Nigel S., Chambers S., Johnson R. Operations Management
Подождите немного. Документ загружается.


and the inspectors have to have sufficient knowledge and experience. But whatever approach
to risk is taken, it can only be effective if the organizational culture that it is set in fully sup-
ports a ‘risk-aware’ attitude. This is particularly important where operations are producing
new or uncertain outputs, as in software engineering. Carnegie Mellon University Software
Engineering Institute has identified seven management principles essential to effective risk
management.
3
Table 19.1 is adapted from those principles.
Identify the potential causes of failure
The causes of some failures are purely random, like lightning strikes, and are difficult, if
not impossible, to predict. However, the vast majority of failures are caused by something
that could have been avoided. So, as a minimum starting point, a simple checklist of failure
causes is useful. In fact the root cause of most failure is usually human failure of some type;
nevertheless, identifying failure sources usually requires a more evident set, such as that
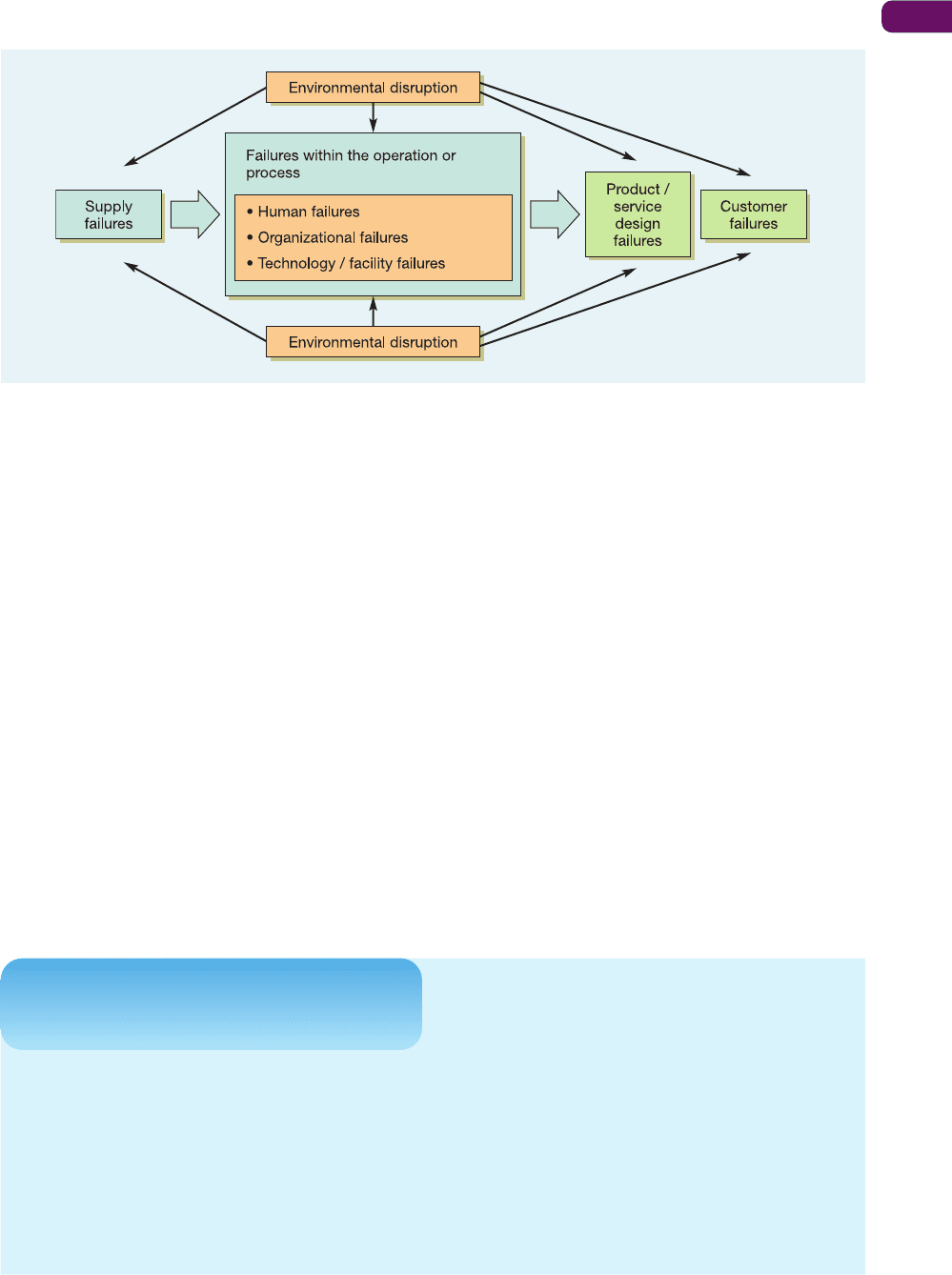
illustrated in Figure 19.3. Here, failure sources are classified as: failures of supply, internal
failures such as those deriving from human organizational and technological sources, failures
deriving from the design of products and services, failures deriving from customer failures,
and general environmental failures.
