Li S.Z., Jain A.K. (eds.) Encyclopedia of Biometrics
Подождите немного. Документ загружается.

Quantifying Performance
Unlike password-based systems, where a perfect match
between two alphanumeric strings is necessary to vali-
date a user’s identity, a biometric system seldom
encounters two samples of a user’s biometric trait
that result in exactly the same feature set. This is due
to imperfect sensing conditions (e.g., noisy fingerprint
due to sensor malfunction), alterations in the user’s
biometric characteristic (e.g., respiratory ailments
impacting speaker recognition), changes in ambient
conditions (e.g., inconsistent
▶ illumination levels in
face recognition), and variations in the user’s interac-
tion with the sensor (e.g., occluded iris or partial
fingerprints). The variability observed in the biometric
feature set of an individual is referred to as intraclass
variation, and the variability between feature sets ori-
ginating from two different individuals is known as
interclass varia tion. A useful feature set exhibits small
intra-class variation and large interclass variation.
A similarity match score is known as a genuine score
or authentic score if it is the result of matching two
samples of the same biometric trait of a user. It is
known as an impostor score if it involves comparing
two biometric samples originating from different users.
To analyze the performance of a biometric system, the
probability distribution of genuine and impostor match-
ing scores is examined. A genuine matching score is
obtained when two feature sets corresponding to the
same individual are compared, and an impostor
matching score is obtained when feature sets from
two different individuals are compared. In the case of
verification, when a matching score exceeds a certain
threshold, the two feature sets are declared to be from
the same individual; otherwise, they are assumed to be
from different in dividuals. Thu s, there are two funda-
