as well as
place traditional orders by phone or fax. DRUB has just decided to install a new email package. One vendor is

HANDS-ON ACTIVITY 2A 67
offering an SMTP-based two-tier client-server architecture. The second vendor is offering a Web-based email
architecture. Fred doesn’t understand either one but thinks the Web-based one should be better because, in his
words, “The Web is the future.”
a. Briefly explain to Fred, in layperson’s terms, the differences between the two.
b. Outline the pros and cons of the two alternatives and make a recommendation to Fred about which
is better.
III. Accurate Accounting
Diego Lopez is the managing partner of Accurate Accounting, a small accounting firm that operates a dozen
offices in California. Accurate Accounting provides audit and consulting services to a growing number of small-
and medium-sized firms, many of which are high technology firms. Accurate Accounting staff typically spend
many days on-site with clients during their consulting and audit projects, but has increasingly been using email
and Instant Messenger (IM) to work with clients. Now, many firms are pushing Accurate Accounting to adopt
videoconferencing. Diego is concerned about what videoconferencing software and hardware to install. While
Accurate Accounting’s email system enables it to exchange email with any client, using IM has proved difficult
because Accurate Accounting has had to use one IM software package with some companies and different IM
software with others. Diego is concerned that videoconferencing may prove to be as difficult to manage as IM.
“Why can’t IM work as simply as email?” he asks. “Will my new videoconferencing software and hardware
work as simply as email, or will it be IM all over again?” Prepare a response to his questions.
IV. Ling Galleries
Howard Ling is a famous artist with two galleries in Hawaii. Many of his paintings and prints are sold to tourists
who visit Hawaii from Hong Kong and Japan. He paints 6–10 new paintings a year, which sell for $50,000
each. The real money comes from the sales of prints; a popular painting will sell 1,000 prints at a retail price
of $1,500 each. Some prints sell very quickly, while others do not. As an artist, Howard paints what he wants
to paint. As a businessman, Howard also wants to create art that sells well. Howard visits each gallery once a
month to talk with clients, but enjoys talking with the gallery staff on a weekly basis to learn what visitors say
about his work and to get ideas for future work. Howard has decided to open two new galleries, one in Hong
Kong and one in Tokyo. How can the Internet help Howard with the two new galleries?
CASE STUDY
NEXT-DAY AIR SERVICE
See the Web site.
HANDS-ON ACTIVITY 2A
Looking Inside Your HTTP Packets
Figures 2.9 and 2.10 show you inside one HTTP request
and one HTTP response that we captured. The objective
of this Activity is for you to see inside HTTP packets that
you create.
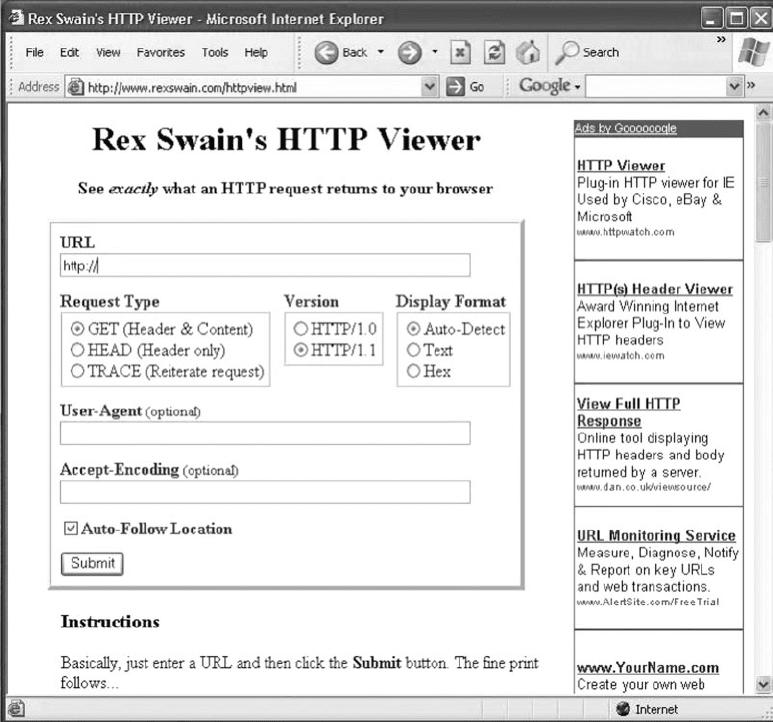
68 CHAPTER 2 APPLICATION LAYER
1. Use your browser to connect to www.rexswain
.com/httpview.html. You will see the screen in
Figure 2.17.