Supply failure
Supply failure means any failure in the timing or quality of goods and services delivered into
an operation. For example, suppliers delivering the wrong or faulty components, outsourced
call centres suffering a telecoms failure, disruption to power supplies, and so on. It can be
an important source of failure because of increasing dependence on outsourced activities
in most industries. Also, global sourcing usually means that parts are shipped around the
world on their journey through the supply chain. Microchips manufactured in Taiwan could
be assembled to printed circuit boards in Shanghai which are then finally assembled into a
computer in Ireland. At the same time, many industries are suffering increased volatility in
demand. Perhaps most significantly there tends to be far less inventory in supply chains that
could buffer interruptions to supply. According to one authority on supply chain manage-
ment, ‘Potentially the risk of disruption has increased dramatically as the result of a too-narrow
focus on supply chain efficiency at the expense of effectiveness.’
4
Part Four Improvement
574
Table 19.1 The seven management principles essential to effective risk management
Corporate perspective
Forward-looking view
Open communication
Integrated
management
Continuous process
Shared vision
Teamwork
• Viewing developments within the context of strategic goals
• Recognizing both the potential value of opportunity and the potential
impact of adverse effects
• Thinking toward tomorrow, identifying uncertainties, managing project
resources and activities while anticipating uncertainties
• Encouraging free-flowing information at and between all levels
• Enabling formal, informal and impromptu communication
• Using processes that value the individual voice (bringing unique
knowledge and insight to identifying and managing risk)
• Making risk management an integral and vital part of operations
• Adapting risk management methods and tools to a project’s
infrastructure and culture
• Sustaining constant vigilance
• Identifying and managing risks routinely through all phases of change
• Mutual vision based on common purpose, shared ownership and
collective communication
• Focusing on results
• Working cooperatively to achieve common goals
• Pooling talent, skills and knowledge
M19_SLAC0460_06_SE_C19.QXD 10/20/09 9:55 Page 574
Chapter 19 Risk management
575
Figure 19.3 The sources of potential failure in operations
The passengers never knew, and to be fair to the airline the
pilot in question was intercepted before he could fly the
aircraft, but it is unsettling to think about being flown by a
pilot who has been drinking. So, if you are an anxious
flyer, or of a nervous disposition, stop reading now.
It was a dramatic example of human failure increasing
operational risk. The headline ran – ‘Pilot arrested over
alcohol fears!’ Why? A pilot had been arrested after he
had boarded a plane at Heathrow Airport on suspicion
Short case
Not what you want to hear
5
of being drunk. After giving a breath test to police,
the 44-year-old pilot, who worked for the US carrier
United Airlines, was arrested and held on suspicion of
‘performing an aviation function whilst exceeding the
alcohol limit’. Responding to the incident, United Airlines
issued a statement saying that ‘Safety is our number
one priority’ and confirming that the pilot had been
‘removed from duty while we are co-operating with
the authorities and conducting a full investigation’.
A statement released by United Airlines said the
company’s alcohol policy was ‘among the strictest
in the industry. We have no tolerance for abuse or
violations of this well-established policy’, it said.
Human failures
There are two broad types of human failure. The first is where key personnel leave, become
ill, die, or in some way cannot fulfil their role. The second is where people are doing their job
but are making mistakes. Understanding risk in the first type of failure involves identifying
the key people without whom operations would struggle to operate effectively. These are not
always the most senior individuals, but rather those fulfilling crucial roles that require special
skills or tacit knowledge. Human failure through ‘mistakes’ also comes in two types: errors
and violations. ‘Errors’ are mistakes in judgement, where a person should have done some-
thing different. For example, if the manager of a sports stadium fails to anticipate dangerous
crowding during a championship event. ‘Violations’ are acts which are clearly contrary to
defined operating procedure. For example, if a maintenance engineer fails to clean a filter in
the prescribed manner, it is eventually likely to cause failure. Catastrophic failures are often
caused by a combination of errors and violations. For example, one kind of accident, where
an aircraft appears to be under control and yet still flies into the ground, is very rare (once in
two million flights). For this type of failure to occur, first, the pilot has to be flying at the wrong
altitude (error). Second, the co-pilot would have to fail to cross-check the altitude (violation).
Third, air traffic controllers would have to miss the fact that the plane was at the wrong altitude
(error). Finally, the pilot would have to ignore the ground proximity warning alarm in the
aircraft, which can be prone to give false alarms (violation).
