Wilamowski B.M., Irwin J.D. The Industrial Electronics Handbook. Second Edition: Industrial Communication Systems
Подождите немного. Документ загружается.

Ad Hoc Networks 7-3
rapid.deployment.of.these.systems.at.a.lower.cost,.without.having.to.lay.cables.to.each.sensor..To.sum.up,.
ad.hoc.netw
orks
.and.alte
rnative
.techn
ologies
.are.enab
ling
.direc
t
.inte
lligent
.comm
unication
.betw
een
.enti
-
ties.
.is.new.para
digm
.is.poised.to.chan
ge
.the.way.we.inte
ract
.with.the.worl
d
.and.perf
orm
.die
rent
.task
s.
7.1.3 ad Hoc Network Characteristic
One.of.the.key.characteristics.of.ad.hoc.networks.is.mobility.due.to.rapid.repositioning.of.nodes..ese.
node
s
.can.eith
er
.move.inde
pendently
.or.are.grou
ped
.toget
her
.whil
e
.thei
r
.move
ment
.can.be.rand
om
.
or.alon
g
.prep
lanned
.rout
es.
.ese.mobi
lity
.mode
ls
.can.have.major.impa
ct
.on.sele
cting
.an.appr
opriate
.
rout
ing
.sche
me,
.whic
h
.may.inu
ence
.the.perf
ormance
.of.the.netw
ork.
.Anot
her
.char
acteristic
.of.ad.hoc.
netw
orks
.is.mult
ihopping
.wher
e
.the.path.from.the.sour
ce
.to.dest
ination
.incl
udes
.seve
ral
.othe
r
.inte
rme-
diate
.node
s.
.Wide-
area
.ad.hoc.netw
orks
.oen.exhi
bit
.mult
iple
.hops.for.obst
acle
.nego
tiation,
.spec
trum
.
reus
e,
.and.ener
gy
.cons
ervation.
.Besid
es,
.an.ad.hoc.netw
ork
.must.eec
tively
.hand
le
.prob
lems
.pert
aining
.
to.add
ressing,
.rou
ting,
.clu
stering,
.posi
tion
.ide
ntication,
.and.pow
er
.con
trol,
.jus
t
.to.nam
e
.a.few
.
Another
.impo
rtant
.feat
ure
.of.the.ad.hoc.netw
orks
.is.ener
gy
.cons
ervation.
.Desig
ning
.ener
gy-ecient
.
proto
col
.is.crit
ical
.for.prol
onged
.oper
ation
.since.most.ad.hoc.node
s
.have.limi
ted
.powe
r.
.e.ad.hoc.
netw
orks
.can.some
times
.grow.up.to.seve
ral
.thou
sand
.node
s,
.all.movi
ng
.in.an.unpr
edictable
.mann
er.
.
Alth
ough
.it.may.be.possi
ble
.to.nd.an.ad.hoc.solu
tion
.for.a.few.fast.node
s
.or.for.a.very.larg
e
.num-
b
er
.of.stat
ic
.node
s,
.the.prob
lem
.aris
es
.when.a.larg
e
.numbe
r
.of.hete
rogeneous
.node
s
.move.in.rand
om
.
dire
ction
.with.die
rent
.spee
d
.over.an.unpr
edictable
.terr
ain.
.us,.mult
ihop,
.mobi
lity,
.and.larg
e
.net-
w
ork
.size.combi
ned
.with.vary
ing
.devi
ce
.char
acteristics
.(het
erogeneity,
.band
width,
.and.batt
ery
.powe
r
.
cons
traints)
.make.the.desig
n
.of.adeq
uate
.rout
ing
.proto
col
.a.major.chal
lenge.
.Besid
es,
.ad.hoc.netw
ork
.
shou
ld
.be.able.to.prev
ent
.any.atte
mpt
.from.intr
uders
.to.eave
sdrop
.and.jam.the.chan
nel.
.Due.to.open.
P2P.netw
ork
.arch
itecture,
.the.ad.hoc.netw
orks
.are.more.vuln
erable
.agai
nst
.mali
cious
.atta
cks
.than.the.
infr
astructured
.coun
terparts.
.ese.atta
cks
.can.be.acti
ve
.or.passi
ve;
.eith
er
.an.atta
cker
.acti
vely
.disru
pts
.
network.operations.or.simply.monitors.data,.controls.trac.patterns,.and.relays.this.information.to.
the.enem
y
.head
quarters.
.e.secu
rity
.for.ad.hoc.netw
orks,
.ther
efore,
.invo
lves
.key.esta
blishment,
.trus
t
.
setu
p,
.secu
re
.rout
ing,
.auth
entication,
.data.aggr
ession,
.etc.,.and.is.ther
efore
.a.lot.more.chal
lenging
.than.
in.con
ventional
.net
works.
7.1.4 Enabling technologies
IEEE. 802.11. WLAN. [802.11]. is. the. most. popular. technology. for. ad. hoc. networks.. ere. are. vari-
ous
. work
ing
. grou
ps
. for. the. stan
dards
. oer
ing
. high
est
. data. rate. up. to. 54.Mbps. and. enha
ncing
.
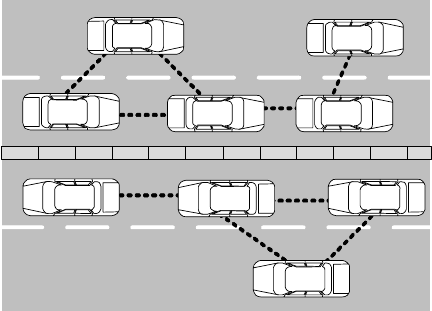
FIGURE 7.2 Vehicular.ad.hoc.networks.
© 2011 by Taylor and Francis Group, LLC

7-4 Industrial Communication Systems
quality-of-service.(QoS).parameters..It.supports.dynamic.frequency.selection,.transmit.power.control,.
and.spec
trum
.and.ener
gy
.mana
gement.
.Besid
es
.enha
nced
.secu
rity
.meas
ures,
.radi
o
.reso
urce
.mana
ge-
ment
.is.als
o
.inc
orporated.
Bluetooth
.[B04
]
.is.a.low-
power
.shor
t-range
.comm
unication
.tech
nology
.desig
ned
.to.conn
ect
.por-
t
able
.elec
tronic
.devi
ces
.like.phon
es,
.PDAs
,
.and.keyb
oards.
.When
ever
.two.Blue
tooth-enabled
.devi
ces
.
come.with
in
.rang
e
.of.one.anot
her,
.they.seam
lessly
.esta
blish
.a.smal
l
.netw
ork.
.Alth
ough
.the.maxi
mum
.
possi
ble
.data.rate.is.only.1.Mbps
,
.low-
cost
.and.low-
power
.capa
bilities
.of.Blue
tooth
.have.stim
ulated
.its.
pene
tration
.in.the.mar
ket.
Infrared
.is.a.poin
t-to-point,
.ultr
a
.low-
power,
.ad.hoc.data.tran
smission
.stan
dard
.desig
ned
.to.oper
ate
.
over.a.dist
ance
.of.1.m.and.is.exte
ndable
.to.2.m.with.high.powe
r.
.It.can.achi
eve
.data.rate
s
.up.to.16.Mbps
.
.
Infr
ared
.is.chea
per
.than.Blue
tooth
.tech
nology,
.and.both.have.thei
r
.own.adva
ntages
.and.disa
dvantages.
HomeRF
.is.a.shor
t-range
.comm
unication
.tech
nology
.inte
nded
.for.smal
l
.area.such.as.home
s
.or.smal
l
.
buil
dings.
.Home
RF
.uses.freq
uency
.hopp
ing
.spre
ad
.spec
trum
.(FHS
S)
.whil
e
.oper
ating
.at.2.4.GHz.and.
oer
s
.dat
a
.rat
es
.up.to.10.Mbps
.
ZigBee
.stan
dard
.is.a.shor
t-range
.wire
less
.comm
unication
.stan
dard
.for.PANs
.
.It.oer
s
.data.rate.up.
to.250.kbps.at.2.4.GHz,.40.kbps.at.915.MHz,.and.20.kbps.at.868.MHz.with.a.rang
e
.of.10–1
00
.m..ZigB
ee
.
uses.IEEE.802.
15.4
.as.physi
cal
.and.medi
um
.acce
ss
.cont
rol
.(MAC
)
.laye
rs.
.Uppe
r
.laye
rs
.as.well.as.ZigB
ee
.
secu
rity
.arc
hitecture
.are.de
ned
.by.the.Zig
Bee
.sta
ndard.
7.2 Protocol Stack
7.2.1 transport Layer
Transport.layer.protocols.are.responsible.for.end-to-end.delivery.of.data..Transmission.control.protocol.
(TCP
)
.is.a.domin
ant
.tran
sport
.laye
r
.prot
ocol
.for.wire
d
.netw
orks.
