Yang J. (ed.) Biometrics
Подождите немного. Документ загружается.


Keystroke Dynamics Authentication 23
Clarke, N. L. & Furnell, S. M. (2007). Authenticating mobile phone users using keystroke
analysis, International Journal of Information Security 6: 1–14.
Conklin, A., Dietrich, G. & Walz, D. (2004). Password-based authentication: A system
perspective, Proceedings of the 37th Hawaii International Conference on System Sciences,
Hawaii.
Crawford, H. (n.d.). Keystroke dynamics: Characteristics and opportunities, Privacy Security
and Trust (PST), 2010 Eighth Annual International Conference on, IEEE, pp. 205–212.
de Magalhaes, T., Revett, K. & Santos, H. (2005). Password secured sites: stepping forward
with keystroke dynamics, International Conference on Next Generation Web Services
Practices.
de Ru, W. G. & Eloff, J. H. P. (1997). Enhanced password authentication through fuzzy logic,
IEEE Expert: Intelligent Systems and Their Applications 12: 38–45.
Doddington, G., Liggett, W., Martin, A., Przybocki, M. & Reynolds, D. (1998). Sheep, goats,
lambs and wolves: A statistical analysis of speaker performance in the nist 1998
speaker recognition evaluation, ICSLP98.
Dozono, H., Itou, S. & Nakakuni, M. (2007). Comparison of the adaptive authentication
systems for behavior biometrics using the variations of self organizing maps,
International Journal of Computers and Communications 1(4): 108–116.
El-Abed, M., Giot, R., Hemery, B. & Rosenberger, C. (2010). A study of users’ acceptance
and satisfaction of biometric systems, 44th IEEE International Carnahan Conference on
Security Technology (ICCST).
El-Abed, M., Giot, R., Hemery, B., Shwartzmann, J.-J. & Rosenberger, C. (2011). Towards the
security evaluation of biometric authentication systems, IEEE International Conference
on Security Science and Technology (ICSST).
Eltahir, W., Salami, M., Ismail, A. & Lai, W. (2008). Design and Evaluation of a Pressure-Based
Typing Biometric Authentication System, EURASIP Journal on Information Security,
Article ID 345047(2008): 14.
Epp, C. (2010). Identifying emotional states through keystroke dynamics, Master’s thesis,
University of Saskatchewan, Saskatoon, CANADA.
Filho, J. R. M. & Freire, E. O. (2006). On the equalization of keystroke timing histograms,
Pattern Recognition Letters 27: 1440–1446.
Gaines, R., Lisowski, W., Press, S. & Shapiro, N. (1980). Authentication by keystroke timing:
some preliminary results, Technical report, Rand Corporation.
Galassi, U., Giordana, A., Julien, C. & Saitta, L. (2007). Modeling temporal behavior
via structured hidden markov models: An application to keystroking dynamics,
Proceedings 3rd Indian International Conference on Artificial Intelligence (Pune, India).
Giot, R., El-Abed, M. & Chri (2011). Unconstrained keystroke dynamics authentication with
shared secret, Computers & Security pp. 1–20. [in print].
Giot, R., El-Abed, M. & Rosenberger, C. (2009a). Greyc keystroke: a benchmark for keystroke
dynamics biometric systems, IEEE International Conference on Biometrics: Theory,
Applications and Systems (BTAS 2009), IEEE Computer Society, Washington, District
of Columbia, USA, pp. 1–6.
Giot, R., El-Abed, M. & Rosenberger, C. (2009b). Keystroke dynamics authentication
for collaborative systems, International Symposium on Collaborative Technologies and
Systems, pp. 172–179.
Giot, R., El-Abed, M. & Rosenberger, C. (2009c). Keystroke dynamics with low constraints
svm based passphrase enrollment, IEEE International Conference on Biometrics: Theory,
179
Keystroke Dynamics Authentication

24 Will-be-set-by-IN-TECH
Applications and Systems (BTAS 2009), IEEE Computer Society, Washington, District
of Columbia, USA, pp. 1–6.
Giot, R., El-Abed, M. & Rosenberger, C. (2010). Fast learning for multibiometrics systems
using genetic algorithms, The International Conference on High Performance Computing
& Simulation (HPCS 2010), IEEE Computer Society, Caen, France, pp. 1–8.