2. In box labeled URL, type any URL you like and
click Submit. You will then see something like the
screen in Figure 2.18. In the middle of the screen,
under the label “Sending Request:” you will see the
exact HTTP packet that your browser generated.
3. If you scroll this screen down, you’ll see the exact
HTTP response packet that the server sent back to
you. In Figure 2.19, you’ll see the response from
the Indiana University Web server. You’ll notice
FIGURE 2.17 The HTTP Viewer
that at the time we did this, Indiana University
was using the Apache Web server.
4. Try this on several sites around the Web to see
what Web server they use. For example, Microsoft
uses the Microsoft IIS Web server, while Cisco
uses Apache. Some companies set their Web
servers not to release this information.
Deliverables
Do a print screen from two separate Web sites that shows
your HTTP requests and the servers’ HTTP responses.
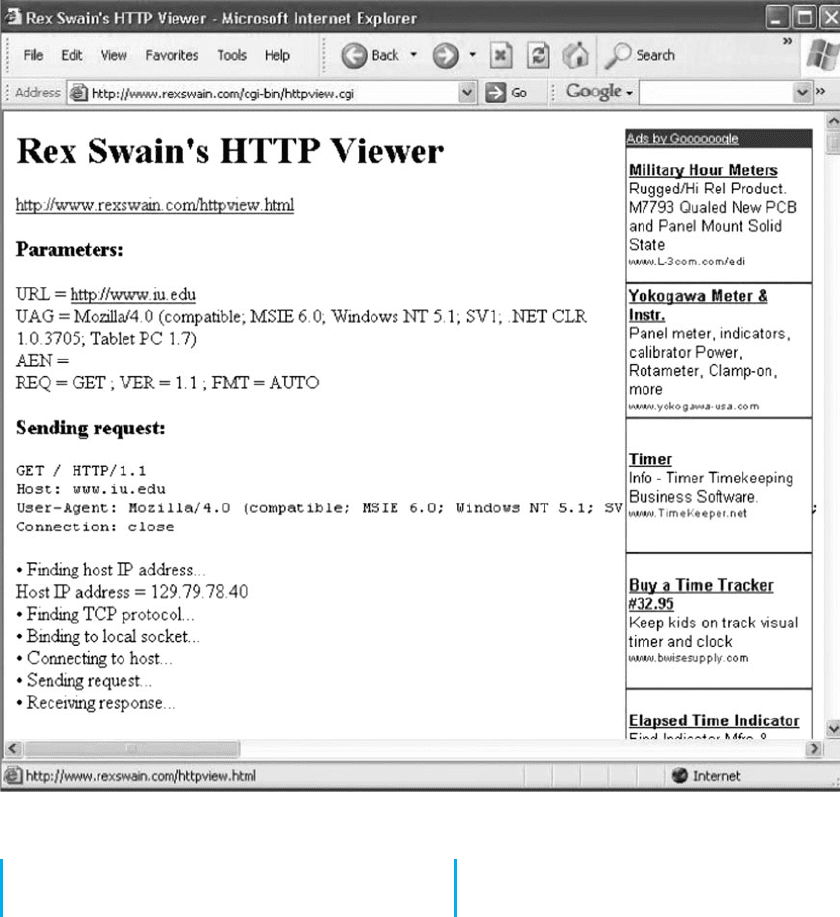
HANDS-ON ACTIVITY 2B 69
FIGURE 2.18 Looking inside an HTTP request
HANDS-ON ACTIVITY 2B
Tracing Your Email
Most email today is spam, unwanted commercial email, or
phishing, fake email designed to separate you from your
money. Criminals routinely send fake emails that try to
get you to tell them your log-in information for your bank
or your PayPal account, so they can steal the information,
log-in as you, and steal your money.