.TCP.is.resp
onsible
.for.cong
estion
.and.ow.
cont
rol,
.and.reli
able
.and.in-o
rder
.deli
very
.of.pack
ets.
.e.uniq
ue
.char
acteristics
.of.wire
less
.ad.hoc.netw
orks
.
such.as.lack.of.infra
structure,
.mobi
lity,
.shar
ed
.band
width
.[SAH
S03],
.cont
ention,
.and.high.bit.erro
r
.rate.
(BER
)
.as.well.as.the.desi
gn
.prin
ciples
.of.TCP.moti
vate
.to.desi
gn
.cust
omized
.tran
sport
.laye
r
.prot
ocols.
7.2.1.1
Why tCP Doe
s Not Suit
ad Hoc Ne
tworks?
e
.fai
lure
.of.TCP.to.wor
k
.wel
l
.in.ad.hoc.net
works
.is.bec
ause
.of.the.fol
lowing
.kno
wn
.pro
blems:
•
. In. laye
red
.arch
itectures,
. TCP. impl
icitly
.assu
mes
.that. pack
et
. loss. is.caus
ed
. due. to.coll
isions.
.
Whereas,.collisions.in.ad.hoc.wireless.networks.are.one.of.the.possible.causes.of.packet.loss,.
alth
ough
.ther
e
.are.also.othe
r
.pote
ntial
.caus
es
.such.as.fadi
ng,
.vary
ing
.link.qual
ity
.[CZW
F04],
.
inte
rference,
.and.noi
se.
•
. Two.comm
unicating
.node
s
.as.well.as.othe
r
.node
s
.shar
ing
.the.same.medi
um
.cont
end
.for.the.medi
um.
•
. e.pack
et
.loss.in.wire
less
.netw
orks
.is.comp
aratively
.high
er,
.and.loss.of.retr
ansmitted
.pack
et
.
furt
her
.deg
rades
.the.per
formance.
7.2.1.2
trans
port Layer Protocols for
ad Hoc Ne
tworks
Transport
.laye
r
.proto
cols
.for.ad.hoc.netw
orks
.can.broa
dly
.be.clas
sied
.into.two.major.appr
oaches
.
[MK0
4];
.TCP.var
iants
.and.non
-TCP
.var
iants.
e
.basic.idea.of.TCP.vari
ants
.is.to.reta
in
.TCP.as.a.tran
sport
.laye
r
.proto
col,
.beca
use
.of.its.glob
al
.
exis
tence,
.and.to.sugg
est
.modi
cations
.in.orde
r
.to.over
come
.the.prob
lems
.asso
ciated
.with.wire
less
.link
s
.
and.mobi
lity.
.TCP.feed
back
.(TCP
-f)
.[F94
]
.is.custo
mized
.in.such.a.way.that.the.send
er
.is.able.to.die
r-
entiate
.betw
een
.cong
estion
.and.a.lost.link
.
.In.this.way,.the.invo
cation
.of.cong
estion
.cont
rol
.algo
rithm
.
is.rest
ricted,
.whic
h
.in.turn.stops.perf
ormance
.degr
adation.
.In.case.of.link.fail
ure,
.the.send
er
.node.is.
expl
icitly
.noti
ed
.by.the.netw
ork
.laye
r
.of.the.neig
hbor
.node
.
.e.send
er
.stops.send
ing
.furt
her
.pack
ets,
.
whil
e
.all.othe
r
.node
s
.list
ening
.to.thes
e
.noti
cations
.inva
lidate
.thes
e
.rout
es
.to.avoi
d
.pack
et
.loss
.
.Expl
icit
.
© 2011 by Taylor and Francis Group, LLC
Ad Hoc Networks 7-5
link.failure.notication.(ELFN).is.a.technique.similar.to.TCP-f.where.route.failures.are.notied.to.
dow
nstream
.nod
es
.in.ELF
N
.mes
sage
.sen
t
.by.ups
tream
.nod
es
.of.the.fai
led
.lin
k.
.Ano
ther
.TCP.var
iant
.is.
ad.hoc.TCP.[LS
01]
.whi
ch
.req
uires
.net
work
.lay
er
.fee
dback
.and.spl
it
.TCP.[KK
FT02]
.to.dea
l
.wit
h
.con
ges-
tion
.co
ntrol
.an
d
.en
d-to-end
.re
liability
.se
parately.
In
.the.non
-TCP
.var
iant
.app
roach,
.the.tra
nsport
.lay
er
.is.bui
lt
.fro
m
.scr
atch
.whi
le
.con
sidering
.the.
lim
itations
.of.wir
eless
.ad.hoc.net
works.
.Alt
hough
.thi
s
.app
roach
.out
performs
.TCP.var
iants
.app
roach
.
in.a.sta
nd-alone
.env
ironment
.[MK
04,
.p..130
],
.it.pos
es
.man
y
.cha
llenges
.whe
n
.the.mac
hines
.wit
h
.suc
h
.
tra
nsport
.lay
er
.hav
e
.to.tal
k
.to.the.glo
bal
.Int
ernet.
.Ad.hoc.tra
nsport
.pro
tocol
.(AT
P),
.one.of.the.non
-TCP
.
var
iants,
.is.spe
cically
.bui
lt
.for.ad.hoc.net
works.
.ATP.exp
loits
.syn
ergies
.bet
ween
.di
erent
.lay
ers
.to.
enh
ance
.per
formance.
.As.men
tioned
.ear
lier,
.one.of.the.dis
advantages
.of.ATP.is.its.inc
ompatibility
.wit
h
.
sys
tems
.th
at
.ar
e
.ru
nning
.pl
ain
.TC
P.
A
.rel
iable
.tra
nsport
.pro
tocol
.for.ad.hoc.net
works
.is.sti
ll
.nee
ded.
.Whi
le
.desi
gning
.a.tra
nsport
.lay
er
.
pro
tocol,
.th
e
.ke
y
.tr
ade-o
.is.be
tween
.co
mpatibility
.an
d
.pe
rformance
.of.th
e
.ne
twork.
7.2.2 Network Layer
Routing.is.used.to.send.the.data.from.source.to.destination..e.easiest.way.is.to.broadcast.the.data.in.
the.net
work
.tha
t
.is.was
teful
.of.the.ban
dwidth
.res
ource.
.A.mor
e
.ec
ient
.way.is.to.com
pute
.rou
te
.fro
m
.
sou
rce
.to.des
tination
.and.sen
d
.dat
a
.in.a.mul
tihop
.fas
hion.
.er
e
.are.di
erent
.way
s
.to.cla
ssify
.rou
ting
.
pro
tocols.
.e.rou
ting
.pro
tocols
.can.be.cla
ssied
.on.the.basi
s
.of.(a).the.way.the.rou
ting
.inf
ormation
.is.
upd
ated,
.(b).net
work
.str
ucture
.(a
t
.and.hie
rarchical),
.and.(c).posi
tion
.and.non
position-based
.rou
ting
.
pro
tocols.
.e.di
erent
.ca
tegories
.ar
e
.di
scussed
.in.th
e
.fo
llowing
.se
ctions.
7.2.2.1
Pro
active,
react
ive, and Hybrid
rout
ing Protocols
Proactive
.rou
ting
.pro
tocols
.are.als
o
.kno
wn
.as.tab
le-driven
.pro
tocols.
.e.con
sistent
.and.up-
to-date
.
rou
ting
.tab
les
.are.com
puted
.ahe
ad
.of.tra
nsmission
.tim
e.
.Whe
never
.topo
logy
.cha
nges,
.upd
ate
.mes
-
sages
.are.tri
ggered
.to.ass
ure
.con
sistency
.of.net
work
.map.bei
ng
.mai
ntained
.at.eac
h
.nod
e.
.Des
tination-
sequenced
.dis
tance
.vec
tor
.(DS
DV)
.[PP
94]
.is.a.pro
active
.rou
ting
.pro
tocol,
.whi
ch
.use
s
.Bel
lman
.For
d
.
alg
orithm
.to.com
pute
.the.sho
rtest
.pat
h
.and.ens
ures
.loo
p-free
.rou
ting
.tab
les.
.Wire
less
.rou
ting
.pro
tocols
.
(WR
P)
.[MS
GJ96],
.bas
ed
.on.imp
roved
.Bel
lman
.For
d,
.res
trict
.rou
te
.upd
ates
.to.imm
ediate
.nei
ghbors
.
onl
y.
.e.clu
ster
.gat
eway
.swi
tch
.rou
ting
.(CG
SR)
.red
uces
.rou
ting
.tab
le
.size.and.rou
ting
.inf
ormation
.
exc
hange
.by.emp
loying
.a.clu
stering
.hie
rarchy
.whe
re
.onl
y
.the.clu
ster
.hea
ds
.com
municate
.amo
ng
.the
m-
selves.