Errors
Violations
M19_SLAC0460_06_SE_C19.QXD 10/20/09 9:55 Page 575

Organizational failure
Organizational failure is usually taken to mean failures of procedures and processes and
failures that derive from a business’s organizational structure and culture. This is a huge
potential source of failure and includes almost all operations and process management. In
particular, failure in the design of processes (such as bottlenecks causing system overloading)
and failures in the resourcing of processes (such as insufficient capacity being provided at
peak times) need to be investigated. But there are also many other procedures and processes
within an organization that can make failure more likely. For example, remuneration policy
may motivate staff to work in a way that, although increasing the financial performance of
the organization, also increases the risk of failure. Examples of this can range from sales
people being so incentivized that they make promises to customers that cannot be fulfilled,
through to investment bankers being more concerned with profit than the risks of financial
over-exposure. This type of risk can derive from an organizational culture that minimizes
consideration of risk, or it may come from a lack of clarity in reporting relationships.
Technology and facilities failures
By ‘technology and facilities’ we mean all the IT systems, machines, equipment and buildings
of an operation. All are liable to failure, or breakdown. The failure may be only partial, for
example a machine that has an intermittent fault. Alternatively, it can be what we normally
regard as a breakdown – a total and sudden cessation of operation. Either way, its effects
could bring a large part of the operation to a halt. For example, a computer failure in a super-
market chain could paralyse several large stores until it is fixed.
Product / service design failures
In its design stage, a product or service might look fine on paper; only when it has to cope
with real circumstances might inadequacies become evident. Of course, during the design
process, potential risk of failure should have been identified and ‘designed out’. But one
only has to look at the number of ‘product recalls’ or service failures to understand that
design failures are far from uncommon. Sometimes this is the result of a trade-off between
fast time-to-market performance and the risk of the product or service failing in operation.
And, while no reputable business would deliberately market flawed products or services,
equally most businesses cannot delay a product or service launch indefinitely to eliminate
every single small risk of failure.
Customer failures
Not all failures are (directly) caused by the operation or its suppliers. Customers may ‘fail’
in that they misuse products and services. For example, an IT system might have been
well designed, yet the user could treat it in a way that causes it to fail. Customers are not
‘always right’; they can be inattentive and incompetent. However, merely complaining about
customers is unlikely to reduce the chances of this type of failure occurring. Most organiza-
tions will accept that they have a responsibility to educate and train customers, and to design
their products and services so as to minimize the chances of failure.
Environmental disruption
Environmental disruption includes all the causes of failure that lie outside of an operation’s
direct influence. This source of potential failure has risen to near the top of many firms’
agenda since 11 September 2001 and the global ‘credit crunch’ of 2008. As operations
become increasingly integrated (and increasingly dependent on integrated technologies
such as information technologies), businesses are more aware of the critical events and
malfunctions that have the potential to interrupt normal business activity and even stop the
entire company. Risks in this category include everything from cybercrime to hurricanes,
from terrorism to political change.
Part Four Improvement
576
M19_SLAC0460_06_SE_C19.QXD 10/20/09 9:55 Page 576
Chapter 19 Risk management
577
E-security
7
Any advance in processes or technology creates risks. No real advance comes without
threats and even danger. This applies particularly to e-business. In almost all businesses
information has become critical. So, information security management has become a particu-
larly high priority. But herein lies the problem. The Internet, which is the primary medium
for conducting e-business, is by design an open non-secure medium. Since the original pur-
pose of the Internet was not for commercial purposes, it is not designed to handle secure
transactions. There is a trade-off between providing wider access through the Internet,
and the security concerns it generates. Three developments have amplified e-security con-
cerns. First, increased connectivity (who does not rely on internet-based systems?) means
that everyone has at least the potential to ‘see’ everyone else. Organizations want to make
Happy birthday! 1 May 2008 saw the 30
th
anniversary
of junk electronic mail, or spam as it has become known.
It was in 1978 that Gary Thuerk, a Marketing Executive
at the Digital Equipment Corporation (DEC), a US
mini-computer manufacturer, decided it would be a
great sales ploy to let Arpanet (the direct ancestor of
the Internet) researchers on the west coast of the USA
know that DEC had incorporated the network’s protocols
directly into one of its operating systems. So Thuerk’s
secretary typed in all the researchers’ addresses and
dispatched the message using the e-mail program, which
at the time was very primitive. But not all the recipients
were happy. Arpanet’s rules said that the network could
not be used for commercial purposes and not everyone
wanted to know about the content of the message; it just
seemed intrusive.