Giot, R., Hemery, B. & Rosenberger, C. (2010). Low cost and usable multimodal biometric
system based on keystroke dynamicsand 2d face recognition, IAPR International
Conference on Pattern Recognition (ICPR), IAPR, Istanbul, Turkey, pp. 1128–1131.
Acecptance rate: 54/100.
Giot, R. & Rosenberger, C. (2011). A new soft biometric approach for keystroke dynamics
based on gender recognition, Int. J. of Information Technology and Management (IJITM),
Special Issue on: "Advances and Trends in Biometric pp. 1–17. [in print].
Grabham, N. & White, N. (2008). Use of a novel keypad biometric for enhanced user identity
verification, Instrumentation and Measurement Technology Conference Proceedings, 2008.
IMTC 2008. IEEE, pp. 12–16.
Guven, A. & Sogukpinar, I. (2003). Understanding users’ keystroke patterns for computer
access security, Computers & Security 22(8): 695–706.
Hocquet, S., Ramel, J.-Y. & Cardot, H. (2006). Estimation of user specific parameters in
one-class problems, ICPR ’06: Proceedings of the 18th International Conference on Pattern
Recognition, IEEE Computer Society, Washington, DC, USA, pp. 449–452.
Hocquet, S., Ramel, J.-Y. & Cardot, H. (2007). User classification for keystroke dynamics
authentication, The Sixth International Conference on Biometrics (ICB2007), pp. 531–539.
Hosseinzadeh, D. & Krishnan, S. (2008). Gaussian mixture modeling of keystroke patterns for
biometric applications, Systems, Man, and Cybernetics, Part C: Applications and Reviews,
IEEE Transactions on 38(6): 816–826.
Hwang, S.-s., Lee, H.-j. & Cho, S. (2006). Improving authentication accuracy of unfamiliar
passwords with pauses and cues for keystroke dynamics-based authentication,
Intelligence and Security Informatics 3917: 73–78.
Ilonen, J. (2003). Keystroke dynamics, Advanced Topics in Information Processing–Lecture .
ISO/IEC 19795-1 (2006). Information technology biometric performance testing and reporting,
Technical report, International Organization for Standardization ISO/IEC 19795-1.
ISO/IEC FCD 19792 (2008). Information technology – security techniques –security evaluation
of biometrics, Technical report, International Organization for Standardization
ISO/IEC FCD 19792.
Janakiraman, R. & Sim, T. (2007). Keystroke dynamics in a general setting, Lecture notes in
computer science 4642: 584.
Kang, P. & Cho, S. (2009). A hybrid novelty score and its use in keystroke dynamics-based
user authentication, Pattern Recognition p. 30.
Karnan, M., Akila, M. & Krishnaraj, N. (2011). Biometric personal authentication using
keystroke dynamics: A review, Applied Soft Computing 11(2): 1565 – 1573. The Impact
of Soft Computing for the Progress of Artificial Intelligence.
Khanna, P. & Sasikumar, M. (2010). Recognising Emotions from Keyboard Stroke Pattern,
International Journal of Computer Applications IJCA 11(9): 24–28.
Killourhy, K. & Maxion, R. (2008). The effect of clock resolution on keystroke dynamics,
Proceedings of the 11th international symposium on Recent Advances in Intrusion Detection,
Springer, pp. 331–350.
180
Biometrics

Keystroke Dynamics Authentication 25
Killourhy, K. & Maxion, R. (2009). Comparing anomaly-detection algorithms for keystroke
dynamics, IEEE/IFIP International Conference on Dependable Systems & Networks, 2009.
DSN’09, pp. 125–134.
Killourhy, K. & Maxion, R. (2010). Keystroke biometrics with number-pad input, IEEE/IFIP
International Conference on Dependable Systems & Networks, 2010. DSN’10.
Kohonen, T. (1995). Self-organising maps, Springer Series in Information Sciences 30.
Lopatka, M. & Peetz, M. (2009). Vibration sensitive keystroke analysis, Proceedings of the 18th
Annual Belgian-Dutch Conference on Machine Learning, pp. 75–80.
Marsters, J.-D. (2009). Keystroke Dynamics as a Biometric, PhD thesis, University of
Southampton.
Martinez-Diaz, M., Fierrez-Aguilar, J., Alonso-Fernandez, F., Ortega-Garcia, J. & Siguenza,
J. (2006). Hill-climbing and brute force attacks on biometric systems: a case study
in match-on-card fingerprint verification, Proceedings of the IEEE of International
Carnahan Conference on Security Technology (ICCST).