.Opti
mized
.lin
k
.sta
te
.rou
ting
.(OL
SR)
.is.a.dis
tributed,
.tab
le-driven,
.and.pro
active
.rou
ting
.pro
to-
col
.for.mob
ile
.ad.hoc.net
works
.tha
t
.wor
k
.on.the.pri
nciple
.of.“mu
ltipoint
.rel
ays,”
.whi
ch
.mea
ns
.sel
ecting
.
a.set.of.nod
es
.fro
m
.wit
hin
.one
-hop
.nei
ghbor
.to.pro
vide
.abi
lity
.to.rea
ch
.all.the.two
-hop
.nei
ghbors.
.OLS
R
.
works.well.in.large-scale.and.high-density.network.but.incurs.large.routing.overhead.
Overhead
.of.per
iodic
.upd
ates,
.slo
w
.rou
te
.rep
air,
.and.mai
ntenance
.of.unu
sed
.rou
ting
.inf
ormation
.
are.few.of.the.pro
blems
.of.the.pro
active
.rou
ting
.pro
tocols.
.To.ove
rcome
.the
se
.iss
ues,
.rea
ctive
.rou
ting
.
pro
tocols
.ha
ve
.be
en
.de
signed.
Unlike
.the.pro
active
.rou
ting
.pro
tocols,
.the.rea
ctive
.rou
ting
.pro
tocols
.do.not.mai
ntain
.rou
ting
.tab
les
.
and.com
pute
.rou
tes
.whe
never
.req
uired.
.es
e
.are.als
o
.kno
wn
.as.“on
-demand”
.rou
ting
.pro
tocols.
.Rou
te
.
dis
covery
.is.acc
omplished
.by.oo
ding
.req
uest
.in.the.net
work.
.Alt
hough,
.les
s
.con
trol
.ove
rhead
.mak
es
.
the
m
.sca
lable,
.lar
ger
.del
ays
.are.inc
urred
.whi
le
.dis
covering
.rou
te
.whe
never
.nee
ded.
.Dyn
amic
.sou
rce
.
rou
ting
.(DS
R)
.[DD
96]
.and.ad.hoc.on-
demand
.dis
tance
.vec
tor
.(AO
DV)
.[PR
99]
.are.two.exa
mples
.of.
rea
ctive
.pro
tocols.
.AOD
V
.is.bas
ed
.on.DSD
V
.but.is.rea
ctive
.and.loo
p
.fre
e.
.Tem
porally
.ord
ered
.rou
ting
.
alg
orithm
.(TOR
A)
.[PC
97]
.is.a.rea
ctive
.sch
eme
.and.is.uni
quely
.fea
tured
.by.mai
ntaining
.mul
tiple
.pat
hs
.
bet
ween
.gi
ven
.pa
ir
.of.so
urce
.an
d
.de
stination
.no
des.
ere
.are.di
erent
.rou
ting
.pro
tocols
.whi
ch
.exh
ibit
.a.hyb
rid
.app
roach
.for.rou
ting,
.for.exa
mple,
.zon
e-
based
.rou
ting
.(ZB
R)
.[DH
Y03].
.ZBR.is.mor
e
.sui
table
.for.lar
ge
.net
works
.whe
re
.the.net
work
.is.div
ided
.into.
clusters..Intracluster.routing.is.proactive.while.intercluster.routing.is.reactive.in.ZBR..Other.protocols.
© 2011 by Taylor and Francis Group, LLC
7-6 Industrial Communication Systems
in.this.category.comprise.core.extraction.distributed.ad.hoc.routing.(CEDAR).protocol.[SSB99].and.
zone-based.hierarchical.link.state.(ZHLS).routing.protocol.
7.2.2.2
Flat and Hierarchical routing Protocols
Hierarchical
.routing.protocols.arrange.nodes.in.the.form.of.clusters.or.trees.where.every.cluster.has.a.clus-
ter
.head..Cluster.heads.may.also.aggregate.data.from.cluster.nodes.to.reduce.the.number.of.packet.trans-
missions
.and.hence.conserve.energy.[CPF05].or.may.provide.gateway.to.external.networks..Advantages.
of.hierarchical.routing.protocols.include.scalability.and.ecient.communication.[AK04]..AODV,.DSDV,.
and.DSR.are.examples.of.at.routing.protocols,.while.CGSR.is.an.example.of.hierarchical.routing.scheme.
7.2.2.3
Position- and Nonposition-Based routing Protocols
It
.is.experimentally.veried.that.reactive.and.proactive.routing.protocols,.including.AODV,.DSDV,.and.DSR.
that.do.not.use.location.information.in.routing.decisions,.face.scalability.issues.as.opposed.to.location-based.
routing.strategies.[S02]..Location-based.routing.depends.upon.the.physical.position.of.the.nodes.in.the.net-
work
.to.take.routing.decisions.[MWH01]..To.get.location/position.information,.the.node.may.use.a.low-
power
.global.positioning.system.(GPS).if.the.nodes.are.outdoor.or.may.rely.on.relative.positioning.techniques.
based.on.the.signal.strength.or.manual.registration.process..Several.position-based.routing.schemes.[SL01].
have.already.been.presented.by.the.research.community..Position-based.routing.algorithms.are.classied.into.
greedy.and.restricted.directional.ooding..In.greedy.approaches,.the.distance.toward.the.sink.node.is.either.
maximized.or.minimized.depending.upon.forwarding.strategy,.while.in.directional.ooding,.the.data.are.
always.ooded.toward.the.nodes.which.are.in.the.direction.of.the.destination.node..Greedy.perimeter.state-
less
.routing.(GPSR).[KK00].and.geographic.distance.routing.(GEDIR).[SL01].are.examples.of.position-based.
routing.protocols.working.on.the.principle.of.greedy.forwarding.approach.
7.2.3 MaC Layer
MAC.schemes.are.used.to.dene.policy.for.accessing.the.shared.medium.in.ad.hoc.networks..Limited.
spectrum,. multiple.access,. node.mobility,. error-prone. environment,. and. characteristics. of. wireless.
medium.like.noise,.fading,.and.interference.compel.to.design.MAC.schemes.customized.for.wireless.
environments..e.MAC.schemes.for.ad.hoc.networks.can.be.classied.into.contention-free.and.con-
tention-based
.protocols..Contention-free.protocols.work.better.in.infrastructure-driven.networks.with.
a.master.node.controlling.the.medium.access..Contention-based.protocols.work.in.a.decentralized.fash-
ion
.and.can.be.divided.into.random.access.and.controlled.access.(scheduling-.and.reservation-based).
protocols..e.performance.of.such.protocols.is.deteriorated.by.hidden.and.exposed.terminal.problems.
and.requires.special.attention.
Let
.us.assume.that.node-1.is.sending.data.to.node-2,.as.shown.in.Figure.7.3..Furthermore,.assume.
that.node-3.is.also.about.to.send.data.to.node-2..As.node-3.is.out.of.the.transmission.range.of.node-1,.
Range of 1 Range of 2 Range of 3
1 2 3 4
FIGURE 7.3 Hidden.and.exposed.terminal.problem.
© 2011 by Taylor and Francis Group, LLC
Ad Hoc Networks 7-7
it.will.sense.the.medium.as.free.and.sends.data.to.node-2.which.will.result.in.a.collision..is.is.known.as.
hid
den
.ter
minal
.pro
blem;
.nod
e-1
.and.nod
e-3
.are.hid
den
.fro
m
.eac
h
.oth
er.
.is.iss
ue
.is.sol
ved
.by.req
uest-
to-send/clear-to-send
.(RT
S/CTS)
.mec
hanism.
.Now
,
.ass
ume
.tha
t
.nod
e-3
.kno
ws
.by.RTS
/CTS
.mec
hanism
.
tha
t
.nod
e-1
.and.nod
e-2
.are.com
municating;
.it.wil
l
.ref
rain
.fro
m
.com
municating
.wit
h
.nod
e-4
.as.wel
l,
.
tho
ugh
.nod
e-4
.is.bey
ond
.the.ran
ge
.of.nod
e-2
.and.thu
s
.cha
nnel
.cap
acity
.wil
l
.be.unn
ecessarily
.was
ted.
.
is.is.kn
own
.as.ex
posed
.te
rminal
.pr
oblem.
7.2.3.1
r
and
om
acce
ss Schemes
In
.ran
dom
.acc
ess
.sch
emes
.(al
so
.kno
w
.as.con
tention-based
.sch
eme),
.nod
es
.con
tend
.for.the.sha
red
.
cha
nnel
.wit
h
.the.nei
ghboring
.nod
es
.(no
des
.wit
hin
.int
erference
.ran
ge)
.and.the.win
ning
.nod
es
.get.
hol
d
.of.the.med
ium.
.Suc
h
.sch
emes
.can
not
.gua
rantee
.QoS.bec
ause
.acc
ess
.to.the.cha
nnel
.is.not.gua
r-
anteed
.and.is.ran
dom.