It is very easy to fake a return address on an email,
so simply looking to make sure that an email has a
valid sender is not sufficient to ensure that the email was
actually sent by the person or company that claims to
have sent it. However, every SMTP email packet con-
tains information in its header about who actually sent the
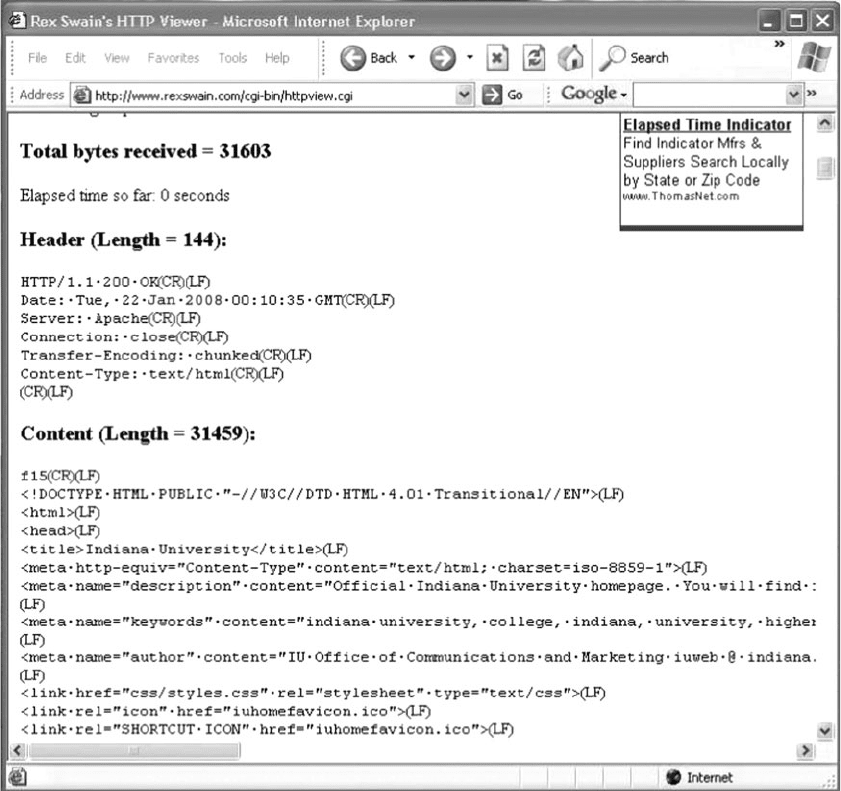
70 CHAPTER 2 APPLICATION LAYER
FIGURE 2.19 Looking inside an HTTP response
email. You can read this information yourself, or you can
use a tool designed to simplify the process for you. The
objective of this Activity is for you to trace an email you
have received to see i f the sending address on the email
is actually the organization that sent it.
There are many tools you can use to trace your email.
We like a tool called eMail Tracker Pro, which has a free
version that lasts 15 days.
1. Go to www.emailtrackerpro.com and download
and install eMail Tracker Pro.
2. Login to your email and find an email message
you want to trace. I recently received an email
supposedly from Wachovia Bank; the sender’s
email address was aw-login@wachovia.com.