Modi, S. K. & Elliott, S. J. (2006). Kesytroke dynamics verification using spontaneously
generated password, IEEE International Carnahan Conferences Security Technology.
Monrose, F., Reiter, M. & Wetzel, S. (2002). Password hardening based on keystroke dynamics,
International Journal of Information Security 1(2): 69–83.
Monrose, F. & Rubin (1997). Authentication via keystroke dynamics, Proceedings of the 4th
ACM conference on Computer and communications security, ACM Press New York, NY,
USA, pp. 48–56.
Monrose, F. & Rubin, A. (2000). Keystroke dynamics as a biometric for authentication, Future
Generation Computer Syststems 16(4): 351–359.
Montalvao Filho, J. & Freire, E. (2006). Multimodal biometric fusion–joint typist (keystroke)
and speaker verification, Telecommunications Symposium, 2006 International,
pp. 609–614.
Nguyen, T., Le, T. & Le, B. (2010). Keystroke dynamics extraction by independent component
analysis and bio-matrix for user authentication, in B.-T. Zhang & M. Orgun (eds),
PRICAI 2010: Trends in Artificial Intelligence, Vol. 6230 of Lecture Notes in Computer
Science, Springer Berlin / Heidelberg, pp. 477–486.
Obaidat, M. & Sadoun, B. (1997). Verification of computer users using keystroke dynamics,
Systems, Man and Cybernetics, Part B, IEEE Transactions on 27(2): 261–269.
Pavaday., N., ., S. S. & Nugessur, S. (2010). Investigating & improving the reliability and
repeatability of keystroke dynamics timers, International Journal of Network Security &
Its Applications (IJNSA), 2(3): 70–85.
Pohoa, V. v., Pohoa, S., Ray, A. & Joshi, S. S. (2009). Hidden markov model (hmm)-based user
authentication using keystroke dynamics, patent.
Rao, B. (2005). Continuous keystroke biometric system, Master’s thesis, University of California.
Ratha, N. K., Connell, J. H. & Bolle, R. M. (2001). An analysis of minutiae matching strength,
Audio- and Video-Based Biometric Person Authentication.
Revett, K. (2008). Behavioral biometrics: a remote access approach, Wiley Publishing.
Revett, K. (2009). A bioinformatics based approach to user authentication via keystroke
dynamics, International Journal of Control, Automation and Systems 7(1): 7–15.
Revett, K., de Magalhães, S. & Santos, H. (2006). Enhancing login security through the use of
keystroke input dynamics, Lecture notes in computer science 3832.
Revett, K., de Magalhaes, S. & Santos, H. (2007). On the use of rough sets for user
authentication via keystroke dynamics, Lecture notes in computer science 4874: 145.
181
Keystroke Dynamics Authentication

26 Will-be-set-by-IN-TECH
Rodrigues, R., Yared, G., do NCosta, C., Yabu-Uti, J., Violaro, F. & Ling, L. (2006). Biometric
access control through numerical keyboards based on keystroke dynamics, Lecture
notes in computer science 3832: 640.
Rogers, S. J. & Brown, M. (1996). Method and apparatus for verification of a computer user’s
identification, based on keystroke characteristics. US Patent 5,557,686.
Ross, A. & Jain, A. (2004). Biometric sensor interoperability: A case study in fingerprints,
Proc. of International ECCV Workshop on Biometric Authentication (BioAW), Springer,
pp. 134–145.
Ross, A., Nandakumar, K. & Jain, A. (2006). Handbook of Multibiometrics, Springer.
Sang, Y., Shen, H. & Fan, P. (2004). Novel impostors detection in keystroke dynamics
by support vector machine, Proc. of the 5th international conference on Parallel and
Distributed Computing, Applications and Technologies (PDCAT 2004).
Schneier, B. (1999). Inside risks: the uses and abuses of biometrics, Commun. ACM .
Song, D., Venable, P. & Perrig, A. (1997). User recognition by keystroke latency pattern
analysis, Retrieved on 19.
Spillane, R. (1975). Keyboard apparatus for personal identification.
Stefan, D. & Yao, D. (2008). Keystroke dynamics authentication and human-behavior driven
bot detection, Technical report, Technical report, Rutgers University.