.In.ALO
HA
.[N7
0],
.a.nod
e
.sim
ply
.sen
ds
.dat
a
.as.soo
n
.as.it.is.ava
ilable.
.Slo
tted
.
ALO
HA
.int
roduces
.tim
e
.div
ision
.mul
tiple
.acc
ess
.(TD
MA)–like
.tim
e-slots
.to.red
uce
.the.num
ber
.of.
col
lisions.
.Car
rier
.sen
se
.mul
tiple
.acc
ess
.(CS
MA)–based
.sch
emes
.fur
ther
.enh
ance
.the.per
formance
.by.
car
rier
.sen
se
.mec
hanism.
.e.per
formance
.of.all.suc
h
.sch
emes
.is.adv
ersely
.ae
cted
.by.hid
den
.and.
exp
osed
.ter
minal
.pro
blem.
7.2.3.2
r
ese
rvation-Driven Contention-Based
acce
ss
In
.ord
er
.to.ove
rcome
.the.pro
blems
.of.hid
den
.and.exp
osed
.ter
minal
.pro
blems,
.dyn
amic
.rese
rvation-based
.
protocols.are.designed,.which.operates.on.the.basis.of.RTS/CTS.mechanism..In.such.protocols,.a.node.
ini
tiates
.the.rese
rvation
.pro
cess
.if.it.has.some.dat
a
.to.send
.
.e.send
ing
.nod
e
.send
s
.an.RTS.pac
ket
.to.the.
nex
t
.hop
.
.e.nex
t
.hop.in.tur
n
.rep
lies
.by.a.CTS.mes
sage.
.Suc
h
.a.CTS.is.hea
rd
.by.oth
er
.nod
es
.in.the.vic
in-
ity,
.and.the
y
.kee
p
.qui
et
.unl
ess
.the.dat
a
.are.act
ually
.sent.by.the.ini
tiating
.nod
e.
.MAC.lay
er
.de
ned
.by.IEE
E
.
802
.11
.sta
ndard
.inc
ludes
.dis
tributed
.coo
rdination
.fun
ction
.(DCF
)
.and.poi
nt
.coo
rdination
.fun
ction
.(PC
F).
.
DCF.is.based.on.CSM
A/CA
.and.uses.RTS
-CTS-DATA-ACK
.mech
anism
.for.dat
a
.tra
nsmission,
.whi
le
.PCF.
is.des
igned
.for.inf
rastructure-based
.net
works.
.Oth
er
.imp
ortant
.pro
tocols
.in.thi
s
.cat
egory
.inc
ludes
.mul
-
tiple
.acce
ss
.col
lision
.avo
idance
.(MA
CA)
.[K9
0],
.MAC
A
.for.wir
eless
.LAN
s
.(MA
CAW)
.[BD
SZ94],
.and.oo
r
.
acq
uisition
.mul
tiple
.acce
ss
.(FA
MA)
.[FG
95],
.whi
ch
.are.all.based.on.CSM
A/CA.
7.2.3.3
Sch
eduling-Driven Contention-Based
acce
ss
Such
.pro
tocols
.are.desi
gned
.to.pro
vide
.a.cer
tain
.lev
el
.of.QoS
.
.Sch
eduling
.can.be.a.fun
ction
.of.di
erent
.
par
ameters,
.for.exa
mple,
.rem
aining
.nod
e
.ene
rgy,
.tra
c
.loa
ds,
.and
/or
.bou
nd
.on.pac
ket
.del
ays.
.Som
e
.
of.the.sch
eduling-driven
.MAC.sch
emes
.inc
lude
.dis
tributed
.pri
ority
.sch
eduling
.and.med
ium
.acc
ess
.
[KL
SSK02]
.an
d
.di
stributed
.la
xity-based
.pr
iority
.sc
heduling
.sc
heme
.[K
MS05].
7.2.4 Physical Layer
Physical.layer.translates.communication.requests.from.the.upper.layers.into.hardware-specic.opera-
tions
.to.ena
ble
.tra
nsmission
.or.rec
eption
.of.sign
als.
.es
e
.ope
rations
.nor
mally
.inv
olve
.tim
e
.and.fre
-
quency
.syn
chronization
.whi
le
.als
o
.dea
ling
.wit
h
.har
sh
.tim
e
.var
iant
.and.fre
quency-selective
.wir
eless
.
cha
nnels.
.Besi
des,
.the.per
formances
.can.be.sev
erely
.com
promised
.by.int
erference
.ori
ginating
.fro
m
.
oth
er
.ter
minals
.ope
rating
.on.non
orthogonal
.res
ources,
.the
reby
.req
uiring
.ec
ient
.rec
eive
.str
ategies
.
whi
ch
.giv
e
.goo
d
.com
plexity
.per
formance
.tra
de-o.
.Her
e,
.we.giv
e
.an.ove
rview
.of.phy
sical
.lay
er
.spe
ci-
cation
.for.onl
y
.two.mai
n
.sta
ndards
.sup
porting
.ad.hoc.wir
eless
.net
works,
.i.e
.,
.the.IEE
E
.802
.11
.sta
n-
dard
.for.WLA
Ns
.[80
2.11]
.and.the.Blu
etooth
.spe
cications
.for.sho
rt-range
.wir
eless
.com
munications
.
[B0
1,FBP98].
.e.rs
t
.one.not.onl
y
.all
ows
.sin
gle-hop
.WLA
N
.ad.hoc.net
work
.but.can.also.be.ext
ended
.to.
mul
tihop
.net
works
.cov
ering
.are
as
.of.sev
eral
.squ
are
.kil
ometers,
.whi
le
.the.sec
ond
.one.can.onl
y
.be.use
d
.
to.bu
ild
.sm
aller
.sc
ale
.ad.ho
c
.wi
reless
.bo
dy
.an
d
.PA
Ns.
IEEE
.802
.11
.is.the.rs
t
.wir
eless
.loc
al
.are
a
.net
work
.sta
ndard
.wit
h
.dat
a
.rat
es
.of.up.to.2.Mbp
s
.[80
2.11].
.
e.ori
ginal
.sta
ndard
.has.the
n
.bee
n
.ext
ended
.to.802
.11b,
.802
.11a,
.and.802
.11g
.whi
ch
.ope
rate
.in.the.
© 2011 by Taylor and Francis Group, LLC

7-8 Industrial Communication Systems
2.4.and.5.GHz.unlicensed.band..e.peak.data.rates.of.11.Mbps.are.supported.by.802.11b.and.54.Mbps.
for.802.
11a
.and.802.
11g.
.Die
rent
.tran
smission
.tech
nologies
.such.as.infr
ared,
.orth
ogonal
.freq
uency
.
doma
in
.mult
iplexing
.(OFD
M),
.FHSS
,
.and.dire
ct
.sequ
ence
.spre
ad
.spec
trum
.(DSS
S)
.can.be.empl
oyed.
.
For.any.give
n
.band
width,
.thes
e
.stan
dards
.supp
ort
.die
rent
.data.rate
s
.by.sele
cting
.die
rent
.modu
la-
tion
.sche
mes,
.i.e.,.DBPS
K,
.DQPS
K,
.16-Q
AM,
.etc..Besid
es,
.half.rate.conv
olution
.code
s
.are.used.with.
punc
turing
.to.ensu
re
.reli
able
.data.tran
sfer
.for.a.give
n
.QoS..Sync
hronization
.is.achi
eved
.by.send
ing
.a.
pred
ened
.sequ
ence
.whic
h
.aler
ts
.the.rece
iver
.that.a.signa
l
.is.pres
ent.
.is.is.foll
owed
.by.star
t
.fram
e
.
deli
miter
.whic
h
.den
es
.the.begi
nning
.of.a.fram
e.
.e.next.gene
ration
.for.802.
11
.is.802.
11n,
.whic
h
.is.
desig
ned
.to.ee
ctively
.rep
lace
.all.the.pre
vious
.802
.11
.sta
ndards
.and.ena
bles
.spe
ed
.up.to.540.Mbps
.
e
.Blue
tooth
.tech
nology
.is.the.comm
only
.adopt
ed
.stan
dard
.for.low-
cost,
.shor
t-range
.radi
o
.link
s
.
betw
een
.die
rent
.port
able
.devi
ces
.[MB0
0].
.Also
,
.base
d
.on.the.port
ions
.of.the.Blue
tooth
.spec
ication,
.
the.IEEE.802.
15
.has.been.put.forw
ard
.as.a.WPAN.stan
dard.
.Like.802.
11,
.the.Blue
tooth
.syst
em
.is.oper
-
ating
.in.the.2.4.GHz.indu
strial,
.scie
ntic,
.and.medi
cine
.band.(ISM
).
.e.modu
lation
.uses.Gaus
sian
.
freq
uency
.shi.keyi
ng
.(GFS
K)
.with.a.maxi
mum
.freq
uency
.devi
ation
.of.140–
175
.kHz..e.tran
smission
.
tech
nology
.adopt
ed
.is.FHSS
,
.wher
e
.hopp
ing
.at.up.to.1600.hops
/s
.amon
g
.79.chan
nels,
.whic
h
.are.spac
ed
.
at.1.MHz.sepa
ration.