mental types of errors associated with a verification
system: (i) a false match, which occurs when an im-
postor matching score exceeds the threshold, and (ii) a
false nonmatch, which occurs when a genuine match-
ing score does not exceed the threshold. The error rates
of systems based on fingerprint and iris are usually
lower when compared to those based on voice, face,
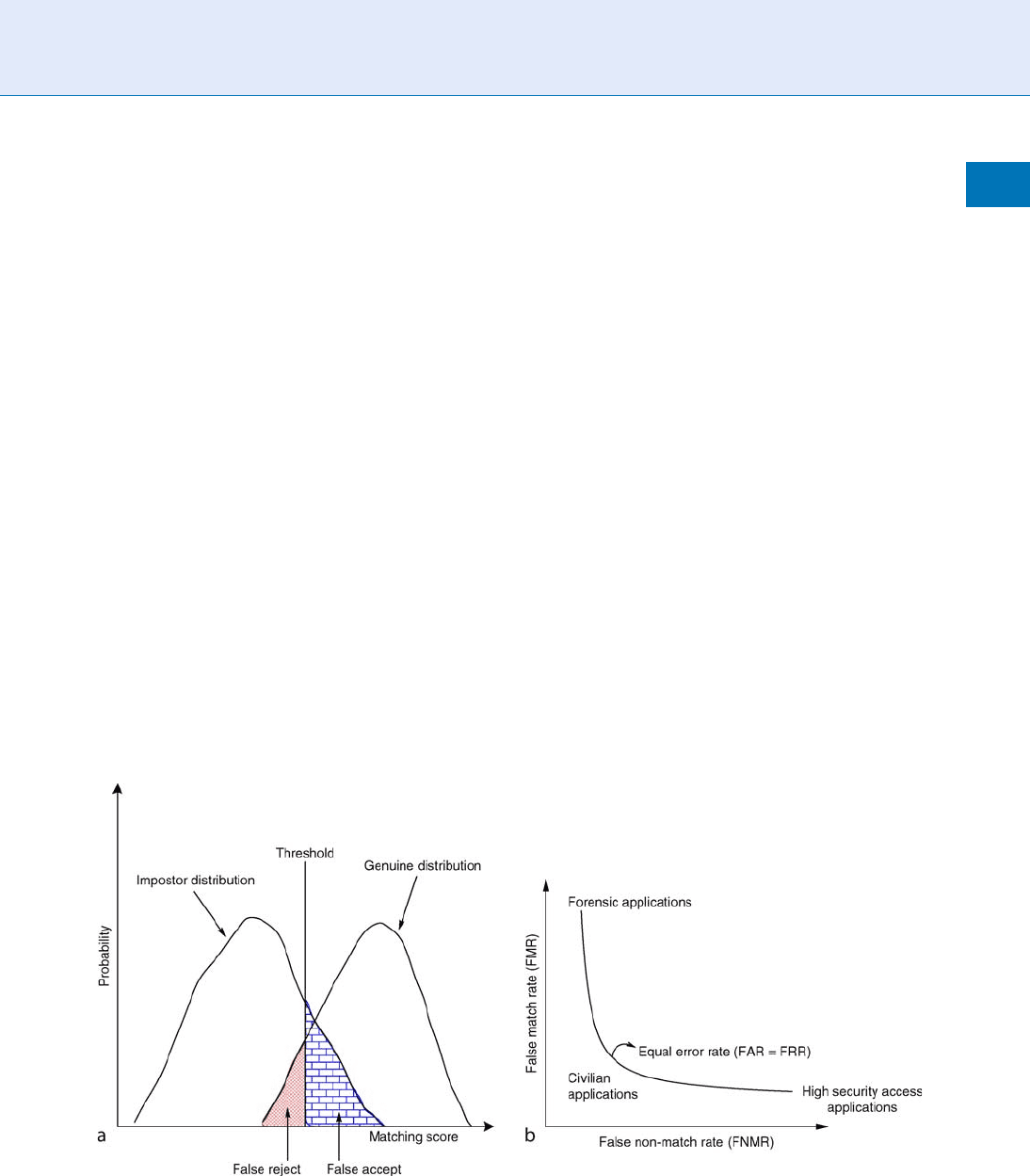
and hand geometry. A Receiver Operating Characteris-
tic (ROC) curve plots the False Non-match Rate
(FNMR – the percentage of genuine scores that do
not exceed the threshold) against the False Match
Rate (FMR – the percentage of impostor scores that
exceed the threshold) a t various thresholds. The
operating threshold employed by a system depends
on the nature of the application. In forensic applica-
tions, for example, a low FNMR is preferred, while in
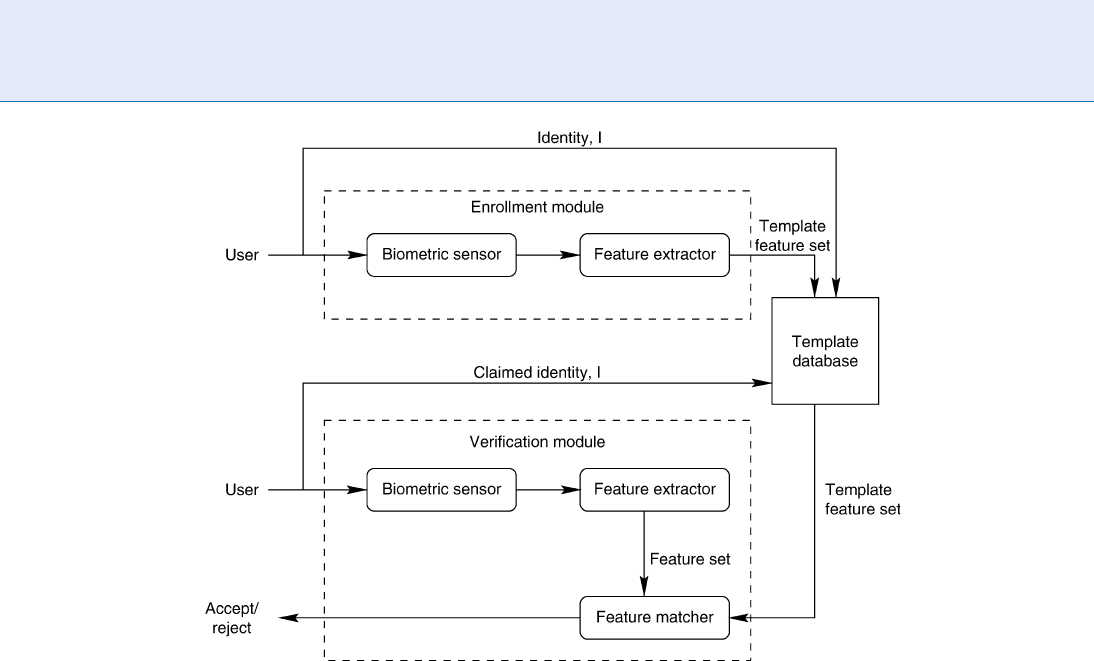
Biometrics, Overview. Figure 2 The enrollment module and the verification module of a biometric system.
170
B
Biometrics, Overview
high security access facilities like nuclear labs, a low
FMR is desired (Fig. 3).
In the case of identification, the input feature set is
compared against all templates residing in the database
to determine the top match (i.e, the best match). The top
match can be determined by examining the match scores
pertaining to all the comparisons and reporting the
identity of the template corresponding to the largest
similarity score. The identification rate indicates the
proportion of times a previously enrolled individual
is successfully mapped to the correct identity in the
system. Here, assume that the question being asked is,
‘‘Does the top match correspond to the correct iden-
tity?’’ An alternate question could be, ‘‘Does any one of
the top k matches correspond to the correct identity?’’
(see [7]). The rank-k identification rate, R
k
, indicates
the propor tion of times the correct identity occurs in
the top k matches as determined by the match score.