3. After you open the email, find the option that
enables you to view the Internet header or source
of the message (in Microsoft Outlook, click the
Options tab and look at the bottom of the box that
pops up). Figure 2.20 shows the email I received
and how to find the SMTP header (which Outlook
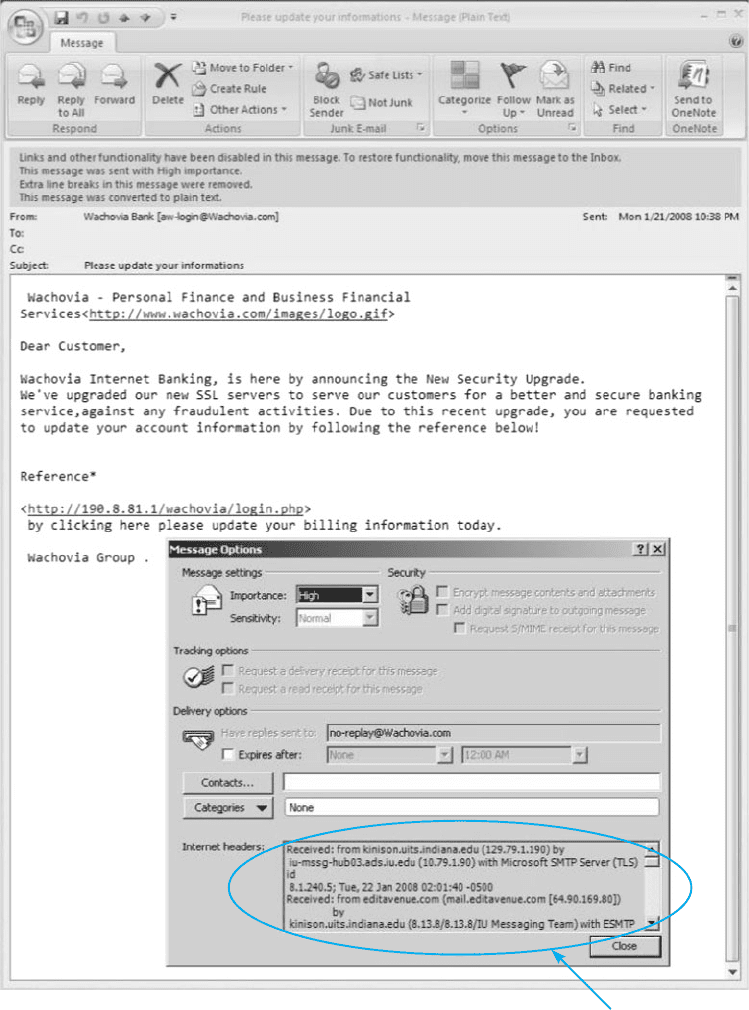
HANDS-ON ACTIVITY 2B 71
Internet headers
FIGURE 2.20 Viewing the SMTP packet header
72 CHAPTER 2 APPLICATION LAYER
calls the Internet header). Copy the entire SMTP
header to the clipboard.
4. Start eMail Tracker Pro. Select Trace an email,
and paste the SMTP header into the box provided.
Click Trace to start the trace.
5. It may take up to 30 seconds to trace the email,
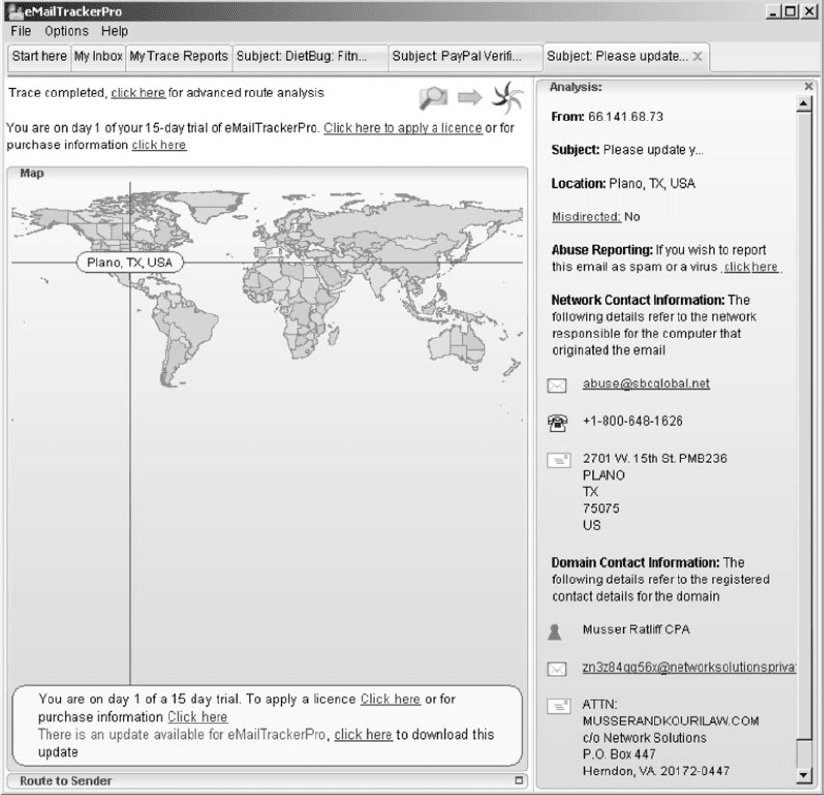
so be patient. Figure 2.21 shows the results from
the email I received. The email supposedly from
Wachovia Bank was actually from a company
named Musser and Kouri Law whose primary
FIGURE 2.21 Viewing the source of the SMTP packet
contact is Musser Ratliff, CPA, which uses SBC in
Plano, Texas, as its Internet service provider. We
suspect that someone broke into this company’s
network and used their email server without per-
mission, or fraudulently used this company’s name
and contact information on its domain registration.