.e.maxi
mum
.tran
smission
.powe
r
.depe
nds
.upon.whic
h
.of.the.thre
e
.powe
r
.clas
ses
.
(as.den
ed
.by.the.stan
dard)
.are.supp
orted
.and.rang
es
.from.1.to.100.mW..A.maxi
mum
.base
-band
.data.
rate.of.723.
2
.kbps.is.supp
orted
.for.each.link
,
.with.optio
ns
.for.1/3.rate.repe
tition
.and.2/3.rate.Hamm
ing
.
forw
ard
.err
or
.cor
rection
.cod
es.
7.3 Performance Evaluation
Traditionally,.the.performance.evaluation.of.ad.hoc.networks.has.been.done.on.a.layer-by-layer.basis..
New.proto
cols
.are.prop
osed
.at.a.cert
ain
.laye
r,
.and.perf
ormance
.stud
ies
.comp
are
.them.with.one.anot
her
.
for.a.numbe
r
.of.scen
arios
.and.vary
ing
.cond
itions.
.e.key.issu
es
.in.the.desig
n
.and.perf
ormance
.of.
MANE
Ts
.are.comp
rehensively
.pres
ented
.in.the.auth
oritative
.refe
rence
.[CCL
03].
.Scor
es
.of.stud
ies
.com-
p
are
.MAC.proto
cols
.for.both.rand
om
.acce
ss
.and.rese
rvation-based
.sche
mes
.for.use.in.ad.hoc.wire
less
.
netw
orks
.pres
enting
.nove
l
.idea
s.
.Simi
larly
.at.the.netw
ork
.laye
r,
.the.perf
ormance
.eval
uation
.of.a.numbe
r
.
of.rout
ing
.prot
ocols
.for.a.vari
ety
.of.work
load
.scen
arios
.has.been.simu
lated
.[B04
].
.More.rece
nt
.and.
comp
rehensive
.simul
ation
.resu
lts
.using.OPNE
T
.Mode
ler
.10.5.[IR1
]
.have.been.carr
ied
.out.for.the.most.
comm
only
.used.rout
ing
.proto
cols,
.for.inst
ance
.AODV
,
.DSR,.and.TORA.[AA0
6].
.Simi
larly,
.the.per-
f
ormance
.of.tran
sport
.laye
r
.proto
cols
.over.MANE
Ts
.has.been.consi
dered
.in.a.numbe
r
.of.stud
ies
.and.
sche
mes
.such.as.dela
ying
.ACKs.[CGL
S08]
.or.using.a.frac
tional
.wind
ow
.incr
ement
.(FeW
)
.have.been.
rece
ntly
.pres
ented
.[WHX
09].
.In.the.same.vein
,
.the.impa
ct
.of.P2P.tra
c
.on.vari
ous
.rout
ing
.proto
cols
.
in.MANE
TS
.has.been.eval
uated
.in.[OSL
05].
.A.consi
deration
.that.cuts.acro
ss
.all.stud
ies
.is.the.choi
ce
.
of.the.mobi
lity
.mode
l.
.Most.stud
ies
.assu
me
.a.rand
om
.way.poin
t
.mobi
lity
.mode
l
.whic
h
.may.not.be.the.
most.appr
opriate
.mode
l
.for.ad.hoc.netw
orks.
.A.comp
rehensive
.fram
ework
.for.eval
uating
.the.impa
ct
.of.
mobi
lity
.in.ad.hoc.netw
orks
.is.pres
ented
.in.[BSH
03],
.and.more.rece
nt
.stud
ies
.have.eval
uated
.the.impa
ct
.
of.the.mobi
lity
.mode
l
.on.rout
ing
.proto
cols
.[TBD
07].
.A.furt
her
.consi
deration
.espe
cially
.for.sens
or
.net-
w
orks
.is.ener
gy
.eci
ency,
.and.a.numbe
r
.of.stud
ies
.pres
ent
.ener
gy-ecient
.sche
mes
.both.at.the.MAC.
and.at.the.net
work
.lay
er
.in.ord
er
.to.inc
rease
.nod
e
.lif
e.
e
.performance.modeling.of.ad.hoc.networks.is.a.complex.problem,.primarily.due.to.the.fact.that.
the.rese
arch
.comm
unity
.does.not.have.a.uni
ed
.fram
ework
.for.unde
rstanding
.the.inte
raction
.of.MAC.
laye
r,
.cong
estion,
.inte
rference,
.netw
ork
.codi
ng,
.and.reli
ability
.[KHP
08].
.e.perf
ormance
.eval
uation
.
of.ad.hoc.netw
orks
.is.furt
her
.comp
ounded
.by.the.choi
ce
.of.the.mobi
lity
.mode
l
.as.well.as.by.the.traf
-
c
.patt
erns
.[PDH
07],
.wher
ein
.it.has.been.demo
nstrated
.that.the.choi
ce
.of.more.repr
esentative
.tra
c
.
patt
erns
.migh
t
.prod
uce
.resu
lts
.that.are.die
rent
.than.trad
itional
.choi
ces
.of.tra
c
.sour
ces.
.Cros
s-layer
.
desig
ns
.have.been.a.major.them
e,
.and.nove
l
.stac
ks
.have.been.prop
osed
.to.impr
ove
.the.perf
ormance
.of.
ad.hoc.and.sens
or
.netw
orks.
.Unde
rstanding
.the.role.and.inte
ractions
.betw
een
.each.subc
omponent
.will.
impr
ove
.our.und
erstanding
.of.the
se
.com
plex
.dis
tributed
.sys
tems.
© 2011 by Taylor and Francis Group, LLC

Ad Hoc Networks 7-9
7.4 Challenges and Issues
7.4.1 Quality-of-Service
With.the.increase.in.portable.computing.devices.and.demand.for.multimedia.applications,.the.impor-
tance
.of.prov
iding
.QoS.in.ad.hoc.netw
orks
.will.cert
ainly
.grow
.
.ere.are.two.key.chal
lenges
.in.prov
id-
ing
.QoS.over.ad.hoc.netw
orks:
.the.ckl
e
.natu
re
.of.the.radi
o
.chan
nel
.and.the.mobi
lity
.of.the.node
s.
.
e.vary
ing
.qual
ity
.of.the.tran
smission
.chan
nel
.due.to.inte
rference
.and.fadi
ng
.resu
lts
.in.dyna
mically
.
chan
ging
.BERs.and.band
width
.thro
ughput
.as.well.as.prob
lems
.for.the.netw
ork
.laye
r
.in.dist
inguishing
.
betw
een
.cong
estion
.or.link
-layer
.loss
.
.Furt
hermore,
.it.is.dic
ult
.to.appl
y
.conv
entional
.tech
niques
.that.
esti
mate
.the.eec
tive
.band
width
.at.a.node.for.prov
iding
.QoS.in.orde
r
.to.ensu
re
.band
width
.rese
rvation,
.
admi
ssion
.cont
rol,
.poli
cing,
.and.ow.cont
rol
.in.ad.hoc.netw
orks.
.e.surv
ey
.pape
rs
.by.[KRD
06]
.and.
[RKM
M06]
.prov
ide
.an.exce
llent
.over
view
.to.the.issu
es
.and.chal
lenges
.by.prov
iding
.a.laye
r-wise
.clas
-
sication
.and.QoS.fram
eworks
.for.ad.hoc.netw
orks.
.QoS.over.mult
ihop
.netw
orks
.pose
s
.furt
her
.chal
-
lenges
.as.each.node.may.be.forw
arding
.mult
iple
.ows.of.vary
ing
.dema
nds
.[MRV
09].
.Rece
nt
.adva
nces
.in.
mult
iple
.inpu
t
.mult
iple
.outp
ut
.(MIM
O)
.tech
nology
.have.led.to.a.grow
ing
.inte
rest
.in.mult
iantenna
.wire
-
less
.ad.hoc.netw
orks
.wher
e
.each.node.has.more.than.one.ante
nna.
.e.adva
nces
.in.MIMO.tech
nology
.
resu
lt
.in.signi
cant
.gain
s
.in.link.capa
city
.whil
e
.comba
ting
.mult
iple
.path.inte
rference
.and.mult
iple-user
.
inte
rference,
.mak
ing
.cro
ss-layer
.app
roaches
.to.pro
viding
.QoS.att
ractive
.[GL
B09].
7.4.2 Energy Management
Since. ad. hoc.wireless. networks. are.mostly.collection. of. battery-operated. portable. devices,. ecient.
ener
gy
.mana
gement
.is.crit
ical.
.ese.netw
orks
.oer.comm
unication
.using.inte
rmediate
.mobi
le
.host
s
.to.
rout
e
.info
rmation,
.seve
rely
.stra
ining
.thei
r
.alre
ady
.limi
ted
.powe
r.