Rank-k performance can be summarized using the
Cumulative Match Characteristic (CMC) that plots
R
k
against k, for k ¼ 1, 2, ... M with M being the
number of enrolled users.
Besides FMR and FNMR, other types of errors are
also possible in a biometric system. The Failure to
Enroll (FTE) error refers to the inability of a biometric
system to enroll an individual whose biometric trait
may not be of good
▶ qualit y (e.g., poor quality fin-
gerprint ridges). Similarly, a biometric system may be
unable to procure good quality biometric data from an
individual during authentication resulting in a Failure
to Acquire (FTA) error.
A biometric system is susceptible to various types of
attacks [8]. For example, an impostor may attempt to
present a fake finger or a face mask or even a recorded
voice sample to circumvent the system. The problem of
fake biometrics may be mitigated by employing
▶ challenge-response mechanisms or conducting live-
ness dete ction tests. Privacy concerns related to the use
of biometrics and protection of biometric templates
are the issues that are currently being studied [9–11].
Applications
Establishing the identity of a person with hig h confi-
dence is becoming critical in a number of applications
in our vastly interconnected society. Questions like ‘‘Is she
really who she claims to be?’’, ‘‘Is this person authorized to
use this facility?’’ or ‘‘Is he in the watchlist posted by the
government?’ ’ are routinely being posed in a variety of
scenarios ranging from issuing a driver’s license to gaining
entry into a country. The need for reliable user
Biometrics, Overview. Figure 3 Evaluating the matching accuracy of a biometric system operating in the verification
mode. (a) Histograms of genuine and impostor matching scores and the two types of errors (False Accept and False
Reject) that are possible in a verification system. (b) A Receiver Operating Characteristic (ROC) curve indicating the
operating point (threshold) for different types of applications. Note that FMR and FNMR are often used as synonyms for
FAR and FRR, respectively.
Biometrics, Overview
B
171
B
authentication techniques has increased in the wake of
heightened concerns about security, and rapid advance-
ments in networking, communication, and mobility.
Thus, biometrics is being increasingly incorporated in
several different applications. These applications can be
categorized into three main groups (see Table 1):
1. Commercial applications such as computer network
login, electronic data security, e-commerce, Internet
access, ATM or credit card use, physical access con-
trol, mobile phone, PDA, medical records manage-
ment, distance learning, etc.
2. Government applications such as national ID card,
managing inmates in a correctional facility, driver’s
license, social security, welfare-disbursem ent, bor-
der control, passport control, etc.
3. Forensic applications such as corpse identification,
criminal in vestigation, parenthood determination, etc.
Summary
The increased demand for reliable and convenient
authentication schemes, availability of inexpensive
computing resources, development of cheap biometric
sensors, and advancements in signal processing have all
contributed to the rapid deployment of biometric sys-
tems in establishments ranging from grocery stores to
airports. The emergence of multibiometrics has further
enhanced the matching performance of biometric sys-
tems [12, 13]. It is only a matter of time before
biometrics integrates itself into the very fabric of soci-
ety and impacts the way we conduct our daily business.
Related Entries
▶ Authentication
▶ Biometric Applications, Overview
▶ Enrollment
▶ Identification
▶ Soft Biometrics
▶ Verification
References
1. Jain, A.K., Flynn, P., Ross, A. (eds).: Handbook of Biometrics.
Springer (2007)
2. Wayman, J.L., Jain, A.K., Maltoni, D., Maio, D. (eds.): Bio-
metric Systems: Technology, Design and Performance Evalua-
tion. Springer, New York (2005)
3. Bolle, R., Connell, J., Pankanti, S., Ratha, N., Senior, A.: Guide to
Biometrics. Springer, New York (2003)
4. Wechsler, H.: Reliable Face Recognition Methods: System De-
sign, Implementation and Evaluation. Springer (2006)
5. Maltoni, D., Maio, D., Jain, A.K., Prabhakar, S.: Handbook of
Fingerprint Recognition. Springer, New York (2003)
6. Jain, A.K., Ross, A., Prabhakar, S.: An Introduction to Biometric
Recognition. IEEE Trans. Circuits Syst. Video Technol., Special
Issue on Image- and Video-Based Biometrics 14(1), 4–20 (2004)
7. Moon, H., Phillips, P.J.: Computational and Performance
Aspects of PCA-based Face Recognition Algorithms. Perception
30(5), 303–321 (2001)
8. Ratha, N.K., Connell, J.H., Bolle, R.M.: An analysis of minutiae
matching strength. In: Proceedings of Third International Con-
ference on Audio- and Video-Based Biometric Person Authenti-
cation (AVBPA), pp. 223–228. Halmstad, Sweden (2001)
9. Prabhakar, S., Pankanti, S., Jain, A.K.: Biometric Recognition:
Security and Privacy Concerns. IEEE Security Privacy Mag. 1(2),
33–42 (2003)
10. Rejman-Greene, M.: Privacy issues in the application of
biometrics: a european perspective. In: Wayman, J.L. Jain, A.K.
