Yanushkevich S.N., Wang P.S.P., Gavrilova M.L., Srihari S.N. (eds.) Image Pattern Recognition. Synthesis and Analysis in Biometrics
Подождите немного. Документ загружается.

April 2, 2007 14:42 World Scientific Review Volume - 9in x 6in Main˙WorldSc˙IPR˙SAB
258 Synthesis and Analysis in Biometrics
his behavior. The aim is to minimize the enrollment time as much as
possible without affecting the accuracy of the system in detection mode.
Since the key codes do not reflect the relation between the keys like their
absolute or relative positions, the pre processing stage (Fig. 10.9) should
include a mapping mechanism in order to convert those sets of keystrokes
into numbers, which are suitable to train the network with. Such numbers
should reflect a specific characteristic for each key and its relation to other
keys. The mapping method used in the previous technique is a binary
mapping since each key is represented by its own network input, and the
effect of other keys was removed by restricting the input to only one high
input at a time. This technique is considered to involve high computation
power requirement, since the number of nodes in the neural network is
large.
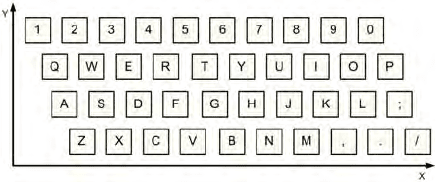
The second approach we propose is based on a keyboard layout mapping
technique. The function of this technique is to replace each key code by its
location on a previously identified keyboard layout. In our implementation
we use the QWERTY keyboard layout depicted by Fig. 10.11
Fig. 10.11. QWERTY Keyboard layout can be used to encode keys as input to the
neural network.
Each key will be presented by a pair of numbers representing its x and
y location. Neural networks can still be used to model the relation between
the keys and the time used to move between them.
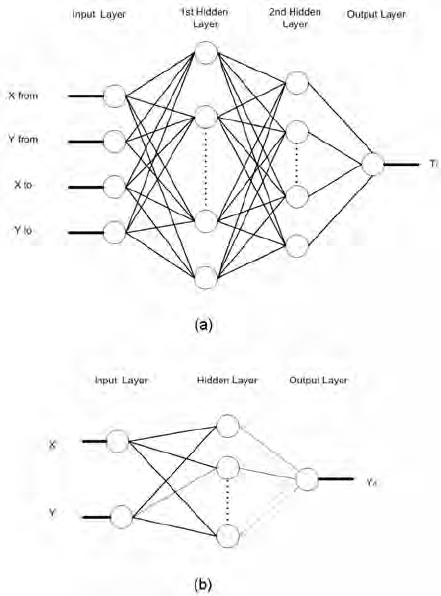
Figures 10.12(a) and 10.12(b) show the neural networks used for the
digraph and monograph analysis respectively. The networks in this case
are lighter than the one used in the previous technique. The numbers of
input nodes are 2 and 4 for each network respectively as only 2 network
inputs are needed to represent a key. The hidden layers consist of 5 nodes
for the monograph network and 12 nodes for the digraph network.
April 2, 2007 14:42 World Scientific Review Volume - 9in x 6in Main˙WorldSc˙IPR˙SAB
Behavioral Biometrics for Online Computer User Monitoring 259
Fig. 10.12. Neural Networks used for free text detection based on keyboard layout
mapping: (a) Digraph Analysis and (b) Dwell Time Analysis.
10.4.4. Free Text detection Based on Sorted Time Mapping
Another mapping technique, which can be used to prepare the data for
the neural network is to sort the key codes based on associated average
time, and accordingly to map them with corresponding order. For the
monographs set, the average time is the dwell time. So, in this case the key
codes will be sorted according to the average dwell time. Key codes will
be mapped to their order in the sorted list before being fed to the neural
network. In this case the mono network will have only one input node. For
the digraph set the sorting order is different. Digraphs will be sorted two
times: the first time they will be sorted according to the average of the
times of all digraphs with the same code in the from-key; the second time
they will be sorted according to the average of the to-key. A key code will
April 2, 2007 14:42 World Scientific Review Volume - 9in x 6in Main˙WorldSc˙IPR˙SAB
260 Synthesis and Analysis in Biometrics
be mapped to its sort order according to whether it is to or from. The input
layer for the neural network in this case consists of two nodes.
The keyboard layout mapping technique doesn’t require a full coverage
of all possible set of keys as it is based on a very definite reference
scheme, which is the keyboard layout. So missing a number of keys
during enrollment phase does not prevent this technique from working.