Deliverables
Trace one email. Print the original email message and the
trace results.
HANDS-ON ACTIVITY 2C 73
HANDS-ON ACTIVITY 2C
Seeing SMTP and POP PDUs
We’ve discussed about how messages are transferred
using layers and the different protocol data units (PDUs)
used at each layer. The objective of this Activity is for
FIGURE 2.22 SMTP packets in Wireshark
you to see the different PDUs in the messages that
you send. To do this, we’ll use Wireshark, which is
one of the world’s foremost network protocol analyzers,
74 CHAPTER 2 APPLICATION LAYER
and is the de facto standard that most professional and
education institutions use today. It is used for network
troubleshooting, network analysis, software and commu-
nications protocol development, and general education
about how networks work. Wireshark enables you to see
all messages sent by your computer and may also let
you see the messages sent by other users on your LAN
(depending on how your LAN is configured).
For this activity you can capture your own SMTP
and POP packets using Wireshark, or use two files that
we’ve created by capturing SMTP and POP packets. We’ll
assume you’re going to use our files. If you’d like to cap-
ture your own packets, read Hands-On Activity 1B in
Chapter 1 and use your two-tier email client to create and
send an email message instead of your Web browser. If
you’d like to use our files, go to the Web site for this
book and download the two files: SMTP Capture.pkt and
POP3 Capture.pkt.
Part 1: SMTP
1. Start Wireshark and either capture your SMTP
packets or open the file called SMTP Capture.pkt.
2. We used the email software on our client com-
puter to send an email message to our email server.
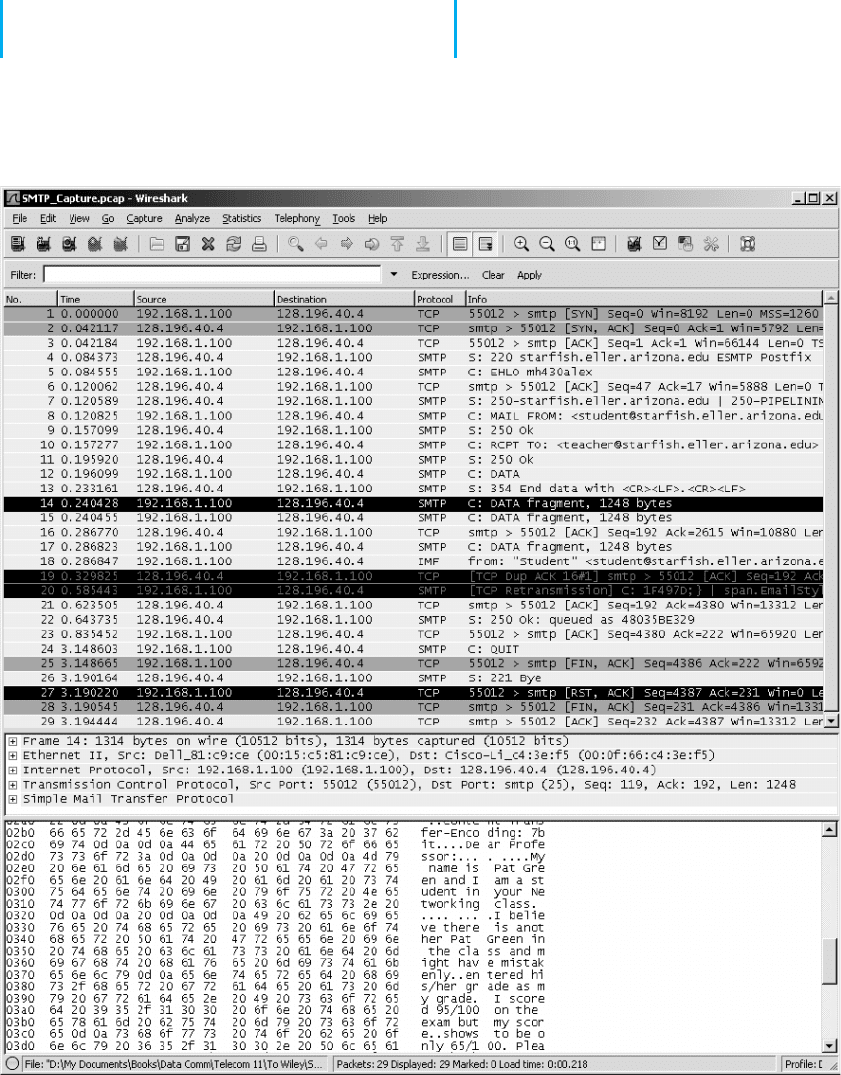
Figure 2.22 shows the packets we captured that
were sent to and from the client computer (called
192.168.1.100) and the server (128.196.40.4) to
send this message from the client to the server.
The first few packets are called the handshake,
as the client connects to the server and the server
acknowledges it is ready to receive a new email
message.
3. Packet 8 is the start of the email message that iden-
tifies the sender. The next packet from the client
(packet 10) provides the recipient address and then
the email message starts with the DATA command
(packet 12) and is spread over several packets ( 14,