Maltoni, D. Maio (eds.) D. Biometric Systems: Technology,
Design and Performance Evaluation, pp. 335–359. Springer,
New York (2005)
11. Kenny, S., Borking, J.J.: The Value of Privacy Engineering.
J. Inform. Law Technol. (JILT) 7(1), (2002)
12. Jain, A.K., Ross, A.: Multibiometric Systems. Commun. ACM,
Special Issue on Multimodal Interfaces 47(1), 34–40 (2004)
13. Ross, A., Nandakumar, K., Jain, A.K.: Handbook of Multi-
biometrics. 1st ed. Springer, New York (2006)
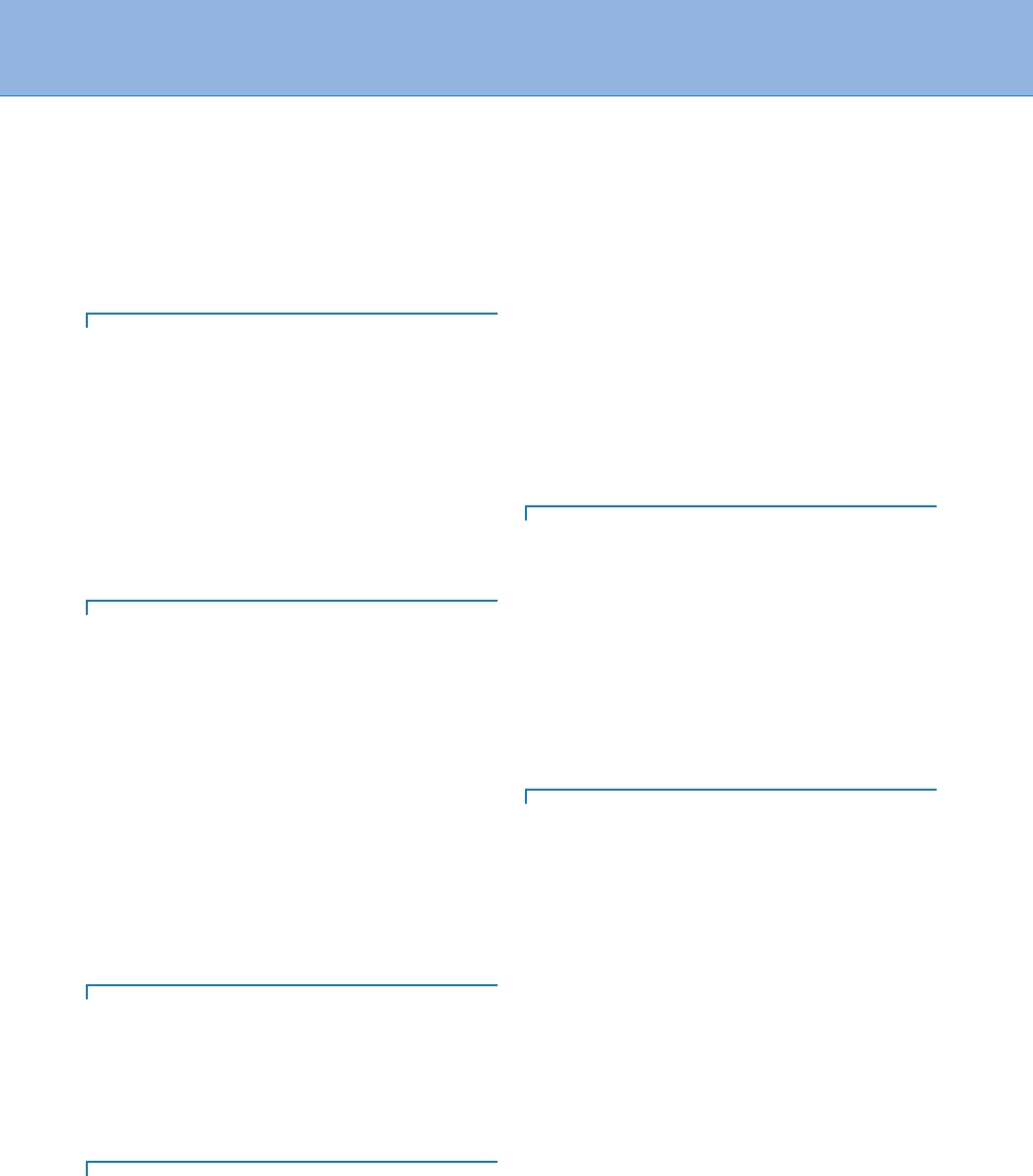
Biometrics, Overview. Table 1 Authentication solutions
employing biometrics can be used in a variety of
applications which depend on reliable user authentication
mechanisms
Forensics Government Commercial
Corpse
identification
National ID card ATM
Criminal
investigation
Driver’s license; voter
registration
Access
control;
computer
login
Parenthood
determination
Welfare
disbursement
Mobile phone
Missing children Border crossing E-commerce;
Internet;
banking;
smart card
172
B
Biometrics, Overview

BIP
▶ Biometric Technical Interface, Standardization
BIR
▶ Common Biometric Exchange Formats Framework
Standardization
Blind Source Seperation
▶ Independent Component Analysis
Blood Vessel Wall
Blood vessel wall is the wall that forms the tubular
channel of blood flow. The walls of arteries and veins
consist of three layers, tuni ca intima, tunica media, and
tunica externa (adventitia). The most inner layer, tuni -
ca intima consists of a surface layer of endothelium
with a basement membrane. In the case of arteries,
there is an internal elastic membrane around it. The
tunica media is composed of smooth muscle and con-
nective tissue. In the case of arteries, there is an exter-
nal elastic membrane around it. The tunica externa is
the connective tissue forming the outmost layer. The
walls of capillaries consist of a single layer of endothe-
lial cells and a basement me mbrane.