Teh, P., Teoh, A., Ong, T. & Neo, H. (2007). Statistical fusion approach on keystroke dynamics,
Proceedings of the 2007 Third International IEEE Conference on Signal-Image Technologies
and Internet-Based System-Volume 00, IEEE Computer Society, pp. 918–923.
Theofanos, M., Stanton, B. & Wolfson, C. A. (2008). Usability & biometrics: Ensuring
successful biometric systems, Technical report, The National Institute of Standards and
Technology (NIST).
Umphress, D. & Williams, G. (1985). Identity verification through keyboard characteristics,
Internat. J. Manâ
˘
A¸SMachine Studies 23: 263–273.
Yu, E. & Cho, S. (2004). Keystroke dynamics identity verification – its problems and practical
solutions, Computers & Security 23(5): 428–440.
182
Biometrics

0
DWT Domain On-Line Signature Verification
Isao Nakanishi, Shouta Koike, Yoshio Itoh and Shigang Li
Tottori University
Japan
1. Introduction
Biometrics attracts attention since person authentication becomes very important in
networked society. As the biometrics, the fingerprint, iris, face, ear, vein, gate, voice and
signature are well known and are used in various applications (Jain et al., 1999; James et al.,
2005). Especially, assuming mobile access using a portable terminal such as a personal digital
assistant (PDA), a camera, microphone, and pen-tablet are normally equipped; therefore,
authentication using the face, voice and/or signature can be realized with no additional
sensor.
Fig. 1. A PDA with a pen-tablet
On the other hand, the safety of biometric data is discussed actively. Every human being has
limited biometrics, for example, only ten fingerprints and one face. If the biometric data are
leaked out and it is known whose they are, they are never used for authentication again.
To deal with this problem, cancelable biometric techniques have been proposed, which use not
biometric data directly but one-to-one transformed data from the biometric data. However,
such a technique is unnecessary if the biometrics itself is cancelable.
Among various biometric modalities, only the signature is cancelable from a viewpoint of
spoofing. Even if a signature shape is known by others, it is possible to cope with the p roblem
by changing the shape. Especially, in on-line signatures, the habit during writing is biometrics
and it is not remained in the signature shape; therefore, to imitate it is quite difficult even if the
signature shape is copied. As a result, the on-line signature verification is actively researched
9

2 Biometrics
(Dimauro et al., 2004; Fierrez & Ortega-Garcia, 2007; Jain et al., 2002; Plamondon & Srihari,
2000). However, the verification performance tends to be degraded since the on-line signature
is a dynamic trait.
We have proposed a new on-line signature verification method in which a pen-position
parameter is decomposed into sub-band signals using the discrete wavelet transform (DWT)
and total decision is done by fusing verification results in sub-bands (Nakanishi et al., 2003;
2004; 2005). The reason why we use only the pen-position parameter is that detecting
functions of other parameters such as pen-pressure, pen-altitude, and/or pen-direction are
not equipped in the PDA.
However, since the signature shape is visible, it is relatively easy to forge the pen-position
parameter by tracing genuine signatures by others. In the proposed method, individual
features of a signature are enhanced and extracted in the sub-band signals, so that such
well-forged signatures can be distinguished from genuine ones. Additionally, in the
verification process of the proposed method, dynamic programming (DP) matching is
adopted to make it possible to verify two data series with different number of sampled points.
The purpose of the DP matching is to find the best combination between such two data series.
Concretely, a DP distance is calculated in every possible combination of the two data series
and as a result the combination which has the smallest DP distance is regarded as the best.
But there are problems in use of the DP matching. The DP distance is obtained as dissimilarity;
therefore, signatures with large DP distances are rejected even if they are of genuine. For
instance, in a pen-tablet system, a pen-up while writing causes large differences in coordinate
values of pen-position and so increases false rejection. On the other hand, signatures with
small DP distances are accepted even if they are forgery. The DP matching forces to match
two signatures even if either is forgery. It increases false acceptance.
Consequently, we propose simply-partitioned DP matching. Two data series compared are
divided into several partitions and the DP distance is calculated every partition. The DP
distance is initialized at the start of a next partition, so that it reduces excessively large DP
distances, that is, the false rejection. On the other hand, limitation of combination in matching
is effective for rejecting forgeries; therefore, it reduces the false acceptance.
There is another important problem when we use the DP matching. The DP distance is
proportional to the number of signature’s sampled data, that is, signature complexity (shape),
so that if it is used as a criterion in verification, each signature (user) has a different optimal
threshold. But, it is general to use a single threshold commonly in an authentication system.