.Addi
tionally,
.in.wire
less
.sens
or
.net-
w
orks,
.many.devi
ces
.are.oper
ated
.by.batt
eries
.that.cann
ot
.be.repl
aced
.at.all..ere
fore,
.ener
gy-ecient
.
desig
ns
.are.requ
ired
.for.thes
e
.devi
ces
.to.enab
le
.them.to.oper
ate
.for.prol
onged
.peri
od
.of.time.with
-
out
.repl
acing
.batt
eries.
.e.powe
r-conservative
.sche
mes
.are.clas
sied
.into.tran
smitter
.powe
r-control
.
mech
anisms
.and.pow
er-management
.alg
orithms.
Power
. cont
rol
. invo
lves
. cont
rolling
. the. host. tran
smission
. powe
rs
. in. acco
rdance
. with. dist
ances
.
betw
een
.the.term
inals
.so.that.any.requ
ired
.crit
erion
.for.the.rece
ived
.powe
r
.can.be.sati
sed.
.In.[RR0
0],
.
two.cent
ralized
.algo
rithms
.are.prop
osed
.whic
h
.outp
ut
.the.tran
smission
.powe
r
.of.each.host.by.con-
s
tructing
.eith
er
.a.uni-
connected
.netw
ork
.or.a.bi-c
onnected
.netw
ork.
.Alth
ough
.thes
e
.algo
rithms
.are.
desig
ned
.for.stat
ic
.netw
orks
.wher
e
.loca
tion
.of.all.host
s
.is.know
n,
.they.allo
w
.a.cont
inuous
.adju
stment
.
of.the.host.tran
smission
.powe
rs
.to.main
tain
.a.cert
ain
.QoS..ese.algo
rithms,
.howe
ver,
.requ
ire
.a.guar
-
anteed
.know
ledge
.of.glob
al
.conn
ectivity
.with
out
.whic
h
.they.may.lead.to.a.disc
onnected
.netw
ork.
.is.
glob
al
.netw
ork
.conn
ectivity
.is.ensu
red
.in.[WLB
W01],
.whic
h
.assu
mes
.that.each.rece
iver
.is.able.to.dete
r-
mine
.the.dir
ection
.of.the.sen
der
.whe
n
.rec
eiving
.a.mes
sage.
Power-management
.stra
tegies
.are.appl
ied
.to.MAC.or.high
er
.laye
rs
.of.OSI.mode
l.
.e.powe
r
.cons
ump-
tion
.of.host
s
.in.ad.hoc.netw
orks
.stro
ngly
.depe
nds
.on.the.MAC.poli
cy
.[WES
W98].
.In.[BCD
99,BCD01],
.
the.auth
ors
.prop
ose
.a.dist
ributed
.cont
ention
.cont
rol
.(DCC
)
.prot
ocol,
.whic
h
.preem
ptively
.esti
mates
.the.
probability.of.successful.transmission.before.transmitting.each.frame.and.defers.transmission.if.
the.prob
ability
.of.succ
ess
.is.too.low..us,.batt
ery
.ener
gy
.is.save
d
.by.avoi
ding
.unne
cessary
.retr
ansmis-
sions,
.whic
h
.cons
ume
.signi
cant
.powe
r.
.In.[RS9
8],
.a.powe
r-aware
.mult
iaccess
.proto
col
.with.signa
ling
.
(PAM
AS)
.is.intr
oduced
.for.powe
r
.cons
ervation
.in.ad.hoc.netw
orks,
.whic
h
.prop
oses
.sepa
rate
.data.and.
signa
ling
.chan
nels.
.e.signa
ling
.chan
nel
.is.used.for.exch
anging
.RTS/
CTS
.pack
ets
.whic
h
.enab
les
.a.host.
to.dete
rmine
.when.and.for.how.long.to.powe
r
.its.ante
nna
.o..Simi
larly,
.seve
ral
.powe
r-saving
.tech
niques
.
are.prop
osed
.[CT0
0,SL01]
.for.the.netw
ork
.laye
r
.for.ad.hoc.netw
orks.
.For.rout
e
.sele
ction,
.thes
e
.proto
cols
.
not.only.take.into.acco
unt
.the.trad
itional
.rout
ing
.proto
col
.metr
ics
.such.as.hop-
count,
.link.qual
ity,
.and.
congestion.but.also.consider.battery.power.levels..Power-management.protocols.are.also.implemented.
© 2011 by Taylor and Francis Group, LLC
7-10 Industrial Communication Systems
for.transport.layer.where.the.TCP.is.modied.to.respond.appropriately.to.unreliable.wireless.environ-
ment
.by.avo
iding
.ret
ransmission
.and.ee
ctive
.con
gestion
.con
trol
.[KK
98].
.In.add
ition,
.pow
er-ecient
.
str
ategies
.are.als
o
.sug
gested
.for.the.app
lication
.lay
er
.whe
re
.the.ope
rating
.sys
tem
.(OS
)
.is.mod
ied
.to.
han
dle
.th
e
.ha
rdware
.an
d
.so
ware
.mo
re
.e
ciently
.[L
S98].
7.4.3 topology and Connectivity
In.most.of.the.ad.hoc.networks,.P2P.communication.topology.is.required,.which.means.each.node.in.
the.net
work
.mus
t
.be.abl
e
.to.com
municate
.wit
h
.any.oth
er
.nod
e
.in.the.sam
e
.net
work.
.To.att
ain
.thi
s,
.
con
nectivity
.bet
ween
.the.ent
ire
.net
works
.mus
t
.be.pro
vided
.all.the.tim
es.
.But.the.lim
ited
.res
ources,
.
unc
ontrolled
.mob
ility
.of.nod
es,
.and.the.cha
racteristics
.of.wir
eless
.com
munication
.cha
nnels
.mak
e
.it.a.
cha
llenging
.iss
ue.
.Top
ology
.and.con
nectivity
.con
trol
.can.hav
e
.a.sign
icant
.imp
act
.on.the.per
formance
.
of.wir
eless
.net
works.
.Suc
h
.alg
orithms
.are.use
d
.to.enh
ance
.ene
rgy
.ec
iency,
.min
imize
.int
erference,
.and.
inc
rease
.e
ective
.ra
te
.by.ad
justing
.tr
ansmission
.po
wer.
Topology
.con
trol
.alg
orithms
.can.be.cat
egorized
.into.cen
tralized
.and.dis
tributed
.[SB
C03].
.Cen
tralized
.
app
roach
.nee
d
.to.hav
e
.the.glo
bal
.kno
wledge
.of.the.net
work
.and.wor
ks
.wel
l
.in.sta
tic
.net
works.
.Dis
tributed
.
app
roach
.use
s
.loc
alized
.inf
ormation
.onl
y
.and.wor
ks
.wel
l
.in.mob
ile
.net
works.
.er
e
.are.man
y
.iss
ues
.
wit
h
.topo
logy
.con
trol
.alg
orithms.
.Opti
mal
.tra
nsmit
.pow
er
.com
putation
.is.one.of.the.mai
n
.cha
llenges.
.
If.hig
h
.tra
nsmit
.pow
er
.is.use
d,
.int
erference
./co
ntention
.ran
ge
.is.inc
reased.
.If.low
er
.pow
er
.is.use
d,
.it.may.
res
ult
.in.a.dis
connected
.net
work.
.Fur
thermore,
.adj
usting
.pow
er
.lev
el
.may.int
roduce
.add
itional
.lat
ency.
.
In.cen
tralized
.app
roach,
.whe
re
.all.the.inf
ormation
.is.sen
t
.to.a.cen
tral
.aut
hority,
.red
ucing
.pro
cessing
.and.
com
munication
.ove
rhead
.is.a.cha
llenging
.tas
k.
.Ec
ient
.topo
logy
.con
trol
.alg
orithms
.whi
ch
.tak
e
.nod
e
.
mob
ility
.in
to
.ac
count
.st
ill
.re
quire
.a.gr
eat
.de
al
.of.at
tention.
7.4.4 Security
Security.is.required.for.secure.communication.and.to.maintain.desired.network.performance.in.ad.
hoc.net
work
.[YL
YLZ04].
.Sec
urity
.iss
ues
.in.ad.hoc.net
works
.are.mor
e
.cha
llenging
.tha
n
.in.con
ven-
tional
.net
works
.bec
ause
.of.ope
n
.acc
ess
.mec
hanism
.and.P2P.arc
hitecture,
.no.inf
rastructure,
.hig
hly
.
dyn
amic
.net
work
.top
ology,
.pub
licly
.kno
wn
.pro
tocols,
.str
ingent
.res
ource
.con
straints,
.and.una
ttended
.
ope
ration.