The cells of vesse l walls control the function of
blood vessels by receiving information not only
from outside the wall but also from the crosstalk
among them. For example, the smooth muscle of a
vessel wall contra cts or relaxes as the reaction to
various a gents. They include neurotransmitters,
paracrine factors, hormones, and nitric oxide. By
the constriction and the dilation, the inner diameter
of the blood vessel changes and the blood pressure is
con trolled.
The inner surface of the vessel wall or the epithelial
layer serves as a smooth barrier. Its selective permeabil-
ity plays an important role in the balancing of fluid
between blood and tissue fluid. The epithelial cells of
the vessel wall also produce the various bioactive
substances.
▶ Performance Evaluation, Overview
Brachycephalic
Brachycephalic is the head form characterized by
an anteroposteriorly short and mediolaterally wide
skull.
▶ Anatomy of Face
Branch-and-Bound Search
A search strategy employed by optimization algorithms
in which the space of candidate solutions is navigated
in a systematic manner via a tree-like structure by
employing upper and lower bounds on the criterion
function being optimized. The search strategy is char-
acterized by three steps: (1) a branching step in which
the space of possible candidate solutions is recursively
partitioned, (2) a bounding step in which upper and
lower bounds are estimated for the criterion function
based on the candidate solutions within each partition,
and (3) a pruning step in which improbable solu tions
are eliminated.
▶ Fusion, Feature-Level
Branch-and-Bound Search
B
173
B

Breeder Documents
Breeder documents are documents accepted for estab-
lishing ground truth with respect to an individual’s
identity. Breeder documents are typically used to
obtain other identity documents or to establish/enroll
an identity to obtain some benefit, privilege, or enti-
tlement. One example of a breeder document is birth
certificate, which may then be used to establish identity
for the purpose of obtaining a driver’s license.
▶ Fraud Reduction, Applications
174
B
Breeder Documents
C
Calibration
It refers to a software or hardware procedure to restore
the initial operational conditions of a sensor or a
device.
▶ Biometric Sensor and Device, Overview
▶ Image Formation
Camera
Camera is the face imaging device delivering either
single image stills or video streams. It generally delivers
a standard analog signal and requires a digitization
device to produce digital images. Low-cost web cameras
provide a standard USB interface to deliver digitized
images in digital format. High-end cameras provide a
standard digital signal for high-resolution images.
▶ Face Device
▶ Image Formation
Camera Device
▶ Face Device
Camera Model
The camera model describes how a point in the 3D
space is projected on the 2D image plane. The projec-
tion that gives the 2D image coordinates of any point
on the 3D space is defined, by the camera model and a
few parameters (camera parameters) such, as the focal
length.
▶ Face Pose Analysis
Camera Point of View
Camera point of v iew is the effective location and
orientation of a camera that would result in the obser-
ved hand silhouette.
▶ Hand Data Interchange Format, Standardization
Cancelable Biometrics
ANDY ADLER
Carleton University, Ottawa, ON, Canada
Synonym
Revocable biometrics
Definition
Cancelable biometrics are designed to allow an indi-
vidual to enroll and revoke a large number of different
biometric samples. Each biometric image is encoded
with a distortion scheme that varies for each applica-
tion. The concept was developed to address the privacy
and security concerns that biometric samples are
limited and must be used for multiple applications.