Since then unwanted Internet-distributed information
has gone on to irritate, infuriate and threaten the whole
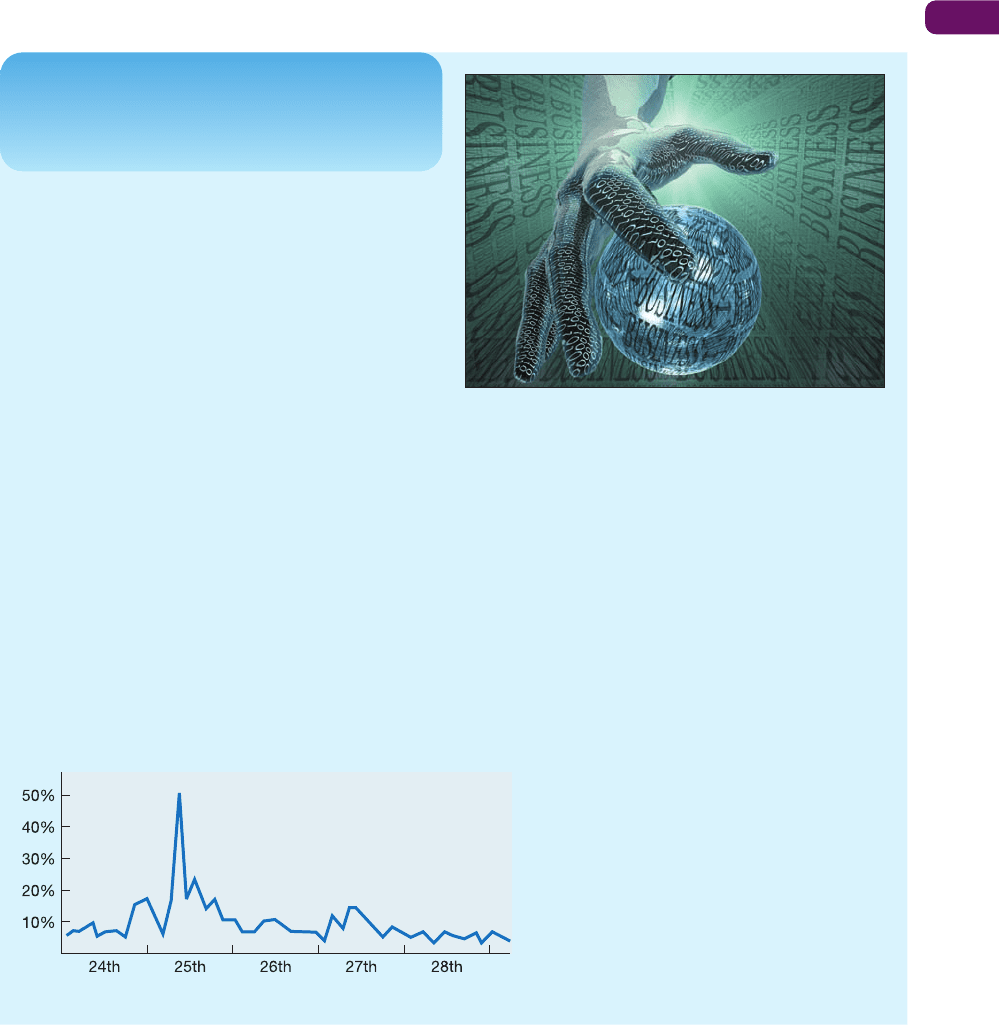
Internet. For example, on 25 January 2003 the ‘SQL
Slammer’ worm, a rogue program, spread at frightening
speed throughout the Internet. It disrupted computers
around the world and, at the height of the attack, its
effect was such that half the traffic over the Internet
was being lost (see Figure 19.4). Thousands of cash
dispensers in North America ceased operating and one
Short case
Viruses, threats and 30 years
of spam
6
police force was driven back to using pencils and paper
when its dispatching system crashed. Yet security experts
believe that the SQL Slammer did more good than harm
because it highlighted weaknesses in Internet security
processes. Like most rogue software, it exploited a flaw
in a commonly used piece of software. Much commonly
used software has security flaws that can be exploited
in this way. Software producers issue ‘patch’ software
to fix flaws but this can actually direct Internet terrorists
to vulnerable areas in the software, and not all systems
managers get around to implementing all patches.
Nevertheless, every rogue program that penetrates
Internet security systems teaches a valuable lesson
to those working to prevent security failures.
Figure 19.4 Internet traffic percentage loss January 2003
Source: Alamy Images
M19_SLAC0460_06_SE_C19.QXD 10/20/09 9:55 Page 577

enterprise systems and information more available to internal employees, business partners
and customers (see Chapter 14 on ERP). Second, there has been a loss of ‘perimeter’ security
as more people work from home or through mobile communications. For example, some
banks have been targeted by criminals seeking to exploit home working, as a hitherto
overlooked flaw in corporate security firewalls. Hackers had hoped to exploit lower levels
of security in home computers to burrow into corporate networks. Third, for some new,
sometimes unregulated, technologies, such as some mobile networks, it takes time to dis-
cover all possible sources of risk. The Internet, after all, is an open system and the rapid rate
of development of new software and systems often means that users do not have an adequate
knowledge about software and systems architecture. This makes users oblivious to potential
vulnerabilities that can lead to serious security breaches.
Yet there is an increasing customer awareness of data security and data confidentiality
which means that companies are viewing e-business security as a potential marketing
advantage. One specialist in this area, Forrester Research, reported that 74 per cent of online
consumers said that online security is an important consideration in choosing a financial
service provider.
Post-failure analysis
One of the critical activities of operations and process resilience is to understand why a
failure has occurred. This activity is called ‘post-failure analysis’. It is used to uncover the
root cause of failures. This includes such activities as the following.