If the common threshold is used for all signatures, it results in degradation of verification
performance. Therefore, we have studied threshold equalization in the on-line signature
verification (Nakanishi et al., 2008). We propose new equalizing methods based on linear and
nonlinear approximation between the number of sampled data and optimal thresholds.
2. DWT domain on-line signature verification
In this section, we briefly explain the proposed on-line signature verification in the DWT
domain.
2.1 System overview
A s ignal flow diagram is shown in Fig. 2. An on-line signature is captured as x and y
coordinate (pen-position) data in a digital pen-tablet system and their sampled data are
184
Biometrics
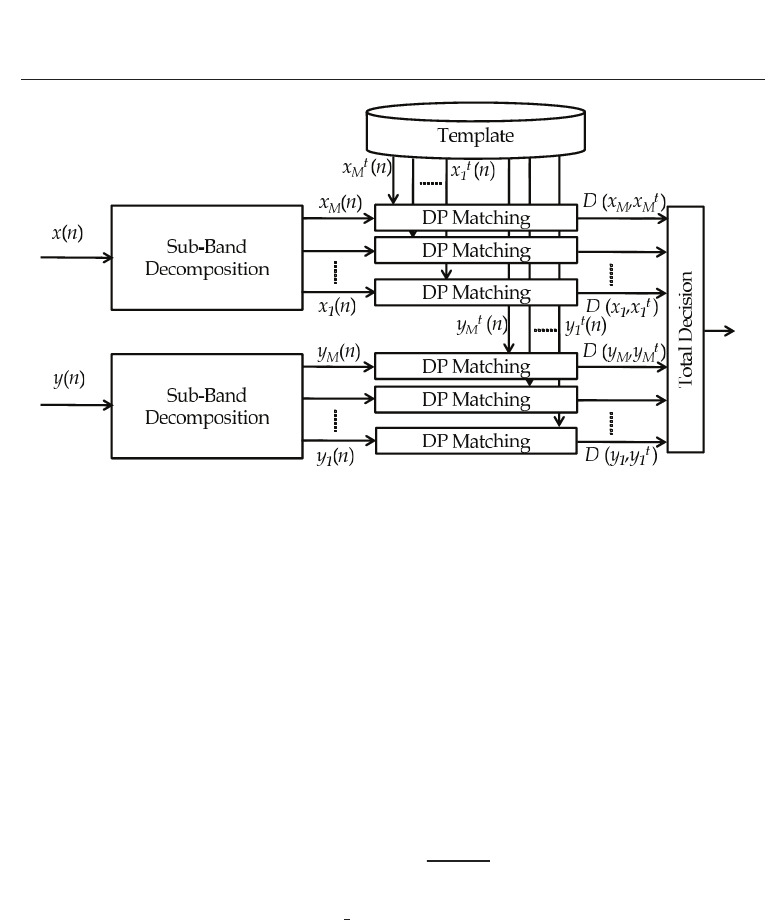
DWT Domain On-Line Signature Verification 3
Fig. 2. DWT domain on-line signature verification
given by x
(n) and y(n) where n = 0, 1, ···, S
n
− 1andS
n
is the number of sampled
data. They are respectively normalized in both time and amplitude domains and then
decomposed into sub-band signals using sub-band filters by the DWT (Nakanishi et al.,
2003; 2004; 2005). In advance of verification, sub-band signals are enrolled as a template
for each user. Templates are generated by ensemble-averaging several genuine signatures.
Please refer to Ref. (Nakanishi et al., 2003) for the details. At the verification stage, each
decomposed signal is compared with its template based on the DP matching and a DP distance
is obtained at each decomposed level. Final score is calculated by combing the DP distances
at appropriate sub-bands in both coordinates. Total decision is done by comparing the final
score with a threshold and it is verified whether the signature data are of genuine or not.
2.2 Feature extraction b y DWT
In the following, the x(n) and y(n) are represented as v(n) together for convenience. The
DWT of the pen-position data: v
(n) is defined as
u
k
(n)=
∑
m
v(m)Ψ
k,n
(m) (1)
where Ψ
k,n
(m) is a wavelet function and ·denotes the conjugate. k is a frequency (level) index.