However, for the sorting technique it is mandatory that the user provide
input at enrollment phase covering the whole set of monitored keys. This
criterion makes the approximation matrix technique and the keyboard
layout technique more suitable if the system is designed to hide the
enrollment process from the user. The sorting technique will be very
effective if a controlled enrollment procedure is used.
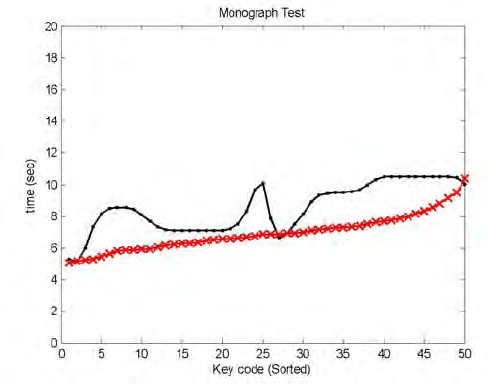
Fig. 10.13. Comparing signatures (Monograph Analysis): User 2’s session compared to
user 1’s reference signature.
Figure 10.13 shows monographs signatures for two different users. The
figure shows the relation between the key code, and the dwell time involved.
The sequence of the keys represented by those codes is different for each user
as they were sorted for each user individually. The Y-axis represents the
output of the neural network after it has been trained with the sorted key
order. Taking a look again at Fig. 10.9, the output of the behavior-modeling
component in this case is equivalent to the curve shown in Fig. 10.13 for
monograph analysis and to a set of curves or a 3-D matrix for digraph
analysis.
April 2, 2007 14:42 World Scientific Review Volume - 9in x 6in Main˙WorldSc˙IPR˙SAB
Behavioral Biometrics for Online Computer User Monitoring 261
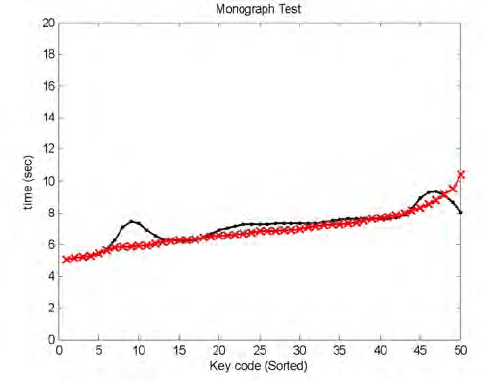
Fig. 10.14. Comparing signatures (Monograph Analysis): User 1’s session compared to
user 1’s reference signature.
Figure 10.14 shows Monograph signature calculated from one of user
1’s sessions compared to his reference signature. Figure 10.13 shows the
signature calculated for one of user 2’s sessions during detection mode as a
result of supplying his session data to User 1’s neural network. We can note
from the figure that the difference between this curve and user 1’s reference
signature is high compared to the difference between user 1’s curves.
10.5. Conclusion
Biometric systems are widely deployed to ensure security in a large
spectrum of today’s industries. Some implementations rely solely on
biometrics; others utilize it to increase their level of security. The choice
to implement a specific biometric technology in an environment is ruled by
a number of factors. Examples of those factors are its accuracy, cost, user
acceptance, and stability on the long term.
In this chapter we present methods based on statistical and artificial
intelligence techniques targeting the use of behavioural biometrics for online
computer user monitoring. The techniques presented in this chapter work
on a large set of features from a newly introduced biometric (mouse
dynamics) and the keystroke dynamics biometric without putting any
restriction on the user at any stage of operation making it suitable for online
April 2, 2007 14:42 World Scientific Review Volume - 9in x 6in Main˙WorldSc˙IPR˙SAB
262 Synthesis and Analysis in Biometrics
identity verification and detection applications. As those biometrics gain
high acceptability they also gain a relatively high accuracy. In experiments
conducted in our lab, we achieve an overall accuracy of FAR =0.00651,
and FRR =0.01312. This is based on a number of experiments conducted
locally and remotely through our lab involving a set of 22 participants.
Acknowledgments
This work was partly supported by the Natural Science and Engineering
Research Council of Canada (NSERC) through an Idea-to-Innovation grant.
We would like to thank all the participants in the experimental evaluation
of our framework, as well the Innovation Development Corporation of the
University of Victoria for their support. We would like also to thank Dr
Svetlana Yanushkevich for her review and valuable comments on this work.
Bibliography
1. Ahmed, A. A. E. and Traor´e, I. (2005). Detecting computer intrusions using
behavioural biometrics, Proc. 3rd Annual Conf. Privacy, Security and Trust,
New Brunswick, Canada, pp. 91–98.