Security
.for.ad.hoc.net
works
.ent
ails
.key.est
ablishment
.and.tru
st
.set
up,
.sec
recy
.and.aut
hentication,
.
pri
vacy,
.sec
ure
.rou
ting,
.int
rusion,
.and.sec
ure
.dat
a
.agg
regation
.[PS
W04].
.re
e
.mai
n
.goa
ls
.of.sec
urity
.
as.dis
cussed
.in.[DP
T03]
.are.to.mai
ntain
.con
dentiality
.(da
ta
.pro
tection),
.int
egrity
.(un
authorized
.dat
a
.
tam
pering),
.and.ava
ilability
.(se
rvice
.ava
ilability
.any
where
.and.any
time).
.Com
mon
.sec
urity
.thr
eats
.out
-
lined
.in.[PS
S00]
.and.dis
cussed
.in.[DP
T03]
.inc
lude
.“st
ealing
.con
dential
.inf
ormation,
.tam
pering
.inf
or-
mation,
.re
source
.st
ealing,
.an
d
.de
nial-of-
.se
rvice
.at
tacks.”
Following
.is.the.sum
mary
.of.the.ope
n
.res
earch
.opp
ortunities
.and.cha
llenges
.in.the.sec
urity
.imp
le-
mentation
.for.ad.hoc.net
works,
.whi
ch
.are.dis
cussed
.in.[ZF
Z08,R96,RFLW96].
.Bec
ause
.of.the.wir
eless
.
env
ironment
.and.lac
k
.of.re
wall-like
.dev
ices,
.the.eav
esdroppers
.can.spo
of
.the.ong
oing
.com
munica-
tion
.tha
t
.com
promises
.con
dentiality,
.pri
vacy,
.and.int
egrity
.of.dat
a.
.On.the.net
work
.lay
er,
.mal
icious
.
nod
es
.can.int
roduce
.den
ial-of-service
.att
acks,
.hol
es,
.and.tam
per
.inf
ormation
.com
promising
.bas
ic
.
sec
urity
.pri
mitives,
.for.exa
mple,
.ava
ilability
.and.int
egrity
.of.dat
a.
.er
efore,
.des
igning
.sec
ure
.rou
t-
ing
.pro
tocols
.is.one.of.the.cha
llenging
.are
as
.in.ad.hoc.net
works.
.[T9
7]
.and.[SM
G97]
.are.a.few.eo
rts
.
in.thi
s
.dir
ection.
.e.maj
or
.cha
llenge
.is.the.aut
hentication
.of.the.pub
lic
.key
s,
.whi
ch
.can.be.sol
ved
.by.
using.identity-based.cryptography..As.the.security.operations.are.very.frequent.in.ad.hoc.networks,.
it.req
uires
.an.ec
ient
.sym
metric
.key.alg
orithm
.for.aut
hentication
.and.enc
ryption.
.Key.rev
ocation
.
sho
uld
.hap
pen
.whe
n
.a.nod
e
.is.dec
lared
.as.mal
icious
.or.whe
n
.it.is.und
er
.com
promise
.nod
e
.att
ack.
.
Alt
hough
.di
erent
.key.rev
ocation
.sch
emes
.are.wor
king,
.sti
ll
.the
re
.is.a.dem
and
.for.uni
versal
.key.
rev
ocation
.sch
eme
.[ZF
Z08].
© 2011 by Taylor and Francis Group, LLC
Ad Hoc Networks 7-11
references
[802.11].IEEE standard for Wireless LAN Meduim Access Control: MAC and PHY Specications,.ISO/IEC.
8802-11,.1999(E),.1999.
[AA06]
.S..Ahme
d
.and.M..S..Ala
m,
.Perf
ormance
.eval
uation
.of.impo
rtant
.ad-hoc.netw
ork
.pro
tocols,
.
EURAS
IP Journal on Wireless Communications and Networking,
.1–11,.2006.
[AK04]
.J..N..Al-Ka
raki
.and.A..E..Kam
al,
.Rou
ting
.tec
hniques
.in.wire
less
.sens
or
.netw
orks:
.A.surv
ey,
.IEEE
Wir
eless Communications,
.11,.6–28,.2004.
[B01]
.C..Bis
dikian,
.An.over
view
.of.the.bluet
ooth
.wire
less
.tec
hnology,
.IEEE Co
mmunication Magazine,
.
Decem
ber
.2001.
[B04]
.A..Bou
kerche,
.Perf
ormance
.eval
uation
.of.rou
ting
.pro
tocols
.for.ad-hoc.wire
less
.netw
orks,
.Jou
rnal of
Mobile Networks and Applications,
.9,.333–342,.2004.
[B
CD01]
.L..Bon
oni,
.M..Con
ti,
.and.L..Don
atiello,
.A.dis
tributed
.mec
hanism
.for.pow
er
.sav
ing
.in.IEE
E
.802
.11
.
Wir
eless
.LAN
,
.ACM
Journal of Mobile Networks and Applications (MONET),
.6,.211
–222,
.200
1.
[BCD99]
.L..Bon
oni,
.M..Con
ti,
.and.L..Don
atiello,
.A.dis
tributed
.con
tention
.con
trol
.mec
hanism
.for.pow
er
.
sav
ing
.in.ran
dom-access
.ad-
hoc
.wir
eless
.loc
al
.are
a
.net
works,
.in.IEE
E International Workshop on
Mobile Multimedia Communications (MoMuC),
.San.Die
go,
.CA,.pp..114
–123,
.Nov
ember
.15–
17,
.199
9.
[BDSZ94]
.V..Bha
rgavan,
.A..Demer
s,
.S..Shen
ker,
.and.L..Zhan
g,
.MACAW
:
.A.medi
a
.access.pro
tocol
.for.
wire
less
.LAN
s,
.ACM S
IGCOMM Computer Communication Review,
.24(4),.212–225,.1994.
[BSH03]
.F..Bai
,
.N..Sadag
opan,
.and.A..Helm
y,
.e.IMPORT
ANT
.fram
ework
.for.ana
lyzing
.the.Imp
act
.of.
Mob
ility
.on.Perf
ormance
.Of.RouT
ing
.pro
tocols
.for.Adh
oc
.NeTw
orks,
.Jou
rnal of Ad-Hoc Networks,
.
1,.383–403,.2003.
[CCL03]
.I..Chl
amtac,
.M..Con
ti,
.and.J..J.-N..Liu
,
.Mob
ile
.ad-hoc.netw
orking:
.Imp
eratives
.and.cha
llenges,
.
Jou
rnal of Ad-Hoc Networks,
.1,.13–64,.2003.
[CGLS08]
.J..Chen,.M..Gerl
a,
.Y..Z..Lee
,
.and.M..Y..Sanadidi
,
.TCP.wit
h
.dela
yed
.ACK.for.wire
less
.netw
orks,
.
Jou
rnal of Ad-Hoc Networks,
.6,.1098–1116,.2008.
[CPF05]
.K..S..Cha
n,
.H..Pis
hro-Nik,
.and.F..Fek
ri,
.Ana
lysis
.of.hierarc
hical
.algo
rithms
.for.wire
less
.sens
or
.
netw
ork
.rou
ting
.pro
tocols,
.IEEE Wi
reless Communications and Networking Conference,
.3,.13–17,.
Mar
ch
.2005.
[CT00]
.J.-H..Cha
ng
.and.L..Tas
siulas,
.Energ
y
.cons
erving
.rou
ting
.in.wire
less
.ad-hoc.netw
orks,
.in.19th
An
nual Joint Conference of the IEEE Computer and Communications Societies (INFOCOM),
.vol
.
.1,.
Tel-A
viv,
.Israe
l,
.pp
.
.22–31,.Ma
rch
.2000.
[CZWF04]
.X..Chen,.H..Zhai
,
.J..Wan
g,
.and.Y..Fan
g,
.TCP.perf
ormance
.over.mob
ile
.ad-hoc.netw
orks,
.
Can
adian Journal of Electrical and Computer Engineering,
.29,.129–134,.2004.
[DD96]
.D..B..John
son
.and.D..A..Mal
tz,
.Dyn
amic
.sour
ce
.rou
ting
.in.ad.hoc.wire
less
.netw
orks,
.in.Mob
ile
Computing,
.Kl
uwer,
.Bos
ton,
.MA,.1996.
[D
PT03]
.D..Die
trich,
.P..Pal
ensky,
.and.A..Tre
ytl,
.Com
munication
.in.aut
omation
.wit
h
.the.emp
hasis
.on.sec
u-
rity,
.in.EUSAS (European Society for Automatic Alarm Systems) Workshop,.Rome,.Italy,.pp..89–104,.
Jun
e
.16–
17,
.200
3.
[F94]
. S.. Floyd
,
. TCP. and. explicit. cong
estion
. not
ication,
. ACM J
ournal of SIGCOMM Computer
Communication Review,
.24,.8–23,.1994.