15, and 17) because it is too large to fit in one Eth-
ernet frame. (Remember that the sender’s transport
layer breaks up large messages into several smaller
TCP segments for transmission and the receiver’s
transport layer reassembles the segments back into
the one SMTP message.)
4. Packet 14 contains the first part of the message
that the user wrote. It’s not that easy to read, but
by looking in the bottom window, you can see
what the sender wrote.
Deliverables
1. List the information in the SMTP header (to, from,
date, subject, message ID#).
2. Look through the packets to read the user’s mes-
sage. List the user’s actual name (not her email
address), her birth date, and her SSN.
3. Some experts believe that sending an email mes-
sage is like sending a postcard. Why? How
secure is SMTP email? How could security be
improved?
Part 2: POP
1. Start Wireshark and either capture your SMTP
packets or open the file called POP3 Capture.pkt.
2. We used the email software on our client com-
puter to read an email message that was our
email server. Figure 2.23 shows the packets we
captured that were sent to and from the client
computer (called 128.196.239.91) and the server
(128.192.40.4) to send an email message from the
server to the client. The first few packets are called
the handshake, as the client logs in to the server
and the server accepts the log in.
3. Packet 12 is the POP STAT command (status) that
asks the server to show the number of email mes-
sages in the user’s mailbox. The server responds in
packet 13 and tells the client there is one message.
4. Packet 16 is the POP LIST command that asks
the server to send the client a summary of email
messages, which it does in packet 17.
5. Packet 18 is the POP RETR command (retrieve)
that asks the server to send message 1 to the client.
Packets 20, 22, and 23 contain the email message.
It’s not that easy to read, but by looking in the bot-
tom window for packet 20, you can see what the
sender wrote. You can also expand the POP packet
in the middle packet detail window (by clicking on
the + box in front of it), which is easier to read.
Deliverables
1. Packets 5 through 11 are the log-in process. Can
you read the user id and passwords? Why or why
not?
2. Look through the packets to read the user’s mes-
sage. List the user’s actual name (not her email
address), her birth date, and her SSN.