During enrollment, the input biometric image is sub-
jected to a known distortion controlled by a set of
#
2009 Springer Science+Business Media, LLC

parameters. The distorted bio metric sample can, in
some schemes, be processed with standard biometrics
algorithms, which are unaware that the features pre-
sented to them are distorted. During matching, the live
biometric sample must be distorted with the same
parameters, which must be securly stored. The cancel-
able nature of this scheme is provided by the distor-
tion, in that it is not the user’s ‘‘actual’’ biometric that
is stored, but simply one of an arbitrarily large number
of possible permutati ons. One concern with cancelable
biometrics is the secure management of the distortion
parameters.
Introduction
Cancelable biometrics describes a class of biometric
matching algorithms designed to address the security
and privacy concerns because of the limited number
of biometric samples. This limitation – humans have
only one face, two eyes and up to ten fingers – raises
several concerns (
▶ Security and Liveness, Overview):
(1) the same biometric must be enrolled into multiple
applications, potentially allowing cross application
privacy and security vulnerabilities; for example, fin-
gerprint images given to enter an amusement park may
then be used to spoo f a user to their bank; (2) a
compromised biometric sample is a permanent loss
to a user, unlike other security systems, where, for
example, new cards or passwords can be issued; and
(3) network protocols based on biometrics are poten-
tially vulnerable to replay attacks.
Cancelable biometrics algorithms address these
concerns by creating multiple varied independent bio-
metric samples by processing the input image (or tem-
plate features) with a parameterized distortion. The
concept was developed by Ratha et al. [1] and subse-
quently extended by many others (e.g., [2, 3, 4, 5, 6]).
During enrollment, the input biometric image is sub-
jected to a known distortion controlled by a set of
distortion parameters. The distorted biometric sample
can, in some schemes, be processed w ith standard
biometrics algorithms, which are unaware that the
features presented to them are distorted. During
matching, the live biometric sample must be distorted
in exactly the same way, otherwise it cannot match the
enrolled sample. This distortion must also satisfy the
constraint that multiple different distortion profiles
cannot match. Thus, the cancelable nature of this
scheme is provided by the distortion, in that it is not
the user’s ‘‘actual’’ biometric, which is stored, but
simply one of an arbitrarily large number of possible
permutations. Cancelable biometrics is simil ar in some
ways to biometric encryption (
▶ Biometric Encryp-
tion), but differs primarily in that the goal of a cancel-
able biometric scheme is a Match/Nonmatch decision,
while biometric encryption releases an encoded token
or cryptographic key.
Two classes of cancelable biometrics are defined by
Bolle et al. [2]: signal and feature domain distortions.
For signal domain distortion, the raw biometric
image is distorted. This image is subsequently pro-
cessed by a traditional biometric system, which may
be unaware of the distortions. Requirements for this
scheme are that the di stortion be large enough to
create independent input images, but constrained
such that the biometric system is able to identify and
reliably register landmarks on the image. Examples are
given for face, iris, and voice. For feature domain dis-
tortion, the biometric image is first processed to extract
the template features, which are then distorted. This
scheme may still use a traditional biometric template
match algorithm. Feature distortion is recommended
for fingerprints, where calculated minutiae are scram-
bled. It is difficult to envisage a simple fingerprint
image di stortion scheme, which destroys the original
minutiae while still preserving a fingerprint-like image.
It is emphasized that, much like a cryptographic hash
function, there is no need to invert cancelable distor-
tions, rather such distortions are designed to be one-
way functions in which comparison is performed in
the distorted space.
The first cancelable biometric algorithms for
face recognition were proposed by [ 7]. The distortion
takes place in the raw image space, since face recogni-
tion feature sets are not standardized. This places
tight constraints on the nature of the distortion, since
severely distorted faces will not be recognized and
properly encoded by the al gorithms. A different ap-
proach is taken by Savvides et al. [5] in which the
cancelable distortion is tied to a face recognition algo-
rithm based on correlation filters. Enrolled and test
face images are distorted with a random kernel calcu-
lated from a key to generate an encry pted correlation
filter. Since the same convolution kernel is present for
both images, its effect is mathematically cancelled in
the correlation filter. This scheme is somewhat similar
176
C
Cancelable Biometrics

to the biometric encryption approach of Soutar et al.
[9]. Boult [3] proposes a scheme in which face recog-
nition feaures are encoded via scaling and rotation;
The resulting data are separated into a ‘‘general
wrapping’’ number, whi ch is encrypted with a one-
way transform, and a fractional par t, which is pre-
served undestorted. Comparison is based on robust
distance measures, which saturate at large distances.
The cancelable fingerprint templates of [8] use the
minutiae rather than the raw image, since this allows
both minutiae position and angle to be permuted
(increasing the degrees of freedom of the transforma-
tion), and since distortion will interfere with the fea-
ture extraction process. The distortion is modeled on
the electric field distribution for random charges.