● Accident investigation, where large-scale national disasters like oil tanker spillages and
aeroplane accidents are investigated using specifically trained staff.
● Failure traceability, where procedures ensure that failures can be traced back to where they
originated.
● Complaint analysis, where complaints (and compliments) are used as a valuable source
for detecting the root causes of failures of customer service.
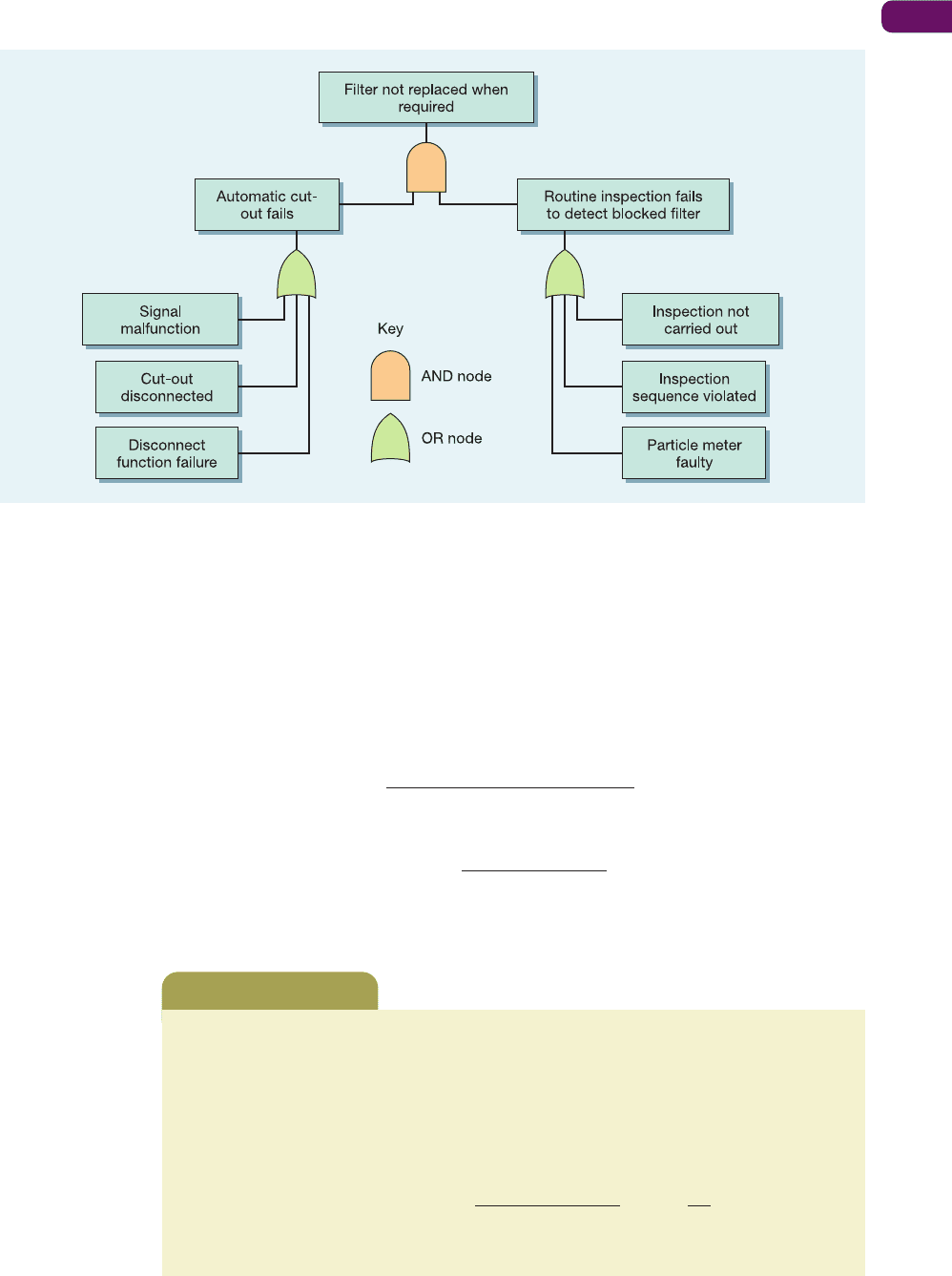
● Fault tree analysis, where a logical procedure starts with a failure or a potential failure
and works backwards to identify all the possible causes and therefore the origins of that
failure. Fault tree analysis is made up of branches connected by two types of nodes: AND
nodes and OR nodes. The branches below an AND node all need to occur for the event
above the node to occur. Only one of the branches below an OR node needs to occur for the
event above the node to occur. Figure 19.5 shows a simple tree identifying the possible
reasons for a filter in a heating system not being replaced when it should have been.