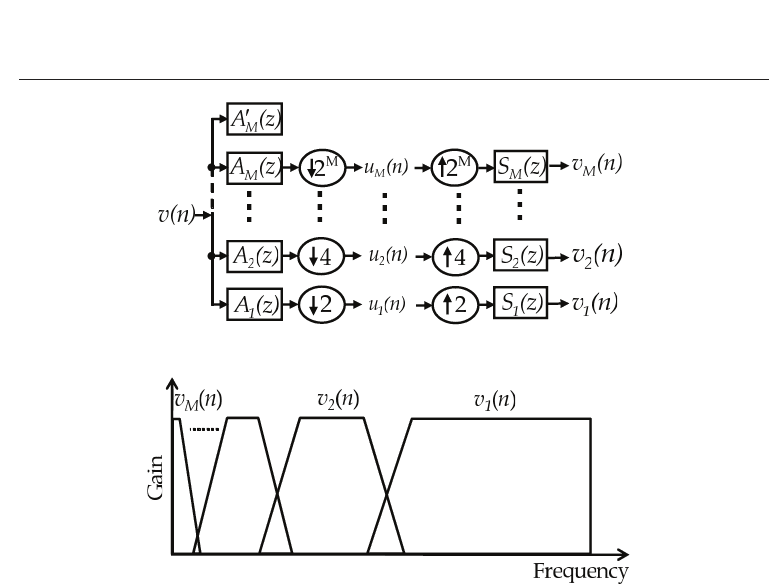
It is well known that the DWT corresponds to an octave-band filter bank (Strang & Nguyen,
1997) of which parallel structure and frequency characteristics are shown in Fig. 3, where
(
↓2
k
)and(↑2
k
) are down-sampling and up-sampling, respectively. M is the maximum level
of the sub-band, that is, the decomposition level. A
k
(z) and S
k
(z) (k = 1, ···, M) are analysis
filters and synthesis ones, respectively.
The synthesized signal: v
k
(n) in each sub-band is the signal in higher frequency band and
called Detail which corresponds to the difference between signals. Therefore, we adopt the
Detail as an enhanced individual feature which can be extracted with no specialized function:
pen-pressure, pen-altitude, and/or pen-direction which are not equipped in the PDA.
185
DWT Domain On-Line Signature Verification
4 Biometrics
(a) Parallel structure
(b) Frequency characteristics
Fig. 3. Sub-band decomposition by DWT
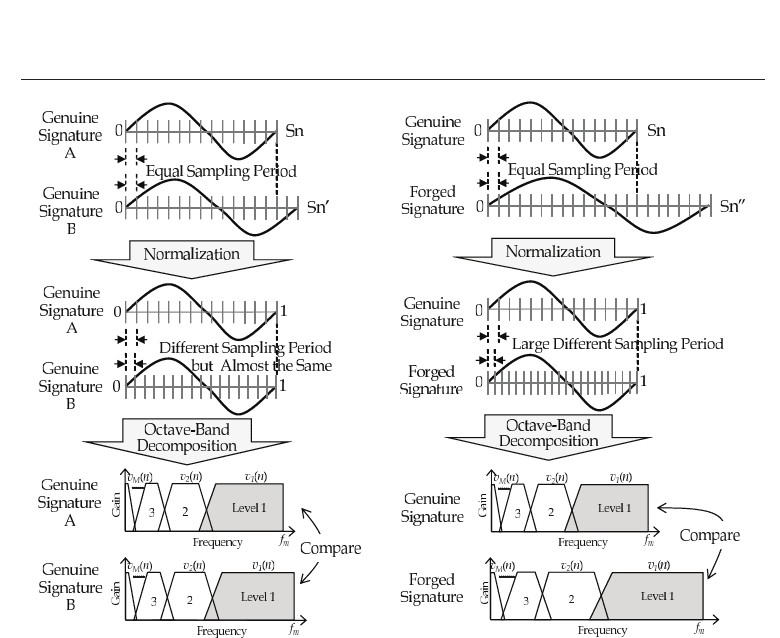
Let us get another perspective on the effect of the sub-band decomposition using Fig. 4. Each
signature is digitized at equal (common) sampling period using a pen-tablet system. In the
proposed system, writing time of all signatures is normalized in order to suppress intra-class
variation. Concretely, the sampling period of each signature is divided by the number of
sampled data and so becomes real-valued.
Even genuine signatures have different number of sampled data; therefore, all signatures have
different normalized sampling periods, that is, different sampling frequencies.