Results show a small impact on biometric errors
(5% increase in FRR) over undistorted features. A
theoretical approach to cancelable biometrics uses
▶ shielding functions [4], to allow a verifier to check
the authenticity of a prover (user wanting to be ver-
ified) without learning any biometric information,
using proposed d-contracting and E-revealing func-
tions. The proposed system was based on simple
Gaussian noise models and not tested with an actual
biometric system. Unfortunately, it is unclear how
practical functions can be found that account for the
inherent biometric feature variability.
A ‘‘biohashing’’ approach has been proposed by
Teoh et al. [6] and applied to many different modalities
including fingerprint, face, and palm. This scheme
applies a wavelet Fourier-Mellen transform (a rotation
and scale invariant transform) to input images. Each
bit of the tempate is calculated based on the inner
product of the transformed image with a random
image generated from a code. The claimed performance
of this approach is 0% EER. Unfortunately, it has been
shown by Kong et al. [10] that this high performance is
actually due to the code being treated as a guaranteed
secure password. Without this assumption, biohashing
approaches show overall poor error rates.
In general, cancelable biometrics may be seen to
represent a promising approach to address biometric
security and privacy vulnerabilities. However, there
are several concerns about the security of such
schemes. First, there is very little work analyzing their
security, except for an analysis of biohashing [10].
Secondly, while distortion schemes should be ‘‘prefer-
ably non-invertible’’ [2], no detailed proposed scheme
has this property. In fact, it would appear to be trivial
to ‘‘undistort’’ the template given knowledge of the
distortion key in most cases. Third, cancelable
biometrics would appear to be difficult to implement
in the untrusted scenarios for which they are proposed:
if the user does not trust the owne r of the biometric
sensor to keep the biometric private, how can they
enforce privacy on the distortion parameters used?
This last concern is perhaps the most serious: the
security of cancelable biometrics depends on secure
management of the distortion parameters, which
must be used for enrollment and made available at
matching. Furthermore, such keys may not be much
better protected than current passwords and PINs. In
summary, cancelable bio metrics offer a possible solu-
tion to certain serious security and privacy concerns of
biometric technology; however, current schemes leave
a number of important issues unaddressed. Research is
very active in this subject, and may succeed in addres-
sing these concerns.
Related Entries
▶ Fingerprints Hashing
▶ Security and Liveness, Overview
References
1. Ratha, N., Connell, J., Bolle, R.: Cancelable biometrics. In Proc.
Biometric Consortium Conference, Washington DC, USA
(2000)
2. Bolle, R.M., Connell, J.H., Ratha, N.K.: Biometric perils and
patches. Pattern Recogn. 35, 2727–2738 (2002)
3. Boult, T.: Robust distance measures for face-recognition sup-
porting revocable biometric tokens Proc. 7th Int. Conf. on Auto-
matic Face Gesture Recog Southampton, UK, pp. 560–566 (2006)
4. Linnartz, J.-P., Tuyls, P.: New shielding functions to enhance
privacy and prevent misuse of biometric templates. In Proc.
AVBPA, Guiford, UK, LNCS 2688, 393–402 (2003)
5. Savvides M, Vijaya Kumar BVK, Khosla, P.K.: Cancelable bio-
metric filters for face recognition. In Proc. Int. Conf. Pattern
Recognition, pp. 922–925 (2004)
6. Teoh, A.B., Ngo, D.C., Goh, A.: Biohashing: two factor authenti-
cation featuring fingerprint data and tokenised random number.
Pattern Recogn. 37, 2245–2255 (2004)
7. Ratha, N.K., Connell, J.H., Bolle, R.M.: Enhancing security and
privacy in biometrics-based authentication systems. IBM Syst. J.
40, 614–634 (2001)
8. Ratha, N., Connell, J., Bolle, R.M., Chikkerur, S.: Cancelable
biometrics: A case study in fingerprints. Proc. Int. Conf. Pattern
Recogn. 4, 370–373 (2006)
Cancelable Biometrics
C
177
C

9. Soutar, C., Roberge, D., Stoianov, A., Gilroy, R., Vijaya Kumar, B.
V.K.: Biometric Encryption using image processing. Proc. SPIE
Int. Soc. Opt. Eng. 3314, 178–188 (1998)
10. Kong, A., Cheung, K.-H., Zhang, D., Kamel, M., You, J.: An
analysis of biohashing and its variants. Pattern Recogn. 39,
1359–1368 (2006)
Canonical Face Model
Canonical face model is the model that is used to store
face images in databases. Once a facial image is ac-
quired, it is resized and transformed to match the size
and the orientation of the canonical face model, in
which it is then stored in a database and used for face
recognition tasks. For face recognition in documents,
the canonical face model proposed by the International
Civil Aviation Organization (ICAO) for the machine
readable travel documents is used by many passport
and immigration offices in many countries. This model
stores faces using 60 pixels between the eyes, which
ensures that feature-based face recognition technique s
can be applied on these images. It has been argued
however that this canonical face model may not be
suitable for face recognition in video, due to the fact
that face resolution in video is normally lower than
60 pixels between the eyes.