Likelihood of failure
The difficulty of estimating the chance of a failure occurring varies greatly. Some failures
are well understood through a combination of rational causal analysis and historical per-
formance. For example a mechanical component may fail between 10 and 17 months of
its installation in 99 per cent of cases. Other types of failure are far more difficult to predict.
The chances of a fire in a supplier’s plant are (hopefully) low, but how low? There will be
some data concerning fire hazards in this type of plant, but the estimated probability of
failure will be subjective.
‘Objective’ estimates
Estimates of failure based on historical performance can be measured in three main ways:
failure rates – how often a failure occurs; reliability – the chances of a failure occurring;
and availability – the amount of available useful operating time. ‘Failure rate’ and ‘reliability’
are different ways of measuring the same thing – the propensity of an operation, or part
of an operation, to fail. Availability is one measure of the consequences of failure in the
operation.
Part Four Improvement
578
M19_SLAC0460_06_SE_C19.QXD 10/20/09 9:55 Page 578
Failure rate
Chapter 19 Risk management
579
Failure rate
Failure rate (FR) is calculated as the number of failures over a period of time. For example,
the security of an airport can be measured by the number of security breaches per year, and
the failure rate of an engine can be measured in terms of the number of failures divided by
its operating time. It can be measured either as a percentage of the total number of products
tested or as the number of failures over time:
FR =×100
or
FR =
number of failures
operating time
number of failures
total number of products tested
Figure 19.5 Fault tree analysis for failure to replace filter when required
A batch of 50 electronic components is tested for 2,000 hours. Four of the components
fail during the test as follows:
Failure 1 occurred at 1,200 hours
Failure 2 occurred at 1,450 hours
Failure 3 occurred at 1,720 hours
Failure 4 occurred at 1,905 hours
Failure rate (as a percentage) =×100 =×10 = 8%
The total time of the test = 50 × 2,000 = 100,000 component hours
4
50
number of failures
number tested
Worked example
➔
M19_SLAC0460_06_SE_C19.QXD 10/20/09 9:55 Page 579
Bath-tub curves
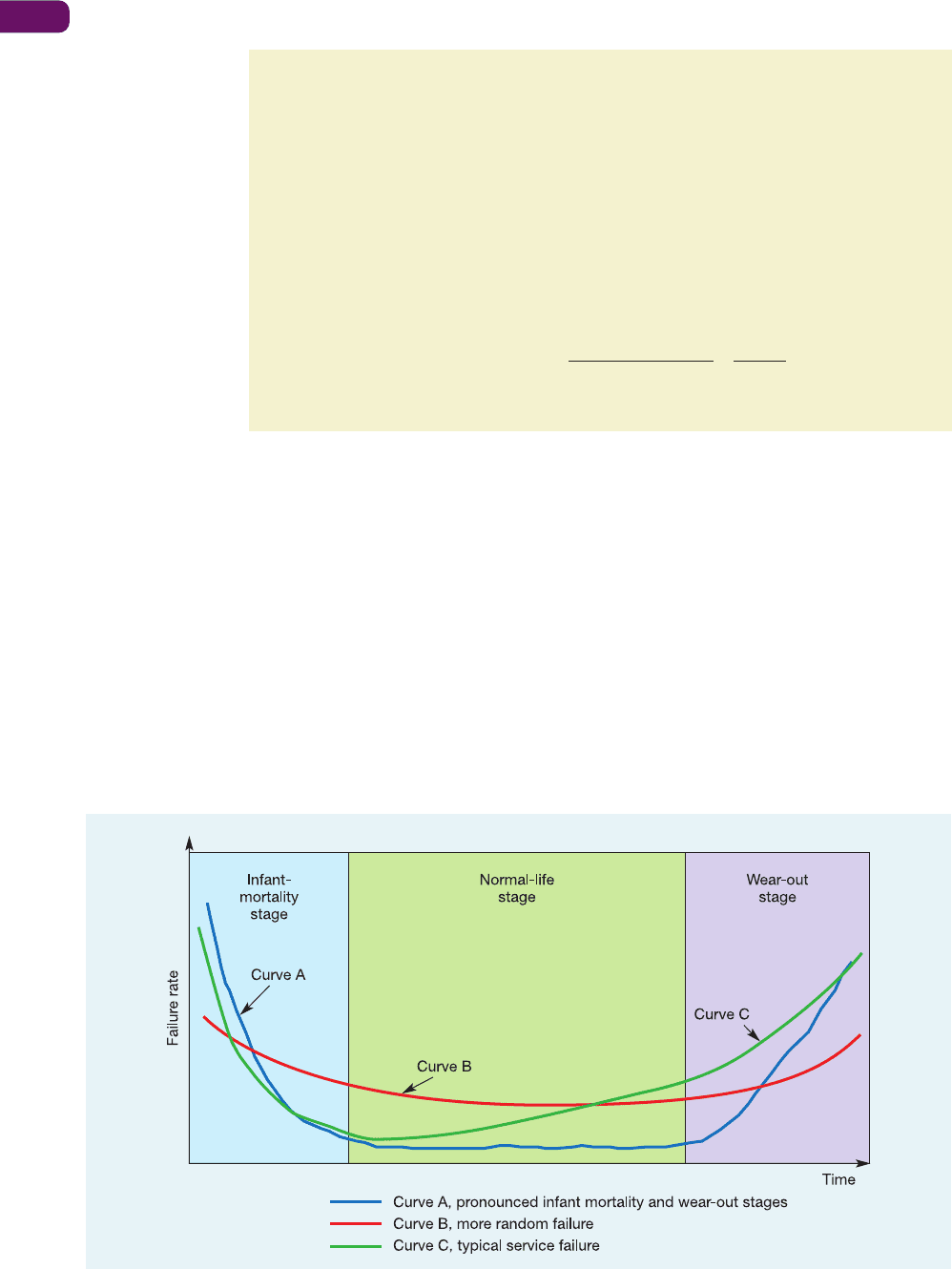
Sometimes failure is a function of time. For example, the probability of an electric lamp
failing is relatively high when it is first used, but if it survives this initial stage, it could still
fail at any point, and the longer it survives, the more likely its failure becomes. The curve
which describes failure probability of this type is called the bath-tub curve. It comprises three
distinct stages: the ‘infant-mortality’ or ‘early-life’ stage where early failures occur caused
by defective parts or improper use; the ‘normal-life’ stage when the failure rate is usually low
and reasonably constant, and caused by normal random factors; the ‘wear-out’ stage when the
failure rate increases as the part approaches the end of its working life and failure is caused
by the ageing and deterioration of parts. Figure 19.6 illustrates three bath-tub curves with
slightly different characteristics. Curve A shows a part of the operation which has a high initial
infant-mortality failure but then a long, low-failure, normal life followed by the gradually