In general, variation of writing time in the genuine signatures is small, so that their sampling
periods (frequencies) are comparable as shown in Fig. 4 (a). On the other hand, in the case
of forged signatures, the variation of writing time is relatively large since it is not easy for
forgers to imitate writing speed and rhythm of genuine signatures. Thus, sampling periods
(frequencies) of the forged signatures become greatly different from those of the genuine
signatures as in Fig. 4 (b).
The maximum frequency: f
m
of the octave-band filter bank is determined by the sampling
frequency based on the “sampling theory". If the sampling frequencies are greatly different,
each octave band (decomposition level) includes greatly different frequency elements as
illustrated in (b). In other words, even if levels compared are the same, frequency elements
included in one level are d ifferent from the other, so that the differences between genuine
signatures and forged ones are accentuated.
186
Biometrics
DWT Domain On-Line Signature Verification 5
(a) Comparison of genuine signatures (b) Comparison of a genuine signature with its
forgery
Fig. 4. Effect of sub-band decomposition
The advantage was confirmed comparing with a time-domain method (Nakanishi et al., 2005).
Of course, if forgers imitate writing speed and rhythm of genuine signatures, it is impossible
for the proposed method to distinguish forged signatures from genuine ones.
2.3 Verification by DP matching
Since on-line signatures have large intra-class variation, one-to-one matching cannot be
applied in verification. In order to deal with the problem, the verification was performed
every stroke (intra-stroke or inter-stroke) in the conventional system (Nakanishi et al., 2003;
2004; 2005; 2008). However, a part of signature databases eliminates the data in inter-strokes
and so we could not apply the conventional system to such a database.
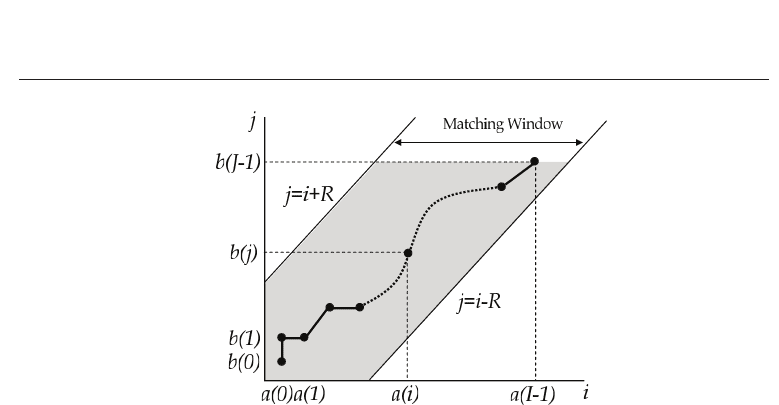
Therefore, we introduce DP matching into the verification process. The DP matching is
effective in finding the best combination between two data series even if they have different
number as illustrated in Fig. 5.
Letting the two data series be a
(i)(i = 0, 1, ···, I − 1) and b(j)(j = 0, 1, ···, J −1),thelocal
distance at kth is defined as
d
(k)=|a(i)
k
−b(j)
k
| (k = 0, 1, ···, K − 1) (2)
187
DWT Domain On-Line Signature Verification
6 Biometrics
Fig. 5. DP matching
where instead of i and j, k is used as another time index since these data are permitted to be
referred redundantly.
By accumulating the local distances in one possible combination between the two series, a DP
distance is given by
D
(a, b)=
K−1
∑
k=0
w(k)d(k) (3)
where w
(k) is a weighting factor. After calculating the DP distance in all possible
combinations, we can find the best combination by searching the combination with the
smallest DP distance.
Moreover, since the DP distance depends on the number of sampled data, the normalized DP
distance is used in general.
nD
(a, b)=D(a, b)/
K−1
∑
k=0
w(k) (4)
Assuming the weight is symmetric: (1-2-1) and the initial value is zero,
K−1
∑
k=0
w(k)=I + J.(5)
In the proposed method, the DP distance is obtained at each sub-band level. Let the DP
distance at lth level be D
(v, v
t
)
l
where v is sampled data series of a signature for verification
and v
t
is that of a template, the normalized DP distance is given by
nD
(v, v
t
)
l
= D( v, v
t
)
l
/(V
n
+ T
n
) (6)
where V
n
is the number of sampled data in the verification signature and T
n
is that of the
template.
188
Biometrics