[FBP98]
.M..Falo
utsos,
.A..Ban
erjea,
.and.R..Pan
kaj,
.QoSMI
C:
.Qua
lity
.of.serv
ice
.sensi
tive
.mul
ticast
.Int
ernet
.
Pro
tocol,
.SI
GCOMM Computer Communication Rev.
.28(4),.144–153,.1998.
[FG95]
.C..L..Fu
llmer
.an
d
.J..J..Gar
cia-Luna-Aceves,
.Floo
r
.acqui
sition
.mu
ltiple
.access.(FAMA).fo
r
.pac
ket-
radio
.net
works,
.ACM S
IGCOMM Computer Communication Review,
.25,.262–273,.1995.
[GLB09]
.R..Guima
rães,
.L..Cerd
à,
.J..M..Bar
celó,
.J..Garcí
a,
.M..Voo
rhaen,
.and.C..Blon
dia,
.Qua
lity
.of.ser-
v
ice
.thro
ugh
.ban
dwidth
.reser
vation
.on.mul
tirate
.ad-hoc.wire
less
.netw
orks,
.Ad-ho
c Networks,
.7(2),.
388–400,.Ma
rch
.2009.
[IR1]
. OPNE
T.
Mode
ler
. versio
n
. 10.5,. OPNE
T
. Tec
hnologies,
. Inc.,. avai
lable
. at. htt
p://www.opnet.com,
.
accessed.on.December.13,.2009.
© 2011 by Taylor and Francis Group, LLC
7-12 Industrial Communication Systems
[KHP08].D..Koutsonikolas1,.Y..C..Hu,.and.K..Papagiannaki,.How.to.evaluate.exotic.wireless.routing.protocols?.
in.Pro
ceedings ACM HotNets,
.Cal
gary,
.Can
ada,
.Oct
ober
.200
8.
[KK00]
.B..Kar
p
.and.H..T..Kung
,
.GPSR:.Gre
edy
.perim
eter
.sta
teless
.rou
ting
.for.wire
less
.netw
orks,
.in.
Pro
ceedings of the 6th Annual international Conference on Mobile Computing and Networking,
.
Bost
on,
.MA,.Augu
st
.2000.
[KK98]
.R..Krav
ets
.and.P..Kri
shnan,
.Pow
er
.man
agement
.tec
hniques
.for.mob
ile
.communic
ation,
.in.ACM
In
ternational Conference on Mobile Computing and Networking (MobiCom),
.New.Yor
k,
.pp..157–168,.
Oct
ober
.1998.
[KKFT02]
.S..Kop
party,
.S..Kri
shnamurthy,
.M..Falo
utsos,
.and.S..K..Tri
pathi,
.Spli
t
.TCP.for.mob
ile
.ad-hoc.
net
works,
.IEE
E Global Telecommunications Conference GLOBECOM ‘02,
.vol
.
.1,.Tai
pei,
.Tai
wan,
.
pp..138–142,.No
vember
.2002.
[KLSSK02]
.V..Kan
odia,
.C..Li,.A..Sabh
arwal,
.B..Sadeghi,.and.E..Knigh
tly,
.Dist
ributed
.prio
rity
.sch
eduling
.
and.me
dium
.access.in.ad-ho
c
.net
works,
.ACM J
ournal of Wireless Networks,
.8,.455–466,.2002.
[K
MS05]
.I..Kar
thigeyan,
.B..S..Man
oj,
.and.C..Siv
a
.Ram.Mur
thy,
.A.dis
tributed
.lax
ity-based
.pri
ority
.sch
eduling
.
sch
eme
.for.tim
e-sensitive
.tra
c
.in.mob
ile
.ad-
hoc
.net
works,
.Jou
rnal of Ad-hoc Networks,
.3,.27–
50,
.200
5.
[KRD06]
.S..Kuma
r,
.V..S..Rag
havan,
.and.J..Deng
,
.Medi
um
.access.cont
rol
.pro
tocols
.for.ad-hoc.wire
less
.
netw
orks:
.A.sur
vey,
.Ad H
oc Networks,
.4(3),.326–358,.Ma
y
.2006.
[LS01]
.J..Liu.and.S..Sing
h,
.ATCP
:
.TCP.for.mob
ile
.ad-hoc.netw
orks,
.IEEE Jo
urnal on Selected Areas in
Communications,
.19,.1300–1315,.2001.
[LS98]
.J..R..Lorch.and.A..J..Smith,.Soware.strategies.for.portable.computer.energy.management,.IEEE
Jou
rnal of Personal Communications,
.5,.60–73,.1998.
[MB00]
.B..A..Mi
ller
.an
d
.C..Bi
sdikian,
.Bl
uetooth Revealed,
.Pr
entice
.Ha
ll,
.Ne
w
.Yo
rk,
.2000.
[M
K04]
.P..Moh
apatra
.and.S..Kri
shnamurthy,
.Ad-
hoc Networks: Technologies and Protocols,
.Spr
inger,
.
New.Yor
k,
.2005.
[M
RV09]
.J..C..Mun
darath,
.P..Ram
anathan,
.and.B..D..Van.Vee
n,
.A.qua
lity
.of.ser
vice
.awa
re
.cro
ss-layer
.app
roach
.
for.wir
eless
.ad-
hoc
.net
works
.wit
h
.sma
rt
.ant
ennas,
.Ad
Hoc Networks,
.7(5
),
.891
–903,
.Jul
y
.200
9.
[MSGJ96]
.S..Murt
hy
.and.J..J..Gar
cia-Luna-Aceves,
.An.ec
ient
.rou
ting
.pro
tocol
.for.wir
eless
.net
works,
.
Jou
rnal of Mobile Networks and Applications,
.1,.183
–197,
.199
6.
.htt
p://dx.doi.org/10.1007/BF01193336
[MWH01]
.M..Mau
ve,
.J..Widmer
,
.and.H..Har
tenstein,
.A.surv
ey
.on.posit
ion-based
.rou
ting
.in.mob
ile
.ad-
hoc
.net
works,
.IEEE Ne
twork Magazine,
.15,.30–39,.2001.
[N70]
.N..Abra
mson,
.e.ALOH
A
.system:.Ano
ther
.alt
ernative
.for.comp
uter
.communic
ations,
.AFIPS Jo
int
Computer Conferences,
.Vo
l.
.37,.Ho
uston,
.TX,.pp
.
.281–285,.No
vember
.17–19,.1970.
[O
SL05]
.L..B..Oli
veira,
.I..G..Siq
ueira,
.and.A..A..F..Lou
reiro,
.On.the.perf
ormance
.of.ad-
hoc
.rou
ting
.pro
tocols
.
und
er
.a.pee
r-to-peer
.app
lication,
.Jou
rnal of Parallel and Distributed Computing,
.65,.133
7–1347,
.200
5.
[PC97]
.V..Par
k
.and.S..Cor
son,
.Temp
orally-ordered
.rou
ting
.algo
rithm
.(TOR
A),
.vers
ion 1 functional speci-
cation, ETF Internet dra, IETF MANET Working Group,
.Flar
ion
.Tec
hnologies,
.Inc..Bridg
ewater,
.
NJ,.1997.
[PD
H07]
.H..Pucha,.S..M..Das,.and.Y..C..Hu,.e.perf
ormance
.impac
t
.of.trac.pat
terns
.on.rou
ting
.pro-
t
ocols
.in.mob
ile
.ad-hoc.netw
orks,
.Com
puter Networks: e International Journal of Computer and
Telecommunications Networking,
.51,.3595–3616,.2007.
[PP94]
.C..E..Perk
ins
.and.P..Bha
gwat,
.High
ly
.dyn
amic
.destin
ation
.seq
uenced
.dist
ance
.vec
tor
.rou
ting
.
(DSDV
)
.fo
r
.mo
bile
.com
puters,
.Co
mputer Communication Review,
.234–244,.Oc
tober
.1994.
[PR99]
.C..Perk
ins
.and.E..Roy
er,
.Ad-ho
c
.on.deman
d
.dist
ance
.vec
tor
.rou
ting,
.in.Pro
ceedings of the 2nd
IEEE Workshop on Mobile Computing Systems & Applications,
.Ne
w
.Orle
ans,
.LA,.Fe
bruary
.1999.
[PSS00]
.P..Palen
sky,
.T..Saut
er,
.and.C..Sch
waiger,
.Sec
urity
.und.Feld
busse—ein
.Widers
pruch,
.Jou
rnal of
Information Technology,
.42,.31–37,.2000.
[PSW04]
.A..Perr
ig,
.J..Sta
nkovic,
.and.D..Wag
ner,
.Sec
urity
.in.wire
less
.sens
or
.netw
orks,
.Com
munications of
the ACM,
.47,.53–57,.2004.
[R96]
.M..K..Reit
er,
.Dist
ributing
.tru
st
.wit
h
.the.Ram
part
.too
lkit,
.Com
munications of the ACM,
.39(4),.
71–74,.1996.
© 2011 by Taylor and Francis Group, LLC