increasing likelihood of failure as it approaches wear-out. Curve B is far less predictable. The
Part Four Improvement
580
But:
one component was not operating 2,000 − 1,200 = 800 hours
one component was not operating 2,000 − 1,450 = 550 hours
one component was not operating 2,000 − 1,720 = 280 hours
one component was not operating 2,000 − 1,905 = 95 hours
Thus:
Total non-operating time = 1,725 hours
Operating time = total time − non-operating time
= 100,000 − 1,725 = 98,275 hours
Failure rate (in time) ==
= 0.000041
4
98,275
number of failures
operating time
Figure 19.6 Bath-tub curves for three types of process
Early life failure
Normal life failure
Wear-out failure
M19_SLAC0460_06_SE_C19.QXD 10/20/09 9:55 Page 580

The number of components
In the example, the reliability of the whole system was only 0.8, even though the reliability
of the individual components was significantly higher. If the system had been made up of
more components, then its reliability would have been even lower. The more interdependent
components an operation or process has, the lower its reliability will be. For one composed
of components which each have an individual reliability of 0.99, with 10 components the
system reliability will shrink to 0.9, with 50 components it is below 0.8, with 100 components
it is below 0.4, and with 400 components it is down below 0.05. In other words, with a pro-
cess of 400 components (not unusual in a large automated operation), even if the reliability
of each individual component is 99 per cent, the whole system will be working for less than
5 per cent of its time.
Mean time between failures
An alternative (and common) measure of failure is the mean time between failures (MTBF)
of a component or system. MTBF is the reciprocal of failure rate (in time). Thus:
MTBF =
operating hours
number of failures
Chapter 19 Risk management
581
distinction between the three stages is less clear, with infant-mortality failure subsiding only
slowly and a gradually increasing chance of wear-out failure. Failure of the type shown in
curve B is far more difficult to manage in a planned manner. The failure of operations which
rely more on human resources than on technology, such as some services, can be closer to
curve C. They may be less susceptible to component wear-out but more so to staff complacency
as the service becomes tedious and repetitive.
Reliability
Reliability measures the ability to perform as expected over time. Usually the importance
of any particular failure is determined partly by how interdependent the other parts of the
system are. With interdependence, a failure in one component will cause the whole system
to fail. So, if an interdependent system has n components each with their own reliability, R
1
,
R
2
,..., R
n
, the reliability of the whole system, R
s
, is given by:
R
s
= R
1
× R
2
× R
2
× ...× R
n
where
R
1
= reliability of component 1
R
2
= reliability of component 2
etc.
An automated pizza-making machine in a food manufacturer’s factory has five major
components, with individual reliabilities (the probability of the component not failing)
as follows:
Dough mixer Reliability = 0.95
Dough roller and cutter Reliability = 0.99
Tomato paste applicator Reliability = 0.97
Cheese applicator Reliability = 0.90
Oven Reliability = 0.98
If one of these parts of the production system fails, the whole system will stop working.