2. Ahmed, A. A. E. and Traor´e, I. (2003). System and method for determining
a computer user profile from a motion-based input device. PCT patent
application with the World Intellectual Property Organization,filedbythe
University of Victoria (PCT/CA2004/000669) filing date: 3 May 2004
priority date: 2 May 2003.
3. Bergadano, F., Guneti, D. and Picardi, C. (2002). User authentication
through keystroke dynamics, ACM Trans. Information and System Security,
5, 4 pp. 367–397.
4. Bleha, S., Slivinsky, C. and Hussein, B. (1990). Computer-access security
systems using keystroke dynamics, IEEE Trans. Patt. Anal. Mach. Int. 12,
pp. 1217–1222.
5. Brown, M. and Rogers, S. J. (1993). User Identification Via Keystroke
Characteristics of Typed Names Using Neural Networks. Int. J. Man-
Machine Studies, 39, pp. 999–1014.
6. Coello Coello, C. A. (2006). Evolutionary algorithms: basic concepts and
applications in biometrics, this issue.
7. Denning, D. (1987). An intrusion detection model, IEEE Trans. Software
Engineering, 13, 2, pp. 222–232.
8. Gaines, R., Lisowski, W., Press, S. and Shapiro, N. (1980). Authentication by
keystroke timing: some preliminary results, Rand. Report R-256-NSF. Rand
Corporation.
April 2, 2007 14:42 World Scientific Review Volume - 9in x 6in Main˙WorldSc˙IPR˙SAB
Behavioral Biometrics for Online Computer User Monitoring 263
9. Guneti D. and Picardi, C. (2005). Keystroke analysis of free text, ACM Trans.
Information and System Security, 8, 3, pp. 312–347.
10. Legget, J. and Williams, G. (1988). Dynamic identity verification via
keystroke characteristics, Int. J. Man-Mach. Stud. 35, pp. 859–870.
11. Monrose, F. and Rubin, A. (1997). Authentication via keystroke dynamics,
Proc. 4th ACM Conf. Computer and Communications Security, pp. 48–56.
12. Oel, P., Schmidt, P. and Shmitt, A. (2001). Time prediction of mouse-
based cursor movements, Proc. Joint AFIHM-BCS Conf. Human-Computer
Interaction, 2, pp. 37–40.
13. Parker, J. R. (2006). Composite systems for handwritten signature
recognition, this issue.
14. Popel, D. V. (2006). Signature analysis, verification and synthesis in pervasive
environments, this issue.
15. Whisenand, T. G. and Emurian, H.H. (1999). Analysis of cursor movements
with a mouse. Computers in Human Behavior, 15, pp. 85–103.
16. Whisenand, T. G. and Emurian, H. (1996). Effects of angle of approach on
cursor movement with a mouse: consideration of fitts’ law, Computer in
Human Behavior, 12, 3, pp. 481–495.
17. Yanushkevich, S. N., Stoica, A. and Shmerko, V. P. (2006). Fundamentals of
biometric-based training system design, this issue.
18. Yanushkevich, S. N., Stoica, A., Shmerko, V. P. and Popel, D. V. (2005).
Biometric Inverse Problems, Taylor & Francis/CRC Press.
April 2, 2007 14:42 World Scientific Review Volume - 9in x 6in Main˙WorldSc˙IPR˙SAB
This page intentionally left blankThis page intentionally left blank
April 2, 2007 14:42 World Scientific Review Volume - 9in x 6in Main˙WorldSc˙IPR˙SAB
PART 3
BIOMETRIC SYSTEMS AND
APPLICATIONS
265
April 2, 2007 14:42 World Scientific Review Volume - 9in x 6in Main˙WorldSc˙IPR˙SAB
266
This page intentionally left blankThis page intentionally left blank

April 2, 2007 14:42 World Scientific Review Volume - 9in x 6in Main˙WorldSc˙IPR˙SAB
PART 3
LARGE-SCALE BIOMETRICS
Positive identification and verification
Negative identification and verification
Errors
Performance evaluation
Reliability and selectivity
EVOLUTIONARY ALGORITHMS
Evolutionary strategies
Applications to biometrics
MEASUREMENTS OF BIOMETRICS
Segmentation
Disambiguation
Semantics
HUMAN BIOMETRIC SENSOR INTERFACE
Biometric system performance
Biometric sample quality
Ergonomics in biometric system design
BIOMETRIC-BASED TRAINING SYSTEM
DESIGN
Physical access security systems
Techniques of training estimations
Prototyping
Knowledge-based decision making
support
267