▶ Face Databases and Evaluation
CANPASS
▶ Iris Recognition at Airports and Border-Crossings
▶ Simplifying Passenger Travel Program
Capillary Blood Vessel
Capillary blood vessels are minute blood vessels,
5–10 mm in diameter, carrying blood from arterioles
to venules. Blood flows from the heart to arteries. The
arteries diverge into narrow arterioles, and then fur-
ther diverge into capillaries. The blood in the capil-
laries is collected into venules. The venules converge
into veins that carry the blood to the heart.
The capillaries are very thin and form a fine net-
work called a capillary bed. The capillar y wall consists
only of a single layer of cells, the endothelium. This
layer is so thin that it acts as a semipermeable mem-
brane in the interchange of various molecules between
blood and tissue fluid. It supplies oxygen, water, and
lipids from the blood, and carries away the waste
product such as carbon dioxide and urea from the
tissue. Though each capillary is very thin, the capillaries
form vast networks. The surface area of the capillary bed
in the total body amounts to 6,000 m
2
. Various stimu-
lations from our living environment cause the change
in the amount of blood in the capillary bed. In
biometrics, this change should be taken into account
particularly in venous pattern authentication.
▶ Performance Evaluation, Overview
Capture Volume
The volume in which an image-based biometric can be
successfully captured.
▶ Iris Device
▶ Iris on the Move
Casts
A three-dimensional plaster cast can be made of a
person’s foot, as another aid in barefoot morphology
comparison. The foot is placed in specially made foam,
used in podiatry and orthotics, in order to capture the
shape of the foot. Dental casting material can be
poured into the foam, and, upon setting, a solid
three-dimensional replica of the foot will be recovered.
▶ Forensic Barefoot Comparison
178
C
Canonical Face Model

CBEFF
Common Biometric Exchange Formats Framework.
▶ Biometric Technical Interface, Standardization
CBEFF Biometric Data Block (BDB)
The BDB contains biometric data. The values of the
mandatory CBEFF data elements, BDB Format Owner,
and BDB Format Type encoded in the SBH identify the
format of the BDB. A typical BDB could contain data
conforming to one of the data interchange formats
specified in ISO/IEC 19794 or one of the ANSI INCITS
biometric data format standards (or a proprietary
format).
▶ Common Biometric Exchange Formats Framework
Standardization
CBEFF Biometric Information
Records (BIRs)
BIRs are well-defined data structures that consist of
two or three parts: the standard biometric header
(SBH), the biometric data block (BDB), and the op-
tional security block (SB). CBEFF permits considerable
flexibility regarding BIR structures and BDB content,
but does so in a way that makes it easy for biometric
applications to evaluate their interest in processing a
particular BIR.
▶ Common Biometric Exchange Formats Framework
Standardization
CBEFF Security Block (SB)
The Security Block (SB) is an optional third compo-
nent of Common Biometric Exchange Formats Frame-
work Biometric Information Records (BIR). The SB
may carry integrity data (e.g., digital signature or MAC
(message authentication code)) or might also carry
data associated with the encryption of the CBEFF
Biometric Data Block (BDB). The format owner/for-
mat type approach was adopted to support the securit y
block. This enables any public or private organization
that wants to provide security solutions for BDBs and
BIRs to identify and publish its security data formats in
a standard way. The SB format owner/format type
fields in the CBEFF Standard Biometric Header pro-
vide this SB identifier. CBEFF requires that if an integ-
rity mechanism is applied to the BIR, then that
mechanism must cover both the SBH and the BDB.
▶ Common Biometric Exchange Formats Framework
Standardization
CBEFF Standard Biometric Header
(SBH)
The header of a BIR (Standard Biometric Header –
SBH) specifies metadata that describe specific charac-
teristics of the biometric data contained in the data
structures (e.g., biometric data format, modality, its
creation date). It can also convey information useful
to support security of the biometric data (e.g ., security/
integrity optio ns), and other user-required data
(e.g., user-defined payload, challenge-response data).
CBEFF standards explicitly require that the SBH not be
encrypted. This ensures that the header can always
be examined by an application with the minimum
necessary processing. CBEFF does, however, provide
definitions for a couple of optional data elements that
may be encrypted within the header.
▶ Common Biometric Exchange Formats Framework
Standardization
CBEFF Wrapper
Synonym
BIR
CBEFF Wrapper
C
179
C