Thus the reliability of the whole system is:
R
s
= 0.95 × 0.99 × 0.97 × 0.90 × 0.98
= 0.805
Worked example
Mean time between
failures
Reliability
M19_SLAC0460_06_SE_C19.QXD 10/20/09 9:55 Page 581
Availability
Availability is the degree to which the operation is ready to work. An operation is not avail-
able if it has either failed or is being repaired following failure. There are several different
ways of measuring it depending on how many of the reasons for not operating are included.
Lack of availability because of planned maintenance or changeovers could be included, for
example. However, when ‘availability’ is being used to indicate the operating time excluding
the consequence of failure, it is calculated as follows:
Availability (A) =
where
MTBF = the mean time between failures of the operation
MTTR = the mean time to repair, which is the average time taken to repair the
operation, from the time it fails to the time it is operational again.
MTBF
MTBF + MTTR
Availability
Part Four Improvement
582
In the previous worked example which was concerned with electronic components, the
failure rate (in time) of the electronic components was 0.000041. For that component:
MTBF ==24,390.24 hours
That is, a failure can be expected once every 24,390.24 hours on average.
1
0.000041
Worked example
A company which designs and produces display posters for exhibitions and sales
promotion events competes largely on the basis of its speedy delivery. One particular
piece of equipment which the company uses is causing some problems. This is its large
platform colour laser printer. Currently, the mean time between failures of the printer is
70 hours and its mean time to repair is 6 hours. Thus:
Availability ==0.92
The company has discussed its problem with the supplier of the printer who has offered
two alternative service deals. One option would be to buy some preventive maintenance
(see later for a full description of preventive maintenance) which would be carried out
each weekend. This would raise the MTBF of the printer to 90 hours. The other option
would be to subscribe to a faster repair service which would reduce the MTTR to
4 hours. Both options would cost the same amount. Which would give the company the
higher availability?
With MTBF increased to 90 hours:
Availability ==0.938
With MTTR reduced to 4 hours:
Availability ==0.946
Availability would be greater if the company took the deal which offered the faster repair
time.
70
70 + 4
90
90 + 6
70
70 + 6
Worked example
M19_SLAC0460_06_SE_C19.QXD 10/20/09 9:55 Page 582

Failure mode and effect analysis
One of the best-known approaches to assessing the relative significance of failure is failure
mode and effect analysis (FMEA). Its objective is to identify the factors that are critical to
various types of failure as a means of identifying failures before they happen. It does this by
providing a ‘checklist’ procedure built around three key questions for each possible cause of
failure:
● What is the likelihood that failure will occur?
● What would the consequence of the failure be?
● How likely is such a failure to be detected before it affects the customer?
Chapter 19 Risk management
583
‘Subjective’ estimates
Failure assessment, even for subjective risks, is increasingly a formal exercise that is carried
out using standard frameworks, often prompted by health and safety, environmental, or
other regulatory reasons. These frameworks are similar to the formal quality inspection
methods associated with quality standards like ISO 9000 that often implicitly assume unbiased
objectivity. However, individual attitudes to risk are complex and subject to a wide variety
of influences. In fact many studies have demonstrated that people are generally very poor
at making risk-related judgements. Consider the success of state and national lotteries. The
chances of winning, in nearly every case, are so low as to make the financial value of the
investment entirely negative. If a player has to drive their car in order to purchase a ticket,
they may be more likely to be killed or seriously injured than they are to win the top prize.
But, although people do not always make rational decisions concerning the chances of failure,
this does not mean abandoning the attempt. But it does mean that one must understand the
limits to overly rational approaches to failure estimation, for example, how people tend to
pay too much attention to dramatic low-probability events and overlook routine events.
Even when ‘objective’ evaluations of risks are used, they may still cause negative con-
sequences. For example, when the oil giant Royal-Dutch Shell took the decision to employ
deep-water disposal in the North Sea for their Brent Spar oil platform, they felt that they
were making a rational operational decision based upon the best available scientific evidence
concerning environmental risk. Unfortunately Greenpeace disagreed and put forward an
alternative ‘objective analysis’ showing significant risk from deep-water disposal. Eventually
Greenpeace admitted their evidence was flawed but by that time Shell had lost the public
relations battle and had altered their plans.
The idea that failure can be detected through in-process inspection is increasingly seen
as only partially true. Although inspecting for failures is an obvious first step in detecting
them, it is not even close to being 100 per cent reliable. Accumulated evidence from
research and practical examples consistently indicates that people, even when assisted
by technology, are not good at detecting failure and errors. This applies even when spe-
cial attention is being given to inspection. For example, airport security was significantly
strengthened after 11 September 2001, yet one in ten lethal weapons that were entered
into airports’ security systems (in order to test them) were not detected.
8
‘There is no such
thing as one hundred per cent security, we are all human beings’, says Ian Hutcheson, the
Director of Security at Airport Operator BAA. No one is advocating abandoning inspection
as a failure detection mechanism. Rather it is seen as one of a range of methods of
preventing failure.
Critical commentary
M19_SLAC0460_06_SE_C19.QXD 10/20/09 9:55 Page 583
